

By Oded Vanunu, Dikla Barda, Roman Zaikin
Highlights
- Blockchain Vigilance Unveils Million-Dollar Heist: Our Threat Intel Blockchain system uncovered an ongoing Rug Pull event, and traced the actor behind this scheme
- The Scammer’s Tactics: Exploiting Hype for Ill-Gotten Gains, The perpetrator lured unsuspecting victims into investing.
- Unraveling the Scam: A Step-by-Step Deception The scam operated in several stages, including the creation of fake tokens, the manipulation of liquidity pools, simulated trading activities, and the extraction of funds.
- Check Point Researchers calls out investors to understand the details of this step-by-step process, crucial to protect themselves from falling victim to similar schemes.
Background
In the dynamic realm of cryptocurrency, recent events have highlighted the ever-present threat of Rug Pulls—deceptive maneuvers that leave investors empty-handed. Our Threat Intel Blockchain system, developed by Check Point, recently sounded the alarm on a sophisticated scheme that managed to pilfer nearly $1 million. Let’s delve into the details of this elaborate crypto con and understand how it unfolded.
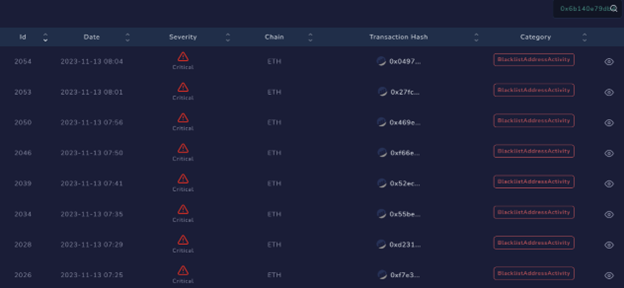
Check Point’s Threat Intel blockchain system identified and alerted the following address 0x6b140e79db4d9bbd80e5b688f42d1fcf8ef97798
This address involves in blacklisted activities, our system has begun monitoring the activities associated with the wallet address:
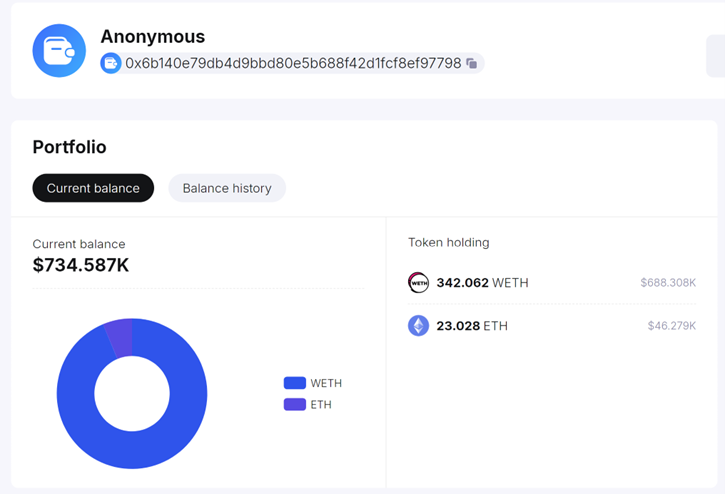
This is the balance of the scammer’s wallet (15/11/23), This address operated 40 distinct rug pulls and has been stolen almost 1 million dollars!
The scammer (0x6b140e79db4d9bbd80e5b688f42d1fcf8ef97798) tactic is to create tokens based on the latest hypes to lure victims to buy his tokens, for example, the token name GROK 2.0 (0xd4b726c5b5e6f63d16a2050ee3ac4a0f0f81f1d4), possibly derived from a well-known AI system (X GROK), is intended to attract buyers.
The Anatomy of the Scam:
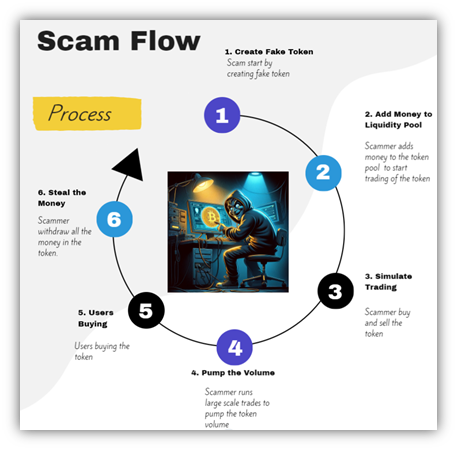
How did this elaborate scam work, and how did it manage to siphon off a substantial sum? Here’s a breakdown:
- Creating Fake Tokens: The scam commenced with the creation of deceptive tokens, exemplified by the token GROK 2.0. The choice of names often mirrored trending topics to attract unsuspecting buyers.
- Adding Money to the Liquidity Pool: To create a façade of legitimacy, the scammer injected funds into the token pool, creating the illusion of a vibrant and active token.
- orchestrated Trading Activities: Leveraging a specialized function (0x521da65d) in the contract, the scammer executed simulated trades, making it appear as if genuine buying and selling were occurring. However, it was merely a ruse orchestrated by the scammer.
- Pumping Up the Volume: Another function (0xf029e7cf) came into play, facilitating large-scale trades between WETH cryptocurrency and the GROK token. This artificial inflation created a sense of high demand and value, enticing investors to join in.
- Attracting Buyers: Capitalizing on the perceived attractiveness of the token, users began buying in, unaware of the impending deception.
- Taking the Money: Once the token had sufficiently lured in investors, the scammer executed the final move—withdrawal of liquidity from the token pool, leaving token purchasers with empty hands and depleted funds.
Technical part
The scammer used 2 different smart contracts to trade and pump the token volume. The first contract address he used is 0x2ef3216e95e2b7c8e378ae64534100e69598f955 which contained the simulated trading function (0x521da65d).
function 0x521da65d
The function 0x521da65d is responsible for selling and buying the token for the scammer, this function has been executed 226 times for just this token. The function’s behavior is contingent on the Boolean varg7, which dictates its course, leading to two separate execution routes.
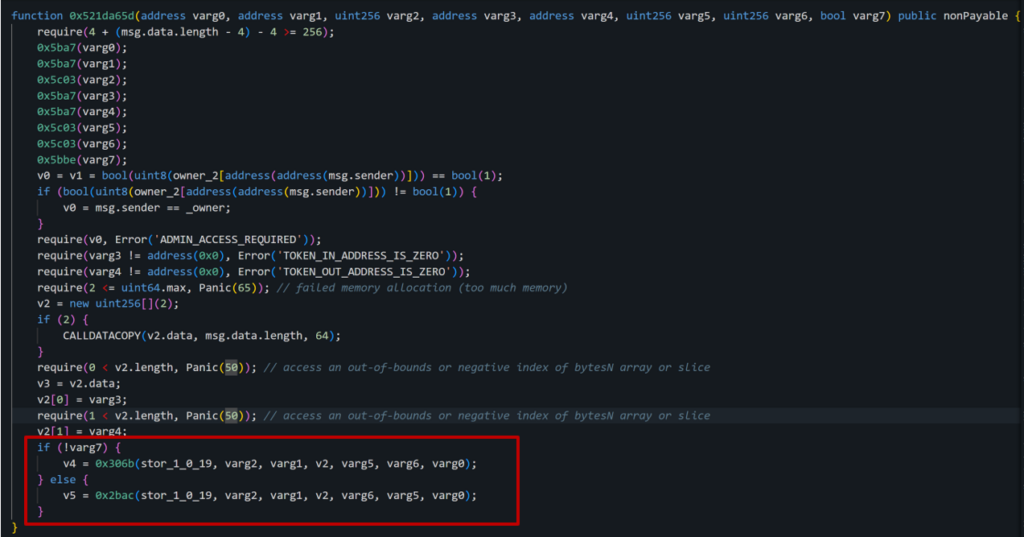
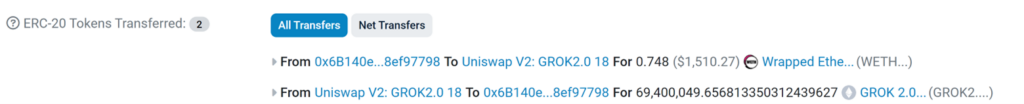
The first route (0x306b) is swapping from WETH cryptocurrency to GROK 2.0 (buying)
As you can see in this image:
And the 2nd route (0x2bac) represents swapping from GROK 2.0 to WETH (selling)
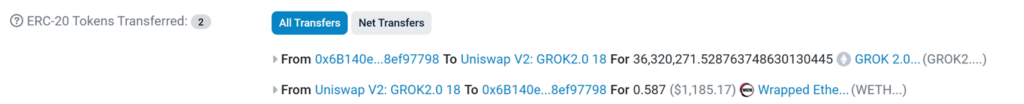
For the second smart contract, the scammer operated using the address 0x4b2a0290e41623fbfeb5f6a0ea52dc261b65e29b, where he executed the function 0xf029e7cf to artificially boost the token’s volume.
function 0xf029e7cf
This function receives five parameters:
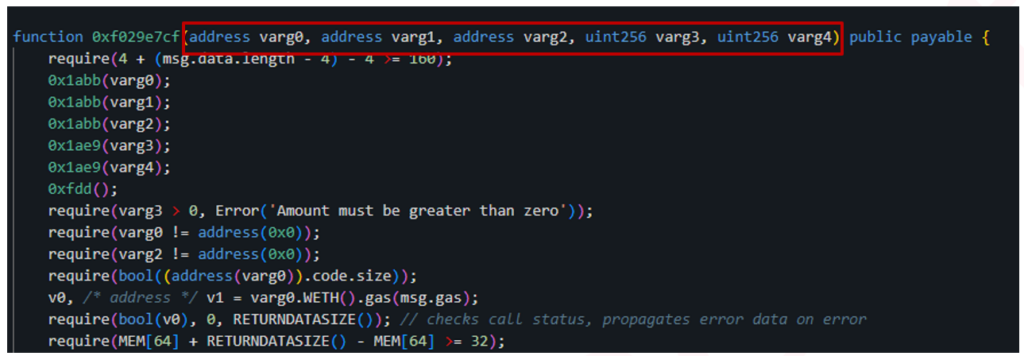
decoding the following data sent to this function unveil the following arguments:
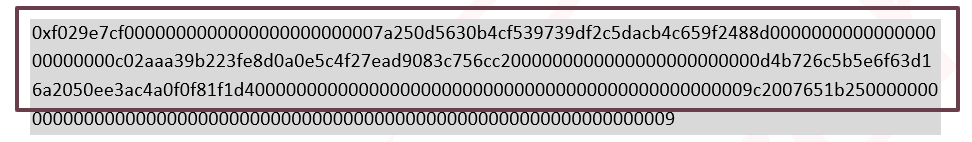
Varg0 is the Uniswap router address that the scammer will use to swap the tokens.
Varg1 is the WETH cryptocurrency address, which will be used to swap against the GROK token.
Varg2 is the GROK 2.0 token address.
Varg3 is the amount of the token to swap.
Varg4 is the number of times to swap this token.
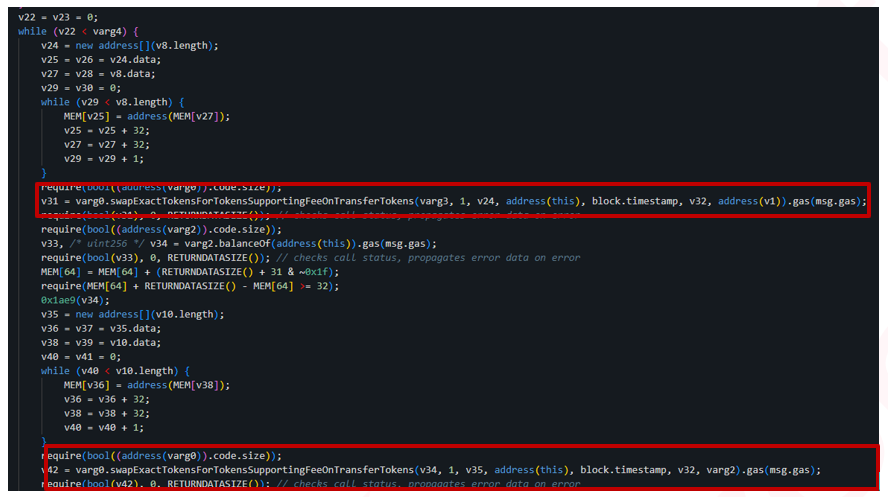
Looking deeper into the function we revealed the scammer used the function ‘swapExcatToekensSupportingFeeOnTransferTokens’ from Uniswap Router (varg0) to swap 9 times (varg4) from WETH(varg1) to GROK(varg2) and from GROK to WETH with a total amount of $ 420,000 which pumps the volume of the token and lures traders and bots to buy it.
The swaps loop can be seen in the following screenshot:
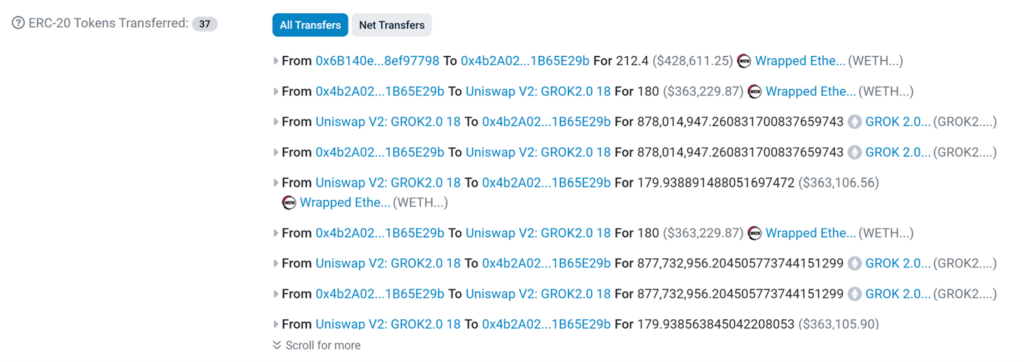
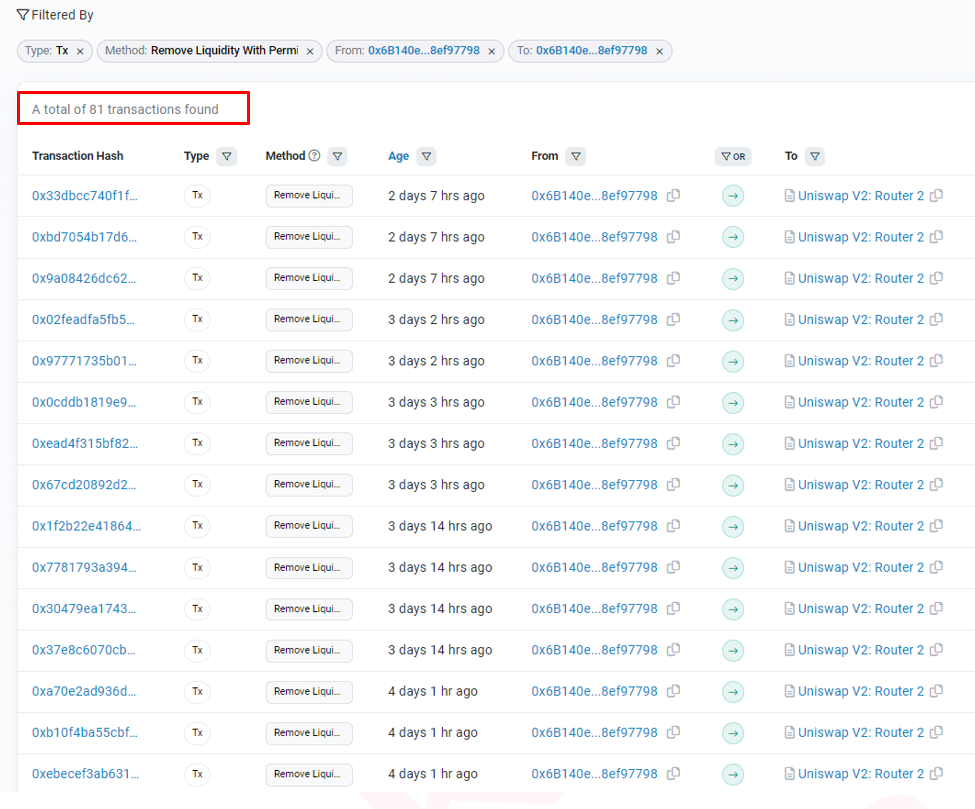
In the scam’s final phase, the scammer withdrew funds from the token’s liquidity pool after attracting a sufficient number of buyers and the token price increase. This is demonstrated by the fact that they removed liquidity from their deceptive tokens on 81 occasions.
Conclusion:
As the crypto landscape continues to evolve, staying vigilant and informed is paramount for investors. The recent Rug Pull incident serves as a stark reminder of the need for heightened awareness and due diligence. By understanding the tactics employed by scammers, we can collectively work towards creating a safer and more secure crypto environment.
It’s crucial to note that our commitment to safeguarding the crypto community extends beyond mere detection. Check Point researchers are actively monitoring domains associated with the identified scammer’s wallet address and similar. The Threat Intel Blockchain system, developed by Check Point, continues to accumulate valuable information on emerging threats, and this intelligence will be shared in the coming future. In this collaborative effort, we aim to empower investors with the knowledge needed to navigate the crypto space securely and protect themselves from potential pitfalls. For more information contact us at: [email protected]





