
By Oded Vanunu, Dikla Barda, Roman Zaikin
A recent investigation conducted by Check Point Research has revealed a sophisticated NFT scam campaign operating on a large scale:
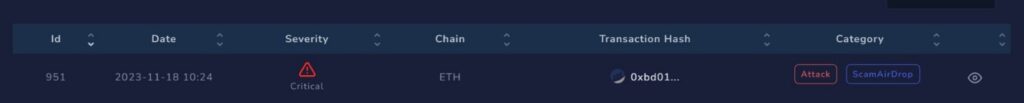
This campaign is unique in its methodology, employing a source spoofing technique to target a broad spectrum of token holders. It specifically focuses on more than 100 highly popular projects, aiming its attacks at token holders.
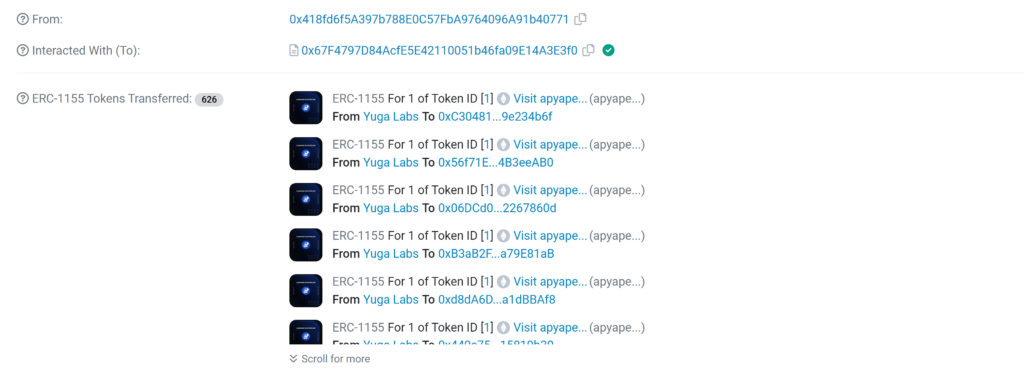
For instance, if you are listed as an APE token holder, the attacker would send you an airdrop labeled as an Ape NFT airdrop. The rationale behind this is that the attacker lacks access to the email addresses of APE token holders and, consequently, cannot directly identify the token owners. To circumvent this, the attacker devised an alternative method of reaching out to specific token holders through NFT airdrops linked to a specially crafted website for each targeted token. This approach lends the transactions an appearance of legitimacy, seemingly originating from trusted sources. An example of such a transaction can be viewed here:
The transaction cunningly appears to be from Yuga Labs-the company behind Bored Ape Yacht Club NFTs
Check Point’s Threat Intel blockchain system played a crucial role in alerting us to this emerging threat. Our investigation uncovered an extensive infrastructure that distributed AIRDROPs to more than 200K people mimicking famous projects, some of the projects can be seen in the image below:

The attacker’s modus operandi for each airdrop involves setting up a dedicated website for claiming rewards. Unsuspecting victims are enticed to connect their wallets to these sites, unknowingly granting full access to their funds.
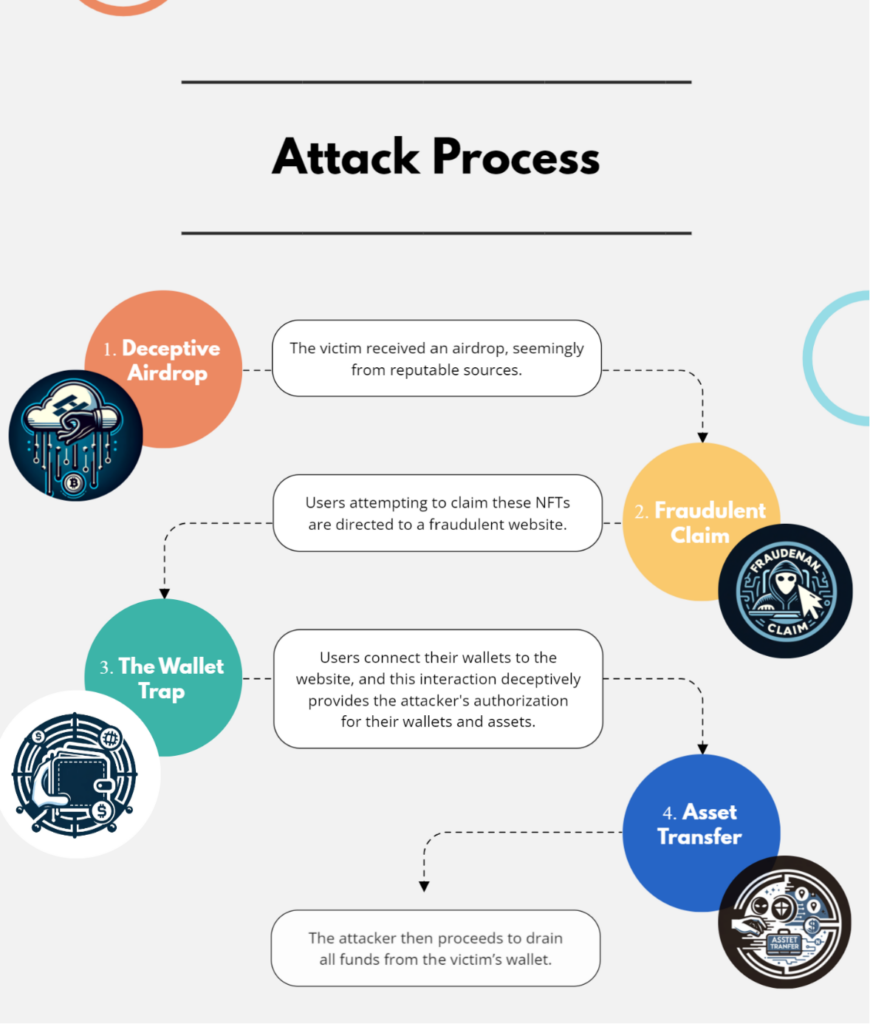
The attack unfolds in the following stages:
- The victim receives an airdrop, seemingly from a reputable source.
- The victim is then enticed to claim their NFT reward on a fraudulent website.
- Upon connecting their wallet to the website, the victim unwittingly authorizes the attacker.
- The attacker then proceeds to drain all funds from the victim’s wallet.
This sophisticated scam highlights the need for heightened vigilance in the ever-evolving landscape of digital assets and blockchain technology.
Deep Dive
Let’s delve into a specific transaction to better understand the mechanics of the scam. By examining the following transaction:
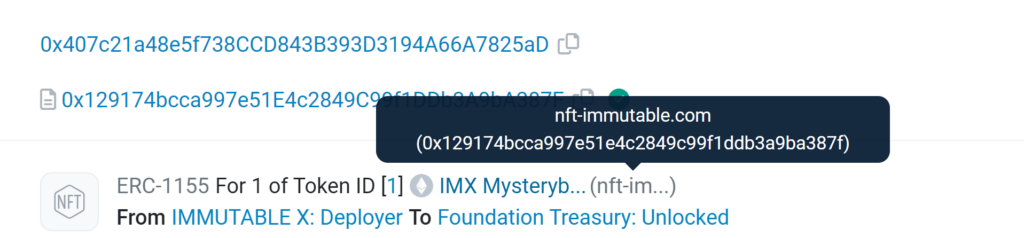
We observe what seems to be a distribution of a fake IMX NFT, allegedly issued by “IMMUTABLE X Deployer,” an address recognized as the original deployer of the IMX token.
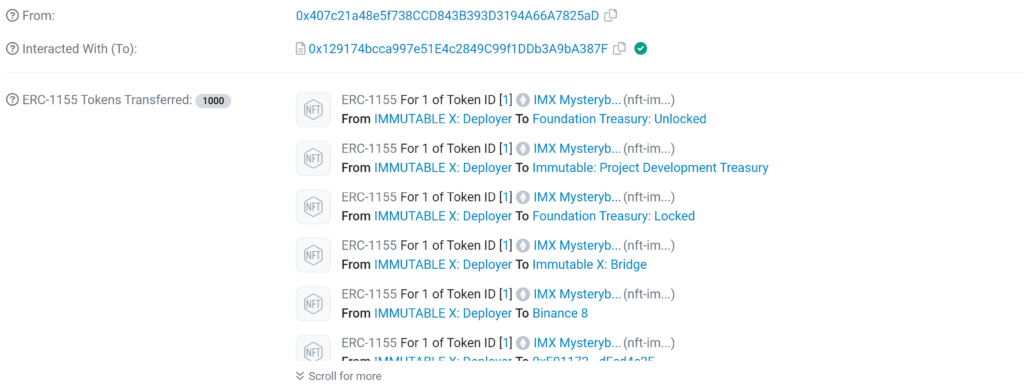
The Immutable Group, comprising the Immutable Platform and Immutable Games, is renowned for its role in developing and publishing web3 games on Ethereum. This reputation makes any association with it, such as an NFT airdrop, seem credible and trustworthy. However, a closer look at the transaction logs reveals a different story.
Upon scrutinizing the transaction logs, it becomes evident that the “From” address has been spoofed. This deception is facilitated by the way Etherscan processes transaction information, which is derived from the logs created by Solidity’s emit command. In Solidity, the emit command is used to record logs on the blockchain. While this feature is integral for maintaining a record of events, it can be manipulated to create misleading information. Consequently, the NFT in question did not originate from “IMMUTABLE X”, just as we previously demonstrated with Yuga Labs and other entities seemingly listed in the “From” section on Etherscan.
This situation highlights how blockchain transactions are interpreted and presented. While blockchain explorers like Etherscan are invaluable tools for navigating and understanding blockchain transactions, they are not immune to manipulation.
By using the emit command, malicious actors can create transaction logs that give a false impression of a transaction’s origin, misleading both users and automated scanners. This tactic is particularly effective in the world of NFTs, where the perceived legitimacy of an item’s source can significantly impact its value and desirability.
The method of the transaction executed is “airdrop”:
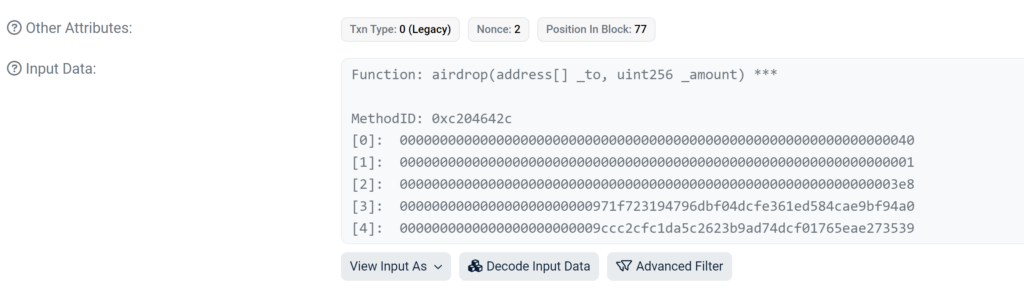
The analysis continues with a closer examination of the transaction’s execution context. The transaction in question is executed by the contract at address 0x129174bcca997e51E4c2849C99f1DDb3A9bA387F. This particular contract serves as a proxy, meaning it doesn’t directly implement the airdrop function itself. Instead, the actual implementation is delegated to another contract at address 0x5A954283c8600a96274bb5a1E3CfDE2e0Dc32Ea0.
A notable point about this implementation contract is that its code is not verified. This lack of verification makes it challenging to directly understand its functionality through conventional means. However, through the process of decompiling the contract, we can glean some insights into its behavior. Notably, the contract includes an event named TransferSingle, as can be seen in the image below.
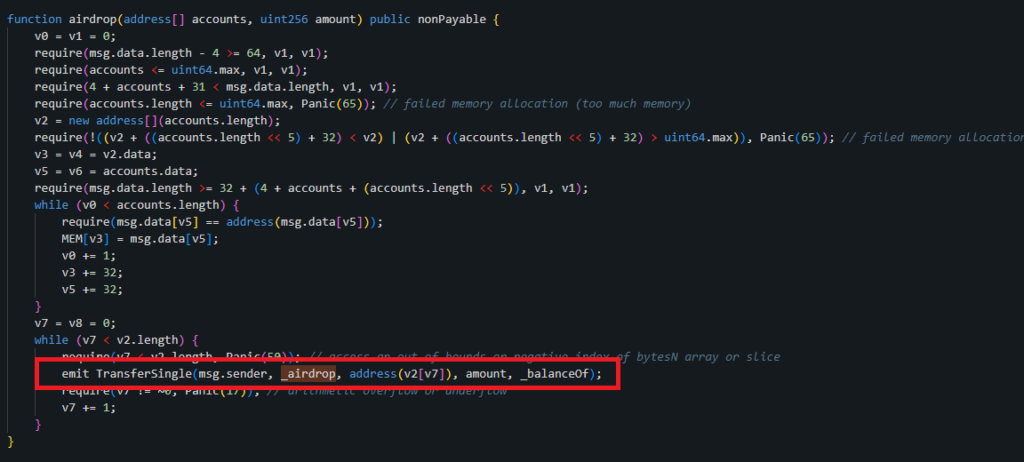
Additionally, the decompiled code reveals a parameter named _airdrop, which is stored at the location STORAGE[0x03] on the blockchain as can be seen in the image below. This parameter is crucial as it indicates the contract’s ability to store or manage state information related to the airdrop process.
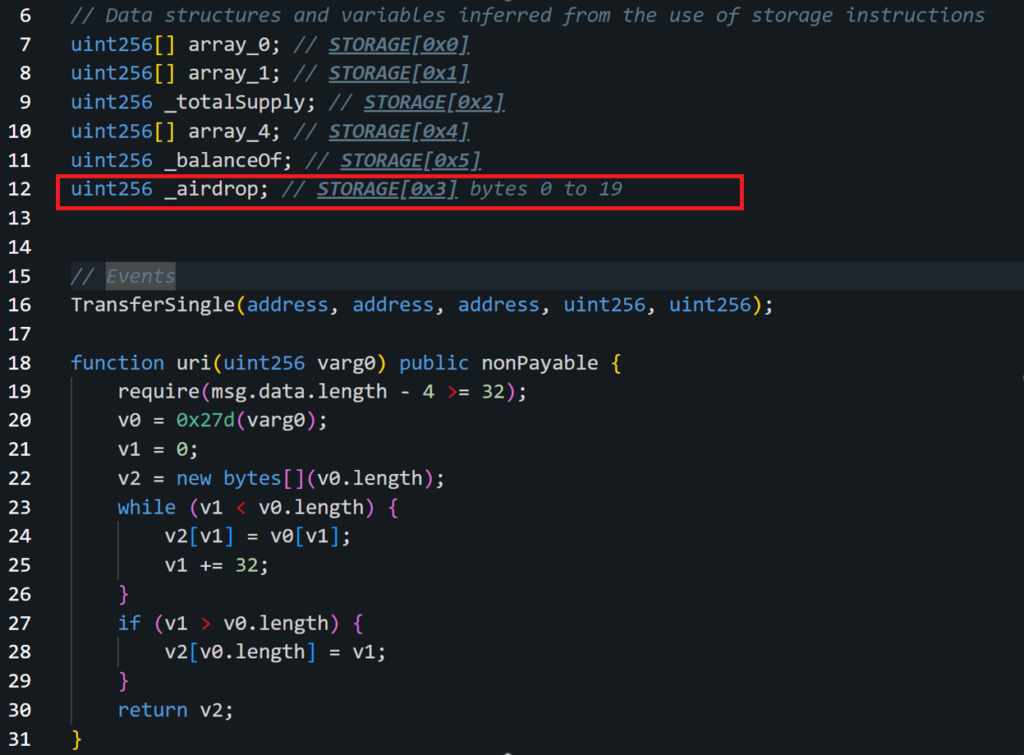
The usage of a proxy contract in this context is particularly noteworthy. Proxy contracts are often used in blockchain development for various reasons, including upgradeability and modularity. However, in this scenario, the proxy serves as a layer of obfuscation, distancing the visible, user-facing contract from the actual logic implementation, which resides in an unverified contract. This separation can make it more difficult for users or analysts to ascertain the true nature and intent of the transaction, especially when the implementation details are hidden or obfuscated.
The discovery of the TransferSingle event and the _airdrop parameter in the decompiled contract provides valuable insights into the mechanics of the scam. It suggests a level of sophistication in the scammer’s approach, utilizing complex smart contract interactions to execute the deceptive airdrop. This level of complexity highlights the need for rigorous scrutiny when interacting with smart contracts, especially in cases where contract code is unverified or where proxy contracts are used.
To find what was located in storage3 we had to read the storage from the blockchain itself via a Python code:
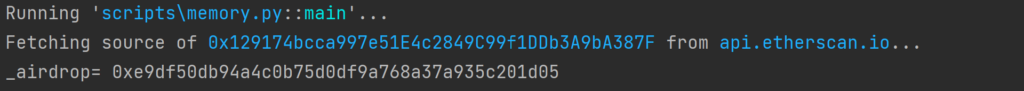
We can see that _airdrop contains the address 0xe9df50db94a4c0b75d0df9a768a37a935c201d05, which is the real address of IMMUTABLE X deployer so the scammer just uses an emit TransferSingle to mislead the users into thinking that this is the actual address that sent them the NFT AIRDROP.
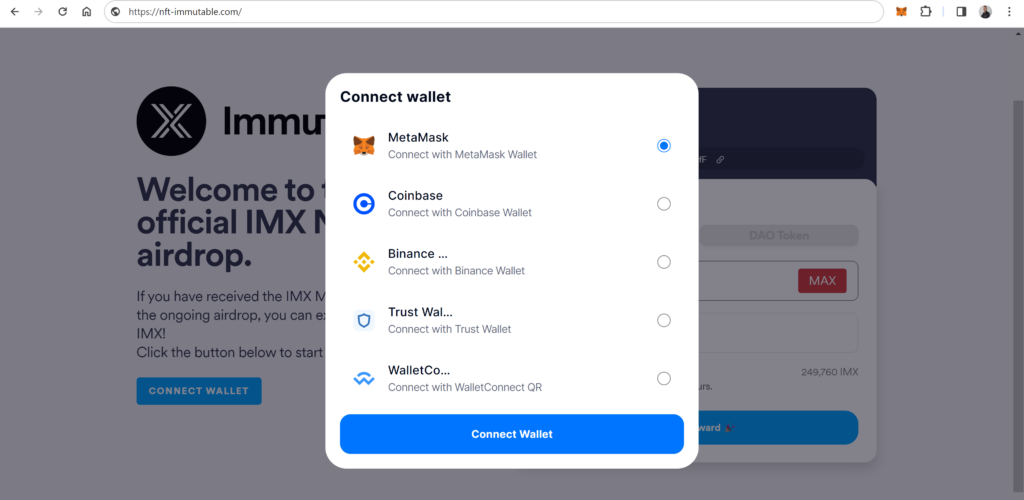
The next phase of the scam involves an intricately designed trap that uses the NFT itself as bait. Each NFT in this AIRDROP includes a link to a specific website:
This website is a crucial component of the scam, as it is carefully crafted to appear legitimate and entice the recipient of the AIRDROP to engage further. The unsuspecting user, upon receiving the AIRDROP and possibly intrigued or excited by the prospect of claiming it, is likely to visit the linked website.
Once the victim navigates to this website, they find themselves on a page that, while appearing genuine and trustworthy, is a sophisticated phishing site designed for wallet theft. The site’s primary goal is to deceive the victim into signing a transaction under false pretenses. This is a classic phishing tactic, but it’s given a new twist in the context of the blockchain and NFTs.
The website typically presents the victim with an opportunity to claim the NFT or access some exclusive benefit associated with it. In doing so, it prompts the user to connect their cryptocurrency wallet to the site. This step is common in legitimate NFT interactions, which adds to the illusion of authenticity. However, the critical difference here is that, once connected, the site will attempt to trick the user into signing a transaction that grants the scammer access to the user’s funds.
This type of attack exploits the trust and excitement that can come with receiving an NFT, particularly from a seemingly reputable source. The combination of a fake AIRDROP with a phishing website represents a sophisticated and multi-faceted approach to scamming. It underscores the importance of being extremely cautious when receiving unexpected digital assets and highlights the need for heightened vigilance when interacting with any external links or websites associated with such assets.
For users in the blockchain and NFT space, it’s crucial to be skeptical of unsolicited AIRDROPS and to thoroughly verify the legitimacy of any associated websites or links before interacting with them, especially when these interactions involve connecting a digital wallet or signing transactions.
Conclusion
This elaborate NFT scam sheds light on the increasingly sophisticated methods employed by attackers in the digital asset space. It’s a stark reminder of the ever-present need for vigilance and skepticism, particularly in environments where high-value assets like NFTs and cryptocurrencies are involved.
Key takeaways for the reader:
- Be Wary of Unsolicited Airdrops: Always approach unexpected airdrops with caution. If something seems too good to be true, it often is. Verify the source before interacting with any airdrop.
- Scrutinize Embedded Links: Be extremely cautious with links embedded in NFTs or other digital assets. These links can lead to phishing sites designed to steal your credentials and funds.
- Understand Smart Contract Interactions: Recognize that interacting with a smart contract can have significant implications. Be particularly cautious about signing transactions or connecting your wallet to unfamiliar websites.
- Educate Yourself: Stay informed about common scam tactics and educate yourself on safe practices when dealing with blockchain technology and digital assets.
- Use Trusted Tools and Resources: Utilize trusted blockchain explorers and tools for verifying the legitimacy of transactions, contracts, and airdrops. However, remember that even these tools can be fooled under certain circumstances.
- Double-Check Sources: If an airdrop or transaction claims to be from a well-known company or project, verify through official channels. Scammers often use the names of reputable entities to gain trust.
- Practice Safe Browsing: Ensure that your internet browsing is secure. Use web browser extensions that can help detect and block phishing sites.
- Secure Your Assets: Consider using hardware wallets for storing significant amounts of cryptocurrency. They offer an additional layer of security against online phishing attempts.
The blockchain ecosystem, while innovative and promising, is also a fertile ground for sophisticated scams. As the technology continues to evolve, so do the tactics of those looking to exploit it. Staying educated, cautious, and skeptical are your best defenses against such threats. Always take the time to verify before taking action, especially when your digital assets are at stake.
The Threat Intel Blockchain system, developed by Check Point, continues to accumulate valuable information on emerging threats, and this intelligence will be shared in the future. In this collaborative effort, we aim to empower investors with the knowledge needed to navigate the crypto space securely and protect themselves from potential pitfalls. For more information contact us at: [email protected]





