
Introduction
Until last year, hacktivism has primarily been associated with groups like Anonymous – decentralized and unstructured collectives made up of private individuals with a variety of agendas. Anonymous has launched multiple campaigns against a wide range of targets based on the preferences and wishes of its members. There was no real ideological affiliation or connection between the group’s members, and apparently no long-term agenda. Anyone, regardless of political affiliation, is welcome to join.
In the past year, things have changed. As one of the multiple fallouts of conflicts in Eastern Europe and the Middle East, some hacktivism groups stepped up their activities in form and focus to a new era; Hacktivism is no longer just about social groups with fluid agendas. The upgraded hacktivism is better organized, structured and more sophisticated. Though the change began in specific conflict-related geographical regions, it has now spread west and even further. Major corporations and governments in Europe and the US are being heavily targeted by this emerging type of hacktivism. In recent months, the US, Germany, Lithuania, Italy, Estonia, Norway, Finland, Poland and Japan suffered severe attacks from state-mobilized groups, which in some cases have had a significant impact. The recent attacks targeted not only the governments of these countries, but also major corporations like Lockheed Martin, a global defense contractor. Also, the latest large-scale attacks on the Albanian government were executed by a state-mobilized hacktivist group.
The major hacktivist groups that appeared in the last year share many characteristics of structured organizations: clear and consistent political ideology, a well-designed hierarchy for members and leadership, a formal recruitment process and even tools that the groups provide to their members. In addition, the groups and their members are aligned on the targets, and in a few cases, there is even organized cooperation between groups. In addition, the groups also have robust public relations operations to publicize and promote their successes, including on major media channels and websites.
All this allows the new hacktivism groups to be mobilized to governmental narratives and achieve strategic and broad-based goals with higher success levels – and much wider public impact – than ever before. Hacktivist groups no longer consist of a few random individuals who carry out small DDoS or defacement attacks on low-tier websites. These are coordinated organizations which launch organized large-scale DDOS and disruptive attacks against their targets, with far-reaching public relations. Therefore government agencies and organizations should consider themselves duly warned.
Old School Hacktivism
Examples of old-school hacktivist attacks include campaigns like Operation KKK against Ku Klux Klan supporters and members, the campaign against the United Nations in retaliation for not granting a seat to Taiwan, Operation AntiSec, whose goal was to steal and publish classified government documents, #Opwhales to support whale preservation, and more. In some cases, there were even contradictory campaigns executed by Anonymous within the same year, such as the #OpTrump and #OpHillaryClinton campaigns.
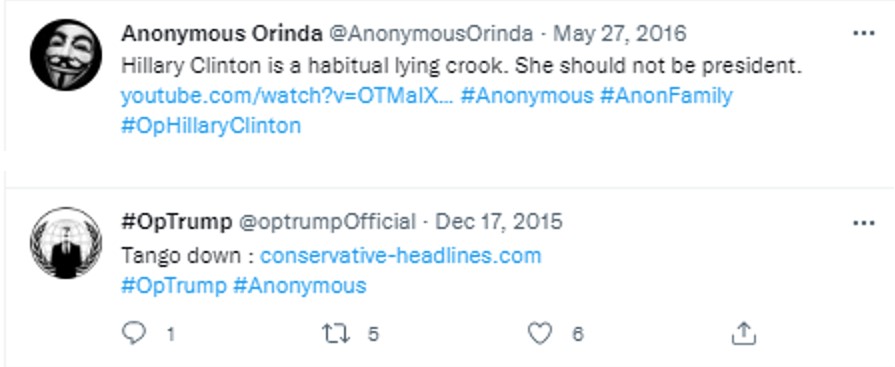
Figure 1 – Example of contradictory campaigns executed by Anonymous
Hacktivism Model 2022 – Mobilization to Government Agendas
The shift in hacktivism began quietly 2 years ago in the Middle East, with several hacktivist groups like Hackers of Savior, Black Shadow and Moses Staff that focused exclusively on attacking Israel. Most did not hide their affiliation with the Iranian regime’s anti-Israel narrative. In parallel, several other groups in the Middle East, the most prominent being Predatory Sparrow, focused solely on attacking pro-Iranian targets. Their only shared agenda is opposition to the Iranian regime.
The geo-political agenda that mobilized hacktivism is not limited to the Middle East but is also an essential part of the Russian-Ukrainian war. In early 2022, the Belarusian Cyber-Partisans group, formed in 2020 to oppose the Belarussian government, began launching destructive cyber-attacks to stymie Russia’s troops.
The IT Army of Ukraine was publicly mobilized by the Ukrainian government to attack Russia. The new hacktivism also saw groups that supported the Russian geopolitical narrative, with groups like Killnet, Xaknet, From Russia with Love (FRwL), NoName057(16), and more.
Although the new hacktivism started in specific and limited geographical areas, the Russian-mobilized groups soon turned their focus from being solely on Ukraine, but on anyone opposing the Russian agenda, i.e. Europe, the United States and even Asia. This included significant attacks on governments and major corporations in the US, Lithuania, Italy, Estonia, Norway, Finland, Poland, Japan, and more.
These groups have also clearly stated agendas supporting Russian information warfare and interests, as we can see in the manifest of Noname057(16).
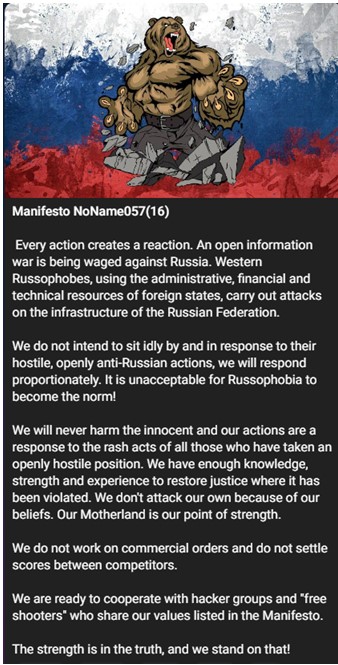
Figure 2 – Manifest of Noname057(16) group
This group has a clear pro-Russian agenda, and has been regularly targeting Ukraine, and expanding their focus. During the last few months, Noname057(16) targeted many countries in the European Union which publicly supported Ukraine, such as Poland, Lithuania, Latvia, Slovakia and Finland. NoName057(16) also notably attacked the website of the Finnish Parliament in August, after Finland expressed interest in joining NATO.
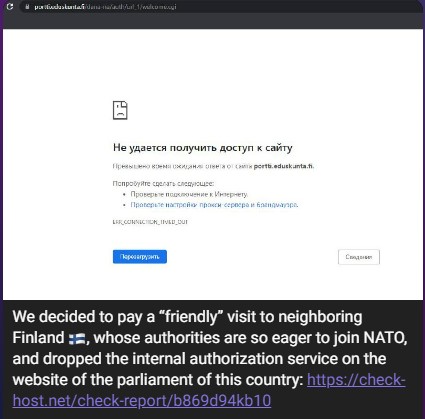
Figure 3 – Noname057(16) targeting of Finnish Parliament
From Russia with Love (FRwL) is another group that sticks to the same state-mobilized modus operandi but gets less public attention. The group focuses on publishing private information on its Telegram channel and claims to have committed several attacks on “Russia’s enemies.” They claim to have gained sensitive information on Estonia and Lithuania by accessing Telegram channels related to the Ukrainian Security Service. FRwL joined the wave of attacks on Lockheed Martin and its subcontractors who produce HIMARS, that are part of the American assistance delivered to Ukraine. FRwL also claimed to breach Gorilla Circuits, a USA Printed Circuit Board Manufacturer, who are one of Lockheed Martin’s suppliers.
On the other side of the conflict, there are also multiple mobilized hacktivist groups who side with Ukraine. Some, like the IT Army of Ukraine, are officially run by the Ukrainian government. The IT Army of Ukraine was established days after the Russian invasion began and coordinated skilled volunteers from all over the world to operate under Ukrainian directive. According to CSS Zurich, the IT Army consists of both multiple global volunteers that work to coordinate DDoS attacks against Russian targets, and an additional team that works on deeper levels, perhaps comprised of Ukrainian defense and intelligence experts that can carry out more complicated cyber operations against specific Russian targets.
One of the most dominant groups joining the IT Army of Ukraine is TeamOneFist, the Pro-Ukraine collective that in August targeted Khanty-Mansiysk City in Russia, damaging the natural gas power plant and also causing a blackout at its airport.
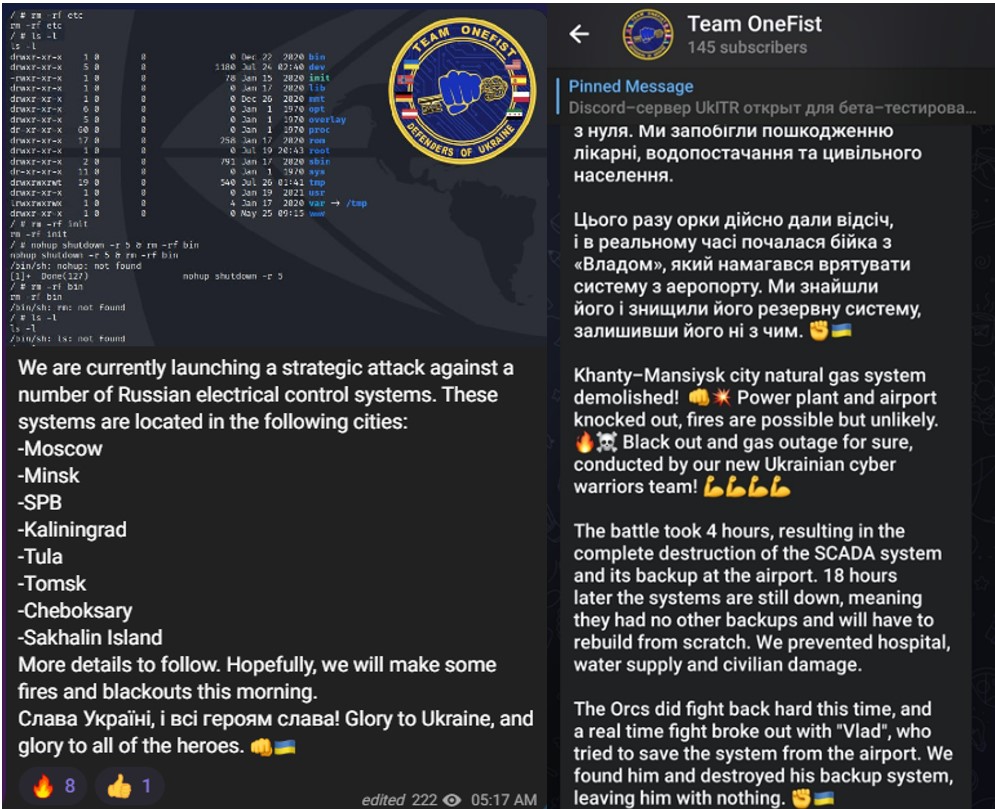
Figure 4 – Team OneFist claims on the attack against Khanty-Mansiysk city in Russia
Although the pro-Ukrainian-mobilized groups currently focus exclusively on Russia, they still established precedents for state-affiliated and mobilized hacktivism.
During the last few months, we also saw a clear proliferation of Iranian state-mobilized hacktivism targeting Europe and NATO. On July 15, 2022, Albania suffered a serious cyberattack which temporarily shut down numerous Albanian government digital services and websites. The group that took responsibility for this attack is a hacktivist group called Homeland Justice, which is affiliated with Iran’s Ministry of Intelligence and Security. In this case, Homeland Justice clearly serves the Iranian government’s agenda against Mujahedin-e-Khalq (MEK), an Iranian dissident group sheltered by the Albanian government.
Killnet Case Study – Starting East and Going West
One of the major actors in the hacktivist ecosystem is Killnet, which was publicly launched around the end of February 2022, at the start of the Russian–Ukrainian war. The group began their aggressive activity in March, with targets mostly in Ukraine. However, in April the group completely shifted its focus to support Russian geopolitical interests all over the world. Between late February and September, the group claimed to have executed more than 550 attacks. Only 45 of them were against Ukraine, less than 10% of the total number of attacks.
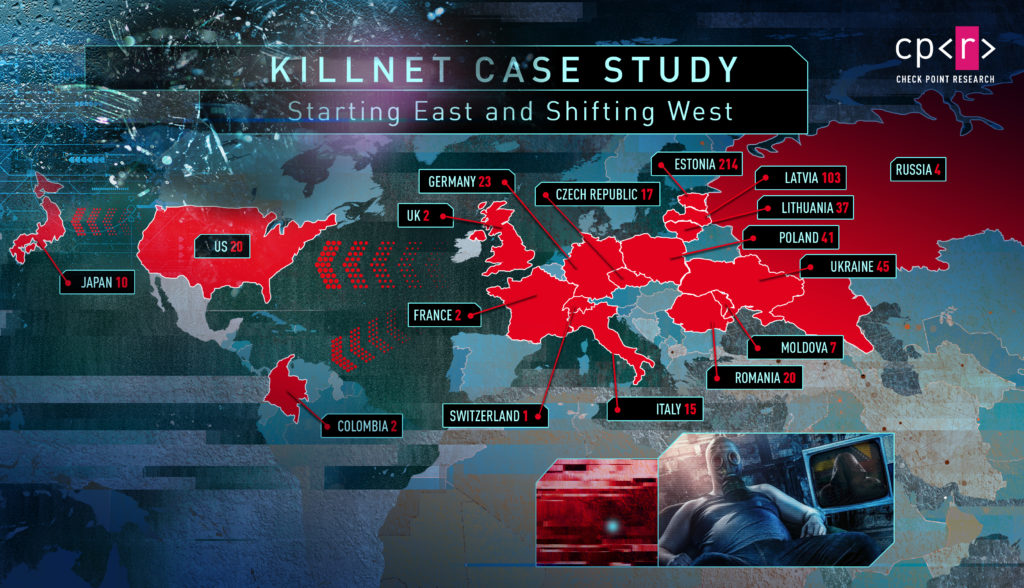
Figure 5 – Distribution of Killnet attacks by country
Many of those attacks were against high-profile targets like major government websites, large financial companies, airports, and more. While in some cases it is difficult to understand the real impact, in many cases the attacks were clearly successful. They caused downtime for major websites, many of which provide essential public services.
Here are several examples of the attacks executed by Killnet:
- In March, the group executed a DDoS attack on Bradley International Airport in Connecticut (US). The US authorities confirmed an attempted large-scale DDOS attack on the airport’s website.

Figure 6 – Announcement about the attack against Bradley International Airport
- In April, websites belonging to the Romanian Government, such as the Ministry of Defense, Border Police, National Railway Transport Company and a commercial bank, were rendered unreachable for several hours. These attacks were in response to a statement made by the Romanian leader of the Social Democratic Party Marcel Ciolacu, who offered to provide weapons to Ukraine.
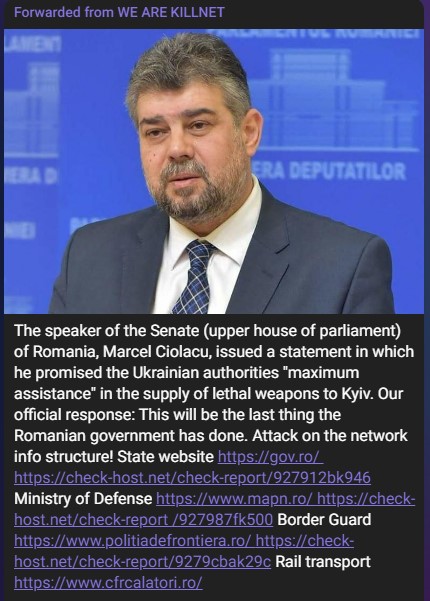
Figure 7 – Announcement about the attack against the Romanian government
- In May, major DDOS attacks were executed against two major EU countries:
- Several German targets were affected, including German government and politicians’ websites, among them Chancellor Olaf Scholz’s party-affiliated site, Germany’s Defense Ministry, the German Parliament, Federal Police and several state police authorities. All this was a response to the Scholz administration’s efforts to supply military equipment to Ukraine. The government authorized the transfer of 50 Gepard anti-aircraft installations and announced the delivery of seven self-propelled, rapid-fire artillery systems.
- Italy’s Parliament, military and National Health Institute were
- In June, two very significant waves of attacks were executed against Lithuania and Norway in response to severe geopolitical developments between those countries and Russia:
- Following the decision of Lithuania’s government to halt the transit of Russian goods to Kaliningrad, a wave of major attacks hit Lithuanian public services and the private sector. During the attack, Jonas Skardinskas, the Head of cybersecurity at the Lithuanian National Cyber Security Center (NCSC), warned that the disruptions might continue for several days with the transport, energy and financial sectors bearing the brunt of the attacks. At some point, the majority of Lithuanian websites were not accessible from IP addresses outside of the country, most likely as a preemptive measure to mitigate the attack.
- The same month, several large Norwegian organizations were taken offline. This attack was believed to be executed as a result of a dispute over transit through Norwegian territory to an Arctic coal-mining settlement controlled by Russia.
- In July, Killnet focused their efforts on Poland and caused several government websites to be unavailable. Most of the attacks were directed against government portals, tax authorities and police websites.
- August was quite a busy month for Killnet. It started with an attack on Latvia. After declaring Russia a “State sponsor of Terrorism”, the Latvian Parliament’s website suffered a major DDoS attack. Later in the month, Estonia faced its most extensive cyber-attacks since 2007, as a response to the removal of Soviet monuments. The effectiveness of those attacks was questionable, as it seems that Estonia was well prepared for such scenarios. During August, Killnet also started focusing on the United States. The giant American manufacturer Lockheed Martin was heavily targeted by Killnet as a response to providing military systems to the Ukrainian army. In parallel, Killnet also targeted the US Electronic Health Monitoring and Tracking System and the US Senate, which was debating sending additional aid to Ukraine.
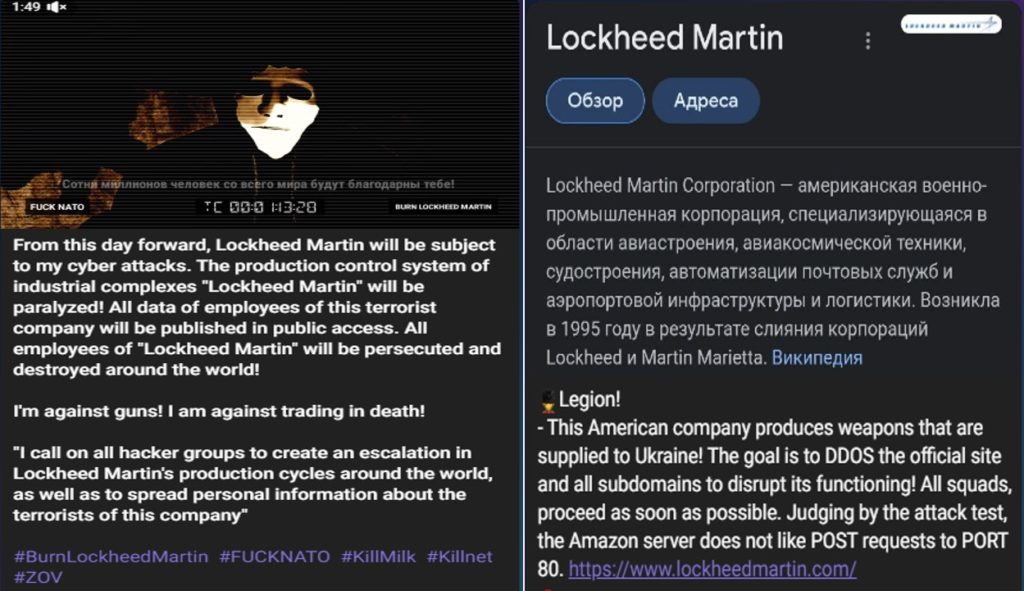
Figure 8 – Announcement about the attack against Lockheed Martin
- In September, the group targeted Asia for the first time and focused its efforts on Japan, due to Japan’s support for Ukraine. With the escalation of the Russian–Japanese conflict over the Kuril Islands, Killnet successfully attacked multiple top Japanese websites, including the e-government, the public transportation websites for Tokyo and Osaka, the JCB payment system, and Mixi, Japan’s second largest social media site.
Leadership, Recruitment & Tools
Organizational Structure
The major hacktivist groups that arose during the past year are characterized by their well-structured operations which allow them to not only achieve targeted attacks in waves but also attract more skilled individuals. These individuals are usually motivated by a clear state-affiliated ideology, and their goals are incorporated into a manifesto and/ or set of rules to follow. For example, Killnet has more than 89,000 subscribers on their Telegram channel and is organized in a military-like structure with a clear top-down hierarchy. Killnet consists of multiple specialized squads to perform attacks which answer to the main commandment. There are currently around a dozen sub-groups, the main one being Legion. All of these groups are led by an anonymous hacker called KillMilk, who announced his intention to go solo in July, but is still involved in the group’s activity. Legion and the squads (known as: “Jacky”, “Mirai”, “Impulse”, “Sakurajima”, “Rayd”, “Zarya”, “Vera”, “Phoenix”, “Kajluk”, “Sparta” and “DDOSGUNG”) are referred to as Killnet’s special forces, with Legion referred to as its Cyber Intelligence Force.

Figure 9 – Recruitment announcement to the squads of the Legion
Multiple small squads are organized around the largest group and its former leader, KillMilk, which relays attack orders to each group’s “commander”, which allows independent infrastructures, inevitably improving the survival of the entire organization. This proves effective as the squads continue to recruit members and increase in number. Their Telegram page contains rules, discussions about targets, and instructions on joining/creating additional squads by members who seek autonomy or “promotion.”
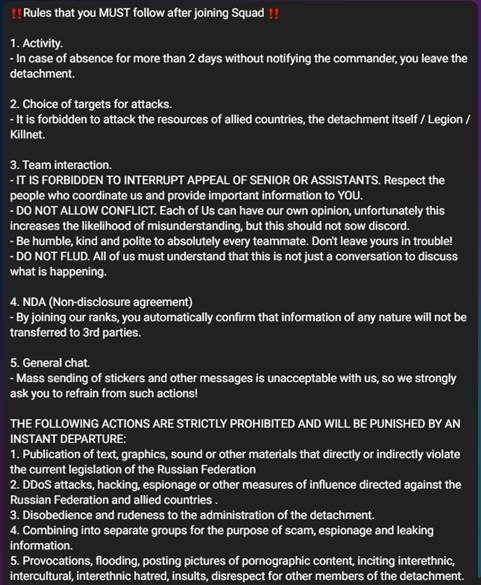
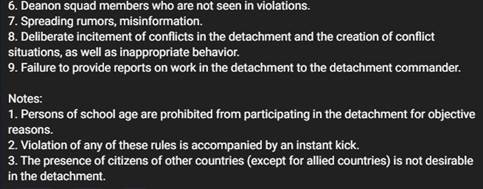
Figure 10 – Rules of the Legion
Killnet’s evolution has put them in a position where other groups want to collaborate with them or officially join forces.
Recruitment
Another interesting and new phenomenon concerns the groups’ recruitment methods. Unlike Anonymous, who takes pride in welcoming everyone, with no requirement of proof of skills or specific agenda, the new era hacktivists only accept members who meet certain minimum requirements.
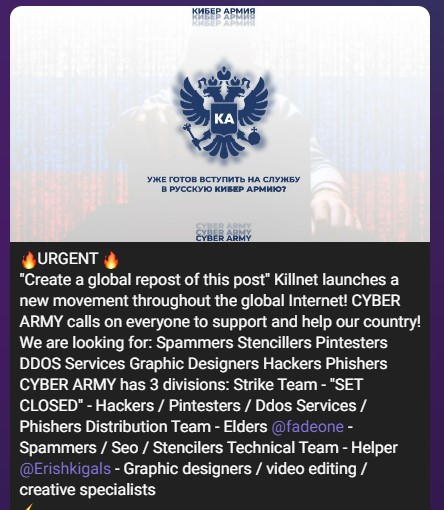
Figure 11 – Required professionals to Killnet
Many groups, such as Killnet and its squads, choose to invest in “proper” recruitment programs advertised on their Telegram channels. Some groups have a pre-selection process to bring only skilled hackers or experts in a particular field, to reduce the risk of making mistakes that could expose the whole operation.
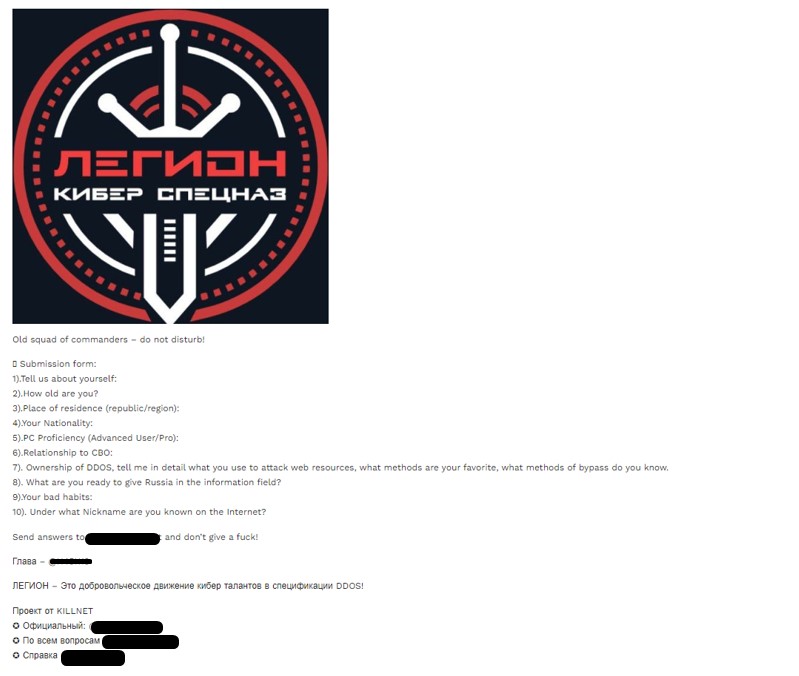
Figure 12 – Recruitment form to the squads of the Legion
However, recently we observed KillNet relaying DDoS attacks instructions to the masses, perhaps due to a lack of manpower to carry out all its intended actions.
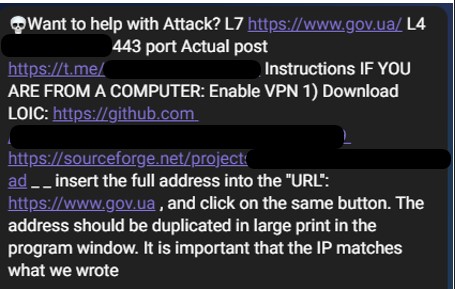
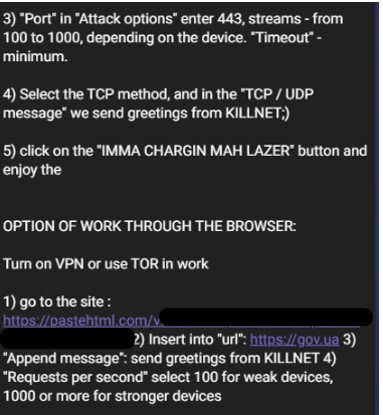
Figure 13 – DDoS attacks instructions by Killnet
On several occasions, we also saw KillNet offering rewards for individuals performing real-world, not virtual, vandalism in Ukraine.
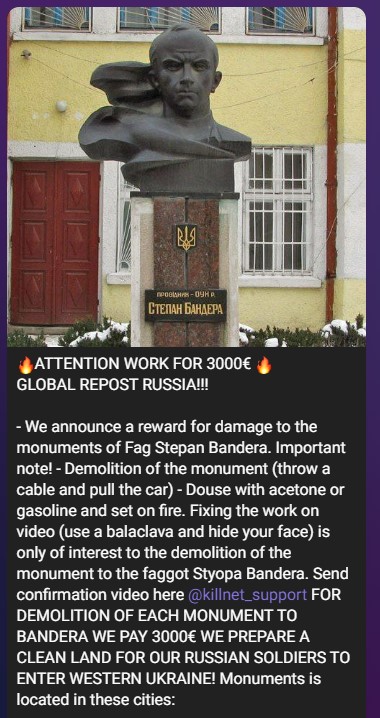
Figure 14 – KillNet offering a reward for anyone willing to physically sabotage monuments on their behalf in Ukraine
The recruitment process is similar for many Russian state-mobilized groups. For example, XakNet (who also refer to themselves as the “Team of Russian Patriots”) is a Russian-speaking group that has been active as early as March 2022. XakNet threatened to retaliate against Ukrainian organizations for any cyber-attacks carried out against Russia and has targeted several entities within Ukraine and leaked the contents of a Ukrainian government official’s email. XakNet declared they will not recruit hackers, pentesters, or OSINT specialists without proven experience and skills.
Figure 15 – XakNet talent acquisition announcement
Other groups, like the pro-Russian NoName057(16), may offer training through different means such as e-learning platforms, tutorials, courses or mentoring.
Tools & Technological Prowess
Hacktivist groups strive to utilize more advanced tools in their attacks, as the more damaging the attacks, the more exposure and notoriety for the group. We have seen flashes of advanced tactics globally, but with the immediate and repetitive nature of hacktivism campaigns, most of the activity was focused around DDoS attacks through the use of huge botnets:
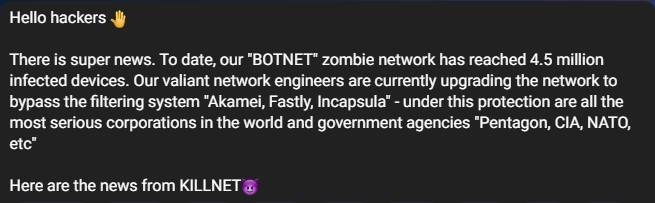
Figure 16 – Killnet’s claim about the size of their botnet
According to Avast, NoName057(16) uses a RAT known as Bobik, which has been around since 2020 together with Redline stealer. Recent reports state that devices infected with Bobik are part of a botnet carrying out DDoS attacks on behalf of NoName057(16).
In some cases, we see the group allegedly uses much more sophisticated destructive tools. For example, TeamOneFist is linked to destructive activities against Russian SCADA systems, and the Belarusian Cyber Partisans breached the computer systems of Belarusian Railways, right before the conflict started. In August, From Russia with Love (FRwL), claimed to have written their own Locker-like ransomware called “Somnia”.
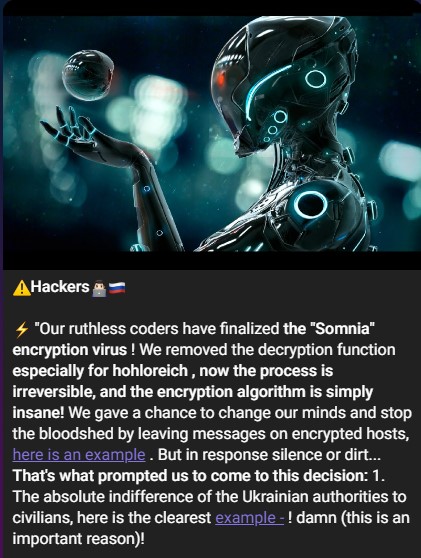
Figure 17 – From Russia with Love claim about launch of ransomware
Conclusion
Conflicts in Eastern Europe and the Middle East in the last few years affected the lives of many and escalated situations in broad domains across the world. One of the most significant escalation can be observed in the cyberspace ecosystems. During the previous decade, hacktivism was mostly a buzz word, which did not pose significant risks to global organizations. Having become more organized, structured, and sophisticated, hacktivism has ushered in a renaissance era. More concerning now is, many hacktivist groups have a very clear state-affiliated agenda and serve the special interests of specific governments. Even though this all began in specific conflict areas, we already see its proliferation to the west and beyond. We further expect hacktivist operators to enhance their arsenal and unleash state-level destructive attacks. Another growing worry is the fact that more and more governments are inspired by the success of new state-mobilized hacktivist groups, which may signify this phenomenon is here to evolve into a long-term activity.





