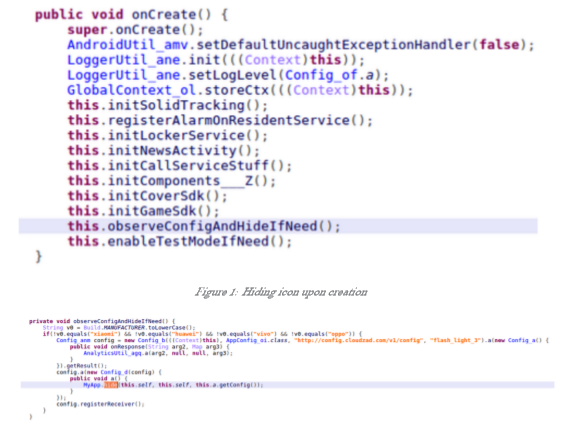
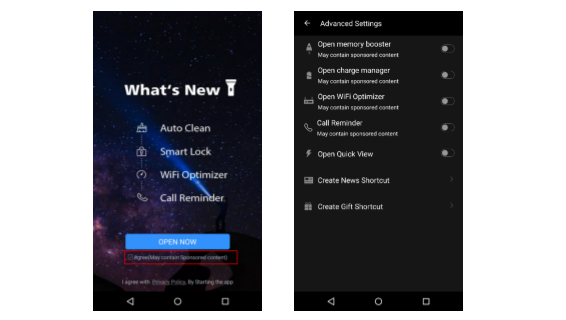
Check Point researchers have detected a new type of adware roaming Google Play, the official app store of Google. The suspicious scripts override the user’s decision to disable ads showing outside of a legitimate context, and then, in many of the apps, hides its icon to hinder efforts to remove it. This is a purely malicious activity, as it has no other possible purpose other than eluding the user.
Dubbed ‘LightsOut’, the malware hid itself in 22 different flashlight and utility apps, and reached a spread of between 1.5 million and 7.5 million downloads. Its purpose? To generate illegal ad revenue for its perpetrators at the expense of unsuspecting users.
The deception was far reaching in its disruption to the user. As some users noted, the apps forced them to press on the ads to answer calls and perform other activities on their device. Indeed, another user reported that the malicious ad activity continued even after he purchased the ad-free version of the app, taking the abuse to a whole new level.
Check Point notified Google about all these malicious apps, who soon removed them from the Google Play store.
Video demo of how the malware works.
How It Works
LightsOut embeds the malicious Solid SDK inside seemingly legitimate flashlight and utility apps. This has two malicious capabilities, which are both embedded in most samples found, and are triggered by the Command and Control server. The first is hiding its icon when the app is launched for the first time, making it much harder for a user to remove. This is a purely malicious activity, as it has no other possible purpose other than eluding the user.
The malicious app then offers the user a checkbox, as well as a control panel, in which they can enable or disable additional services, including the displaying of ads. The events that will trigger ads are any Wi-Fi connection, the ending of a call, a plugged in charger or the screen being locked.
Should the user choose to disable any of these functions however, ‘LightsOut’ can override that choice and continue to display ads out of context. Furthermore, since the ads are not directly connected to ‘LightsOut’s activity, the user is unlikely to understand what caused them. And, even if they do realize the app is to blame, they won’t be able to find the app’s icon and remove it from their device.
An example of LightsOut malicious ad activity is displayed in the diagram below. One of the ad triggers (in this case, the end of a phone call), occurs and the user’s configurations are then checked. If the user disabled the ads, but the command and control server directed the app to display an ad anyway, it will display the intrusive ad.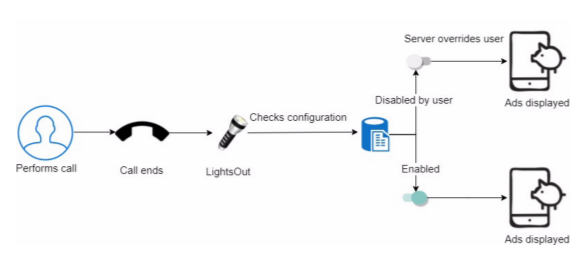
What Can Be Learned?
Despite the vast investment Google has recently made in the security of their App Store, ‘LightsOut’ reminds us once again that users need to be wary of downloading from App Stores and are advised to have protection while using them. Many users are still unaware of the dangers lurking for them, and continue to install fishy apps such as flashlights.
For a less technical understanding of this discovery, please see the Check Point Blog.
Appendix 1: Solid SDK malware
C&C server: http[:]//cloudzad.com/
Package names on Google Play:
| Package Name | Downloads (Min) | Downloads (Max) |
| com.smart.swipe.whitedot | 50,000 | 100,000 |
| com.wifi.network.realtime | 10,000 | 50,000 |
| pro.filetrans.app | 5,000 | 10,000 |
| com.network.guard.tool | 1,000 | 5,000 |
| com.brightest.ledflashlight | 1,000 | 5,000 |
| com.arc.voice.recorder.pro | 1,000 | 5,000 |
| pro.freewifi.password | 10,000 | 50,000 |
| com.call.recorder.pro | 100,000 | 500,000 |
| com.solidunion.callrecorder | 1,000,000 | 5,000,000 |
| com.realtime.app.cleaner | 10,000 | 50,000 |
| com.nfl.flashlight | 5,000 | 10,000 |
| hd.background.wallpaper.theme | 100,000 | 500,000 |
| com.ledflashlight.cool | 10,000 | 50,000 |
| com.master.wifikey.booster | 100,000 | 500,000 |
| com.wifimaster.network.speedtest | 50,000 | 100,000 |
| com.freewifi.connect.booster | 100,000 | 500,000 |
| com.brightest.ledflashlight.almighty | 5,000 | 10,000 |
| com.brightest.ledflashlight.best | 10,000 | 50,000 |
| rec.call.recording.manager | 1,000 | 5,000 |
| com.smart.freewifi.booster | 1,000 | 5,000 |
| com.brightest.ledflashlight.pro | 10,000 | 50,000 |
| com.dr.clean.lite | 5,000 | 10,000 |
| Total | 1,585,000 | 7,565,000 |
Package names outside Google Play:
| com.free.wifi.update |
| com.master.clean |
| com.fancy.locker |
SHA-256 Hashes:
f5b98f91c4ccb6f9530434adce285e25e503a7afb6ea97a03bea57c319cd2fbc 52209fa52052b8086ae5213d0a51c053ca07a6f36a131f2627be55db17f39ae7