Introduction
Cobalt Group is a financially motivated cyber-crime gang that has been active since at least 2016. The group is mainly interested in carrying out attacks against banks, in an attempt to access the banks’ internal networks and potentially take over sensitive components, such as ATM-controlling servers or card-processing systems. Although the Europol arrested Cobalt Group’s leader in 2018, the group remains active until this day.
Check Point Research recently uncovered a Cobalt Group campaign that went after a bank in Kazakhstan, and crafted a particularly convincing malicious document carrying the bank’s logo. What is more worrying is that the document itself could have been downloaded from the bank’s official website, adding to its legitimacy and making potential victims less suspicious. This article will describe the full infection chain of the attack, as well as the attribution process of this attack.
Decoy Document
The investigation into this attack started when we came across a malicious document hosted on the promotional website of the Kassa Nova Bank, which according to its description provides financial products and services to the public and to small enterprises in Kazakhstan.
The malicious file was hosted amongst the documents repository of the bank, making it even easier to confuse with a legitimate document:
https://kassanova[.]kz/files/docs/T47188445.doc
After being downloaded and launched, the document displays a decoy message in Russian asking victims to enable its content. Coupled with the use of Kassa Nova’s logo in the document’s body, this socially-engineered content can easily trick victims to run the embedded malicious macros:
 Figure 1: The decoy document
Figure 1: The decoy document
MD5: 7f0f3689b728d12a00ca258c688bf034
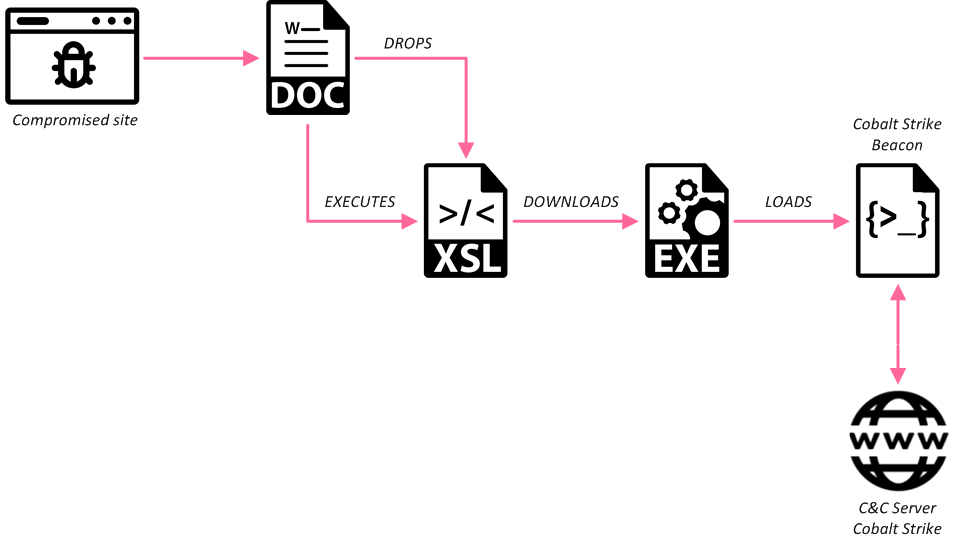
Enabling the macros starts a multi-stage infection chain that eventually downloads and executes a Cobalt Strike beacon, providing the attackers with a foothold inside the target organization.
Such use of common penetration testing tools for offensive operations is a known practice among many threat groups, especially Cobalt Group. Not only does this practice saves threat actors a lot of development effort, it also makes the attribution a lot harder.
 Figure 3: Obfuscated macros code
Figure 3: Obfuscated macros code
The Macros
The Document_Open macro function is automatically triggered by Word once the user presses the “Enable Macros” button.
The code used is heavily obfuscated, the variable names appear to be randomly generated, and the code contains comments that are a combination of random words:
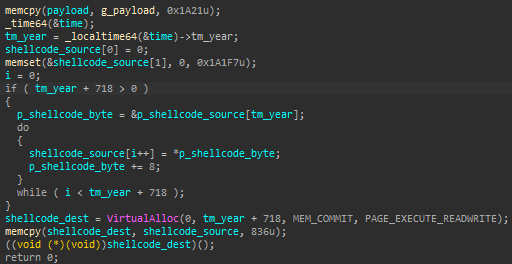
The purpose of the macros is to write an XSL file to the local disk, C:\Windows\Temp\aA3jY9HP.xsl, and run it using an execution technique known as “SquiblyTwo”.
 Figure 4: Shell execution of Jscript using WMIC
Figure 4: Shell execution of Jscript using WMIC
This technique makes use of the legitimate WMIC utility, where attackers can invoke either JScript or VBScript code form an XSL file, simply by running the following command:
wmic os get /format:[XSL_FILE_PATH]
In our case, the XSL file contains JScript code that downloads the next stage executable from a remote server address, runs it, and eventually deletes the XSL file to remove any traces:
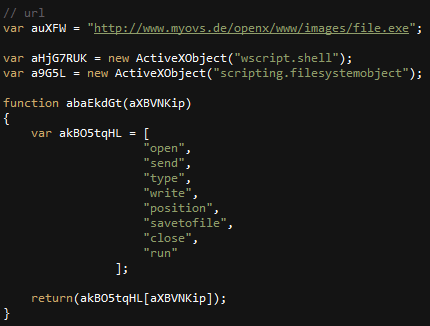 Figure 5: Snippet from the JScript embedded in the XLS file
Figure 5: Snippet from the JScript embedded in the XLS file
The domain which hosted the next stage payload, myovs[.]de, belongs to Otto Schmidt, a German media company in the tax, business, and corporate law market. Apparently, this company’s website was also compromised prior to the attack.
The Payload
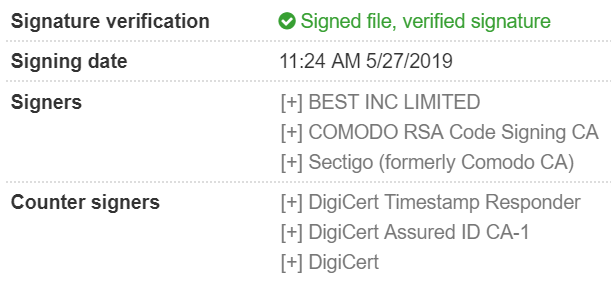
The downloaded “file.exe” payload is a signed executable, and it has a valid certificate by Sectigo:
Figure 6: Signed downloaded payload
MD5: a26722fc7e5882b5a273239cddfe755f
The executable communicates with 185.61.149[.]186/rpc to download and decrypt a Cobalt Strike beacon. The beacon then communicates with the following URL on the same IP address:
http://185.61.149[.]186/owa/?wa=UdHv7kfAh0akFkK7uZW2P721Wm-ceiYOj1wqEiX7QBO6kvCNkDwV_Pbukex3OZnbJ6vDEY3ipA9ZLnKXnzKobrVlsrak93OoUclN-ofsPEHv_7_1CT1Jcqtcwxiv6rQO53GpZd5hTYG4hfP4s96PWTb3IkM9H3VTbu8RnaSplGs&path=/calendar
Surprisingly, this communication resembles legitimate requests made when viewing the Office 365 Outlook calendar. Looking up the unique request header led us to a GitHub project called “Malleable C2 Profiles”, which offers a variety of “profiles” that mimic the communication patterns of legitimate services, known malware families or even APT groups.
This can be an effective way of evading detection and exfiltrating data from an infected system, without raising any suspicions, as someone monitoring the network might mistake this for legitimate Office 365 traffic.
Cobalt Trails
Even though the existence of Cobalt Strike beacons in association with a Central Asian bank reduces the amount of possible responsible APT groups to a very short list, additional evidence was required in order to conclude that Cobalt Group was behind this operation.
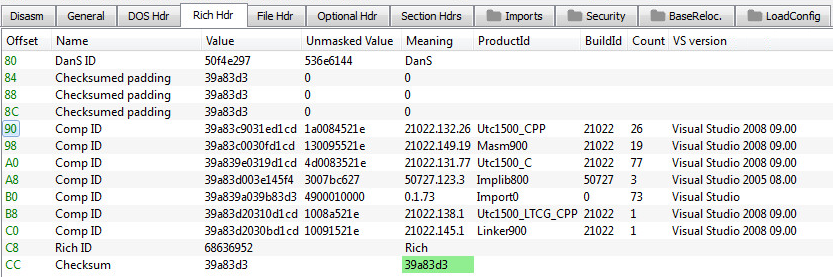
When investigating executable files, one can gain insight into what tools the developers (or threat actors) used to compile the executable file, by looking at the “Rich Headers”.
At times this information about the development environment can lead to more samples from the same threat actor, which reused the same building environment over multiple compilations of the same variants of malware.
Figure 7: Decoded Rich Headers from the payload (as shown by PE-bear)
Utilizing this technique to find similar files, we were able to uncover a large number of similar Cobalt Strike loaders.
Comparing the loaders’ logic verifies our assumption that the samples are indeed related:
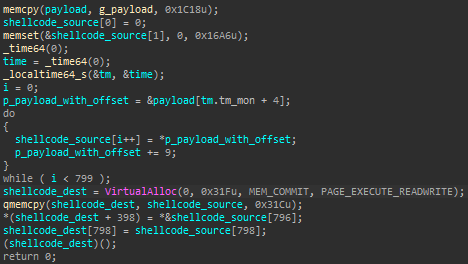
Both samples rely on a similar algorithm in order to correctly extract the next stage shellcode, using the current month or the year as an offset for the decoding, as noted by @VK_Intel.
If the month or the year do not match the intended window of operation, the next stage of the attack would not be executed correctly.
Figure 8: “file.exe” payload Figure 9: Matched sample
Furthermore, one of the found samples exhibited a unique project name in its debugging information: BATLE_SOURCE
C:\Users\d\Documents\тр\shell\BATLE_SOURCE\ONLY_EXE\SMRS-30.10.2018\smrs\Release\smrs.pdb
MD5: 02c11b8697aeec84249316733c2a0c2d
This is the exact project name (and similar folder path) as can be found in older, previously attributed Cobalt Group loaders, which can be traced back to 2016:
C:\Users\DNS\Documents\тр\shell\BATLE_SOURCE\SampleService_run_shellcode_from-memory10-02-2016\Release\SampleService.pdb
MD5: af82af8f5d540943aaba20920d015530
After taking into the account the overlap in TTPs, targets and the technical similarities to previous attacks, we were able to associate this campaign to Cobalt Group operations with high confidence.
Macro Builder Kit
In addition to the executable payload, during our investigation, we tried to hunt for similar documents by using unique features of the involved artifacts. Interestingly enough, we were able to find several malicious samples that emerged around the same time we discovered the document in question.
The comparison below between the VBA call graph of the Kassa Nova document macros and another document we found shows that they are quite similar, with the only difference being the random function names, which still maintain the same string length:
 Figure 10: The VBA call graph from the analyzed campaign
Figure 10: The VBA call graph from the analyzed campaign
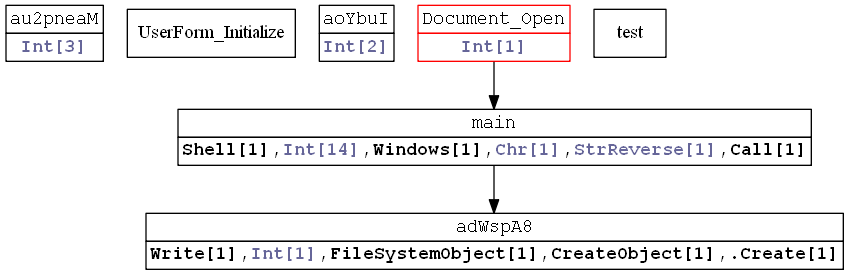 Figure 11: The VBA call graph from another campaign
Figure 11: The VBA call graph from another campaign
Moreover, the XSL files that were dropped by these documents are almost identical to the one dropped by the attack we described and even included the same comments and code formatting. However, this appeared to be the only connection between these delivery documents and ours, since they would eventually drop banking Trojans such as Dridex, IcedID and Ursnif.
The fact that the payloads belong to different campaigns suggests that once again Cobalt Group utilized a macro builder kit sold in underground criminal forums. In the past, Cobalt Group was observed utilizing other “commercial” exploit building frameworks such as “ThreadKit” and “Microsoft Word Intruder”.
Previous Attacks
Cobalt group is known to be especially active in Eastern Europe and Central Asia, and as it turns out, this is not even the first time that Kassa Nova bank was involved in a Cobalt Group related attack: During December 2018, a malicious attachment was sent from the e-mail address belonging to one of the bank’s employees, to other potential targets in the financial sector.
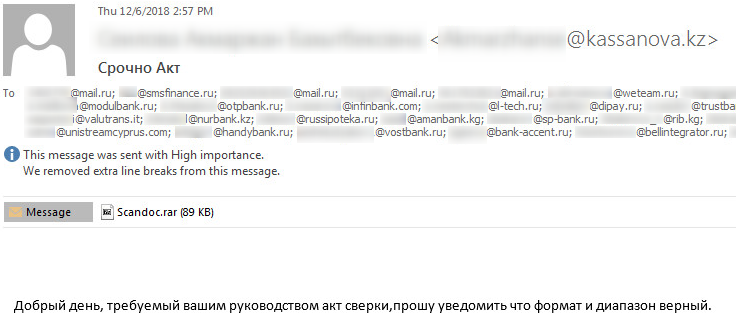 Figure 12: Malicious E-mail from Kassa-Nova bank to partners
Figure 12: Malicious E-mail from Kassa-Nova bank to partners
This is known TTP of Cobalt Group – compromising one company in order to compromise another, by sending malicious emails from a credible trusted partner.
The e-mail attachment in question utilized the newly disclosed CVE-2018-15982 to install CobInt – a signature reconnaissance tool used by Cobalt Group, only a day after 360CoreSecurity disclosed information about the use of this 0-day in the wild.
Conclusion
Whether it is compromising the bank’s website, building a tailored document to masquerade as a legitimate one, using a valid certificate for the payload and more, this looks like another well-calculated attack that was carefully planned ahead of time. Cobalt Group does not seem to be bothered by the arrest of one of its leader and is rather expanding its toolset and going after new targets.
Check Point contacted the representatives of the Kassa Nova bank as soon as the attack was discovered, who then confirmed that the attack was detected by internal systems and successfully remediated.
Appendix A: IOCs
https://kassanova[.]kz/files/docs/T47188445.doc – Malicious document drop-zone
7f0f3689b728d12a00ca258c688bf034 – MD5: Malicious document
a26722fc7e5882b5a273239cddfe755f – MD5: Downloaded Payload
185.61.149[.]186 – Cobalt Strike beacon C2
Appendix B: Cobalt beacon configuration
Decoder: proper_beacon_decoder.py by Jason Reaves and Josh Platt
{
'PROTOCOL': '0',
'SPAWNTO_X64':'%windir%\\sysnative\\gpupdate.exe',
'SLEEPTIME': '30000',
'C2_VERB_GET': 'GET',
'DNS_SLEEP': '0',
'MAXGET': '1398102',
'USERAGENT': 'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko)', 'PORT': '80',
'DNS_IDLE': '134744072',
'C2_POSTREQ': "[('_HEADER', 0, 'Accept: */*'), ('BUILD', ('BASE64URL',)), ('PREPEND', 0, 'wla42='), ('PREPEND', 0, 'xid=730bf7;'), ('PREPEND', 0, 'MSPAuth=3EkAjDKjI;'), ('PREPEND', 0, 'ClientId=1C0F6C5D910F9;'), ('PREPEND', 0, 'MicrosoftApplicationsTelemetryDeviceId=95c18d8-4dce9854;'), ('HEADER', 0, 'Cookie')]",
'WATERMARK': '3',
'PUBKEY': '30819f300d06092a864886f70d010101050003818d00308189028181008f8c237f7f407fcf5f47e2d76c589982b2595ead0d45d4e4ea875b2d07f2b8283f64786c7a142d3ce78baa01d1bb14479162d14520cc8ba15b1dc0b5e57850ab7bccb95838156dec5b58097a007d0180e358e144653d80381ac240efe9b789adf5f319515651bdfc3eb160b411f5cba2b8e7e21cb2cbc743b5ffb6fba5d2b8ff0203010001',
'SPAWNTO_X86': '%windir%\\syswow64\\gpupdate.exe',
'C2_REQUEST': "[('_HEADER', 0, 'Accept: */*'), ('_HEADER', 0, 'Cookie: MicrosoftApplicationsTelemetryDeviceId=95c18d8-4dce9854;ClientId=1C0F6C5D910F9;MSPAuth=3EkAjDKjI;xid=730bf7;wla42=ZG0yMzA2KjEs'), ('BUILD', ('BASE64URL',))]",
'CRYPTO_SCHEME': '0',
'JITTER': '20',
'C2_CHUNK_POST':'96',
'PIPENAME': '',
'C2_VERB_POST': 'GET',
'SUBMITURI': '/OWA/',
'DOMAINS': '185.61.149.186,/owa/',
'MAXDNS': '235'
}