

Research by: Jaromír Hořejší (@JaromirHorejsi)
Key Points
- AI media generation is a significant trend in how we use the Internet in 2025. Kling AI is a widely used platform, with 6 million users since its launch in June 2024.
- A threat actor mimicked Kling AI and drove traffic to a convincing fake website via counterfeit Facebook pages and paid ads.
- User submissions of a text prompt or image on this fake site produce a seemingly innocent media file whose filename uses Hangul Filler characters to conceal an executable.
- In some cases, the executable’s loader used .NET Native AOT compilation for stealth. Executing it installs an infostealer with monitoring capabilities.
- This campaign has a global reach, with victims reported across multiple regions, most notably in Asia.
Introduction
In early 2025, Check Point Research (cp<r>) started tracking a threat campaign that abuses the growing popularity of AI content generation platforms by impersonating Kling AI, a legitimate AI-powered image and video synthesis tool. Promoted through Facebook advertisements, the campaign directs users to a convincing spoof of Kling AI’s website, where visitors are invited to create AI-generated images or videos directly in the browser.
Instead of delivering a media file, the site offers a malicious “image or video output” for download. These files carry extensions like .mp4 or .jpg but in reality are disguised Windows executables using double extensions and Hangul Filler characters to obscure their true nature in the filesystem and file dialogs.
Users expecting to preview their generated video instead unknowingly launched a loader. In several instances, this executable utilized .NET Native AOT (Ahead-Of-Time) Compilation to complicate analysis and evade many traditional detection techniques. Once executed, the loader staged and deployed follow-up payloads—primarily infostealers to exfiltrate browser-stored credentials, session tokens, and other sensitive data.
In our report, we detail the campaign’s end-to-end kill chain—from the initial lure to payload execution—and focus on the technical mechanisms used for file masquerading, obfuscation, and staged delivery. We analyze the loader’s internals and behavioral footprint and highlight the evolving techniques used to exploit trust in generative AI workflows.
Infection Chain
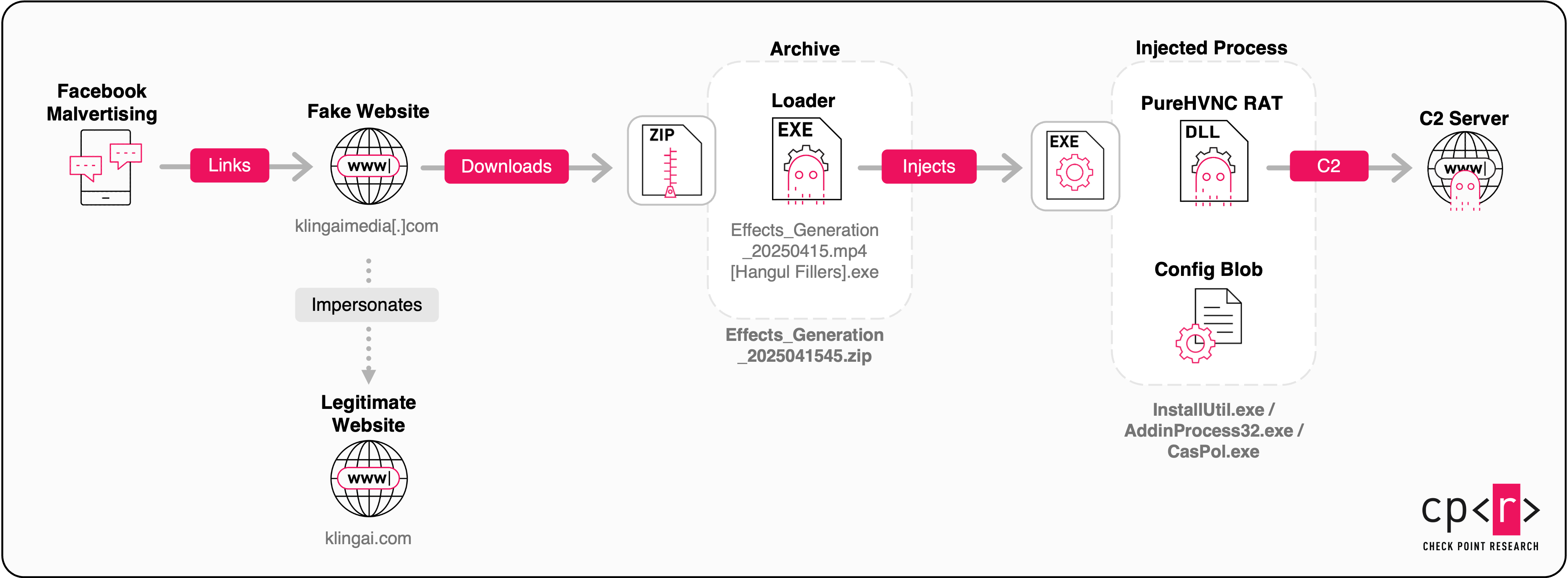
Figure 1 – Fake Kling AI’s Infection Chain.
The campaign, which began in early 2025, uses an infection chain that starts with social media malvertising. To date, we identified approximately 70 promoted posts from fake social media pages impersonating Kling AI.
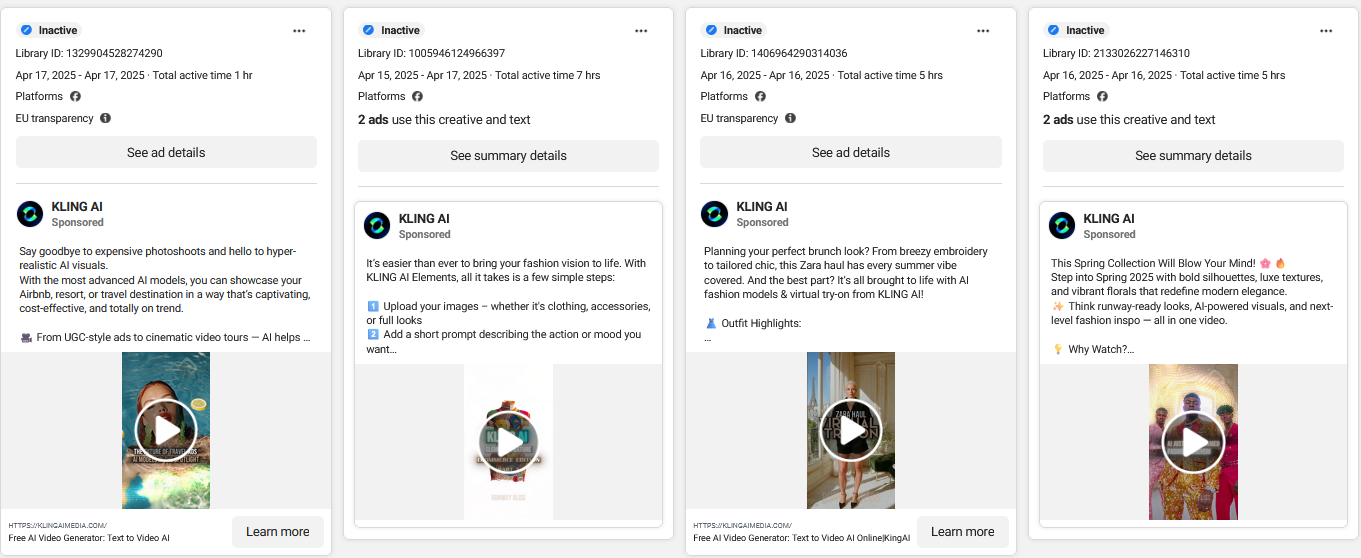

The fake Facebook page contains posts with text and media, together with a link to promote the fake AI generation websites (e.g., klingaimedia[.]com) which are designed to look like a realistic version of the “Kling AI” tool.
When users access the fake AI webpage, they are expected to perform an image-related action such as uploading an image to one of the sub-pages (images, effects, etc.), clicking the “Generate” button, and then waiting for the AI tool to generate results.

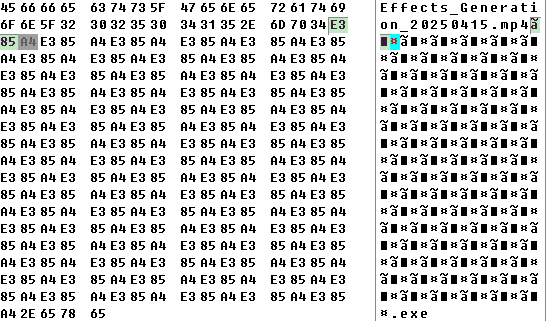
The generated result is a zip archive containing a single .exe file. However, the unzipped filename length is 292 bytes. When viewed in a hex editor, each space character is represented by three bytes 0xE3 0x85 0xA4, a UTF-8 hex encoding for Hangul Filler.
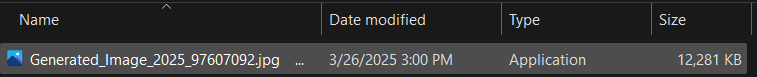
In the default Windows Explorer view, this file is presented as if it were an image due to its deceptive name (Generated_Image_2025_97607092.jpg ...), with the ellipsis (...) subtly hinting that the filename is longer than displayed. Despite appearing like a media file (even showing an image-like icon), the Type column explicitly classifies this file as an Application, exposing its true nature as an executable. This is a classic case of filename masquerading, exploiting long filenames to obscure dangerous file types from users at first glance.
While we observed different types of first-stage loaders, most of them were developed in .NET. The purpose of these loaders is to avoid running in a virtual environment, establishing persistence and performing remote injection of the second stage payload.
One of the loaders written in .NET is noteworthy as it was compiled using Native AOT format, resulting in a file containing no CIL (Common Intermediate Language) code, only machine code. The file should be a few MBs in size, but is inflated by appending some tens of MBs of useless data. A valid or invalid signature is also often appended to the binary.
The developers did not successfully cover all of their tracks and some interesting strings are visible in the loader:
$antiprocesshacker $antivt $melt $persistence $startup
This particular loader employs several anti-analysis tricks, notably by monitoring for analysis tools such as Wireshark, OllyDbg, Procmon, ProcExp, PeStudio, Fiddler, and others. For persistence, the loader sets up a run key in the registry and copies its loader file to a hardcoded path within the %APPDATA%\Local directory. After establishing persistence, it injects the 2nd stage into hardcoded legitimate system processes like InstallUtil.exe, AddInProcess32.exe or CasPol.exe to evade detection.
Reverse engineering the Native AOT binary can be challenging. However, with the help of tools like Washi1337’s plugin for Ghidra, string annotations can be automatically added to the decompiled view.

As you can see from Figure 10 above, the string “$antivt”(anti – virtual)issearchedintheloader’shardcodedconfiguration(“$startup,antivt,antiprocesshacker”), and if found, the loader tests whether it is running in a virtual environment.
Next, the loader checks for the presence of the relevant parameters “$startup” (copy to `%APPDATA%\\Local`, set Run registry persistence), “$melt” (a.k.a. self-delete), and “$persistence” (batch file with endless loop, which restarts the loader every minute, if not present). If present in the configuration, the corresponding method is executed. After successfully passing all the checks, the last function is injecting to the process.
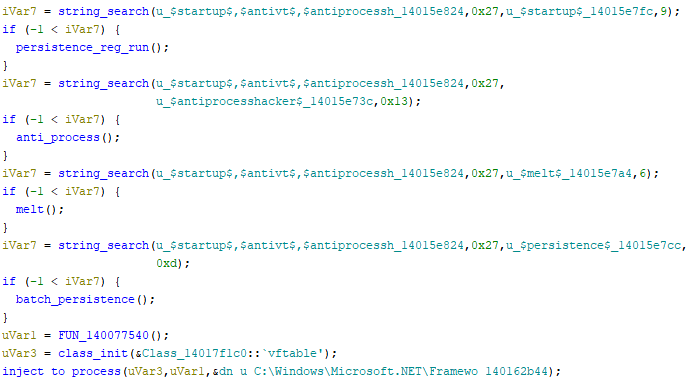
The loader defines an array of 19 names belonging to the analysis processes ($antiprocesshacker). If any of these programs are found running in the memory, the loader immediately exits and does not run the next stage.
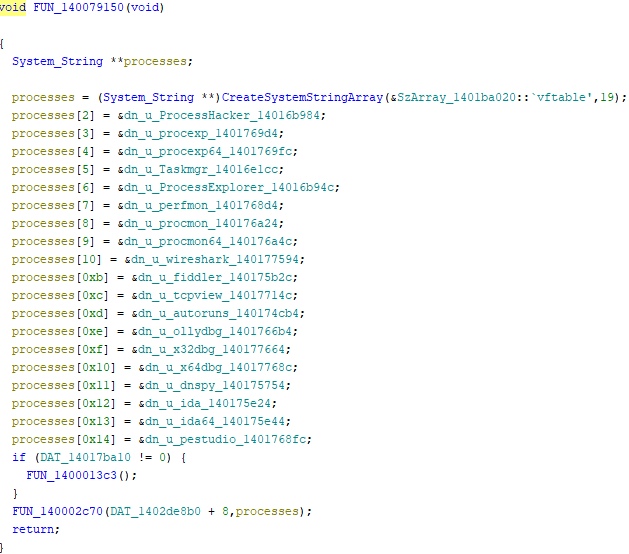
Stage 2 – PureHVNC RAT + Stealer
The second stage is also written in .NET and is usually obfuscated with .NET Reactor. After deobfuscation, PureHVNC Remote Access Trojan (RAT) is the main payload.
All the second-stage samples we analyzed were DLL files with only one public class and exactly one public static method – the intended entry point. Running this method does not require any parameters. We found that the names of classes and methods changed from sample to sample. In some samples, the DeclaringType of this method includes a reference to the PureHVNC Remote Access Trojan (RAT), e.g., PureHVNC_Lib.Iterators.IteratorExecutor.
The most important information is an encoded configuration shown below:
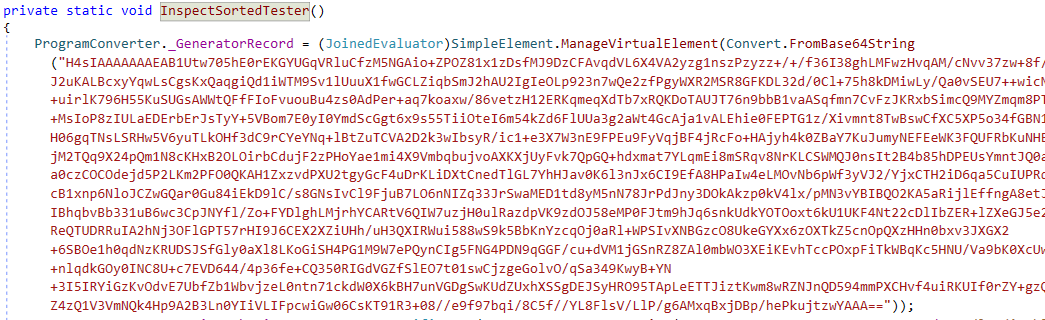
After decoding and decompressing (gzip) the configuration blob, we can immediately see the C2 (Command and Control) IP address, campaign ID, and other information such as the encoded embedded certificate.

- King AI 20/1/2025
- King AI 6/3
- Kling AI 25/03/2025
- KlingAI Home
- Kling AI Test Startup
- Kling AI
- Kling AI New
- GG Kling AI
As you can see from the campaign ID names, some contain a date which is likely when that particular sub-campaign started. Others may include the keyword ‘test’, suggesting the actors were testing new versions.
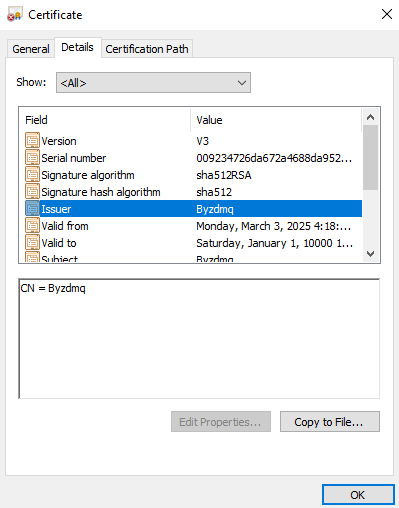
Base64-encoded string (part of the decoded configuration blob) starting with MIIE represents an embedded certificate; CN = Byzdmq.
The RAT also implements extensive stealing capabilities, which include monitoring many browser extensions:
{ "ibnejdfjmmkpcnlpebklmnkoeoihofec", "TronLink" },
{ "nkbihfbeogaeaoehlefnkodbefgpgknn", "MetaMask" },
{ "fhbohimaelbohpjbbldcngcnapndodjp", "Binance Chain Wallet" },
{ "ffnbelfdoeiohenkjibnmadjiehjhajb", "Yoroi" },
{ "cjelfplplebdjjenllpjcblmjkfcffne", "Jaxx Liberty" },
{ "fihkakfobkmkjojpchpfgcmhfjnmnfpi", "BitApp Wallet" },
{ "kncchdigobghenbbaddojjnnaogfppfj", "iWallet" },
{ "aiifbnbfobpmeekipheeijimdpnlpgpp", "Terra Station" },
{ "ijmpgkjfkbfhoebgogflfebnmejmfbml", "BitClip" },
{ "blnieiiffboillknjnepogjhkgnoapac", "EQUAL Wallet" },
{ "amkmjjmmflddogmhpjloimipbofnfjih", "Wombat" },
{ "jbdaocneiiinmjbjlgalhcelgbejmnid", "Nifty Wallet" },
{ "afbcbjpbpfadlkmhmclhkeeodmamcflc", "Math Wallet" },
{ "hpglfhgfnhbgpjdenjgmdgoeiappafln", "Guarda" },
{ "aeachknmefphepccionboohckonoeemg", "Coin98 Wallet" },
{ "imloifkgjagghnncjkhggdhalmcnfklk", "Trezor Password Manager" },
{ "oeljdldpnmdbchonielidgobddffflal", "EOS Authenticator" },
{ "gaedmjdfmmahhbjefcbgaolhhanlaolb", "Authy" },
{ "ilgcnhelpchnceeipipijaljkblbcobl", "GAuth Authenticator" },
{ "bhghoamapcdpbohphigoooaddinpkbai", "Authenticator" },
{ "mnfifefkajgofkcjkemidiaecocnkjeh", "TezBox" },
{ "dkdedlpgdmmkkfjabffeganieamfklkm", "Cyano Wallet" },
{ "aholpfdialjgjfhomihkjbmgjidlcdno", "Exodus Web3" },
{ "jiidiaalihmmhddjgbnbgdfflelocpak", "BitKeep" },
{ "hnfanknocfeofbddgcijnmhnfnkdnaad", "Coinbase Wallet" },
{ "egjidjbpglichdcondbcbdnbeeppgdph", "Trust Wallet" },
{ "hmeobnfnfcmdkdcmlblgagmfpfboieaf", "XDEFI Wallet" },
{ "bfnaelmomeimhlpmgjnjophhpkkoljpa", "Phantom" },
{ "fcckkdbjnoikooededlapcalpionmalo", "MOBOX WALLET" },
{ "bocpokimicclpaiekenaeelehdjllofo", "XDCPay" },
{ "flpiciilemghbmfalicajoolhkkenfel", "ICONex" },
{ "hfljlochmlccoobkbcgpmkpjagogcgpk", "Solana Wallet" },
{ "cmndjbecilbocjfkibfbifhngkdmjgog", "Swash" },
{ "cjmkndjhnagcfbpiemnkdpomccnjblmj", "Finnie" },
{ "dmkamcknogkgcdfhhbddcghachkejeap", "Keplr" },
{ "kpfopkelmapcoipemfendmdcghnegimn", "Liquality Wallet" },
{ "hgmoaheomcjnaheggkfafnjilfcefbmo", "Rabet" },
{ "fnjhmkhhmkbjkkabndcnnogagogbneec", "Ronin Wallet" },
{ "klnaejjgbibmhlephnhpmaofohgkpgkd", "ZilPay" },
{ "ejbalbakoplchlghecdalmeeeajnimhm", "MetaMask" },
{ "ghocjofkdpicneaokfekohclmkfmepbp", "Exodus Web3" },
{ "heaomjafhiehddpnmncmhhpjaloainkn", "Trust Wallet" },
{ "hkkpjehhcnhgefhbdcgfkeegglpjchdc", "Braavos Smart Wallet" },
{ "akoiaibnepcedcplijmiamnaigbepmcb", "Yoroi" },
{ "djclckkglechooblngghdinmeemkbgci", "MetaMask" },
{ "acdamagkdfmpkclpoglgnbddngblgibo", "Guarda Wallet" },
{ "okejhknhopdbemmfefjglkdfdhpfmflg", "BitKeep" },
{ "mijjdbgpgbflkaooedaemnlciddmamai", "Waves Keeper" }
The browser extensions mentioned above may be installed in different directories, based on the installed Chromium-based browser. The list below shows the targeted browsers:
dictionary.Add("Chromium\\User Data\\", "Chromium");
dictionary.Add("Google\\Chrome\\User Data\\", "Chrome");
dictionary.Add("Google(x86)\\Chrome\\User Data\\", "Chrome");
dictionary.Add("BraveSoftware\\Brave-Browser\\User Data\\", "Brave");
dictionary.Add("Microsoft\\Edge\\User Data\\", "Edge");
dictionary.Add("Tencent\\QQBrowser\\User Data\\", "QQBrowser");
dictionary.Add("MapleStudio\\ChromePlus\\User Data\\", "ChromePlus");
dictionary.Add("Iridium\\User Data\\", "Iridium");
dictionary.Add("7Star\\7Star\\User Data\\", "7Star");
dictionary.Add("CentBrowser\\User Data\\", "CentBrowser");
dictionary.Add("Chedot\\User Data\\", "Chedot");
dictionary.Add("Vivaldi\\User Data\\", "Vivaldi");
dictionary.Add("Kometa\\User Data\\", "Kometa");
dictionary.Add("Elements Browser\\User Data\\", "Elements");
dictionary.Add("Epic Privacy Browser\\User Data\\", "Epic Privacy");
dictionary.Add("uCozMedia\\Uran\\User Data\\", "Uran");
dictionary.Add("Fenrir Inc\\Sleipnir5\\setting\\modules\\ChromiumViewer\\", "Sleipnir5");
dictionary.Add("CatalinaGroup\\Citrio\\User Data\\", "Citrio");
dictionary.Add("Coowon\\Coowon\\User Data\\", "Coowon");
dictionary.Add("liebao\\User Data\\", "liebao");
dictionary.Add("QIP Surf\\User Data\\", "QIP Surf");
dictionary.Add("Orbitum\\User Data\\", "Orbitum");
dictionary.Add("Comodo\\Dragon\\User Data\\", "Dragon");
dictionary.Add("Amigo\\User\\User Data\\", "Amigo");
dictionary.Add("Torch\\User Data\\", "Torch");
dictionary.Add("Comodo\\User Data\\", "Comodo");
dictionary.Add("360Browser\\Browser\\User Data\\", "360Browser");
dictionary.Add("Maxthon3\\User Data\\", "Maxthon3");
dictionary.Add("K-Melon\\User Data\\", "K-Melon");
dictionary.Add("Sputnik\\Sputnik\\User Data\\", "Sputnik");
dictionary.Add("Nichrome\\User Data\\", "Nichrome");
dictionary.Add("CocCoc\\Browser\\User Data\\", "CocCoc");
dictionary.Add("Uran\\User Data\\", "Uran");
dictionary.Add("Chromodo\\User Data\\", "Chromodo");
dictionary.Add("Mail.Ru\\Atom\\User Data\\", "Atom");
The RAT also monitors Paths / Registry Keys related to the following programs. These are standalone programs and NOT browser extensions.
Atomic Wallet Bitcoin-Qt Dash-Qt Electrum Ethereum Exodus Jaxx Litecoin-Qt Zcash Foxmail Telegram Ledger Live
Plugin – PluginWindowNotify
PureHVNC has several different plugins. During our research, we observed just one of them, a plugin named PluginWindowNotify, which monitors foreground windows and takes screenshots.
The analysis of its code reveals the plugin’s primary responsibilities: monitoring opened windows, getting their captions, and if an interesting keyword in the caption is found, taking a screenshot and notifying its operators.
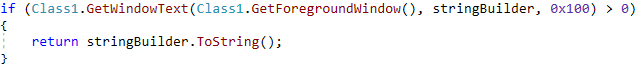
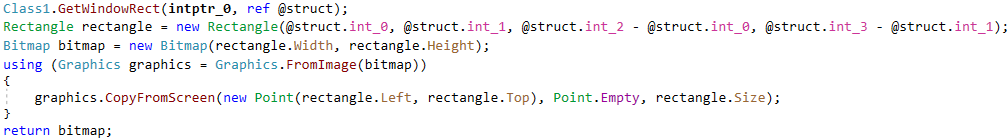
Not surprisingly, this plugin does not notify the operators about all the windows. It contains a list of “interesting” keywords (crypto wallets, banks), and only those are reported back to the operators. A list of monitored window captions is shown below.
coinbase metamask atomic wallet atomicwallet Prosperity Bank Montepio Novobanco Eurobic ABANCA Credito agricola Revolut Santander Bankinter Moey Banco ctt Caixa geral de depósitos Openbank wellsfargo banco bbva banco bac banco av villas banco GNB banistmo banco general bank of america chase bank caixabank gemini.com Gate.io trustwallet gemini.com/exchange Banco pan Brandesco Banco do Brasil Unibanco Banco do Nordeste Banco inter Bybit Poloniex Banco Santander Nubank Truist Bank JP Morgan Chase Citigroup Goldman Sachs usbank HSBC Lloyds Bank Santander UK Virgin Money UK Metro Bank Starling Bank bbva Banco de Bogotá Itaú Corpbanca Colômbia Bancolombia Citibank Colômbia GNB Sudameris BBVA Colômbia Colpatria Banco de Occidente Banco Caja Social Banca Agricola Popolare UniCredit Sanpaolo IMI Intesa Sanpaolo Banco di Napoli Banco da Itália Banco Ambrosiano Banca Sella Group Banca Monte dei Paschi di Siena FinecoBank Banco Ficohsa Banco BBP Banco Azteca Banco Aliado Banco BCT Bank International Banco Bi-Bank Banco General Panamá Caja de Ahorros Banco Davivienda binance exodus paypal facebook ads google ads westernunion Huntington dkb bank dkb.de
Evolution
When searching for previous malvertising campaigns impersonating Kling AI, we found several suspicious, similar-looking websites.
klingxai[.]com kingaitext[.]com ai-kling[.]com klings-ai[.]com klingx[.]ai klingxai[.]com www[.]kling-ai[.]tech www[.]klingai[.]cloud
Most of the websites were already down at the time of our investigation. However, two websites that were still up required similar interactive behavior from the victims. In the case of aikling[.]ai, the loader also generated a payload with a similar naming convention. These two still active campaigns distribute ScreenConnect and were previously reported by security researchers.
aikling[.]ai hxxps[://]aikling[.]ai/Create_standard_mode_photo[.]zip klingturbo[.]com hxxps[://]klingturbo[.]com/images/ai-images/Image_Generation_158666[.]jpg - klingturbo[.]com
Attribution
Facebook malvertising and distributing information stealers have been a favorite technique of Vietnamese threat actors for some time. Researchers who analyzed other LLM/AI themed malvertising campaigns also reported the malware contained variable or field names in the Vietnamese language, as documented here and here.
Not surprisingly, this current campaign included several references (like debug messages) in the Vietnamese language.
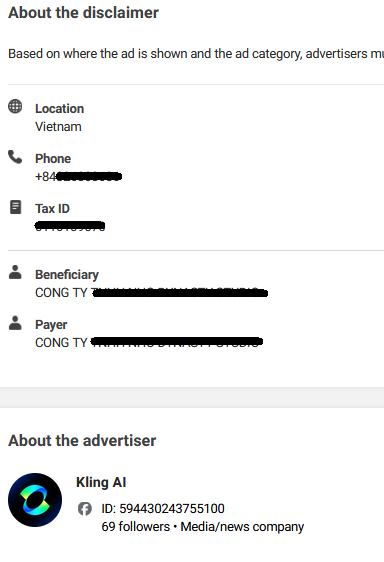
Some advertisers specify their location in Vietnam and include a Vietnamese mobile number. In some cases, the beneficiary and payer have Vietnamese names.
Protections
Check Point Harmony Endpoint and Threat Emulation provide comprehensive coverage of attack tactics, file types, and operating systems and protect against the attacks and threats described in this report.
IOCs
Stage 1 – Loaders (SHA-256):
F5B31BD394E0A3ADB6BD175207B8C3CCC51850C8F2CEE1149A8421736168E13E F89298933FED52511BB78F8F377979190E37367D72CCF4F3B81374A70362CC42 BEEEA592251A0A205B3BDB34802BD2F4F5181EE38226A05EC468A86BE44E9508 732AA8ED8CA9A12F4BFC29A693EC3EBA74ED1B2D00DE4296180D91B86D09747B 7035B5BA24146DB537EEDB1F05E6CAD1775F9F5E81306F72422C03B288F75448 30E26F4FD7CB0AC626950BB01E01A2C02E277727D1D3EC94286A44AF262F37CF 2588FDFA7417D617DF2D31EDDEA710D0F964008ABC2F4860CDFF588AB9786D0A 06D9D60DDBE835ABC5B16911A35732CC9B56EA9425DE210961A15D465823978F 2D5E01CFACDF9F900B51B0539E0809F22CE1859EAC0886866AF35A2EB2DC2D42 5200B27726C0BE8E6F34A3920FBD5D40AEAEC460169B1F3C7A174EBEEE6553D9 699E348260AE5B60CD822325F1C4BF2C793F6F25001357856C58520A9AF10987 D95B3EABFE9892371CB518FD6E733D2D33D2FABB2B1DF4DAB650A8F8E1EA8745 D1B712B215612C8DF5FEF02B614C616A78B723BFFBEC6E10E32BFD0B758DF41B 39D771C12BD5DA15D3FB63905DF1E2C4C7C12B8F77C630A35B247C418950EAFE 4BBAF3ECECD53BC4028723E87B1669268A6FADC4D480590C2D59BB4322A17DE7
Stage 2 – PureHVNC (SHA-256):
B33E162A78B7B8E7DBBAB5D1572D63814077FA524067CE79C37F52441B8BD384 0C9228983FBD928AC94C057A00D744D6BE4BD4C1B39D1465B7D955B7D35BF496 839371CD5A5D66828AC9524182769371DEDE9606826AD7C22C3BB18FB2EE91CB 9DAB2BADFDAE86963B2F13CE8942FE78DD66EC497F8D82DD40C0CB5BEC4FB2A7 CEE3F98B5F175219D025A92EDDEC4FD8BCAAE31E6AD99321AE7C00B822063FC3 A5BACEB97A2BE17FDD0C282292EBB0B5A56A555013A4C8FFFCC2335C504780FB 3FBA4A0942244E9C3AD25A57A21F91B06F8732A2CA36DA948AE5F0AFA51DC72B 557BECFCC7ECCAA5A7368A6D5583404AF26AADEDE2C345D6070E6E9FAB44A641
Plugins (SHA-256):
1E66EBAEF295C2A32245162979D167CEBAD1FECE51B7CDB6A6C3A1D705BEFA6B
Fake website + Fake Facebook pages:
klingaimedia[.]com https://www.facebook[.]com/61574724896485/ https://www.facebook[.]com/61574162357787/ klingaistudio[.]com https://www.facebook[.]com/people/KLING-AI/61574316153107/ klingaieditor[.]com kingaimediapro[.]com kingaivideotext[.]com kingaiplus[.]com
C2 IPs:
185.149.232[.]197 185.149.232[.]221 147.135.244[.]43





