Check Point researchers have carried out an investigative research that allows for a rare opportunity of coming face to face with real-life threat actors. In this case, these threat actors are an Indonesian group called “plaNETWORK”. In operation for the past 7 years, plaNETWORK develops various hacking tools and has actively used them in a large number of hacking incidents. What’s more, those involved in plaNETWORK enjoy bragging about their malicious activity.
Due to the detailed insights into who these threat actors may be, Check Point Research has responsibly reported their findings regarding plaNETWORK to regional law enforcement agencies who are now looking into the matter.
It All Begins With a PHP WebShell Attack on Drupal Servers
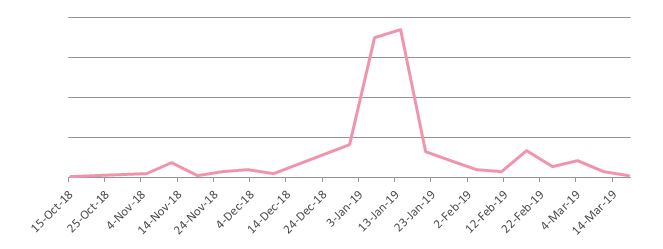
Early January this year we witnessed a surge in attacks utilizing a unique PHP WebShell, attempting to exploit a known Drupal vulnerability dubbed “Drupalgeddon”.
Fig 1: plaNETWORK propagation attempts over time
The PHP WebShell in itself was not out of the ordinary, with its capabilities including:
- Uploading files to a remote server
- Opening a reverse shell
- Executing remote commands
- Auto-defacer for multiple popular CMS’s
With these capabilities, a successful hack would grant attackers the ability to do anything with the victims’ systems.
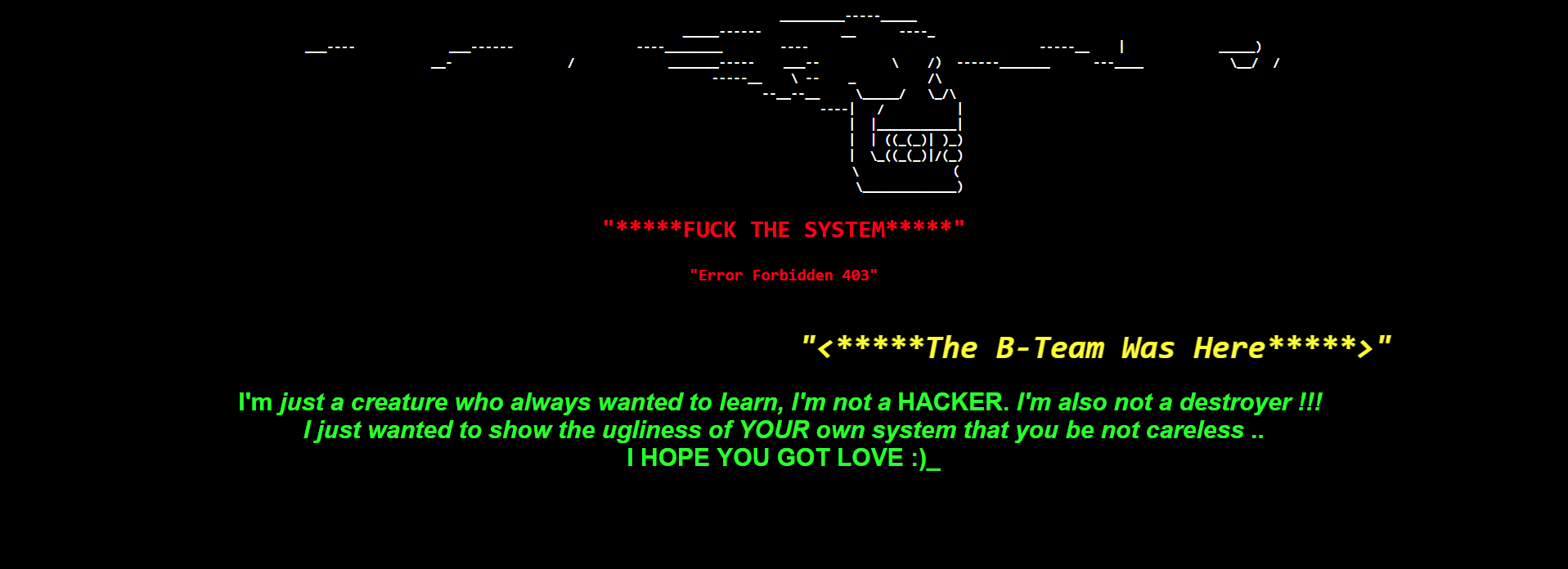
Fig 2: Defaced screen of a hacked site
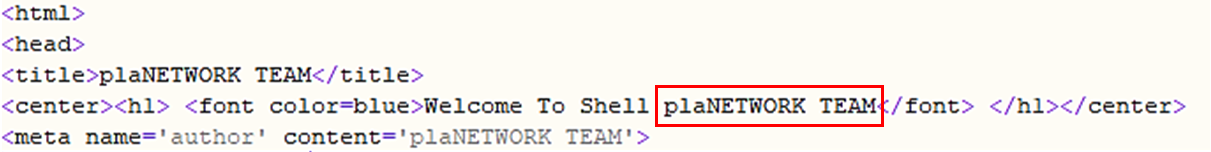
A closer look at the uncovered code, however, revealed a number of interesting strings: several words in Indonesian, various links to code repositories and finally, multiple references to the previously unknown “plaNETWORK team”.
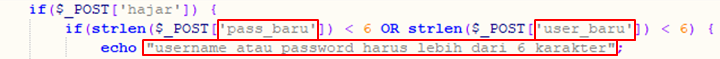
Fig 3: Indonesian functions: “pass_baru” = new pass; “username atau password harus lebih dari 6 karakter” = Username or password must be more than 6 characters
Fig 4: References to the plaNETWORK team in the WebShell code
The code also revealed a phrase we would encounter in multiple occasions on our investigative journey: “We Are Not Hacker”
Fig 5: The “We Are Not Hacker” reference in the code
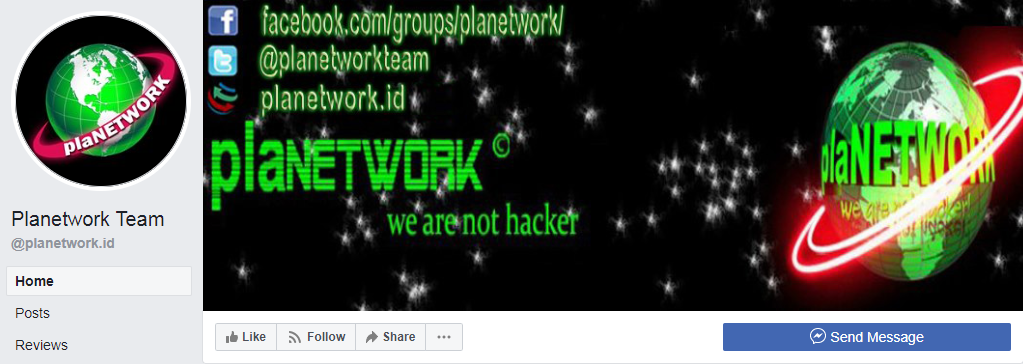
‘plaNETWORK’ – IT Consultancy or Cyber Hacking Group?
Upon searching for ‘plaNETWORK’, the term brought up several legitimate organizations which weren’t quite what we were looking for. Adding Indonesia to the search narrowed it down though, and we were led to the IT consultancy website below:
Figure 6: plaNETWORK IT Support website
While their website “www.planetwork[.]co.id” offers a variety of IT services, it does not appear to be frequently updated. For example, the website features a promotion offer that was expired at the beginning of 2018 in addition to their servers being offline.
At first glance, the company appears to be a legitimate service, and is unlikely to be related to the PHP WebShell we discovered earlier, but we pursued with our investigation just to be sure.
The website features links to multiple social platforms, including Facebook and Twitter.
Unexpectedly, looking at the Twitter account, we were given our first clue that we were indeed on the right path.
Fig 7: Twitter description, translated:
“Receive web page creation services. Interested? Contact via IRC/Web Site”
The Twitter account features the same, very specific, “We Are Not Hacker” slogan, as we’ve previously seen in the WebShell code (Figure 5).
At this point of our investigation, we could safely conclude that the WebShell was pointing us to this little IT company in Indonesia, however one question remained:
Were they really the ones behind the creation of the malicious WebShell, or were they being framed?
Following the Facebook trail, the location of their offices was mentioned in their About page, providing us with our next clue.
Fig 8: plaNETWORK IT Support HQ location
To get closer to the answer, we boarded the ‘Google Earth’ ship to get a closer look at plaNETWORK’s office location.
Fig 9: Zooming in to plaNETWORK’s address in Gorontalo
On the same road as advertised, located in the city of Gorontalo on the Indonesian island of Sulawesi, we found plaNETWORK’s office sign directing us to some of their points of contact.
Fig 10: Street view of store front with names and phone numbers
With the phone number on the sign matching the phone number advertised on the official website, we were confident that we arrived at the right place.
Furthermore, the additional phone numbers on the sign led to us to the Facebook profiles of Farid and Hendra, who not only serve as Facebook page admins in the aforementioned official Facebook page, but also in another page related to plaNETWORK.
The Facebook pages even serve as admins of one another, providing a solid connection between them.
Fig 11: “Planetwork It Support” as page admin of “plaNETWORK”
This newly discovered Facebook page doesn’t look like an IT company any longer, and yet again reveals the true nature of this group, reiterating “We Are Not Hacker”:
Fig 12: Facebook group profile
plaNETWORK’s Key Players on Social Media
A few questions arise in order for us to understand a little more about the reach of plaNETWORK and who is behind this suspicious looking organization. Questions such as, how extensive is their hacking activity? Does plaNETWORK just write the hacking code for others to use or do they also do the hacking themselves? How many people are involved in these activities?
To attempt to answer these questions, we dove in deeper and took a look at their social media presence for any clues.
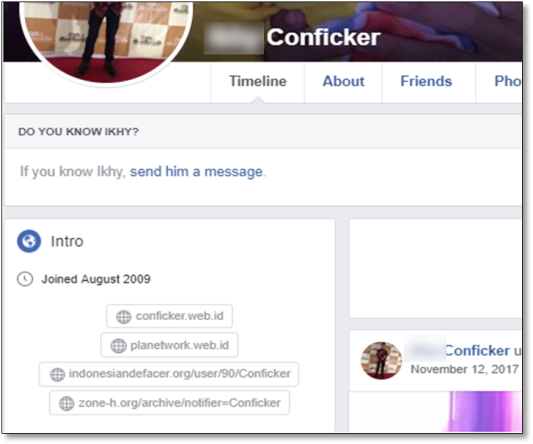
Usually when researching threat actors, attribution to specific individuals is rare. In the case of plaNETWORK, though, we found a list of real Facebook profiles, as well as one profile with a nickname fashioned after the notorious Conficker worm:
Fig 13: Facebook group members and admins
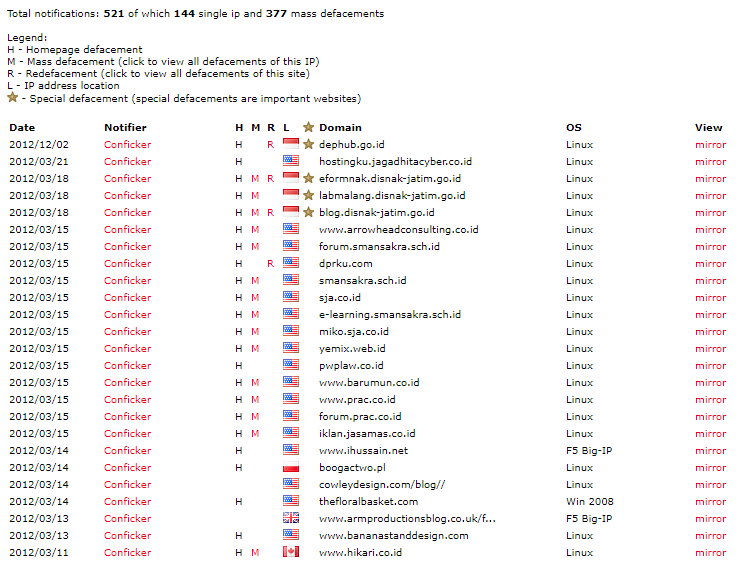
It seems that “Ikhy Conficker” plays a pretty active role in the plaNETWORK team, featuring the team on Conficker’s Facebook profile together with a link to their defacement activity on indonesiandefacer[.]org and zone-h[.]org.
Fig 14: Ikhy Conficker’s Facebook profile
Fig 15: Ikhy Conficker’s Defacements on zone-h.org
So Ikhy Conficker is a hacker defacing dozens of websites. But is this part of the plaNETWORK team’s main activity?
Celebrating plaNETWORK’s Anniversary on YouTube
To get closer to an answer, we decided to get acquainted with the whole team and the atmosphere within which plaNETWORK operates. This led us to a YouTube video in which plaNETWORK can be seen celebrating their group’s 7th anniversary. Once again they reveal their faces, along with their nicknames.
Moreover, they brag about their hacking activities, featuring “brute force attack”, “Backdoors”, “Anonymous condition”, “Back connect”, “Bind”:
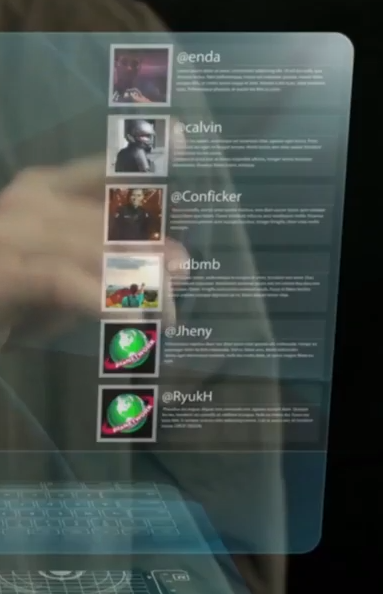
Fig 16: plaNETWORK group members’ nicknames in their anniversary clip
The nicknames of the different group members as spotted in the video: enda, calvin, Conficker, idbmb, Jheny, RyukH, Sonic, Bandila, Ady27.
Fig 17: plaNETWORK team celebrating their 7th anniversary
Fig 18: plaNETWORK with IT services and “We Are Not Hacker” motto combined
Fig 19: “We Are Not Hacker” cake from anniversary movie
More interesting evidence appears in another video on plaNETWORK’s YouTube channel showing an innocuous enough title, stating that it is a beginner’s tutorial for creating websites.
Fig 20: The PlaNetwork YouTube channel
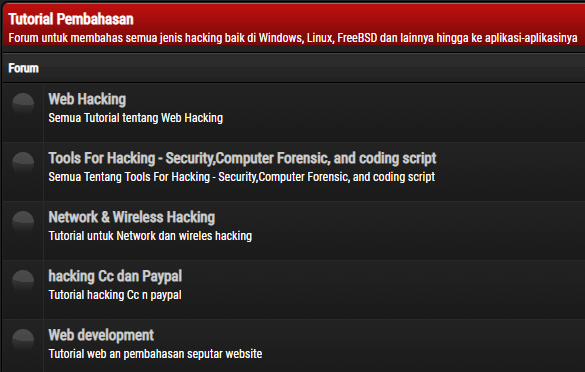
However, a closer look at that video’s display image shows the domain “goverment[.]or.id”. While this domain is currently inactive, it is still registered. By using archive.org’s “WayBack Machine” we found a forum with dozens of posts for hacking advice and tutorials.
Fig 21: Inactive domain
Fig 22: Welcome message: Indonesian Anonymous
Fig 23: Connection to plaNETWORK
Fig 24: Hacking tutorials posted on the forum
So, does plaNETWORK only post hacking “tutorials”, or do they actually practice defacements themselves?
As we had already seen Conficker’s vast defacing activity, we proceeded to check another nickname appearing in the anniversary movie – Calvin.
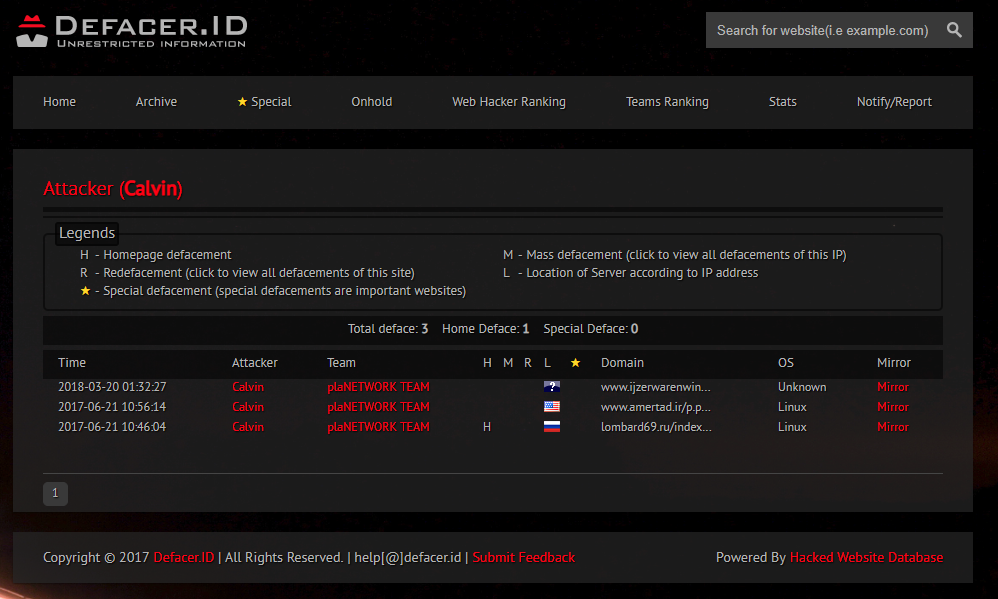
Having found Calvin’s defacer[.]id page, we saw that he mentions he is also part of the plaNETWORK team and brags about defacing various domains:
Fig 25: Calvin from the plaNETWORK team’s defacement page on defacer[.]id
Calvin also references additional members of the plaNETWORK team on his defacement activities. In fact, in each attack Calvin mentions specific team members that participated and helped him, and whose names along with their identity were revealed in the anniversary movie: eNda, Conficker, bandila and others.
Fig 26: Specific credits for each defacement
Fig 27: Specific credits for each defacement
Conclusion:
It seems that we came across a group that started out as an IT consultancy team, offering legitimate services to those in need. But soon the group began to operate on the dark side with their members enjoying the dubious credit they bring to the brand of plaNETWORK.
It is important to note that no defacement is considered legitimate, as long as the website owners have not demanded it before. Therefore, we should not be deceived by the ostensibly educational messages that the members of the group plant on the hacked websites.