THE TAKEAWAY
Check Point’s latest Global Threat Impact Index revealed that 28% of organizations globally were affected by the Roughted malvertising campaign during June.
IN CONTEXT
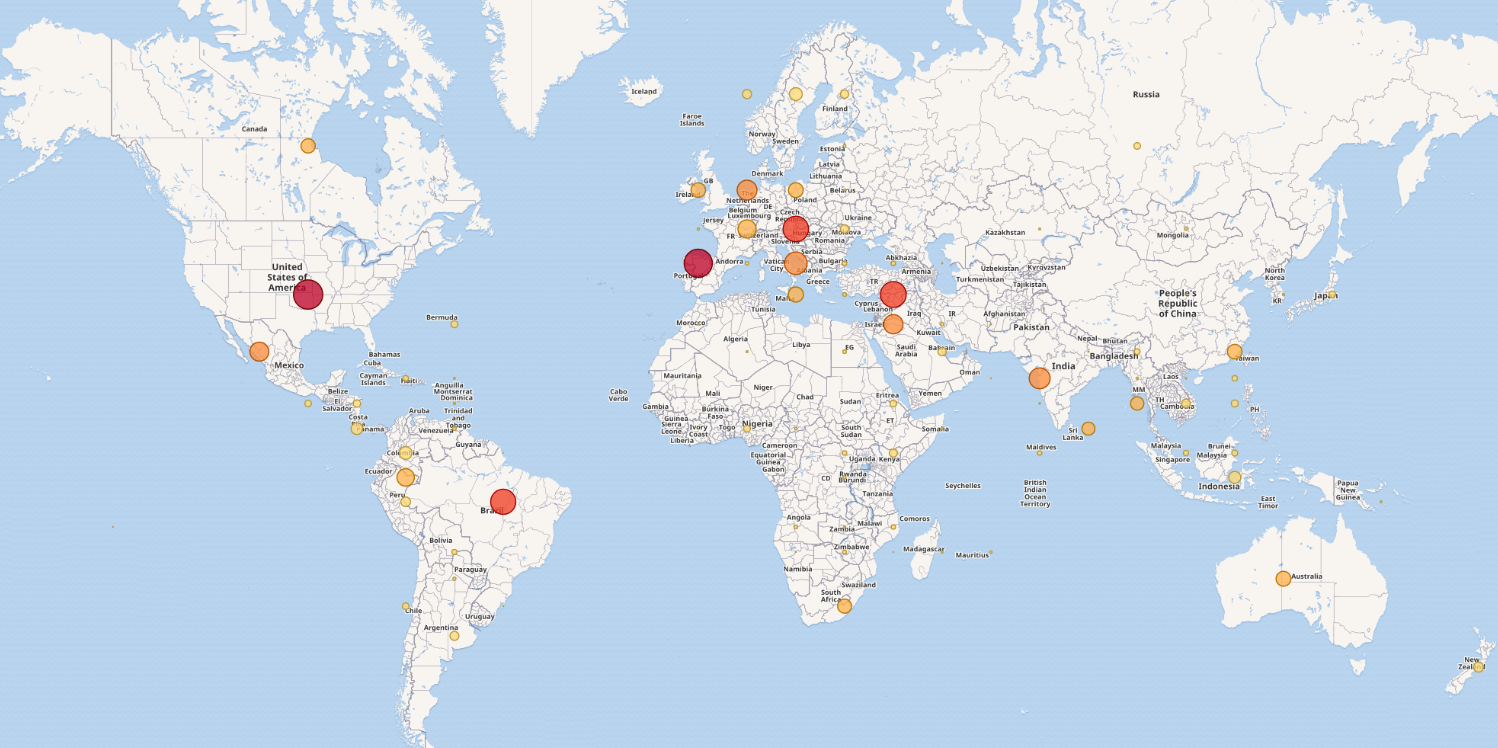
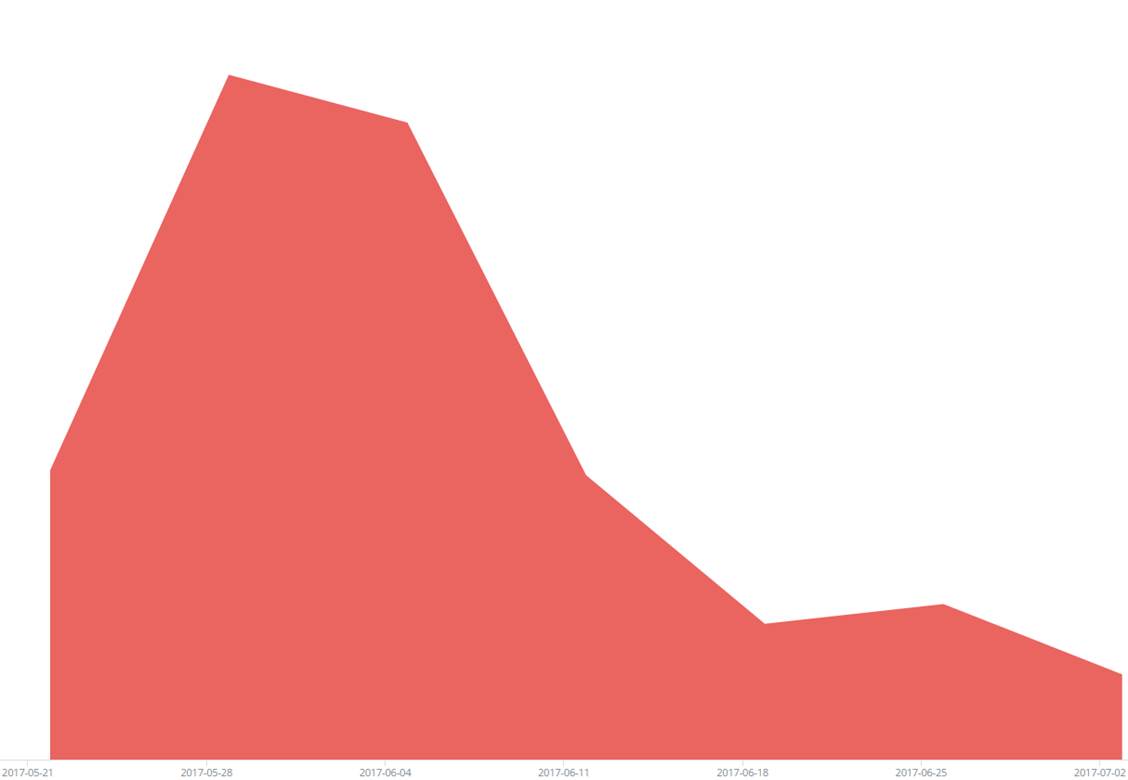
A large-scale malvertising campaign, RoughTed is used to deliver links to malicious websites and payloads such as scams, adware, exploit kits and ransomware. It began to spike in late May before continuing to peak–impacting organizations in 150 different countries. The top affected companies were in the education, communications and retails & wholesale sector. The malvertiding related infection rates spiked in recent months as attackers only have to compromise one online ad provider to reach a wide range of victims with little effort as there is no need to maintain a heavy distribution infrastructure for the malware.
ROUGHTED MAP
ROUGHTED CAMPAIGN TRAFFIC OVER TIME
Second-placed Fireball, which impacted 20% of organizations in May, declined sharply affecting only 5% of businesses in June, while the Slammer worm was the third most common variant, impacting 4% of organizations. The most common malware highlight the wide range of attack vectors and targets cyber-criminals are utilizing, impacting all stages of the infection chain. In contrast to RoughTed, Fireball takes over target browsers and turns them into zombies, which it can then use for a wide range of actions including dropping additional malware, or stealing valuable credentials, while Slammer is a memory resistant worm that can cause denial of service attacks.
This wide variety of attack vectors being utilized was reflected throughout the top ten common malware, which included the Cryptowall (4th) and Jaff (6th) ransomware, HackerDefender, a user mode root kit used to hide files, and Zeus (9th) a banking Trojan.
TOP 10 ‘MOST WANTED’ MALWARE
*The arrows relate to the change in rank compared to the previous month.
- ↑ RoughTed – Large-scale malvertising used to deliver various malicious websites and payloads such as scams, adware, exploit kits and ransomware. It can be used to attack any type of platform and operating system, and utilizes ad-blocker bypassing and fingerprinting in order to make sure it delivers the most relevant attack.
- ↓ Fireball– Browser-hijacker that can be turned into a full-functioning malware downloader. It is capable of executing any code on the victim machines, resulting in a wide range of actions from stealing credentials to dropping additional malware.
- ↑ Slammer – Memory resident worm targeted to attack Microsoft SQL 2000. By propagating rapidly, the worm can cause a denial of service condition on affected targets.
- ↑ Cryptowall – Ransomware that started as a Cryptolocker doppelgänger, but eventually surpassed it. After the takedown of Cryptolocker, Cryptowall became one of the most prominent ransomwares to date. Cryptowall is known for its use of AES encryption and for conducting its C&C communications over the Tor anonymous network. It is widely distributed via exploit kits, malvertising and phishing campaigns.
- ↔ HackerDefender – User-mode Rootkit for Windows, can be used to hide files, processes and registry keys, and also implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means.
- ↑ Jaff – Ransomware which began being distributed by the Necrus botnet in May 2017.
- ↓ Conficker – Worm that allows remote operations and malware download. The infected machine is controlled by a botnet, which contacts its Command & Control server to receive instructions.
- ↑ Nivdort – Multipurpose bot, also known as Bayrob, that is used to collect passwords, modify system settings and download additional malware. It is usually spread via spam emails with the recipient address encoded in the binary, thus making each file unique.
- ↑ Zeus – Banking Trojan that uses man-in-the-browser keystroke logging and form grabbing in order to steal banking information.
- ↓ Rig ek – Exploit Kit first introduced in 2014. Rig delivers Exploits for Flash, Java, Silverlight and Internet Explorer. The infection chain starts with a redirection to a landing page that contains JavaScript that checks for vulnerable plug-ins and delivers the exploit
In mobile malware, Hummingbad was the most common form of malware and was closely followed by Hiddad and Lotoor:
TOP 3 ‘MOST WANTED’ MOBILE MALWARE
- Hummingbad – Android malware that establishes a persistent rootkit on the device, installs fraudulent applications, and with slight modifications could enable additional malicious activity such as installing a key-logger, stealing credentials and bypassing encrypted email containers used by enterprises.
- Hiddad – Android malware which repackages legitimate apps and then released them to a third-party store. Its main function is displaying ads, however it is also able to gain access to key security details built into the OS, allowing an attacker to obtain sensitive user data.
- Lotoor – Hack tool that exploits vulnerabilities on Android operating system in order to gain root privileges on compromised mobile devices.
Throughout May and June organizations were heavily focused on ensuring that they are protected against ransomware, in response to the high profile WannaCry and Petya attacks. However the wide variety of attack vectors being utilized in this month’s index serves as a reminder to organizations that they need to ensure their security infrastructures robustly protect them against all tactics and methods used by cyber-criminals. As such, organizations in every industry sector need a multi-layered approach to their cybersecurity. Our SandBlast™ Zero-Day Protection and Mobile Threat Prevention, for example, protect against the widest range of continually evolving attack types, and also protect against zero-day malware variants.
Check Point’s Global Threat Impact Index and its ThreatCloud Map is powered by Check Point’s ThreatCloud intelligence, the largest collaborative network to fight cybercrime which delivers threat data and attack trends from a global network of threat sensors. The ThreatCloud database holds over 250 million addresses analyzed for bot discovery, more than 11 million malware signatures and over 5.5 million infected websites, and identifies millions of malware types daily.
Check Point’s Threat Prevention Resources are available at: http://www.checkpoint.com/threat-prevention-resources/index.html
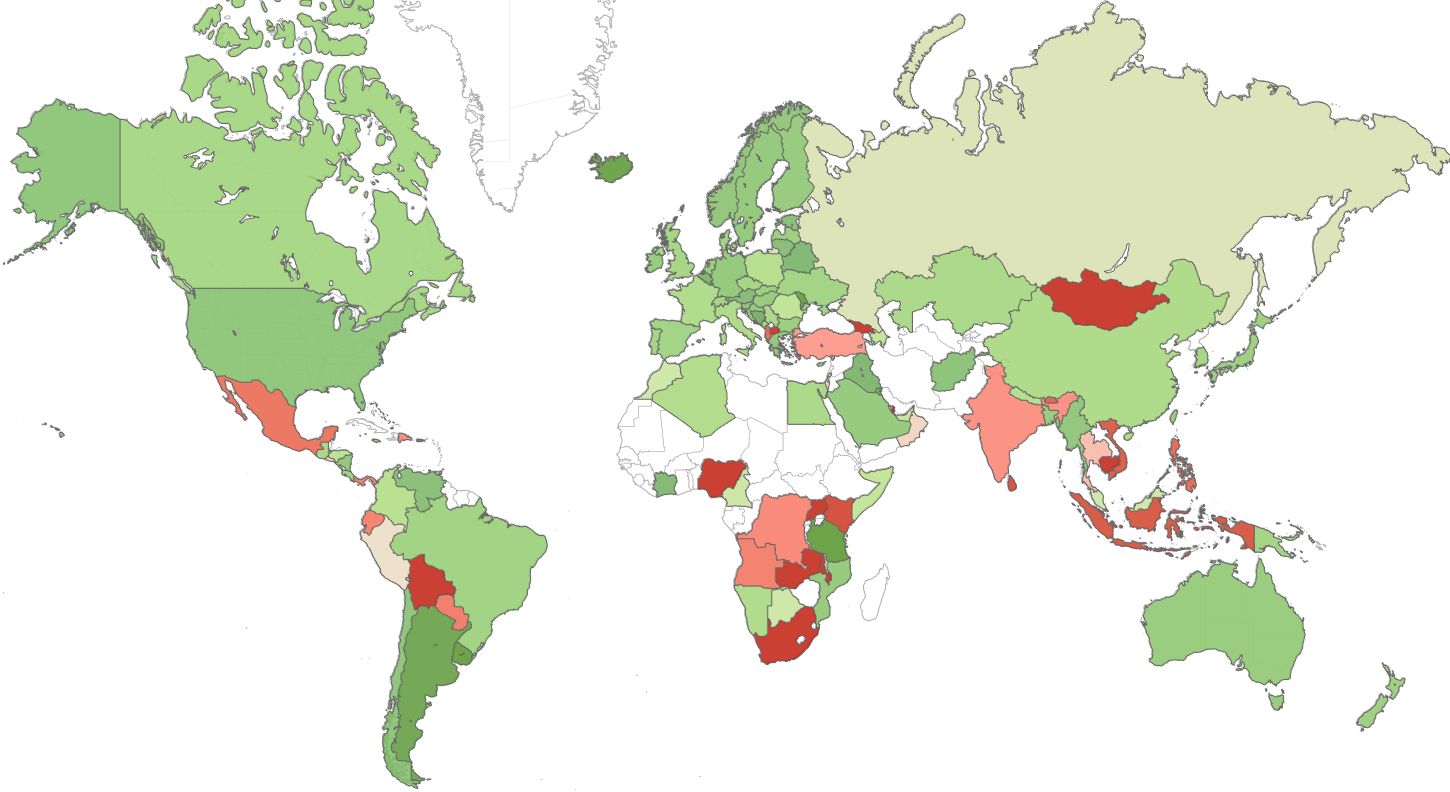
Threat Index per country
The map below displays the risk index globally (green – low risk, red- high risk risker, white – insufficient data), demonstrating the main risk areas around the world.