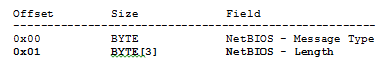Background
Rarely does the release of an exploit have such a large impact across the world. With the recent leak of the NSA exploit methods, we saw the effects of powerful tools in the wrong hands. On April 14, 2017, a group known as the Shadow Brokers released a large portion of the stolen cyber weapons in a leak titled, “Lost in Translation.” This leak contained many exploits, some of which were already patched a month earlier in the Microsoft SMB critical security update (MS17-010). However, many users were unable to update their systems. Even before WannaCry hit, more than 400,000 computers in approximately 150 countries were infected with one of the tools, called DoublePulsar. It is unknown if this wave of infections was carried out by a single or multiple attackers. What is known is that this paved the way for the delivery, in May 2017, of the ransomware attack known as WannaCry.
There has not been such a large scale exploit on a Server Message Block (SMB) since Conficker in 2008. Often turned on by default, SMB is a widely used system for transferring files. In our Brokers in the Shadows report, we will explore the SMB protocol and dive into the mechanisms through which these cyber tools were able to launch their attack. We will also detail many of the tools in the release such as SMBTouch, EternalBlue, and DoublePulsar, along with EternalRocks which wraps these tools into a singular exploit suite.
Finally, we will demonstrate how IPS protected our customers on day zero.
SMB Basics
Windows Client systems use the Common Internet File System Protocol (CIFS) to request file and print services from server systems over a network.
The CIFS Protocol extends the Server Message Block (SMB) Protocol with additional security, file, and disk management support. These extensions introduce new flags, extended requests and responses, and new information levels. All of these extensions follow a request/response pattern in which the client initiates all of the requests. The exception to this pattern is oplock break.
There are three SMB protocol versions, all of which are run over TCP ports 139 and 445. On a given connection, the SMB version used is decided in the following manner:
| Client / Server OS | Windows 8 Windows Server 2012 |
Windows 7 Windows Server 2008 R2 |
Windows Vista Windows Server 2008 |
Previous versions of Windows |
| Windows 8 Windows Server 2012 |
SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 7 Windows Server 2008 R2 |
SMB 2.1 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows Vista Windows Server 2008 |
SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 1.0 |
| Previous versions of Windows |
SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 |
Each SMB message is preceded by a NetBIOS Session Service information block with the following structure:
The message consists of three parts:
- Fixed-length header
- Variable-length parameters block
- Variable-length data block
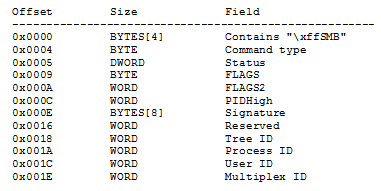
An SMB message header is 32 bytes in length, and has the following structure:
The Command Type field has a one-byte value (such as 0x32) that specifies the SMB command carried within this SMB message.
Each Command Type creates a different Parameter block. The Parameter block changes in structure and size to encompass the command’s parameters.
Attack Analysis
Recently, a new exploit suite was discovered dubbed EternalRocks. This suite gains control over the infected host in order to launch future attacks. EternalRocks uses the SMB exploits published by The Shadow Brokers in order to spread the infection. In this analysis, we will go through the attack chain which can be divided into 3 stages:
- Reconnaissance:
- SMBTouch
- ArchiTouch
- Exploitation:
- EternalBlue
- EternalChampion
- EternalSynergy
- EternalRomance
- Backdoor:
- DoublePulsar
In our analysis we will cover a single tool from each stage.
SMBTouch:
The SMBTouch Reconnaissance tool scans the targets before the attack is launched, and later attaches a detailed report on the target.
The tool collects its info using legitimate SMB messages which provide relevant Information about the victim machines.
For example, extracting the Native OS Version using the SMB_COM_SESSION_SETUP_ANDX (0x73) command.
SMBTouch initiates a session which forces the infected server to disclose OS information. Upon finding a vulnerable OS, SMBTouch proceeds to check the permissions it is granted by the OS. SMBTouch then reports what vulnerabilities are present in the system. This is a familiar procedure in accordance with how exploit kits detect web-browser plugins to analyze vulnerabilities. The information provided by SMBTouch is used to serve a suitable exploit.
EternalBlue exploits (MS17-010) CVE-2017-0144
There is a buffer overflow caused by a memmove operation, which leads to a mathematical error, where a DWORD is being cast to a WORD.
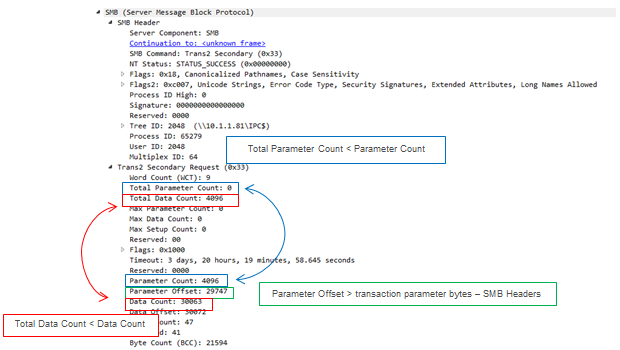
The vulnerability exists at SMB_COM_TRANSACTION2_SECONDARY (0x33) request using the malformed fields: Parameters Offset, Data Count and Parameter count. These allow the exploit to inject the DoublePulsar backdoor into the target machine.
SMB_COM_TRANSACTION2_SECONDARY (0x33) request sending malformed packets
As detailed in the Common Internet File System (CIFS) Protocol specification [MS-CIFS], the aforementioned parameters must meet the following conditions:
ParameterOffset (2 bytes): The offset, in bytes, from the start of the SMB_Header to the transaction parameter bytes contained in this SMB message. This MUST be the number of bytes from the start of the SMB message to the start of the SMB_Data.Bytes.Trans2_Parameters field.
ParameterCount (2 bytes): The number of transaction parameter bytes that are sent in the SMB message. This value MUST be less than TotalParameterCount. The sum of the ParameterCount values across all of the request messages in a transaction MUST be equal to the TotalParameterCount reported in the last request message of the transaction.
DataCount (2 bytes): The number of transaction data bytes that are sent in this SMB message. This value MUST be less than the value of TotalDataCount. The sum of the DataCount values across all of the request messages in a transaction MUST be equal to the smallest TotalDataCount value reported to the server.
However, depending on the setting, the malformed values injection can take place, as we can see below:
These demonstrate the usage of parameter count and data count which are smaller than the total parameter count and total data count. In addition, the parameter offset is bigger than the offset between the SMB headers and the transaction parameter bytes.
Using the above, DoublePulsar backdoor is delivered to the target machine encoded in base64:
Once installed, the backdoor provides a basic communication interface based on the SMB_COM_TRANSACTION2 (0x32) command using the TRANS2_SESSION_SETUP (0x000E) subcommand.
This subcommand is reserved but not implemented. Clients SHOULD NOT send requests using this command code. Servers receiving requests with this command code SHOULD return STATUS_NOT_IMPLEMENTED.
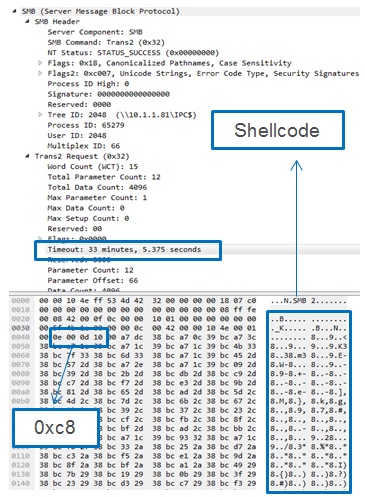
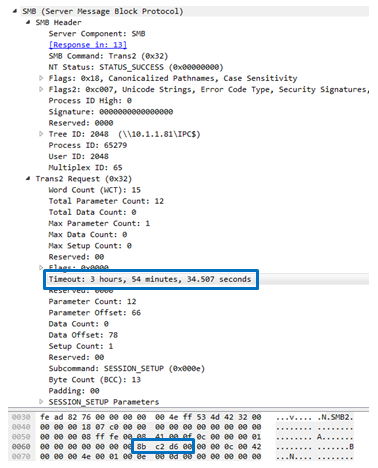
The messages are sent over the Timeout and Multiplex ID fields.
The timeout field is used to deliver the command itself while the Multiplex ID is used to get a positive or negative answer from the backdoor for the requested command.
Timeout field:
Decoding the command (set over the timeout field) is done by using the following expression: 0xff & ((x) + (x >> 8) + (x >> 16) + (x >> 24)).
This leads us to the 3 basic commands (after the decoding by the expression above):
- 0x23 – Checks if a backdoor is installed.
- 0xc8 – Loads DLL or Executes shell code.
- 0x77 – Uninstalls the backdoor.
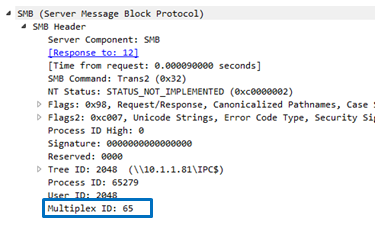
Multiplex ID field:
Together with the previous command, the attacker sets the Multiplex ID with either 0x41(65) or 0x42(66). The backdoor returns a positive answer by sending, respectively, 0x51(81) or 0x52(82),
If it’s a negative answer, 0x41 or 0x42 will be returned.
Here we demonstrate the execution of arbitrary shellcode using the 0xc8 command.
Following that, there is the removal of the backdoor from the target machine using 0x77 command.
Finally, we make sure that the backdoor is no longer installed on the target using 0x23 command.
The backdoor returns negative response (0x41/ 65) showing that our machine is clean and all evidence of an infection is removed.
Check Point IPS Coverage
While many only became aware of the cyber-attacks when WannaCry started infecting computers in May, from the graph below we can see Check Point IPS detecting traffic long before. This coincides with worldwide studies showing the number of machines infected with DoublePulsar. As seen in the graph below, the first large wave of attacks began on April 21st. This was most likely an attack installing the DoublePulsar backdoor onto the victims.
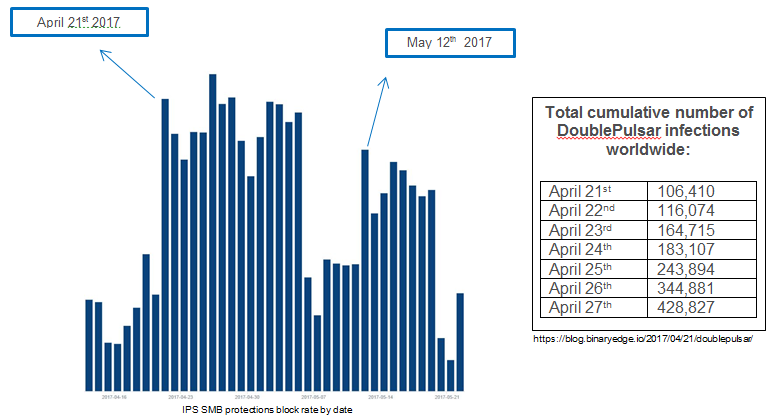
The second peak seen on May 12th, was the beginning of the WannaCry attack which was delivered on top of many of the machines infected with DoublePulsar. We can see from the graph above the large number of logs generated by IPS protecting against this attack traffic.
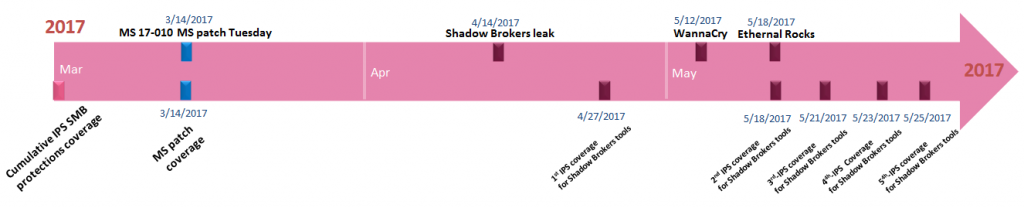
The timeline below shows the protections and attack events from the world (top bar) and IPS responses (lower bar).
- The SMB coverage block represents the cumulative IPS protections covering SMB vulnerabilities
- March 2017 Microsoft releases a critical security update patching SMB vulnerabilities
- IPS simultaneously releases protections covering the MS vulnerabilities
- April 14th the Shadow Brokers release the Lost in Translation exploits to the public
- April 27th IPS releases the first response to the Shadow Brokers leaked Tools
- May 12th WannaCry hits the public as the largest SMB attack
- IPS customers protected from previous SMB coverage
- May 18 EternalRocks suite is seen in the wild using multiple tools from the Shadow Brokers leak
- May 18th – May 25th IPS releases continuous updates to the SMB/RDP EternalRocks exploits
The table below outlines the SMB protections released by IPS that are relevant to the Shadow Brokers release along with the WannaCry and EternalRocks infections.
Check Point IPS Blade provides full protection against all EternalRocks exploits.
| Tool type | Tool name | CVE | Protection Name |
| Reconnaissance | SMBtouch
ArchiTouch |
Microsoft Windows SMBTouch Scanner
Microsoft Windows ArchiTouch SMB Scanner |
|
| Exploitation | EternalBlue
EternalChampion EternalSynergy EternalRomance EsteemAudit Eclipsedwing EBBISLAND aka EBBSHAVE |
MS17-10(CVE-2017-0143)
MS17-10(CVE-2017-0144) MS17-10(CVE-2017-0145) MS17-10(CVE-2017-0146) MS17-10(CVE-2017-0147) MS17-10(CVE-2017-0148) CVE-2017-3623 CVE-2017-9073 MS08-067(CVE-2008-4250) |
Microsoft Windows NT Null CIFS Sessions
Repetitive SMB Rename Command Attempts Ransomware Shared Folder Access Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0143) Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0144) Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0145) Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0146) Microsoft Windows SMB Information Disclosure (MS17-010: CVE-2017-0147) Microsoft Windows SMB Remote Code Execution (MS17-010: CVE-2017-0148) Microsoft Windows EternalBlue SMB Remote Code Execution Microsoft Windows EternalChampion SMB Remote Code Execution Microsoft Windows EternalSynergy SMB Remote Code Execution Microsoft Windows EternalRomance SMB Remote Code Execution Oracle Solaris Remote Shell Code Execution (CVE-2017-3623) Microsoft Windows EsteemAudit RDP Remote Code Execution Microsoft Windows Eclipsedwing RPC Buffer Overflow |
| Backdoor | DoublePulsar | Microsoft Windows DoublePulsar SMB Remote Code Execution |