Introduction
Over the last few years, the adoption of Office 365 in the corporate sector has significantly increased. Its popularity has attracted the attention of cybercriminals who launch phishing campaigns specifically to attack the platform. As 90% of cyber-attacks start with a phishing campaign, Office 365 is an attractive target for threat actors who work to evade the continuously introduced security solutions.
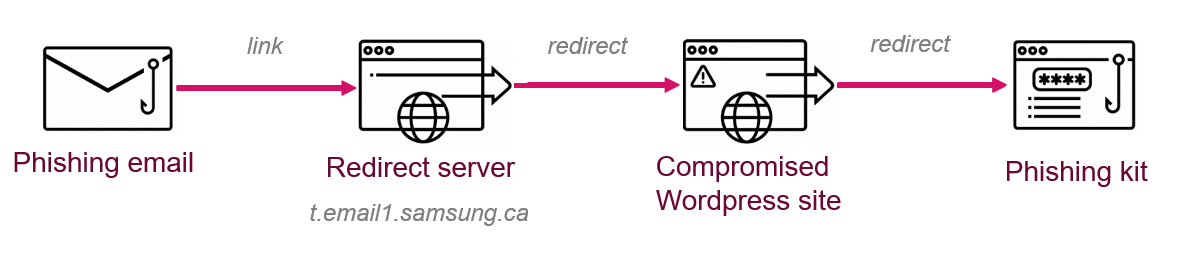
Recently, a seemingly unsophisticated Office 365 phishing campaign caught our attention. The attackers abused an Adobe Campaign redirection mechanism, using a Samsung domain to redirect victims to an O365 themed phishing website. The hackers took advantage of the fact that access to a reputable domain, such as Samsung’s, would not be blocked by security software.
To expand their campaign, the attackers also compromised several websites to inject a script that imitates the same mechanism offered by the Adobe redirection service. Further investigation revealed that the actors behind the campaign implemented a few other interesting tricks to hide the phishing kit and avoid detection at each stage of the attack. This report will describe what we discovered about this Office 365 phishing campaign which used trusted services to allow a new attack.
Before we start
Neither Adobe nor Samsung were compromised in the sense of exploiting a vulnerability. Samsung’s Adobe Campaign server was left available for managing campaigns that were not necessarily part of the company’s marketing efforts.
A redirection mechanism redirects users to a destination specified in the URL they just clicked. This allows campaign managers, for example, to gauge and monitor ongoing advertisement efforts by logging every successful visit before redirecting the user to an ad page.
Attack Flow
In early April of 2020, we detected a phishing campaign that delivered “missed voice message” emails to its victims. Roughly 43% of these attacks targeted European companies while the rest were seen in Asia and the Middle East. The emails prompted users to click on a button that would allegedly take them to their Office 365 account. These emails use some very basic customization, such as a subject line with the target domain name and the username included in the body of the email. Despite the “Message from Trusted server” notification at the top, a vigilant user would have noticed some inaccuracies. Here is an example of one of the phishing emails:
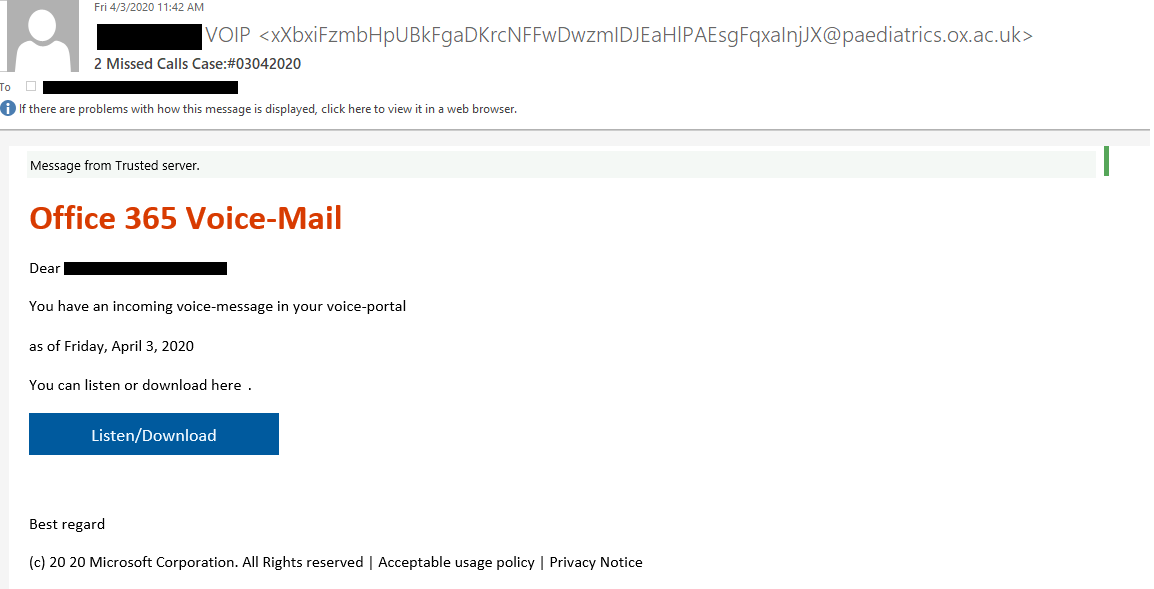
Office 365 Voice-Mail phishing email.
After the victims clicked the button, they were redirected to a phishing page masquerading as the Office 365 login page. Behind the scenes, this redirection consists of two stages: the first stage abused an existing redirection scheme on the legitimate domain (e.g. samsung[.]ca), and the second stage redirected the user to a compromised WordPress site.
Most of the emails came from multiple generated addresses belonging to legitimate subdomains from different departments in the University of Oxford (UK).
xXbxiFzmbHpUBkFgaDKrcNFFwDwzmIDJEaHlPAEsgFqxaInjJX@paediatrics.ox.ac.uk
Example of an auto-generated email address used in this campaign.
The email headers showed that the attackers found a way to abuse one of Oxford’s SMTP servers. The email originated from the NordVPN IP address 194.35.233.10 and then passed to the Oxford SMTP server and the Oxford Relay server as displayed below:
Authentication-Results: spf=pass (sender IP is 129.67.1.166) smtp.mailfrom=paediatrics.ox.ac.uk; xxx; dkim=none (message not signed) header.d=none; xxx; dmarc=bestguesspass action=none header.from=paediatrics.ox.ac.uk;compauth=pass reason=109 Received-SPF: Pass (protection.outlook.com: domain of paediatrics.ox.ac.uk designates 129.67.1.166 as permitted sender) receiver=protection.outlook.com; client-ip=129.67.1.166; helo=relay13.mail.ox.ac.uk; Received: from relay13.mail.ox.ac.uk (129.67.1.166) by MR2FRA01FT016.mail.protection.outlook.com (10.152.50.130) Received: from smtp5.mail.ox.ac.uk ([163.1.2.207]) by relay13.mail.ox.ac.uk with esmtps (TLS1.2:ECDHE_RSA_AES_256_GCM_SHA384:256) (Exim 4.89) (envelope-from <xXbxiFzmbHpUBkFgaDKrcNFFwDwzmIDJEaHlPAEsgFqxaInjJX@paediatrics.ox.ac.uk>) Received: from [194.35.233.10] (helo=[127.0.0.1]) by smtp5.mail.ox.ac.uk with esmtpsa (TLS1.2:ECDHE_RSA_AES_128_GCM_SHA256:128) (Exim 4.89) (envelope-from <xXbxiFzmbHpUBkFgaDKrcNFFwDwzmIDJEaHlPAEsgFqxaInjJX@paediatrics.ox.ac.uk>) From: "XXX VOIP" <xXbxiFzmbHpUBkFgaDKrcNFFwDwzmIDJEaHlPAEsgFqxaInjJX@paediatrics.ox.ac.uk>
Using legitimate Oxford SMTP servers allowed the attackers to pass the reputation check for the sender domain. In addition, there was no need to compromise actual email accounts to send phishing emails because they could generate as many email addresses as they wanted.
First Stage: Abusing Samsung’s Email Redirect
The technique of using Adobe Campaign open redirect was initially discovered in September 2019 on the domain belonging to Adobe itself. In the last few months, it’s been widely abused for phishing purposes. To evade detection, attackers abuse open and reputable Adobe Campaign servers to redirect potential victims to their own phishing websites. This means that the link embedded in the phishing email is part of a trusted domain – one that unknowingly redirects victims to the phishing website.
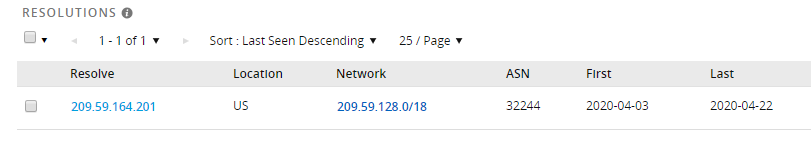
In this case, the Adobe Campaign server belongs to Samsung Canada.
http://t.email1.samsung[.]ca/r/?id=ff1b346f,303d531,303d53e&p1=8107023398&p2=8107023398&p3=DM15290&p4=https://compromised.site#[email protected]
How does this work?t.email1.samsung[.]ca is a subdomain for Samsung-Canada email campaigns, which hosts an Adobe Campaign server. The specially crafted URL contains a parameter called p4 which provides the server with a different redirect destination for each victim.
In our case, the attackers took the existing link from an old, but legitimate Samsung Cyber Monday themed email campaign dating back to 2018. By changing the p4 parameter, they repurposed it to redirect the victim to a domain they controlled instead of http://samsung.com/ca/:
http://t.email1.samsung.ca/r/?id=hf1b346f,303d531,303d53e&p1=8107023398&p2=8107023398&p3=DM15290&p4=http://www.samsung.com/ca/?mkm_rid=8107023398&mkm_mid=DM15290&cid=ca_email_newsletter_holidaycybermonday_20181126_fr-x-x-viewproducts-x-x
By using the specific Adobe Campaign link format and the legitimate domain, the attackers increased the chances for the email to bypass email security solutions based on reputation, blacklists and URL patterns.
However, this is not the first time an Adobe Campaign on Samsung infrastructure was used as a relay for phishing. According to urlscan, the t.info.samsungusa[.]com domain has been used for phishing-related redirects since February 2020.
Second stage: Redirect the User to a compromised WordPress site
The second layer of redirection is used to distance the final phishing page from the original email.
In this case, the attackers used several compromised WordPress sites which contain malicious redirect code.
Introducing another redirection layer enables the attackers to circumvent security solutions that investigate the links within the email. Thus the URL within the email points to a WordPress site instead of a suspicious-looking phishing page.
The redirect code, which is added to the compromised site’s homepage HTML code, also checks if the requested URL contains a # sign followed by an email address. If this condition is met, it redirects the victim to the final phishing kit.
 Redirection code on compromised WordPress sites.
Redirection code on compromised WordPress sites.
As a result, only users that have an email address in the link will be redirected, while users that enter the WordPress site directly do not notice any changes. This trick can prevent the site owners from detecting the abuse of their pages.
More redirects
A few days after the campaign launched, the attackers changed the URL inside the emails to the following one:
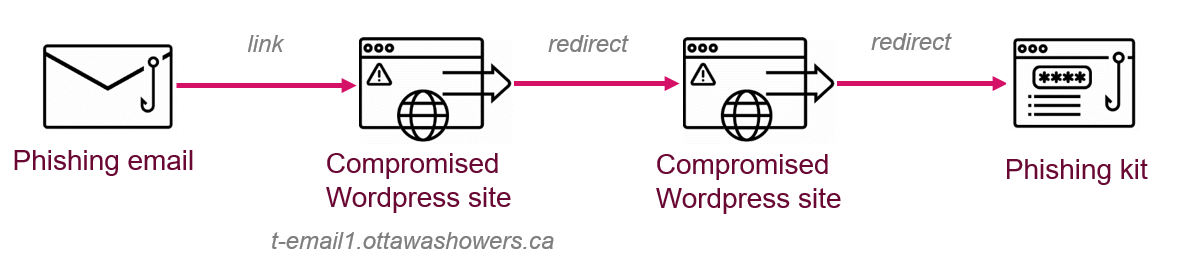
http://t-email1.ottawashowers[.]ca/r/?id=ff1b346f,303d531,303d53e&p1=8107023398&p2=8107023398&p3=DM15290&p4=https://compromised.site&[email protected]
This time, the compromised WordPress site wasottawashowers[.]ca. The attacker set up the subdomain t-email1 and a redirection script in the /r/ folder to mimic Adobe Campaign URLs. The parameters from the original Samsung campaign were left unchanged.
Indication that the domain t-email1.ottawashowers[.]ca was created for the purpose of the campaign.
Phishing attack scheme with compromised WordPress site for first redirect.
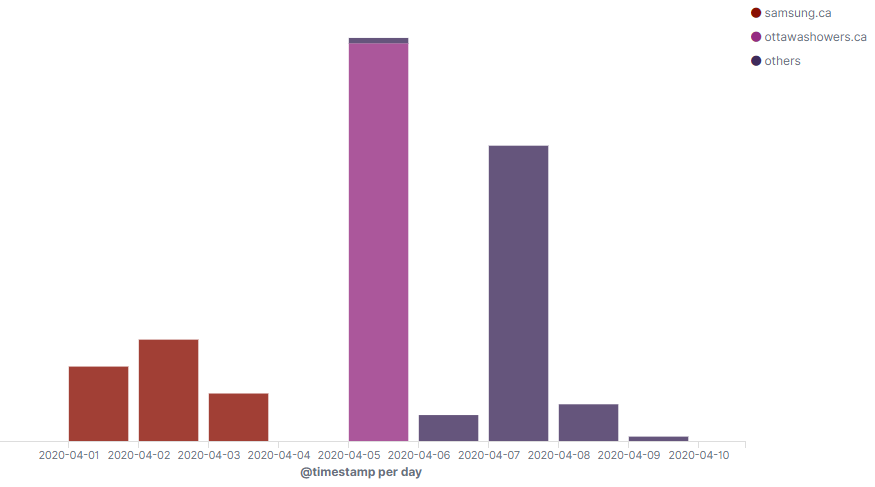
Later on in the campaign, the attackers changed the redirection method to be independent of a specific domain or Adobe Campaign server. They compromised and set up a similar redirect on multiple WordPress sites (to see the full list, go the IOCs section).
Timeline of campaign with different redirect servers.
In addition to changing the redirect domains, the threat actors started to change other (previously constant) parameters in the URL while preserving the basic Adobe URL structure. The parameters are used to check the integrity of the link, as well as to avoid detection by pattern-based engines (which will not automatically block all Adobe Campaign redirects). If a parameter is manually changed in this link, the server returns the message: AUTH FAILED.
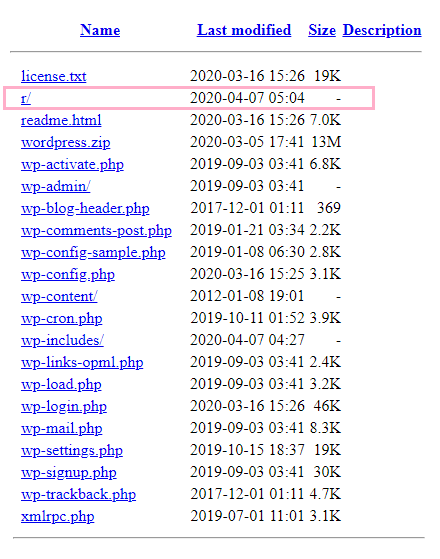
Opendir on one of compromised WordPress sites contains newly created redirect folder r/.
Phishing Kit
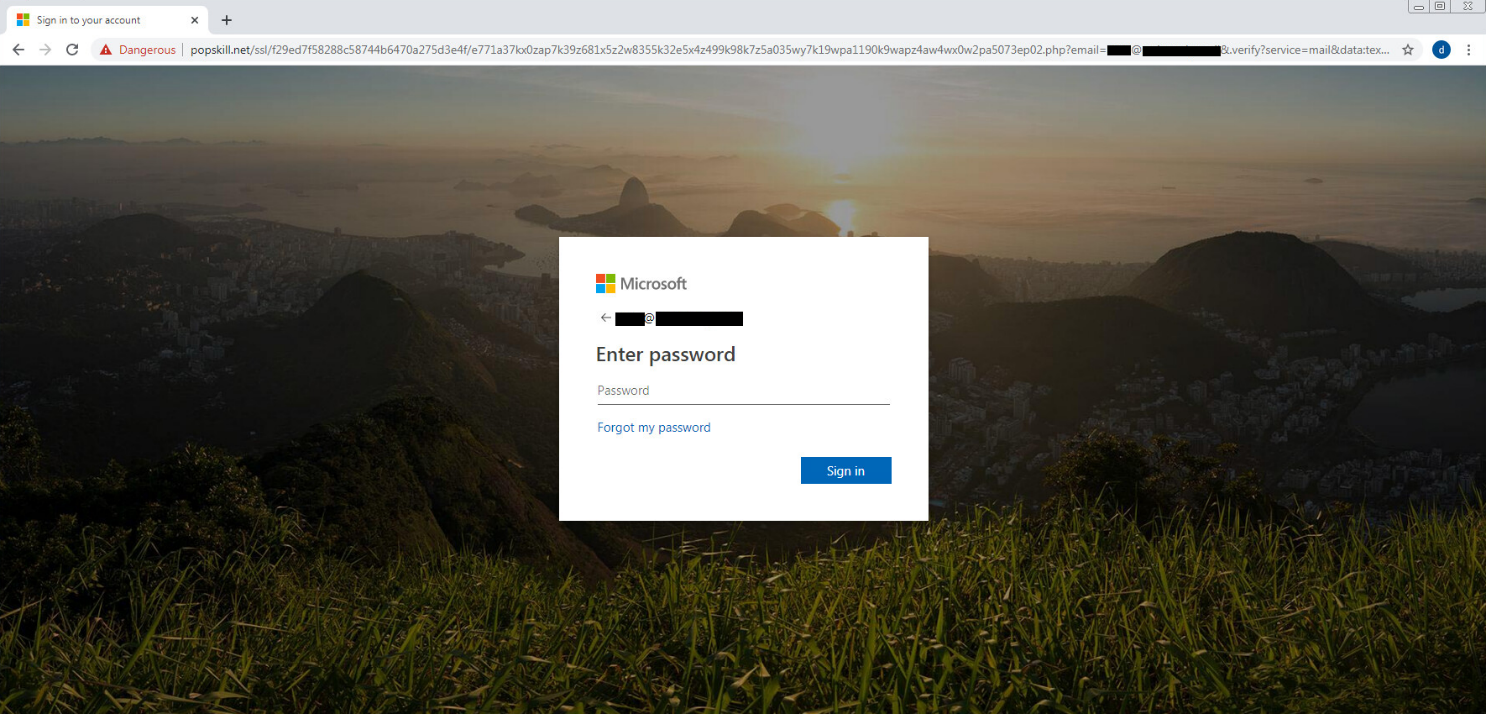
The final phishing kit was located on compromised WordPress sites. In some cases, the phishing kit was located on sites designed to look like a Microsoft login page. A separate virtual directory is created for each victim, so the final URL is different for every victim, even on the same server.
Microsoft phishing page.
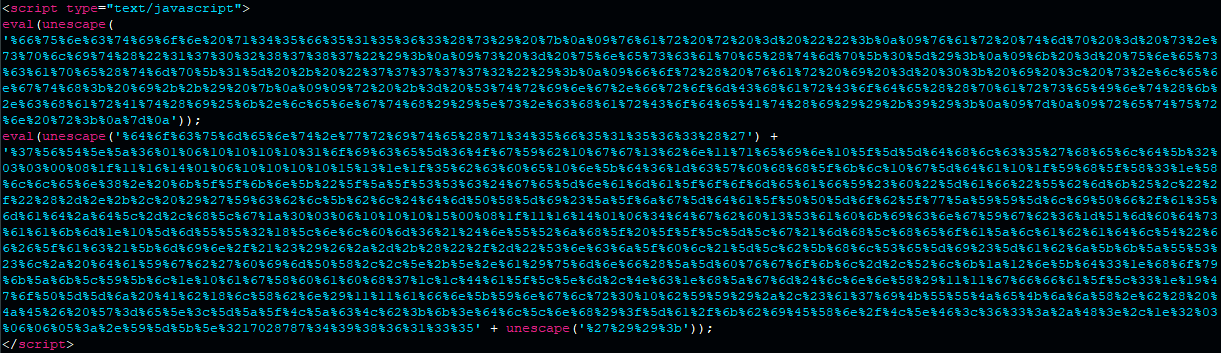
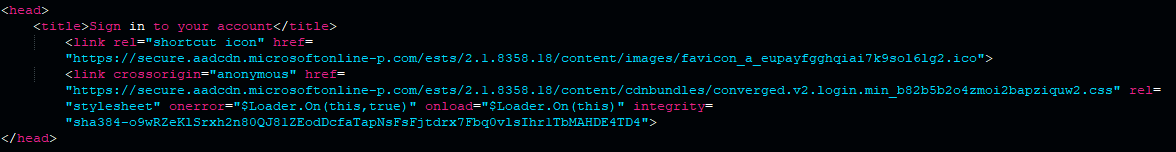
Most of the HTML code of the phishing pages is generated by JavaScript. The phishing page is divided into multiple sections, and each section is obfuscated with multi-byte XOR. For example, the <HEAD> section of the HTML page is a piece of JavaScript code containing 2 hex blobs that are unescaped and evaluated.
Part of an obfuscated phishing page.
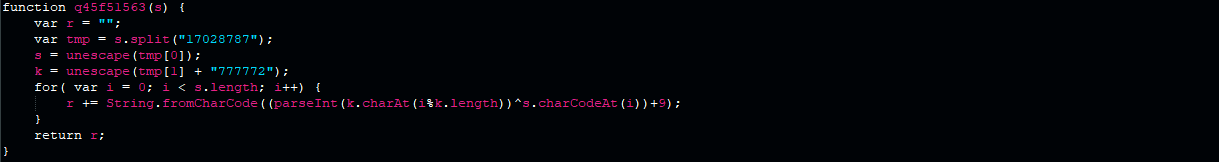
Decoding the first eval() statement reveals the decoding function.
First eval() statement after hex decoding.
This decoding function extracts encoded data (stored in tmp[0]) and XOR key (stored in tmp[1]) from the argument and performs XOR between the data and the key (loop in the code above).
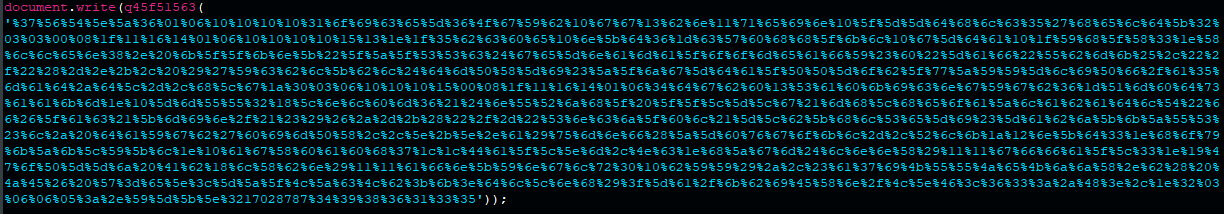
The second eval() statement calls this decoding function and writes the final HTML to the page with document.write():
Second eval() statement after hex decoding
Decoded <HEAD> section of HTML code
Generated HTML code means that all the pages look the same, but they have completely different source codes. Together with obfuscation, this method helps hide the code and its malicious intents from security software.
Conclusion
In this campaign, the attackers used multiple mechanisms to bypass security solutions at each stage.
- Utilizing an Oxford email server to send spam allows them to bypass the sender reputation filters and use generated email accounts instead of compromised actual accounts.
- Links within the email point to a high reputation domain owned by Samsung.
- A chain of redirects lead to a fully-obfuscated phishing page.
During the short campaign period, the attackers continuously developed and improved the redirection method to be independent of a specific domain and the Adobe Campaign servers.
Check Point recommends organizations to use cloud and mail security solutions. The fact these campaigns thrive proves native security solution are easy to bypass – such solutions are essential to remove threats getting into your email and protecting you cloud infrastructure.
Adobe took the relevant actions to prevent this type of attack through its server across all customers.
Appendix A: IOCs
Redirect servers:
t.email1.samsung[.]ca/r/
t-email1.ottawashowers[.]ca/r/
t-email1.instantytpresence[.]com/r/
flycloud.co[.]il/r/
cosmos.org[.]in/r/
iyak.org[.]tr/o/
ankit-gupta.co[.]in/r/
istern.co[.]il/r/
Compromised WP sites hosting Office 365 phishing kits or intermediate redirects:
junestore[.]club
popskill[.]net
yourhindinews[.]com
mrdigitalduniya[.]com
vrpublicnews[.]com
learndigitalseo[.]com
ghassociates.co[.]in
yournewstv[.]com
codewithjustin[.]com
pretrendy[.]com
dalelaganj[.]com
getfasternews[.]com
bloggingthenews[.]com
wpbasket.co[.]il
acornmagic[.]club
heaccountabilitycollective[.]com
legaltax[.]in
cbcvietnam[.]org
zeriio[.]com
ww.indoxxi[.]pl
espinozaweb[.]net
rumahcendekiaunj[.]com
beatanyinvestment[.]club
activedomain53[.]com
absoluteaesthetics.co[.]uk
tremplinedu[.]com
iamkongu[.]com
www.kwentongnoypi[.]com