

Check Point threat Intelligence sensors have picked up a stealth campaign that traditional anti-virus solutions are having a hard time detecting.
On July 17th SandBlast Zero-Day Protection started showing a massive email campaign which was not caught by traditional AV solutions. Even today, on the fourth day of this campaign, when Check Point has already blocked 5,000 unique samples of the campaign, there are still only a handful of samples on VirusTotal, half of which are not detected by any AV scan engine and the others with just a handful of detections.
The campaign is related to the “BlankSlate” spam campaign which sends emails with blank body and in this case blank subject, while the malicious payload is attached in a zipped file, named in the following format – EMAIL_NNNNNN_AAAAAA.zip.

The attachment contains a download and execute JavaScript file which is heavily obfuscated, and includes a mass amount of text ripped off of Wikipedia articles about different countries and cities.
SandBlast unzips the attachments and avoids the obfuscation by emulating the JavaScript, and identifies the communication to the malicious commands & control servers.
The C&C domains for this campaign are quickly changing to avoid blacklisting; all domains were recently registered and have the following pattern:
hxxp://sitename.tld/(support|admin).php?f=1.doc
They also have a low detection rate on Virustotal of about 5 out of 65 reputation services.
We can see the C&C utilizes a traffic redirection script for this and blocks several countries and ISPs from accessing the site.
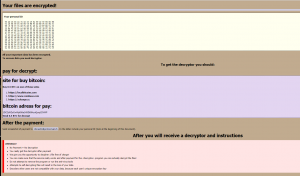
On chosen targets, chosen by their geolocation (for instance, USA), the C&C will return a BTC ransomware payload. The ransomware asks to transfer 0.5 Bitcoins to the following address – 1DCZzWZuCwWptG6e1H5D65HyuQyxp2SVWP and to send a screenshot of the transaction to the following Chinese email – [email protected].
Recommendations:
- Do not open attachments unless you are certain they arrived from a known person in a known context
- Use advanced malware prevention solutions.
- Check Point SandBlast customers are protected against this threat





