The first half of 2019 demonstrated that no environment is immune to cyber attacks. We have witnessed threat actors developing new tool sets and techniques, targeting corporate assets stored on cloud infrastructure, individuals’ mobile devices, trusted third-party suppliers’ application and even popular mail platforms.
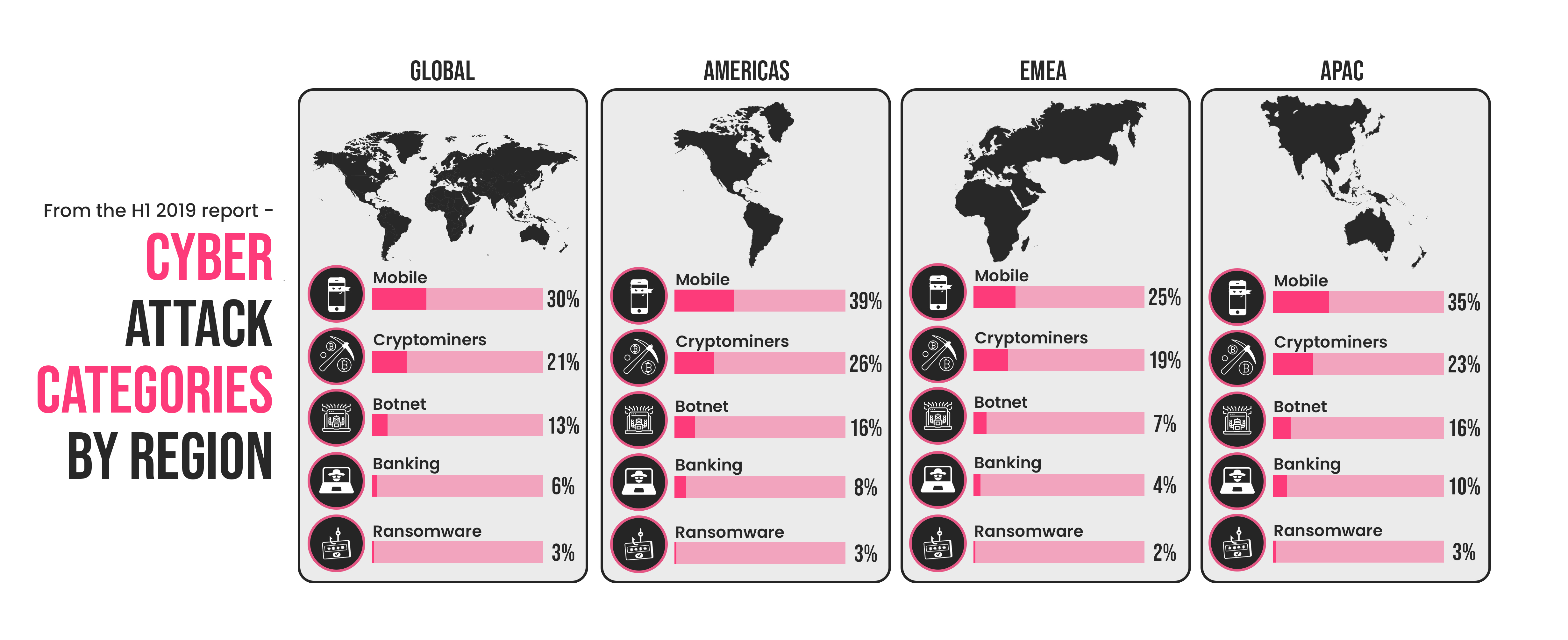
One of the dominating ongoing trends in 2019 is targeted ransomware attacks. This year collaborations between threat actors allowed even more destructive attacks that paralyzed numerous organizations worldwide. What ends with a ransomware attack usually starts with a more silent sequence of bot infections.
Still highly visible, cryptominers are on the decline this year – only 21% of organizations worldwide were affected by cryptominers’ attacks in comparison to 42% during its peak in 2018. This was the outcome after shutting down the ‘CoinHive’ drive-by mining service.
Software supply chain attacks attracted public and government attention. In such attacks threat actors inject malicious code into components of legitimate applications, victimizing a large number of unsuspecting users. The accumulation of several cases since the beginning of the year led the American government to devote special attention to this evolving threat and will soon publish official recommendations on ways to minimize the impact of such attacks.
To provide organizations with the best level of protection, security experts should be attuned to the ever-changing landscape and the latest threats and attack methods. With data drawn from Check Point’s ThreatCloud World Cyber Threat Map between January and June 2019, combined with primary research performed by the company’s cyber security experts , the following report holds a comprehensive overview of the trends observed in the various categories of cryptominers, ransomware, botnet, banking Trojans, data breaches, and mobile threats.