Cryptocurrency values may be tumbling but cyber criminals are still hedging their bets on its long term returns.
Check Point researchers have discovered a new malvertising campaign leading to the Rig Exploit Kit. The first sighting of this particular campaign was made in mid-January 2018 and the current payload served by this campaign is XMRig Monero Miner.
This campaign, dubbed “Slots” due to the gate’s domain theme, differs from other malvertising campaigns due to the use of HTTPS on the traffic that connects Slots’ infrastructure and the Rig Exploit Kit.
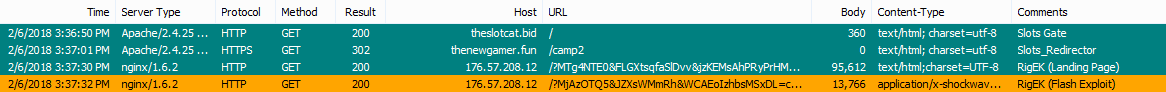
Figure 1: EKFiddle capture of the Slots campaign
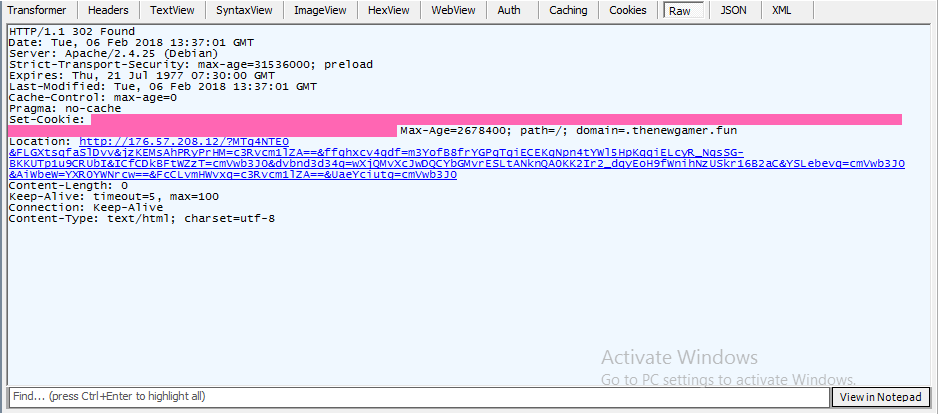
Figure 2: Slots’ gate response.
Figure 3: Slots’ redirector’s response.
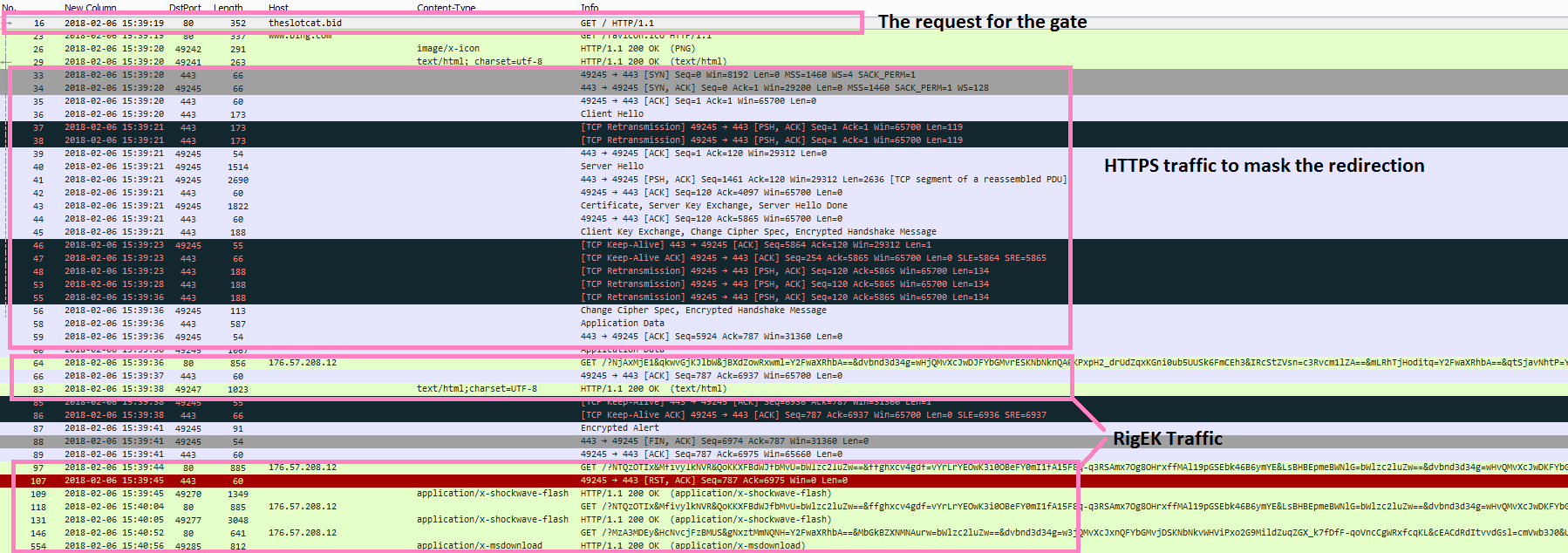
Figure 4: Pcap traffic of the infection chain.
As seen in the above figures, the victim requests the gate page of Slots (via malvertising) that will change the protocol to HTTPS in order to mask the connection between Slots’ infrastructure and Rig’s.
The redirector, with which the victim is communicating via a secure and encrypted connection, will then set a cookie to prevent any future attacks on the victim and will redirect the victim to the Rig Exploit Kit.
IOC’s:
- theonlineslots.bid – Slots’ Gate
- slotcat.bid – Slots’ Gate
- online.bid – Slots’ Gate
- onlineslot.bid – Slots’ Gate
- thenewgamer.fun – Slots’ Redirector
- 176.57.208.12 – Rig EK
- 5ac169f5fc8ac194947a5937b9612d8d – Payload’s MD5
- 07f6d25560ac4b75b9c957f92c9399aedfc28d3c – Payload’s SHA1
- 8f1dc187cdaed434cb05bc1e8a0f69d8d2e54fef – Unpacked XMRig SHA1