

- Popular games such as “Temple Run” or “Subway Surfer” were found to be malicious
- Attackers can use the installed malware as a backdoor in order to gain full control on the victim’s machine
- Most of the victims are from Sweden, Bulgaria, Russia, Bermuda and Spain
Check Point Research (CPR) has spotted new malware that is actively being distributed through Microsoft’s official store. With over 5,000 machines already affected, the malware continually executes attacker commands,
such as controlling social media accounts on Facebook, Google and Sound Cloud. The malware can register new accounts, log in, comment on and “like” other posts.
Disclosure
CPR has reported to Microsoft all detected game publishers that are related to this campaign.
Research by: Moshe Marelus
Introduction:
CPR researchers detected a new malware, dubbed Electron Bot, which has infected over 5,000 active machines worldwide. CPR chose the name based on the last campaign’s C&C domain Electron-Bot[.]s3[.]eu-central-1[.]amazonaws.com.
Electron Bot is a modular SEO poisoning malware, which is used for social media promotion and click fraud. It is mainly distributed via the Microsoft store platform and dropped from dozens of infected applications, mostly games, which are constantly uploaded by the attackers.

Figure 1: VirusTotal score
The attackers’ activity began as an ad clicker campaign discovered at the end of 2018. The malware in question was hiding in the Microsoft store as an app called “Album by Google Photos” which claimed to be published by Google LLC.
The malware has constantly evolved through the years as attackers add new features and techniques to its arsenal.
The bot is built with Electron, a framework for building cross-platform desktop applications using Web scripts. The framework combines the Chromium rendering engine and the Node.js runtime, giving it the capabilities of a browser controlled by scripts like JavaScript.
To avoid detection, most of the scripts controlling the malware are loaded dynamically at run time from the attackers’ servers. This enables the attackers to modify the malware’s payload and change the bots’ behavior at any given time.
Electron bot’s main capabilities are:
-
- SEO poisoning, an attack method in which cybercriminals create malicious websites and use search engine optimization tactics to make them show up prominently in search results. This method is also used as a sell as a service to promote other websites ranking.
- Ad Clicker, a computer infection that runs in the background and constantly connects to remote websites to generate ‘clicks’ for advertisement, hence profiting financially by the amount of times an advertisement is clicked.
- Promote social media accounts, such as YouTube and SoundCloud to direct traffic to specific content and increase views and ad clicking to generate profits.
- Promote online products to generate profits with ad clicking or increase store rating for higher sales.
In addition, the malware’s payload contains functions that control social media accounts on Facebook, Google and Sound Cloud. It can register new accounts, log in, and comment on and “like” other posts.
The malware uses the Electron framework to imitate human browsing behavior and evade website protections.
Infection Chain:
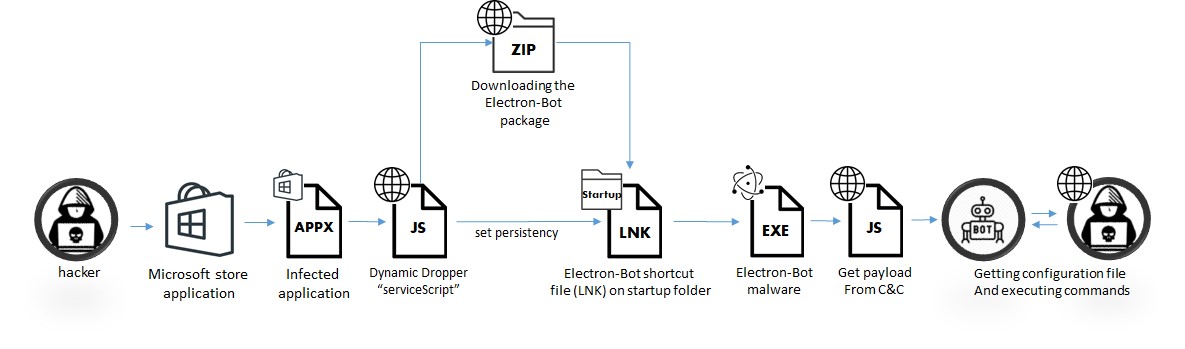
Figure 2: The infection chain
The infection chain is similar to most campaigns, starting with the installation of an infected application downloaded from the Microsoft Store.
When the user launches the game, a JavaScript dropper is loaded dynamically in the background from the attackers’ server. It then executes several actions including downloading and installing the malware and gaining persistency on the startup folder.
The malware is launched at the next system startup. It establishes a connection with the C&C and receives a dynamic JavaScript payload with a set of capability functions. Finally, the C&C sends the configuration file that contains commands to execute.
The Campaign:
The campaign begins when a user downloads one of the infected applications from the legitimate Microsoft store. To demonstrate, CPR used the game “Temple Endless Runner 2”, which was published on September 6, 2021 and has close to one hundred reviews.
Figure 3: Temple Endless Runner 2
When the game is downloaded, the application package file (APPX) is installed in the following directory: “C:\program files\windowsapps\16925JeuxjeuxjeuxGames.TempleRun2TakeTheIdolIfYouD_1.1.0.0_x64__66k318ytnjhfe \app”

Figure 4: The game folder
The game is built with Electron so most of the files in the folder are associated with the Electron framework. The executable file “app.exe” is the main part of the framework and is responsible for rendering all the scripts that are located in the resource folder.
The resource folder houses an ASAR file named “app.asar”, formatted as an archive and used to package source code for an Electron application. The source code will be unpacked only during runtime.
In this analysis, researchers used the “ASAR 7zip extension” to extract the source code from the “app.asar” file.

Figure 5: The source code folder
The source code folder contains a few JavaScript\html files. These files are surprisingly small and most of them contain less than 10 lines of code. However, the files are small because the main scripts are loaded dynamically at run time.
App initialization:
The game is loaded by launching the main script “main.js” which is responsible for basic window initialization and downloading a configuration file from hxxps://s3[.]eu-west-1[.]amazonaws[.]com/jeuxjeuxjeux.files/json-obj-el12/templeendlessrunner2.json.

Figure 6: templeendlessrunner2.json
The configuration file includes links to external scripts needed to run the game.
Here is a summary of the main keys:
- “src” – A link to the original game script on an online browser game site.
- “applicationScript” – A link to the JavaScript file that controls the game interface.
- “applicationCss” – A link to the CSS file for the game window.
- “serviceScript” – A link to a JavaScript file that drops and installs the next stage dropper.
After all scripts are launched, users can play the game.
The Dropper – “serviceScript”:
“serviceScript“ is a JavaScript dropper that contains functions used to download the malware’s package, install it and gain persistency. The script is rendered by the game app on the Electron framework.
AV detection:
The dropper begins by verifying that the infected machine does not have an antivirus product. It does so by checking against a list of hardcoded antivirus products and if an antivirus is detected, the script stops executing.

Figure 7: Anti-virus detection
Image dropping:
Next, the dropper downloads “112942.png” from hxxps://mediafire.com/ file/3v4vlgsi1ve53ya/112942.png. This file is a zip folder with a PNG extension. This mismatch between the file format and the file extension is probably because the malware uses a less suspicious file extension to avoid detection. The zipped content is extracted to the following directory: “C:\users\<username>\appdata\local\packages\microsoft.windows.securityupdate_cw5n1h2txyewy”

Figure 8: The bot folder
The dropped folder structure is similar to the game package first downloaded from the Microsoft Store. It is also an Electron app and the source code is loaded dynamically from an external domain.
Image fix:
In the dropped resource folder, there is a file named “app” without a file extension. Like the infected app, the dropper renames the file to “app.asar” so it will be recognized by Electron as the packed source code file in ASAR format. This was likely initiated so the malware doesn’t run unless it is installed properly by the dropper.
Persistence:
Finally, the dropper creates a shortcut file (lnk) for the “Windows Security Update.exe” located in the dropped folder. It places it in the startup folder to gain persistence.
After it’s installed and gained persistence, the bot automatically starts at the next system startup.
The Bot – “Windows Security Update.exe”:
Bot payload:
Similar to the dropper, the actual malware payload is not stored on the infected computer. After the malware is launched, it loads a small JavaScript from: hxxp://11k[.]online/Ad/javascripts/windowsdef.js

Figure 9: windowsdef.js
“Windowsdef.js” downloads the “main.js”, the actual script that contains all the malware capabilities. This script is hosted on the C&C server under Electron Bot[.]s3[.]eu-central-1[.]amazonaws.com\js\main.js.
Bot Design:
The bot is designed to imitate the following user behavior:
- It opens a new hidden browser window by using the chromium engine in the electron framework
- It sets appropriate HTTP headers e.g. User-Agent and referrer
- It fully renders the requested HTML page
- It imitates human user behavior by moving the mouse, scrolling and keyboard typing

Figure 10: “Human” mouse moving function
Bot Behavior:
After getting its dynamic payload, the malware downloads a configuration file from 11k[.]online/textFileProm.json.

Figure 11: The configuration file
In each configuration file, certain commands have a defined ‘countries’ list. The specific commands can only be executed if the infected machine’s GEO location is present in the provided list.

Figure 12: Command types
- IDLE, POPUNDER, DIRECTLINK, FAST, MEDIUM and BANNER are different ways for the bot to surf web pages. For example, it dictates where to click and what HTTP headers to use
- Google SEO (Search Engine Optimization) – Promotes search results by clicking on a targeted search result. This makes the website more popular by improving its ranking on the result page.
- YouTube – Promotes YouTube channels by watching videos and adding view counts. In some cases, a Gmail account is provided so the bot has the ability to comment, like, and subscribe

Figure 13:The bot’s hardcoded YouTube comments
- PROM_UA – Promotes products that are sold on an online Ukraine store “shopsusa.prom.ua”.

Figure 14: MITRE ATT&CK used techniques
Attack source:
- All variants between 2019 – 2022 were uploaded to a public cloud storage “mediafire.com” from Bulgaria.

Figure 15: mediafire[.]com showing the upload came from Bulgaria
- The Sound Cloud account and the YouTube channel the bot promotes are under the name “Ivaylo Yordanov,” a popular Bulgarian wrestler\soccer player.
- Bulgaria is the most promoted country in the source code.

Figure 16: Bulgaria is the main promoted country
Conclusion and Safety Tips:
Although the bot currently does not engage in high risk activities on the infected machine, it is important to be aware of its capabilities.
This research analyzed a new malware called Electron Bot that has attacked more than 5,000 victims globally. Electron Bot infects machines when downloading certain apps from the official Microsoft store platform. The Electron framework provides Electron apps with access to all of the computer resources, including GPU computing. As the bot’s payload is loaded dynamically at every run time, the attackers can modify the code and change the bots behavior to high risk. For example, they can initialize another second stage and drop a new malware such as ransomware or a RAT. All of this can happen without the victim’s knowledge.
Given most people think that you can trust application store reviews, they do not hesitate to download an application from there. However, CPR researchers warn that there is incredible risk with that and all users should follow a few safety tips when downloading applications:
- Avoid downloading an application with small amount of reviews
- Look for applications with good, consistent and reliable reviews
- Pay attention to suspicious application naming which is not identical to the original name
Remediation:
In order to clean already infected machines, CPR advises users to follow these steps:
- Remove the application downloaded from Microsoft Store.
-
- Go to settings > apps.
- Find the app in the list and select uninstall.
- Remove the malware’s package folder.
- Go to C:\Users\<username>\AppData\Local\Packages.
- Look for one of the following folders and remove it.
- “Microsoft.Windows.SecurityUpdate_cw5n1h2txyewy”
- “Microsoft.Windows.Skype_cw5n1h2txyewy”
- Remove associated LNK file from Start Up folder.
- Go to C:\Users\<username>\AppData\Microsoft\Windows\Start Menu\Programs\Startup.
- Look for a file named Skype.lnk or WindowsSecurityUpdate.lnk and remove it.
Check Point protections:
XDR:
The Electron Bot campaign, was first detected by our XDR product. The detection was based on a combination of suspicious network activity of a periodic bot and endpoint malware behavior.
- win.electronbot.a
- win.electronbot.b
- win.electronbot.c
- wins.electronbot.d
IOC:
Executables:
f2a97841d58aa9050b2275302be6aa78
240e9adca3695da4ba177c0238141881
33145894a81fd3f6fde4f528630b1f7a
Zipped folders:
8720d6cefd71ef30c3fe66965fea841a
0a919ab3c63608e00290c9d4d4eb3a01
07ebca17e1083461fbbe3376fe5ec1ed
ec2c0a9be3ff2a922c02c9e1380eeabd
52c4990d30a8a7b560c57e775895ccad
Game publishers:
Lupy games
Crazy 4 games
Jeuxjeuxkeux games
Akashic games
Goo Games
Bizzon Case
C&C Domains:
11k[.]online
Electron-Bot[.]s3[.]eu-central-1[.]amazonaws.com
Malware hosting sites:
cdn[.]lupygames[.]com
crazy4games-flash[.]s3[.]eu-west-1[.]amazonaws[.]com
ytmp3[.]dog





