After a drastic decline in the volume of spam coming from the Necurs spambot observed by Check Point Telemetry in the past month, the infamous botnet is back once again and is spreading QuantLoader. Necurs, considered to be the world’s largest botnet, was used to distribute several malware families in the past, such as the Locky and Jaff ransomware.
Just before the weekend, Check Point Threat Intelligence sensors spotted a new wave of Necurs spam. The e-mails pretend to be purchase orders or document copies, to lure the victims to open their attachments.
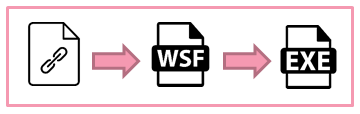
The emails have an attached archive containing a file with a URL. The URL files communicate with hosts in order to download an additional WSF file containing obfuscated JavaScript. This script is used to retrieve a QuantLoader payload, which, in turn, may download additional executables.
After a relatively quiet month, we have seen a peak of around 100,000 emails belonging to the aforementioned campaign in just one day (on March 30th). We have also observed a smaller amount of e-mails (5000) that were sent on March 27th. The sender’s email address on all these messages follows the same pattern, and starts with ‘netadmin’. The low volumes seen at the earlier date indicate that that may have been an initial test before the main wave emerged.
Figure 1: Number of emails sent by Necurs.