

Key Points
- The FunkSec ransomware group emerged in late 2024 and published over 85 victims in December, surpassing every other ransomware group that month.
- FunkSec operators appear to use AI-assisted malware development which can enable even inexperienced actors to quickly produce and refine advanced tools.
- The group’s activities straddle the line between hacktivism and cybercrime, complicating efforts to understand their true motivations.
- Many of the group’s leaked datasets are recycled from previous hacktivism campaigns, raising doubts about the authenticity of their disclosures.
- Current methods of assessing ransomware group threats often rely on the actors’ own claims, highlighting the need for more objective evaluation techniques.
Introduction
The FunkSec ransomware group first emerged publicly in late 2024, and rapidly gained prominence by publishing over 85 claimed victims—more than any other ransomware group in the month of December. Presenting itself as a new Ransomware-as-a-Service (RaaS) operation, FunkSec appears to have no known connections to previously identified ransomware gangs, and little information is currently available about its origins or operations.
Our analysis of the group’s activity indicates that the impressive numbers of published victims may mask a more modest reality both in terms of actual victims as well as the group’s level of expertise. Most of FunkSec’s core operations are likely conducted by inexperienced actors. In addition, it is difficult to verify the authenticity of the leaked information as the group’s primary goal appears to be to gain visibility and recognition. Evidence suggests that in some instances, the leaked information was recycled from previous hacktivist-related leaks, raising questions about its authenticity.
In this report, we explore FunkSec’s ties to hacktivist activity and provide an in-depth analysis of the group’s public operations and tools, including a custom encryptor likely developed by a relatively inexperienced malware author based in Algeria. In a surprising discovery, our findings indicate that the development of the group’s tools, including the encryptor, was likely AI-assisted, which may have contributed to their rapid iteration despite the author’s apparent lack of technical expertise
This case highlights the increasingly blurred line between hacktivism and cybercrime, emphasizing the challenges in distinguishing one from the other. Whether such a distinction genuinely exists—or whether the operators are even aware of or concerned with defining it—remains uncertain. More importantly, It also calls into question the reliability of current methods for assessing the risk posed by ransomware groups, especially when those assessments rely on the public claims of the actors themselves.
Background – FunkSec Activity
FunkSec is an emerging ransomware group that launched its data leak site (DLS) in December 2024 to centralize their ransomware activities. The group uses double extortion tactics, combining data theft with encryption to pressure victims into paying ransoms. Their DLS features breach announcements, a custom-developed DDoS tool, and, more recently, a custom ransomware offered as a Ransomware-as-a-Service (RaaS).

FunkSec gained public attention due to their aggressive tactics and the number of their targets, with more than 85 claimed victims in little over a month of activity. Notably, FunkSec demanded unusually low ransoms, sometimes as little as $10,000, and sell stolen data to third parties at reduced prices. The group’s activities are widely discussed in cybercrime forums, further contributing to their growing notoriety.
Closer analysis of FunkSec’s activities and DarkWeb discussions offers some tantalizing hints about the group, namely that their motivations seem to straddle the line between hacktivism and cybercrime. Interestingly, some members linked to FunkSec previously engaged in hacktivist activities, adding a complex layer to their operations and raising questions about their true objectives. This blend of tactics and backgrounds made FunkSec a particularly intriguing case for deeper investigation.
FunkSec Offerings
Ransomware
FunkSec operators recently began to offer their rapidly evolving custom ransomware. With each new version, many of them published only days apart, their website is updated to highlight the added features. In the announcement for the latest version V1.5, the operators boasted about its low detection rate, sharing a VirusTotal screenshot that showed it was detected by only three antivirus engines at the time of publication.
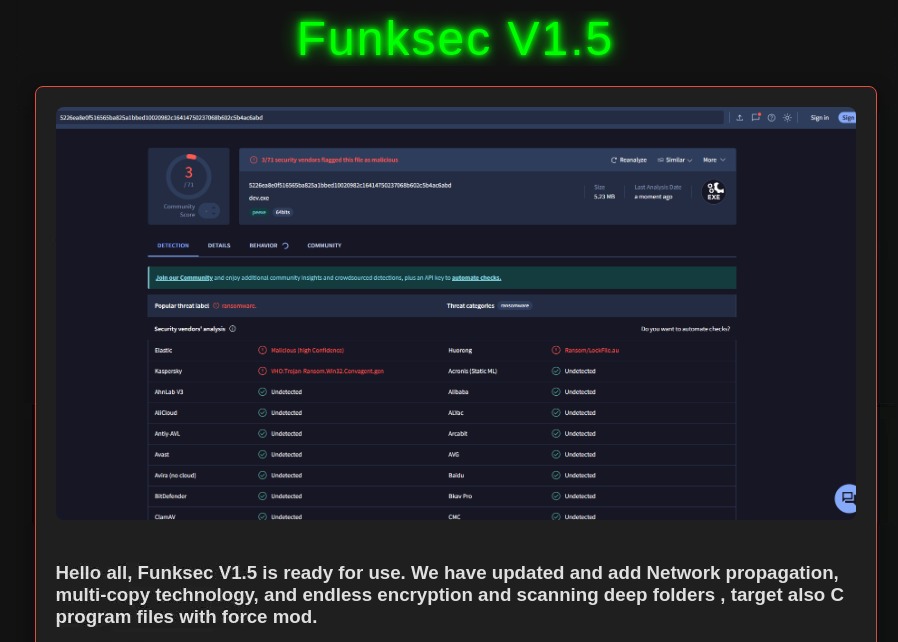
The file referenced in their publication(5226ea8e0f516565ba825a1bbed10020982c16414750237068b602c5b4ac6abd), named dev.exe, was uploaded from an Algerian source, and truly was detected by only 3 engines at the time of upload. The ransomware is identified by using the extension “.funksec”, written in Rust and compiled on the environment of C:\Users\Abdellah\. A full analysis of the malware is provided in the Technical Analysis section.
In our analysis of this ransomware, we uncovered all its versions which point to an ongoing development effort likely carried out by an inexperienced malware author. Notably, most of the versions were uploaded from Algeria, likely by the author himself. Analysis of those samples reveals two variants of the ransom notes. The first references FunkSec, and the second one references Ghost Algeria, another indication that the developer is from Algeria.
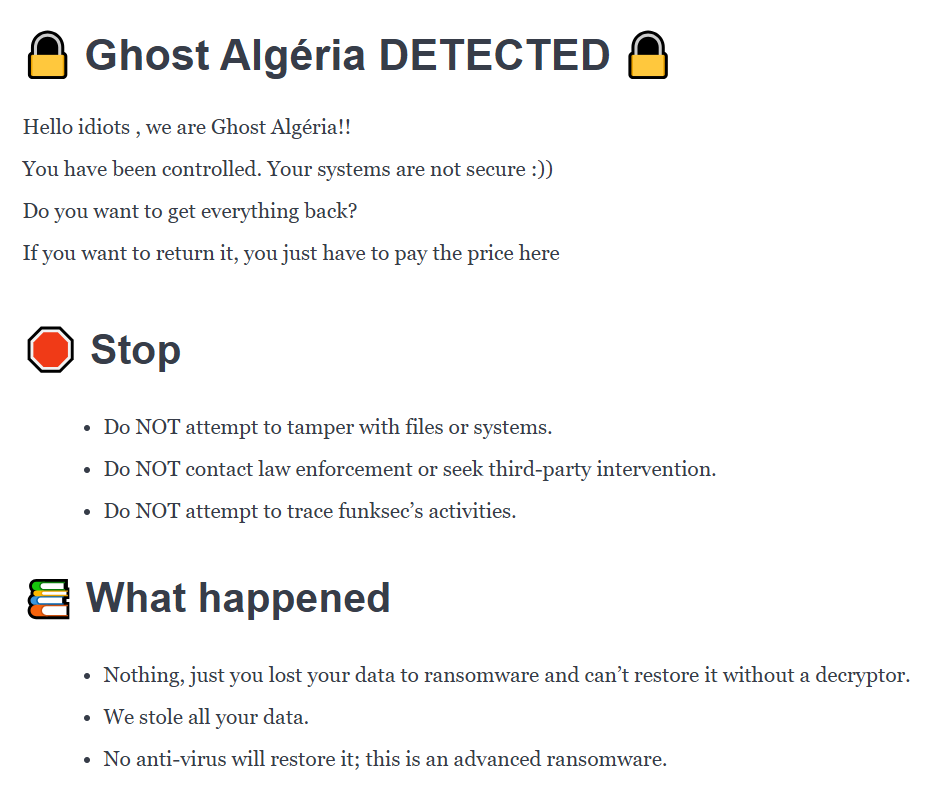
Figure 4 – Ransomware notes used by FunkLocker and Ghost Algeria.
Interestingly, the author also uploaded parts of the malware’s source code, written in Rust. The source code file, named *ransomware.rs*, has parts of the functionality of the compiled binaries and was uploaded to VirusTotal on December 15 from an Algerian source. This prototype version of the ransomware is a simplified implementation and includes these functions:
- Encrypt all files on the user’s system (in the
C:\directory) using a combination of RSA and AES encryption. The original files are deleted after encryption, and encrypted versions with a new extension (.funksec) are created. - Create a ransom note (
readme.me) informing the user that their files have been encrypted and providing instructions for paying a ransom to obtain a decryption key. - Modify the system environment (e.g., changing the desktop background to black).
- Check for administrative/root privileges before executing.
Other free tools
In addition to the ransomware, the FunkSec group offers additional tools, most of them commonly associated with hacktivist activity.

- FDDOS, a Python “Scorpion DDoS Tool”, is a network stress-testing tool designed to perform Distributed Denial-of-Service (DDoS) attacks using either HTTP or UDP flood methods.
- JQRAXY_HVNC an HVNC Server and client C++ program is designed for remote desktop management, automation, and data interaction.
- funkgenerate is a smart password generation and scraping tool designed to scrape emails and potential passwords from given URLs and generate new password suggestions.
Associated Threat Actors
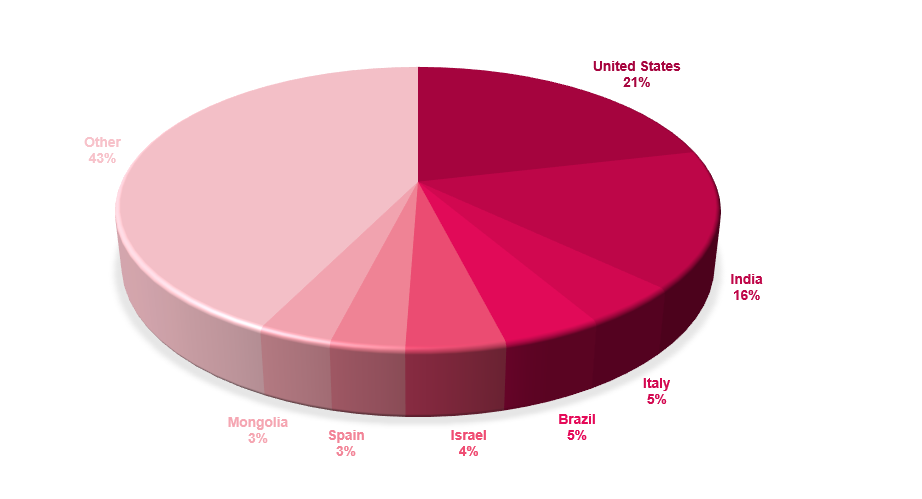
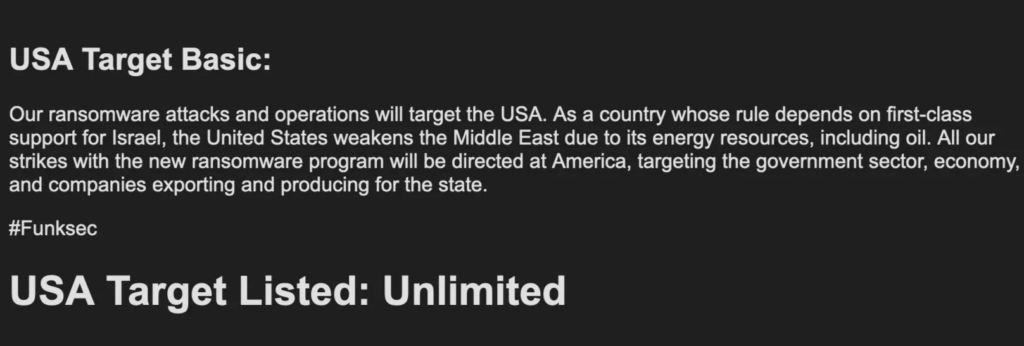
In late 2024, FunkSec emerged without warning and quickly dominated ransomware victim feeds and monitors, seemingly under the guise of hacktivism. By targeting India and the U.S., and aligning with the “Free Palestine” movement, the group leveraged multiple personas and aliases to craft its image and gain visibility.
Scorpion
Scorpion is the most prominent member of FunkSec and is associated with major portions of the group public profiles. This actor uses multiple aliases, most prominently DesertStorm.
The actor first surfaced on the Breached Forum, introducing the FunkSec name through a YouTube video posted via the channel “Scorpion” (@scorpioncybersec) in October 2024. The video alleged that FunkSec leaked a call between then-U.S. presidential candidate Donald Trump and Israeli Prime Minister Benjamin Netanyahu. However, the recording was clearly AI-generated.
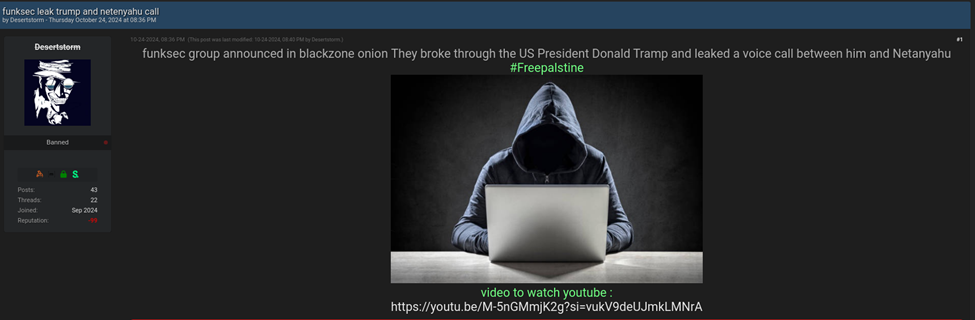
DesertStorm’s YouTube profile listed their location as Russia, though the video’s shared URL suggested it was uploaded from Brazil. DesertStorm continued posting leaks on Breached Forum—most unverified or not credited to FunkSec—until the account was banned in November 2024.
In one of DesertStorm’s posts, they inadvertently shared compromising screenshots that revealed their location to be Algeria, with French-language keyboard settings. A suspected associate, XTN, publicly alerted DesertStorm to this operational security (OpSec) lapse, but DesertStorm did not remove the compromising information.
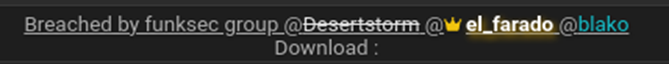
Before DesertStorm’s ban, the actor began tagging two other users, El_Farado and Blako, in forum posts related to FunkSec leaks and activities. While Blako remained inactive on the forums, El Farado gradually assumed a prominent role, promoting FunkSec on forums, sharing leaks, and adding the group’s .onion site to their signature.
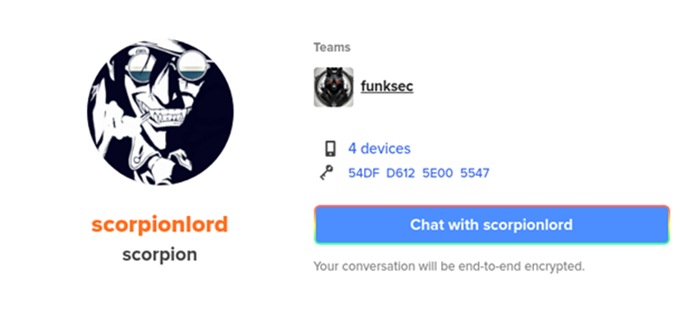
The actor is also linked to a Keybase account under the name “Scorpionlord,” where they are listed as the admin of FunkSec. This account is tied to the FunkSec shame site and DesertStorm’s user on Breached Forum. Scorpionlord is also the username on two other cybercrime forums where the FunkSec’s website was promoted (these users were since removed).
Notably, El Farado’s Keybase profile was registered on the same day as Scorpionlord’s, suggesting a coordinated effort. A third Keybase profile, Blako, was registered only a few days later, further supporting the idea that these personas were all closely linked.
El_farado
El Farado emerged as a key figure in FunkSec’s operations after DesertStorm’s ban from Breached Forum in November 2024. El Farado took on the task of promoting FunkSec, ensuring its visibility on the forum and sharing alleged leaks.
Key connections to FunkSec include:
- Tagged by DesertStorm: DesertStorm’s posts frequently tagged El Farado, linking them directly to FunkSec.
- Keybase Profile Registration: El Farado’s Keybase account was registered on the same day as Scorpionlord’s, implying a strong connection between the two personas.
- Promotional Activity: El Farado actively promoted FunkSec’s .onion site on Breached Forum and shared leaks (often unreliable or recycled).
- Rookie Behavior: El Farado occasionally posted threads asking basic hacking questions like “What do hackers do with leaked data?” This behavior suggests inexperience, corroborating some Scorpion’s admission of the group’s lack of technical know-how.
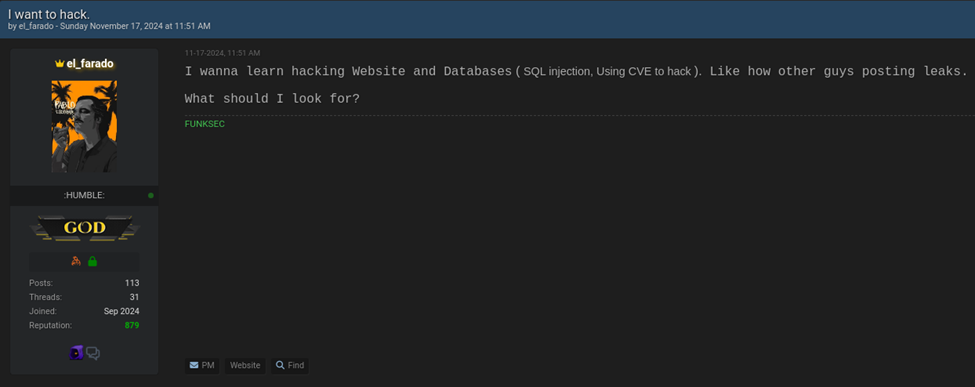
XTN
XTN is associated with FunkSec’s “data sorting” service advertised on their website, while this service’s purpose is not fully clear. Their Keybase account, “xtnn,” connects to their Breached Forum profile, where they describe their location as “El Farado’s room” and reference El Farado in their signature. XTN further solidified their link to FunkSec by publicly warning DesertStorm about their OpSec lapse.
Bjorka
Bjorka, a known Indonesian hacktivist, has a murkier connection to FunkSec. While leaks attributed to FunkSec were reposted by a user named Bjorka on DarkForums, no direct collaboration was verified. Additionally, a Telegram channel named “Bjorkanism” claimed credit for some FunkSec operations, referring to them as “Bjorkanism Ransomware (FunkSec).” These claims are not supported by Bjorka’s official platforms, suggesting attempts at impersonating Bjorka or at most, a loose affiliation.
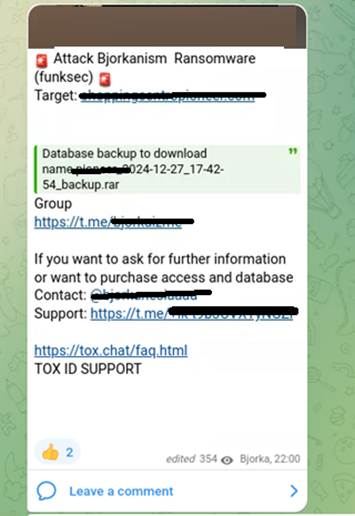
Related Hacktivist Groups
FunkSec attempted to associate itself with several defunct hacktivist groups:
- Ghost Algéria: Referenced in a ransomware note nearly identical to FunkSec’s.
- Cyb3r Fl00d: A defacement screenshot from this group was included in FunkSec-related activity, with FunkSec claiming Cyb3r Fl00d was their “old group.”
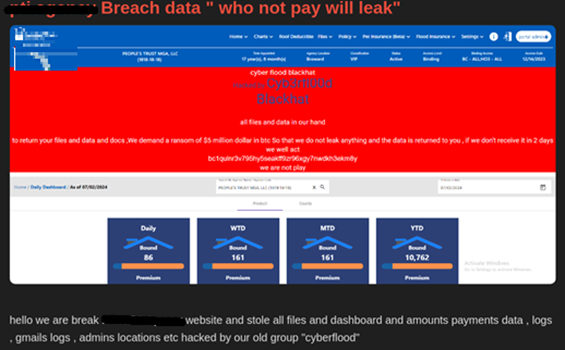
These associations likely represent attempts to boost FunkSec’s credibility by aligning with well-known names rather than direct membership or collaboration.
AI-Assisted capabilities
The individuals behind FunkSec appear to have extensively leveraged AI to enhance their capabilities, as evidenced by their publications and tools. Their public script offerings include extensive code comments with perfect English (as opposed to very basic English in other mediums), likely generated by an LLM agent. Similar patterns are visible in the Rust source code linked to the group’s ransomware, suggesting it may have been developed with AI assistance.
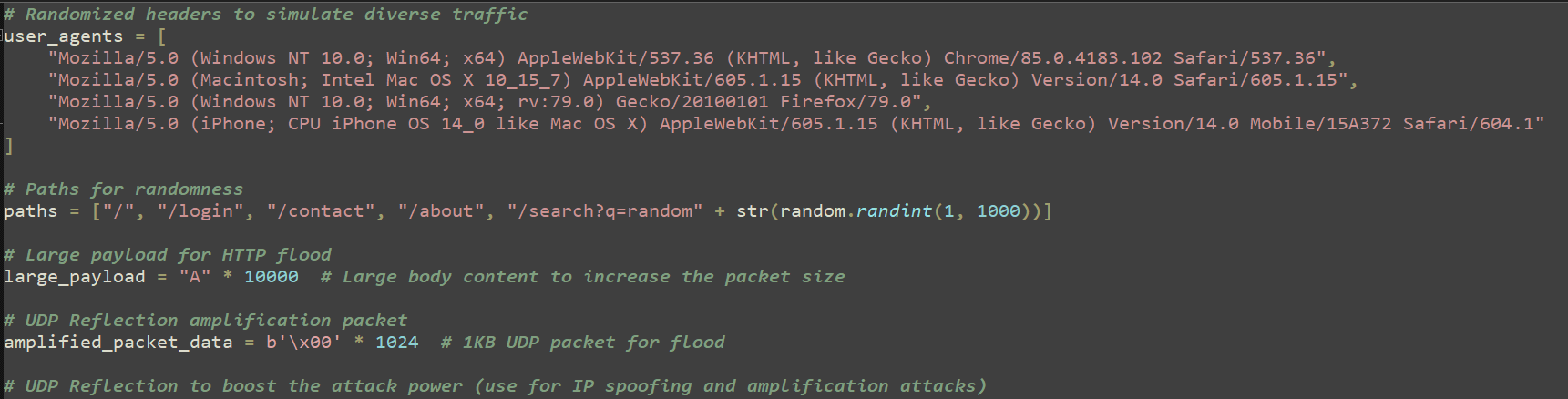
In some of their published messages, the group specifically linked the development of their ransomware to AI-assisted agents, likely providing it with the source code for the ransomware and simply shared the output on their site.
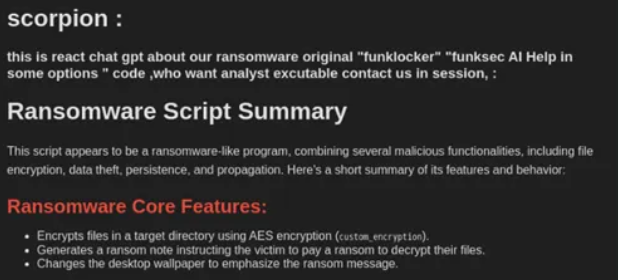
The use of such tools aligns closely with the group’s public claims, as they also released an AI chatbot based on Miniapps to support their operations. Miniapps is a platform that facilitates the creation and use of AI applications and chatbots, often without the restrictions found in more popular systems like ChatGPT. The bot developed by FunkSec is specifically designed to support malicious activities.
Technical Analysis
To better understand the malware, we examined one of the circulated samples. This is a stripped Rust binary, which makes it challenging to effectively reverse engineer. In particular, it is subject to aggressive in-lining of library code (see our previous publication, Inside Akira Ransomware’s Rust Experiment for a clear demonstration of how this works, and how this complicates reverse engineering tasks), and contains many trait implementations that a disassembler may not recognize out of the box, many of which are wrappers for e.g. WriteFileEx or CryptGenRandom. However, a careful analysis reveals some interesting details.
Overall, we were mainly struck by the amount of redundancy in the binary. Control flow seems to repeat itself and call functions again and again from various execution paths; in a typical ransomware, these would only be called once. For example, in this sequence of operations:
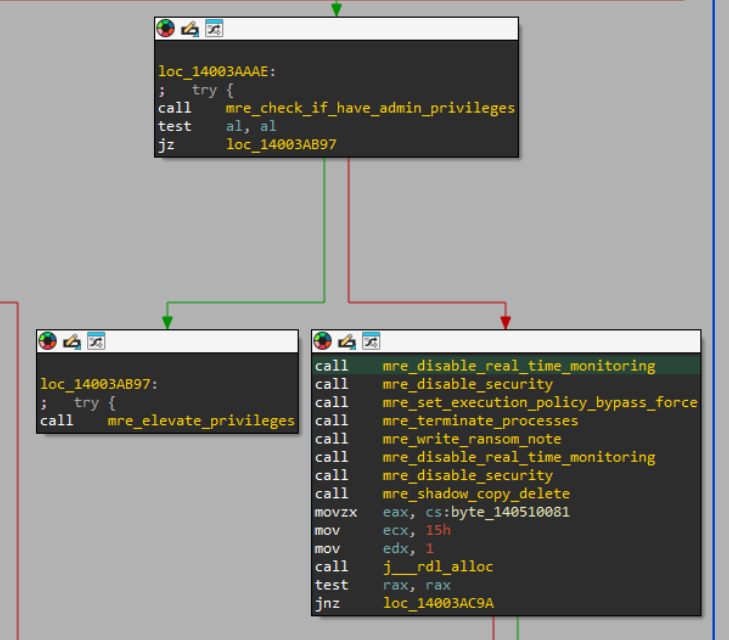
Across the entire binary many of these functions are called twice, or even three or four times; the ‘disable security’ routine, seen above, is called twice in the same basic block. The below recursive function, which iterates into all subdirectories of a given directory and encrypts the targeted files in it, is called a total of five times across the binary.
Some of the repetition is due to duplicated code that invokes the ‘encrypt all directories’ logic with different hardcoded constants each time, such as this invocation that uses the constant RansomwarePassword123:
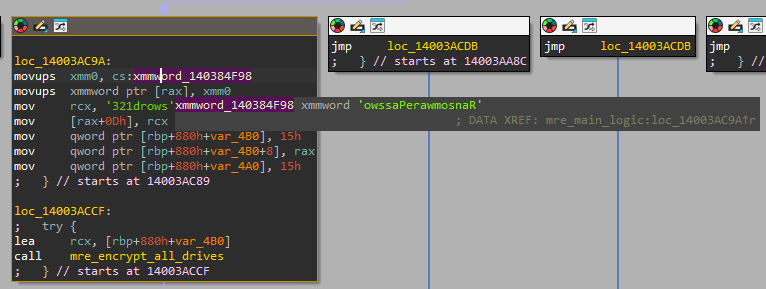
RansomwarePassword123 constant in the code.Aside from the duplicated functionality, the main execution flow of the malware first calls the operations sequence seen earlier (“disable security”, and so on) and then transfers execution to an ‘encrypt all drives’ function. The operations sequence begins by checking whether it has elevated privileges (by trying to execute net session). If not, the binary attempts to relaunch itself with elevated privileges, using the method described here (start-process -wait -Verb runas -filepath '%~nx0' -ArgumentList '<arguments>').
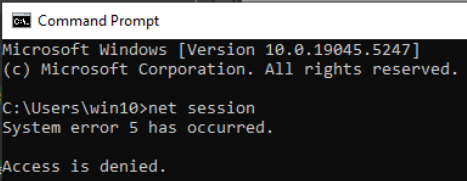
net session without elevated privileges.Once it has elevated privileges, the malware executes the following commands:
| Command | Functionality |
Set-MpPreference -DisableRealtimeMonitoring $true | Disable Windows Defender real-time protection. |
wevtutil sl Security /e:false | Disable Security event logging. |
wevtutil sl Application /e:false | Disable Application event logging. |
Set-ExecutionPolicy Bypass -Scope Process -Force | Disable restrictions placed by the Powershell execution policy. |
vssadmin delete shadows /all /quiet | predictably, delete shadow copy backups. |
The terminate_processes function contains a hardcoded list of processes and services to terminate:
| chrome.exe | firefox.exe | msedge.exe | explorer.exe | outlook.exe | vlc.exe |
| spotify.exe | skype.exe | discord.exe | steam.exe | java.exe | python.exe |
| node.exe | cmd.exe | powershell.exe | taskmgr.exe | wmplayer.exe | tscon.exe |
| notepad.exe | spooler | bits | dnsclient | lanmanworkstation | winmgmt |
| netsh | iphlpsvc | wuauserv | RemoteAccess | ShellHWDetection | SCardSvr |
| TrkWks | wscsvc | CryptSvc | msiserver | MpsSvc | defragsvc |
| upnphost | WindowsUpdate | srservice | wsmprovhost | AppIDSvc | AudioEndpointBuilder |
| Schedule | eventlog | PlugPlay | Netman | bthserv | ShellExperienceHost |
| SMB | WinDefend |
Next, the malware moves on to iterating over each letter drive, recursing through its subdirectories and encrypting each file with one of the targeted extensions. For file encryption, the symmetric encryption used is the chacha20 implementation available in the orion.rs crate. Ephemeral keys are generated using a thin wrapper for CryptGenRandom (and the descriptively-named SystemFunction036). The newly created filename, with the hardcoded .funksec extension, is created using a call to Rust’s format! macro.
The malware then writes to disk the (rather emoji-fied) ransom note.
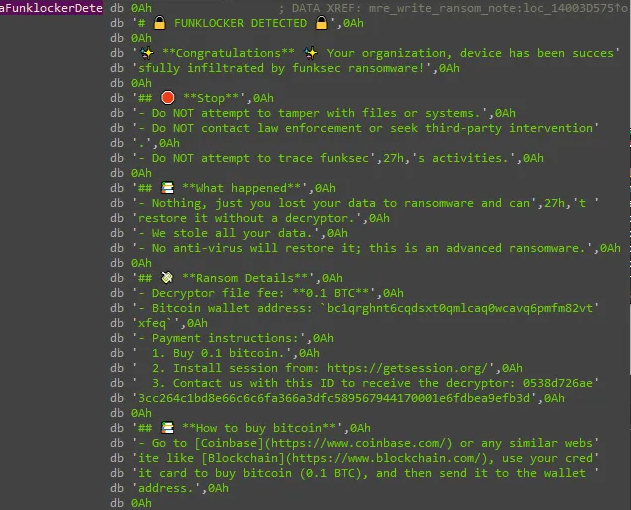
Summary
This report provides an in-depth analysis of FunkSec, a ransomware group with apparent hacktivist tendencies. The custom encryptor, developed by an inexperienced Algerian author, features AI-assisted elements which enables rapid development and improvement. FunkSec’s data leaks often recycle information from previous hacktivist campaigns, casting doubt on the authenticity of their claims. Despite these limitations, their Tor-based operations and low ransom demands have drawn widespread attention in cybercrime forums.
FunkSec’s operations highlight the role of AI in malware development, the overlap between hacktivism and cybercrime, and the challenges in verifying leaked data. It also raises questions about how we assess the threat posed by ransomware groups, as we often rely on the groups’ own claims. These findings reflect a changing threat landscape, where even low-skill actors can make use of accessible tools to cast a very large shadow.
Harmony Endpoint provides comprehensive endpoint protection at the highest security level, crucial to avoid security breaches and data compromise and protects against this threat.
IOCs:
c233aec7917cf34294c19dd60ff79a6e0fac5ed6f0cb57af98013c08201a7a1c 66dbf939c00b09d8d22c692864b68c4a602e7a59c4b925b2e2bef57b1ad047bd dcf536edd67a98868759f4e72bcbd1f4404c70048a2a3257e77d8af06cb036ac b1ef7b267d887e34bf0242a94b38e7dc9fd5e6f8b2c5c440ce4ec98cc74642fb 5226ea8e0f516565ba825a1bbed10020982c16414750237068b602c5b4ac6abd e622f3b743c7fc0a011b07a2e656aa2b5e50a4876721bcf1f405d582ca4cda22 20ed21bfdb7aa970b12e7368eba8e26a711752f1cc5416b6fd6629d0e2a44e5d dd15ce869aa79884753e3baad19b0437075202be86268b84f3ec2303e1ecd966 7e223a685d5324491bcacf3127869f9f3ec5d5100c5e7cb5af45a227e6ab4603





