
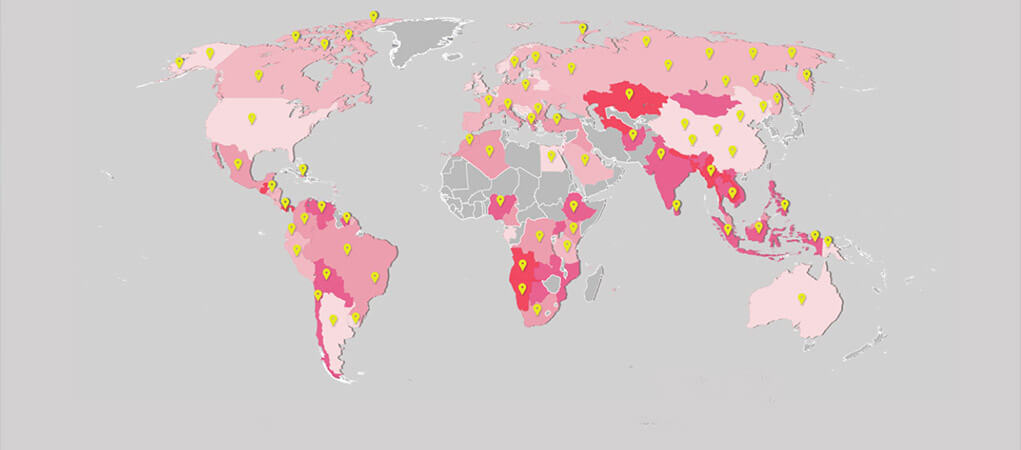
Check Point researchers have been investigating the ransomware campaign in detail since it was first reported. With a new Check Point WannaCry Ransomware Infection Map, the researchers were able to track 34,300 attack attempts in 97 countries. The average pace as of today is one attempt in every three second – indicating a slight decline since the original pace registered two days ago, of one attempt per second. The top country from where attack attempts were registered is India, followed by the USA and Russia.
Maya Horowitz, Threat Intelligence Group Manager at Check Point said, “Although we see it slightly slowing down, WannaCry still spreads fast, targeting organizations across the world. WannaCry is a wakeup call, showcasing how damaging ransomware can be and how quickly it can cause disruption to vital services.”
The Check Point Threat Intelligence and Research team recently announced the registration of a new kill-switch domain used by a fresh sample of WannaCry. Check Point’s live WannaCry Ransomware Infection Map shows key threat statistics and country-specific data in real time. Registration of the domain activated the kill-switch, safeguarding tens of thousands of would-be victims against the ransomware’s damage.
Check Point researchers found that those affected by WannaCry are unlikely to retrieve their files, even if they pay the ransom. A problematic payment and decryption system and false demo of the decryption operation puts into question the capability of WannaCry’s developers to deliver on their promises to decrypt files. So far, the three bitcoin accounts associated with the WannaCry campaign have accumulated approximately $77,000. Despite this, and unlike many other ransomware types, not a single case has been reported of anyone receiving their files back.
In February, Check Point’s released its Anti-Ransomware solution, complementing its SandBlast zero-day protection suite for advanced threat prevention. Built on top of the Check Point Infinity architecture, Check Point offers enhanced threat prevention capabilities against attacks such as WannaCry. The Threat Extraction component strips malware that is embedded in infected documents, the Threat Emulation component ensures only safe content is allowed onto endpoints, while the anti-ransomware solution identifies and blocks ransomware from damaging devices and encrypting files.





