

Research by Dikla Barda, Roman Ziakin and Oded Vanunu
Check Point’s Threat Intel blockchain system identified and alerted that in recent times, fraudsters have evolved to become increasingly sophisticated, exploiting legitimate blockchain protocols to conduct their scams.
The Uniswap Protocol, launched in 2018, is the largest and most popular decentralized exchange for swapping cryptocurrency tokens on Ethereum and other popular blockchains, locking over $1.8 trillion in trading volume and 350 million swaps. As the fifth largest application on Ethereum, Uniswap holds over $4 billion in total value locked (TVL) and consistently achieves billions in weekly trading volume, maintaining its position as the leading decentralized exchange by volume on Ethereum mainnet, Polygon, Arbitrum, and Optimism. Safe.global meanwhile is like a smart contract wallet and claimed to have a total of 69million transactions, with 9.5million accounts deployed totalling $100 billion in total assets stored.
By leveraging the trust and functionality of well-established platforms like Uniswap V3 and Safe.global, these attackers disguise their malicious activities. For instance, scammers cleverly embed their attacks within the multicall aggregate function on Uniswap V3 contract, which allows them to execute multiple transactions in a single call, thereby obfuscating their true intentions.
Similarly, they utilize the GnosisSafeProxy contract to create seemingly legitimate contracts, which are then used to perpetrate fraudulent schemes. This cunning manipulation of trusted protocols not only enhances the credibility of their scams but also makes detection and prevention significantly more challenging.
The Technical Side of Aggregate Function
When the victim receives such a transaction, he will see that the address: 0x5BA1e12693Dc8F9c48aAD8770482f4739bEeD696
Wants to perform aggregate, as can be seen in the following screenshot:
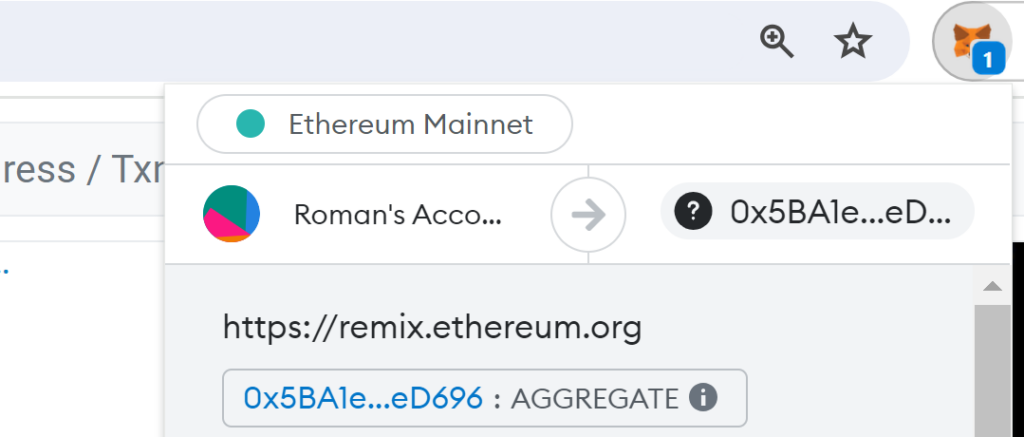
If the victim checks who this address is, he will see it’s a legitimate Uniswap V3 Multicall2 contract.
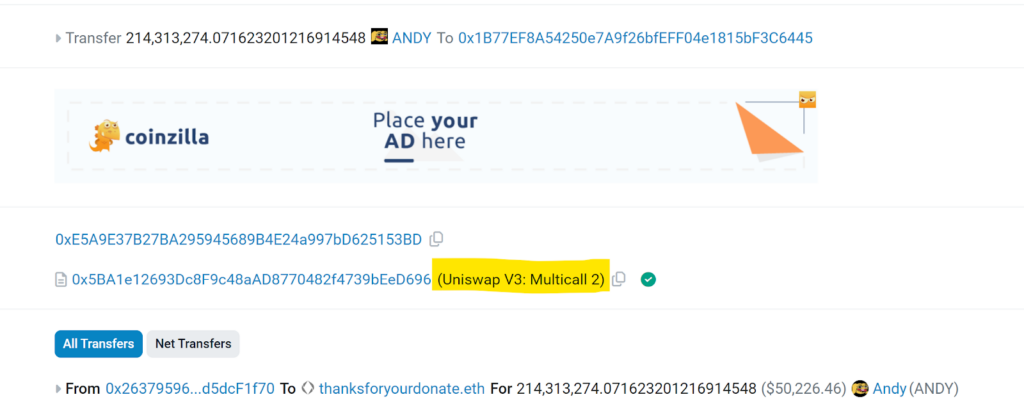
Let’s take a look at the aggregate function in the multicall Uniswap contract :
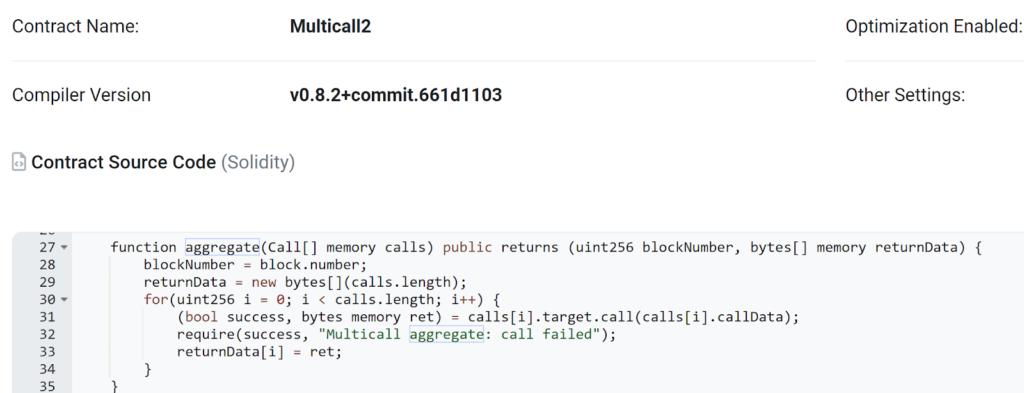
The function takes a single parameter: ‘calls’, which is an array of Call structs. Each Call struct includes:
target: The address of the contract to call.
callData: The data (function signature and parameters) to be sent to the target contract.
The aggregate function iterates over each provided call in the calls array. For each individual call, the function initiates a request to the specified target contract using the given callData. This mechanism enables the aggregate function to execute multiple operations across different contracts in a single transaction, enhancing efficiency and transactional cohesion.
So where is the security concern?
The open nature of the contract, allowing any user to set targets and data parameters, poses a substantial risk. In an environment where asset theft is rampant, the inherent trust placed in recognized addresses such as Uniswap can be exploited. For instance, if a user checks the multicall contract address on platforms like Etherscan, and sees that it is labeled as associated with Uniswap, they could mistakenly assume it is safe. This perceived safety can be dangerous as Uniswap, being a decentralized exchange (DEX), regularly interacts with user wallets for transactions.
Attackers leverage the Uniswap Multicall contract to orchestrate fund transfers from victims’ wallets to their own. They do this by using Uniswap as the spender address. Unsuspecting users, seeing Uniswap listed as the spender and trusting its legitimacy, might then approve transactions they believe are standard operations. This approval unwittingly grants permission for the transfer of their assets directly into the attackers’ wallets.
Here is a real-life example illustrating how such exploitation can occur: 0xe02a450b96a2679557dc6ea214808eb0692e8b96c7a8da47f67e4e26d0086aab In this text, we can see that the Uniswap v3 multicall contract is used:
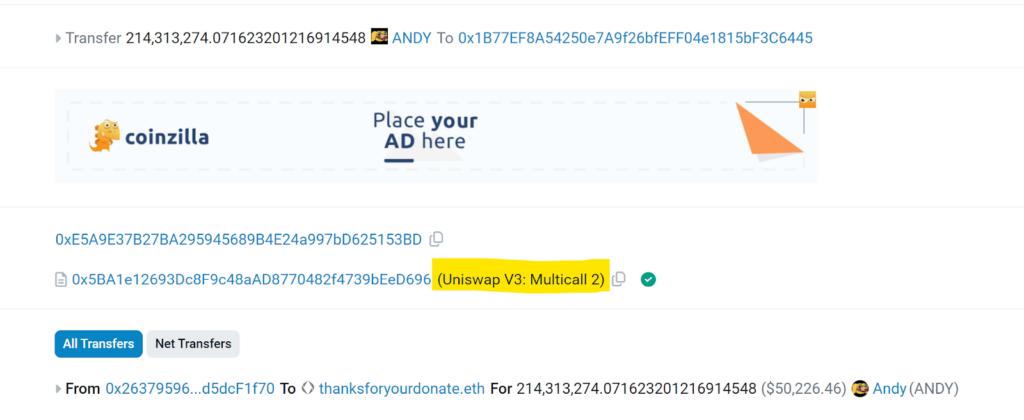
an aggregate function is called:
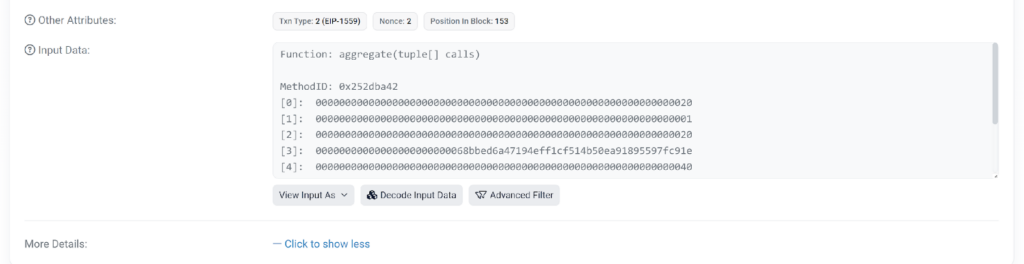
The attacker exploits the aggregate function to execute the transferFrom function, which enables the scammer to withdraw funds on behalf of a specified wallet. To successfully utilize this function, the initiator of the transferFrom transaction must have prior approval to withdraw money from the targeted wallet.
When examining the transaction logs, we observe an approval event. This approval was granted by the victim to the Uniswap Multicall contract just moments earlier when the victim unknowingly signed a request, manipulated by the attacker, to increase the allowance.
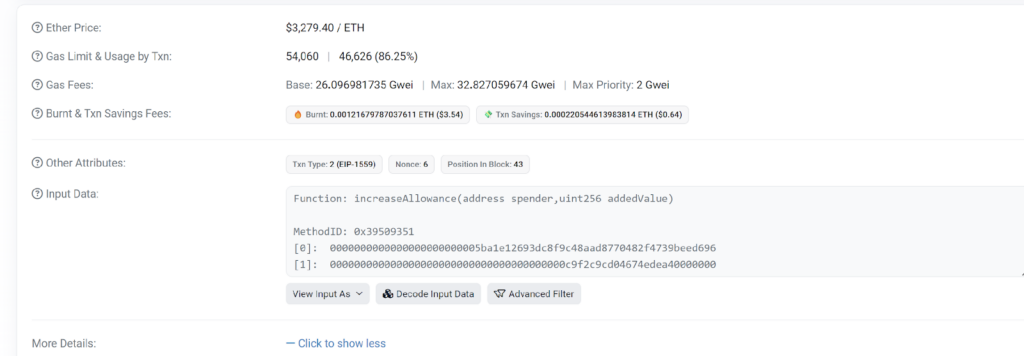
This action effectively raised the limit on the amount the attacker could withdraw from the victim’s wallet.
Following the victim’s approval, the Uniswap Multicall contract was authorized to manage funds on their behalf. Leveraging this approval, the attacker initiated a transferFrom operation via the Multicall contract, which already had permission to access the victim’s funds. Within the aggregate function, the attacker-specified a target—the specific token they intended to steal—and used the transferFrom function to redirect the victim’s money to a wallet under their control.
Safe (formerly known as Gnosis Safe) stands out as a premier choice for multi-signature wallets. This smart contract platform allows users to create and operate wallets that necessitate multiple approvals to execute transactions.
To begin using Gnosis Safe, users must first set up a Safe account through the Safe Interface. This process assigns a unique Safe address to each account, linked to a Safe Proxy. The proxy is pivotal as it holds the funds and conducts transactions on behalf of the account.
However, this infrastructure isn’t immune to misuse. Attackers have been known to use the Gnosis Safe contracts and framework, coaxing unsuspecting victims into signing off on fraudulent transactions.
An attack example seen earlier this year:
https://etherscan.io/tx/0x3c696c2f9af5f2717d74522c19a300cf65d2077aaf9cef435dc186 26d162a524
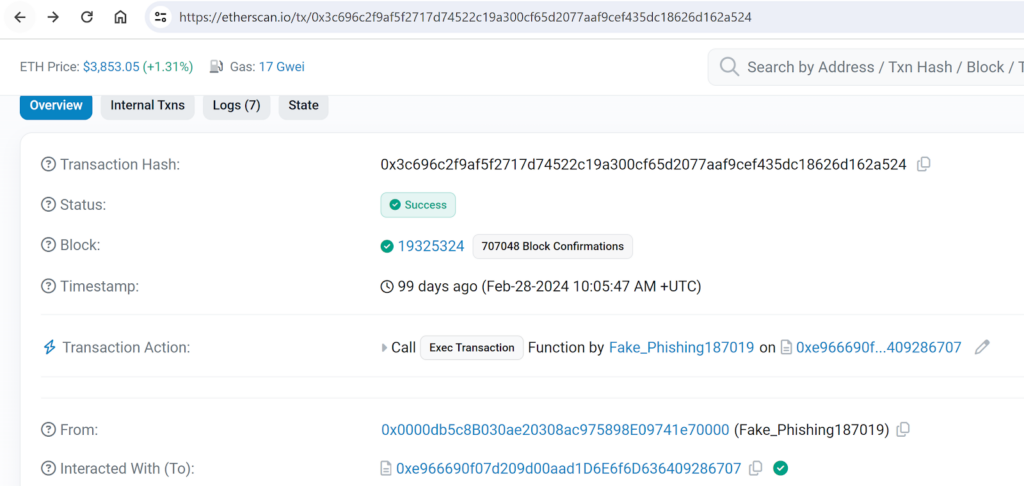
Let’s explore how it unfolds. Initially, the attacker utilizes the Gnosis Safe framework to establish a legitimate proxy contract. Next, the attacker tricks the victim into engaging with this proxy contract, persuading them to carry out an “increase allowance” transaction. This action authorizes the Gnosis Safe Proxy contract to manage tokens from the victim’s
wallet.
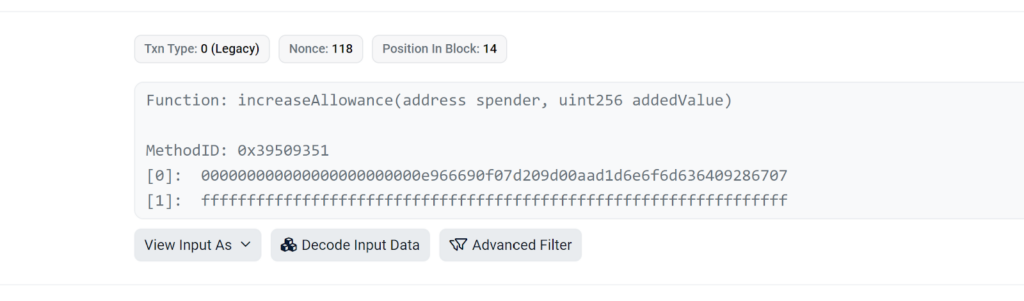
Shortly thereafter, the attacker employs the execTransaction function on the Gnosis Safe Proxy contract to conduct multiple transactions.
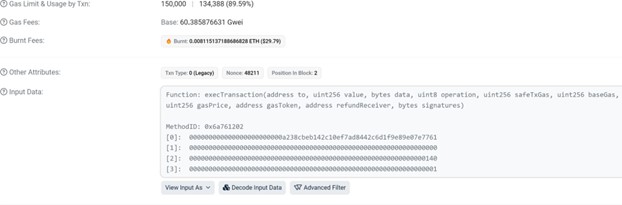
Let’s delve into how this function operates:
When the execTransaction function is triggered on a proxy contract, it forwards this call to the master copy, also known as the singleton. This is achieved using the delegatecall operation in Solidity, enabling the execution of the master copy’s code within the proxy’s storage
context.
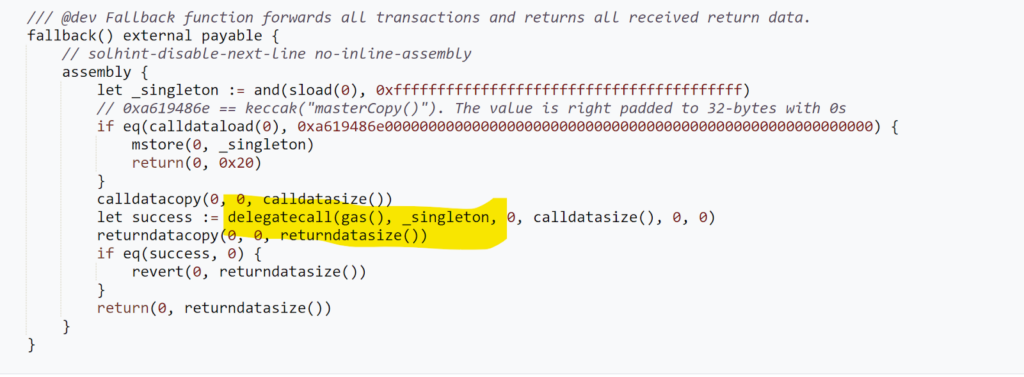
The execTransaction function, as defined in the singleton contract, ensures that transactions are only executed after receiving the requisite approvals from the designated number of owners, verified through their signatures. It also efficiently manages gas payments, ensuring that all transaction costs are adequately covered and refunds are issued where necessary. Furthermore, this function is enhanced by integration with guard contracts, which perform additional security checks. This setup creates a secure and efficient framework for handling multi-signature
transactions.
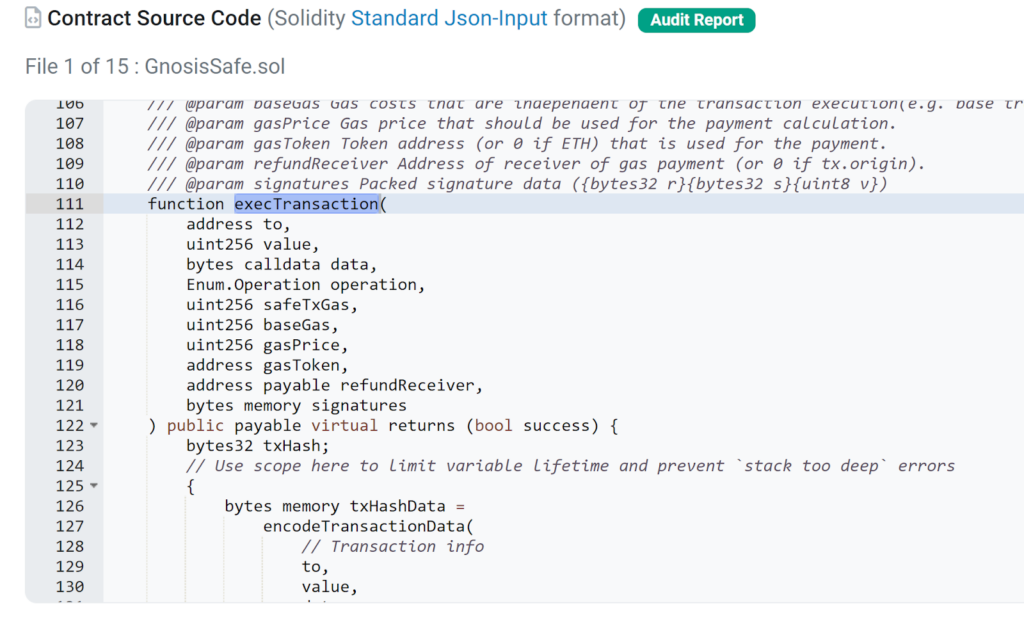
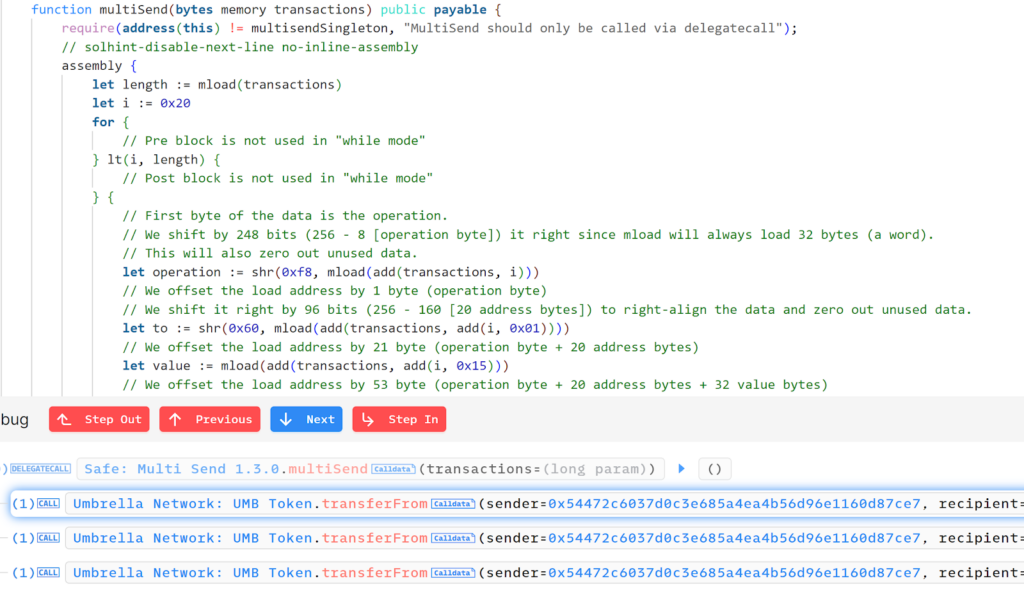
If we examine the code closely, we observe that it involves a call to the Gnosis Safe Executor contract. This contract is specifically designed to facilitate transaction execution on behalf of the Safe. Within this contract, the execute function is triggered, which in turn calls the Safe MultiSend contract.
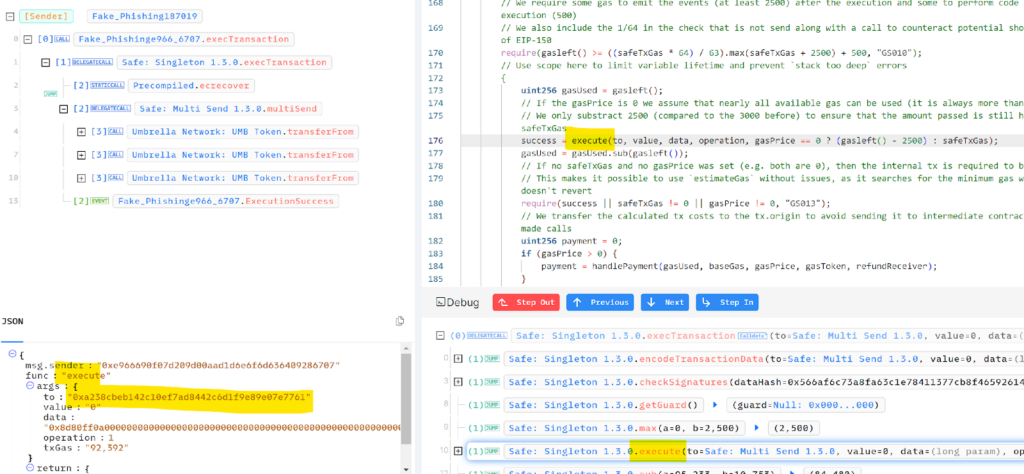
The Safe MultiSend contract is a crucial component of the Gnosis Safe framework. It enables the bundling of multiple transactions into a single operation, much like the aggregate function in Uniswap. This capability is highly beneficial for enhancing efficiency and minimizing gas costs when several actions need to be executed concurrently.
Analyzing the data directed to the MultiSend function reveals that it processes three transferFrom requests involving the token “Umbrella” from the victim, allowing the attacker to drain the tokens from the victim’s wallet.
In light of these sophisticated scams, it is imperative to adopt stringent security measures to safeguard your digital assets.
- Always verify the legitimacy of contracts and their functions before approving any transactions.
- Avoid blindly accepting transactions, even if they appear to come from trusted sources.
- Whenever possible, perform actions directly from the official project websites to ensure authenticity.
- Exercise caution with emails and links on social media, as they can be vectors for scams.
- Regularly monitor your wallet and transaction history for any unusual activity.
- Stay informed about the latest scams and best practices by following reputable blogs and actively engaging with the blockchain community.
By implementing these proactive measures, you can significantly reduce the risk of falling victim to advanced fraudulent schemes.





