February 21, 2017
Introduction
New, sophisticated threats continue to emerge on a daily basis across multiple platforms: social media, mobile platforms, email, and web pages. At the same time, prominent malware and attack methods continue to evolve, bypassing existing security solutions, and tailoring attacks against the largest companies in the world. The devices we use every day are now subject to compromise and can be leveraged for attacks. Even the recent U.S. elections were targeted with significant attacks. The Check Point 2016 H2 Global Threat Intelligence Trends report provides you with the best overview of the cyber landscape; threats, data breaches, trends, attacks and predictions, based on data drawn from the ThreatCloud World Cyber Threat Map between July and December 2016. Information about threats, trends and attacks divided by region can be found in our Check Point 2016 H2 Regional Threat Intelligence Trends report.
Global Trends
DDoS Attacks via IOT Devices
August marked the introduction of the now infamous Mirai Botnet – a first of its kind Internet-of-Things (IoT) Botnet, which attacks vulnerable Internet-enabled digital video recorders (DVR), surveillance cameras (CCTV), and other Internet-enabled devices. It turns them into bots, using the compromised devices to launch multiple high-volume Distributed Denial of Service (DDoS) attacks. In October, the botnet and scanner source code were released publicly – an act which opens the door for future botnet attacks of this kind, making it clear that we will continue to see massive DDoS attacks that utilize such devices.
The Monopoly in the Ransomware Market
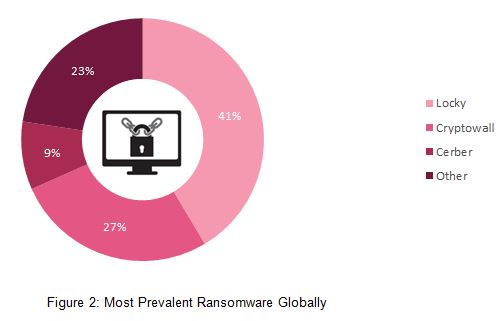
Although thousands of new ransomware variants were observed in 2016, in recent months we witnessed a change in the ransomware landscape, it became more and more centralized, with a few significant malware families dominating the market and hitting organizations of all sizes. Cerber and Locky were first introduced in spring 2016 and over the last few months, new versions of those ransomware families were constantly discovered. Our data even shows that Cerber is ranked among the top 20 malware family attacks in the APAC region.
New File Extensions Used in Spam Campaigns
According to statistics collected by our researchers, the most prevalent infection vector used in malicious spam campaigns throughout the second half 2016 was downloaders based on Windows Script engine (WScript). Downloaders written in Javascript (JS) and VBScript (VBS) dominated the mal-spam distribution field together with similar yet less familiar formats such as JSE, WSF, and VBE.
Different malicious attachments were often sent in zip and rar archives. As many email services, and even clients, block such files by default, Office documents and PDF files are exceptional and commonly sent “as is.” Although there was an increase in large-scale spam campaigns with reasonable social engineering applied, our observations show that the majority of the malicious spam is still poorly written and does very little to convince users of its legitimacy.
Mobile Trends
Threat Factors
Banking Trojans and rough ad-networks remained the main money-making vectors for large scale malware campaigns, with mobile-ransomware found to be on the rise. Interestingly, many banking Trojans have started developing ransomware capabilities as a secondary attack vector. Additionally, as a response to the IoT-based DDOS attacks trend reported above, Google has announced “Android Things”, an IoT OS which will presumably address such security issues and will further extend Android’s relevance.
Threat actors
Following the terrorist acts in Paris and San Bernardino, there has been a lot of discussion regarding the role of mobile-security and secured apps, such as Telegram, in facilitating stealthy communications for terrorists. This controversy peaked at the FBI–Apple encryption dispute , where Apple’s security mechanisms collided with law enforcement needs. Mobile-espionage is likely to become an increasingly active and tense cyber-warzone.
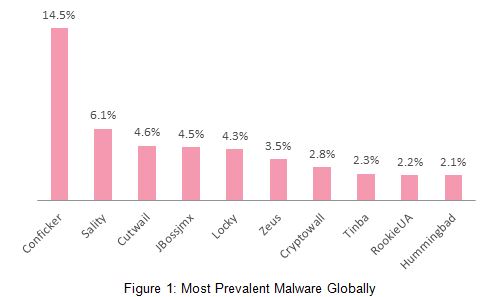
Top Malware Global rank – H2 2016
Top Malware Families
Top Ransomware
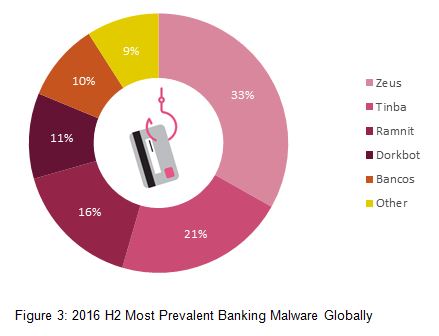
Top Banking Malware
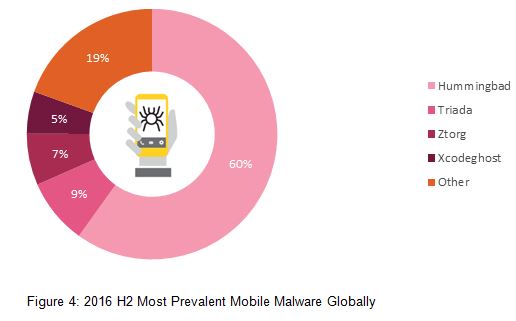
Top Mobile Malware (Global)
Top 2017 Predictions
- IoT devices – both attack target and source – In late December, an LG smart TV running Google TV was found to be infected by the Flocker Android ransomware. We believe that in 2017 the sophistication level of such attacks, as well as scale and diversity, will increase. Devices will be held for ransom, access will be sold on the Dark Web, and compromised devices located within sensitive networks may lead to severe operational damage. Not only will IoT devices be subjected to various attacks, they will also be leveraged to attack other systems, and to launch massive DDoS attacks, such as the Mirai botnet operations. As those devices play an increasing role in our lives, our privacy is now more than ever at risk.
- Malware-as-a-Service industry will take on additional forms – Drive-by attack methods, malware code and a variety of other tools are sold and traded in a business method referred to as Malware-as-a-Service. For instance, Cerber, a ransomware-as-a-service, was one of the most dominant and profitable ransomwares of 2016. We estimate that new and unique collaboration frameworks will continue to emerge, each one more profitable for the actors and destructive for the public.
- Politically-oriented attacks, or psychological warfare – Cyber-attacks were at the heart of the U.S. presidential campaign, as the Democratic National Committee (DNC) experienced a severe security breach. Cyber actions have played a significant role in international affairs, and will become an integral part of every political actor’s toolbox.
- Infection via Steganography (Image Files) – In late November, Check Point researchers exposed a new attack vector, named ImageGate, which embeds malware in image and graphic files. Following that, Locky ransomware has started spreading via SVG and PNG files through Facebook as well. The use of image files, which can easily be uploaded to most of today’s dominant social media websites, creates a whole new set of tools for attackers.
Conclusion
The second half of 2016 demonstrates the nature of today’s cyber environment. New attack vectors targeting home devices as well as large organizations were revealed. At the same time, a few older ransomware families managed to maintain their control over the ransomware market. Ransomware attacks stand out clearly, as the percentage of ransomware out of all recognized attacks worldwide nearly doubled in the second half of the year, from 5.5% in the first half to 10.5% in the second. Our data demonstrates a long tail distribution of some prominent families, and we can also see that most cyber threats are global and cross-regional, although the APAC region stands out as its Top Malware Families chart includes 5 families which do not appear in the other regional charts.
The statistics in this report are based on data drawn from the ThreatCloud World Cyber Threat Map between July and December 2016. Check Point’s ThreatCloud is the largest collaborative network to fight cybercrime, delivering the most up-to-date threat data and cyberattack trends from a global network of threat sensors. The ThreatCloud database identifies millions of malware types daily, and contains more than 250 million addresses analyzed for bot discovery, as well as over 11 million malware signatures and 5.5 million infected websites.