Introduction
With the emerging threat of miners and the rise of cryptocurrencies that have taken the world by storm lately, Check Point Research has been keeping an eye out for mining campaigns. During our work into Monero miners, we stumbled upon several highly active wallets with similar characteristics. As more and more evidence accumulated, our suspicion of a connection between them was confirmed, which helped us find traces of a mining operation that uses the wallets in question.
The mining operation, as it turns out, is run by a threat actor who has had their fair share of a bad reputation, as their name (or sobriquet) has come up before in suspicious contexts. Once we began to dig deeper, we witnessed the evolution of a distributor of friendly software to the mastermind of a large scale mining operation.
The Wallets
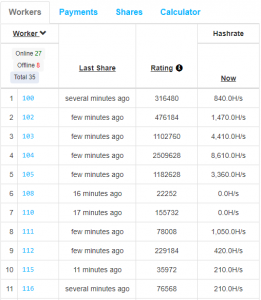
We spotted 17 different wallets that utilized the same mining pool (nanopool.org) and featured similar worker IDs. Worker names in Nanopool mining clients are optional and the usage of three-digits-long overlapping names in different wallets did not look coincidental:
Figure 1: Worker names in two different wallets
The wallets’ statistics from the Nanopool website provide us with a rough estimate of the total Monero amount generated by this operation each month, which currently stands at 37.4, in addition to a payment of 128 XMR from Nanopool.
If we take into account the maximal hash rate of each wallet, we get a sum of 592,000 hashes per second. As a regular PC generates around 100 hashes per second, this means that there are roughly 6000 infected machines.
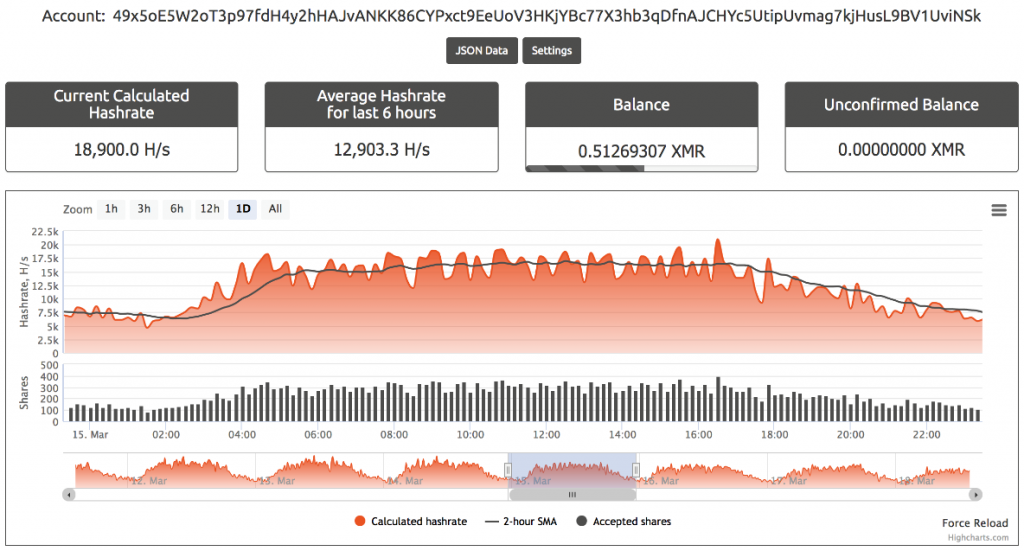
Figure 2: Times and hash rates of one of the crypto wallets.
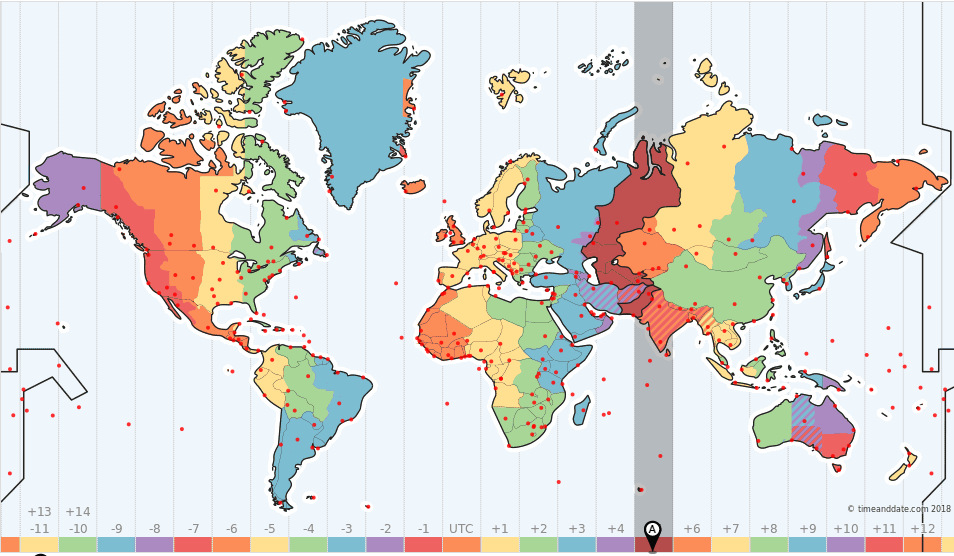
The above graph shows one of the wallets associated with the mining campaign. From the graph, we can see that the hash rate peaks daily from 2am to 3pm UTC. This correlates to working and daytime hours in UTC+5 time zones, and matches our own statistics as we later see that most of the traffic originates from India. A list of all the wallets appears in the IOC section.
Figure 3: Geographic spread of hashes.
The Miners
Looking up the previous wallets in the wild led us to miners that started spreading during the last few months of 2017, with newer samples submitted to VirusTotal on a daily basis.
Early versions of the miners seemed experimental and had random PDBs that were not omitted such as:
- C:\Work\qqq\Release\random.pdb
- C:\Work\blank\Release\blank.pdb
The project was apparently renamed to “xmrig_console_explorer” as seen in the following PDBs from more recent samples:
- C:\Work\Xmrig_console_explorer4\Release\random.pdb
- C:\Work\Xmrig_console_explorer3\Release\corsa.pdb
- C:\Work\Xmrig_console_explorer2\Release\aivengo.pdb
- C:\Work\Xmrig_console_explorer\Release\bdbjdfbvbd.pdb
Initially, the samples used Claymore’s CryptoNote Windows CPU Miner which was downloaded from an S3 bucket (hxxp://s3-us-west-2.amazonaws[.]com/zminer/NsCpuCNMiner
32.exe). As the campaign matured, it started downloading Monero CPU Miner (XMRig.exe) from: hxxp://s3-us-west-2.amazonaws[.]com/upperservice/xmrig.exe.
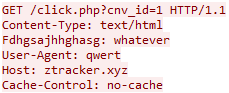
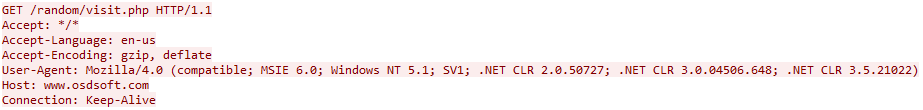
As for their C&C communication, earlier miners contacted hxxp://www.osdsoft[.]com/random
/visit.php after they were executed. Newer ones, on the other hand, contact different C&C domains which resolve to the same IP address (34.211.137[.]44), and have similar names (ztracker or xtracker).
Figure 4: C&C communication
The HTTP request header to the new C&C domains always has the same user-agent (“qwert”), even though the domains constantly change.
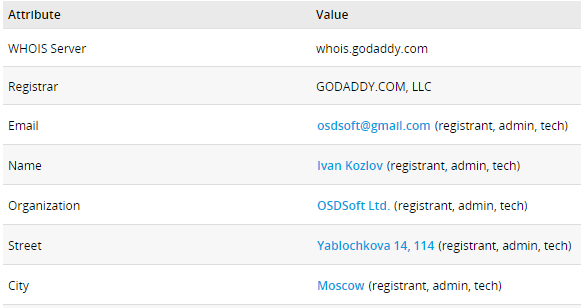
After we looked up these websites’ whois information, we found out that both the old and new ones are registered under the name Ivan Kozlov, and the e-mail address osdsoft@gmail[.]com.
Figure 5: C&C WhoIs information.
OSDSoft
The name Ivan Kozlov was first associated with a website called OSDSoft[.]com. The purpose of this website was to offer a free video downloading software. The screenshots below show Facebook and Youtube accounts that were associated with this website and promoted its product:
Figure 6: OSDSoft’s YouTube videos.
Up until 2014, the home page of this website was still accessible and the software could still be downloaded from it. In the years to follow, however, suspicious executables started being associated with OSDSoft.
In 2017, just when the mining campaign started, other domains such as ztracker[.]club and xtracker[.]club were also registered under the name Ivan Kozlov, with dozens of miner samples reporting back to them when they infect new machines.
The Start of PUP
Years before OSDSoft pivoted into the crypto mining arena it used to distribute potentially unwanted programs (PUP). The PUPs were disguised as legitimate services and had names such as “WindowsUpdater” or “AdvancedPCCareSetup”.
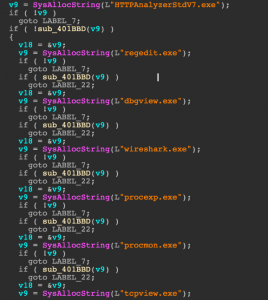
Despite their ‘innocent’ names, uploading the files to Check Point SandBlast showed these executables and their downloaders are stealthy and perform environment checks against virtual machines, analysis tools and Anti-Virus engines before running. They also fingerprint the system they are running on and find out its geolocation by contacting ip-api[.]com.
Figure 7: Example of PUP evasive behavior.
The PUPs download additional programs based on the country the infected machine is located in. This is how, for example, an infected machine in Russia ends up with Mailru, YoutubeAdblockE, Zcash, Monero, PCCleanPlus and several more programs installed on it after executing the PUP.
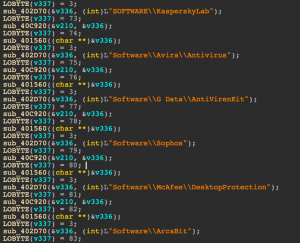
Determining which programs to download is done by examining the content of “bundles.xml”, a list of countries and corresponding programs that is downloaded whether from OSDSoft or from the S3 bucket we have seen in use previously (hxxp://s3-us-west-2.amazonaws[.]com/upperservice/bundles.xml).
The list contains an entry of programs that are downloaded by default regardless of the country, and additional ones that will be selected based on geolocation.
Figure 8: List of programs that are downloaded from the PUP by default.
The PUP downloaders have an embedded list of nearly 60 executables and URLs to download them from. Most of these executables have a high conviction rate in VirusTotal. The large list of programs indicates that this may be a pay-per-install distribution model.
The Distribution Model
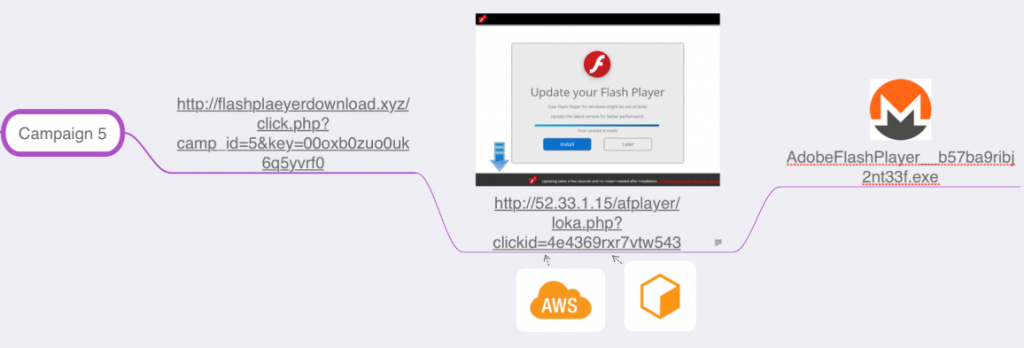
The mining C&C domains were not the only ones which the threat actor registered, as there were more addresses such as flash2update[.]xyz, flashdownload[.]club, and flashplayers[.]club that are under the name Ivan Kozlov.
This clarifies how the miners are spread. The infection flow involves redirecting the victims to misleading websites which offer an update to their Flash player. However, downloading the miner does not seem to be enough for the threat actor, as these fake Flash Player update websites also use CoinHive to mine through the browser. Clicking anywhere on the deceptive Flash page would result in the miner being downloaded: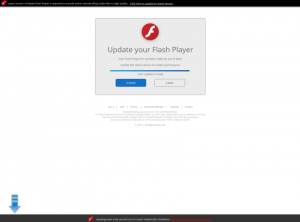
Figure 9: The fake Flash Player update page.
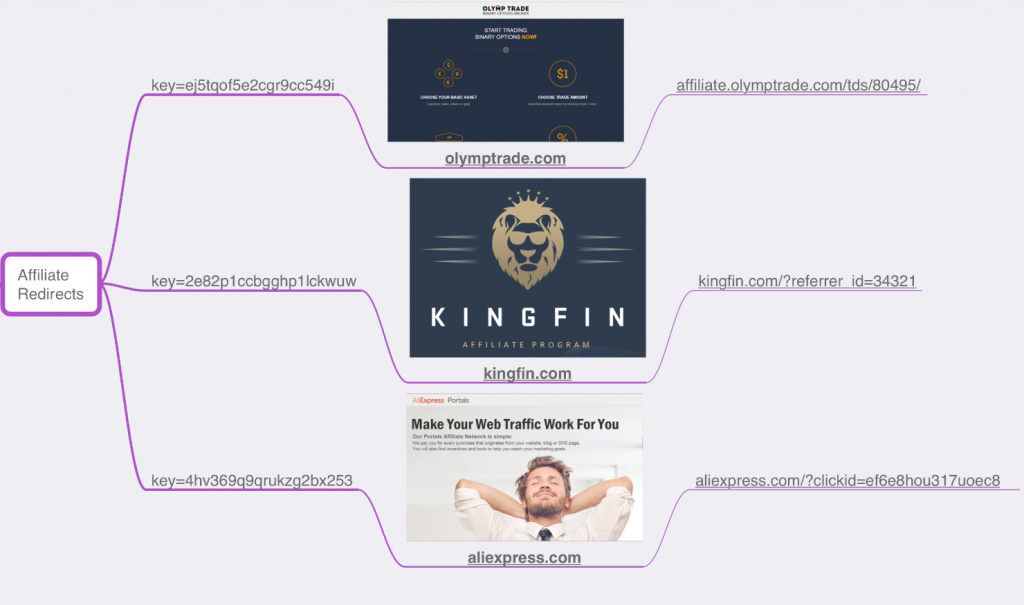
The pattern that appears in the Flash websites (/click[.]php?camp_id=[camp_id]&key=[key]), as well as the format of the HTTP GET request to the C&Cs (/click.php?cnv_id=[cnv_id]), led us to a highly active TDS server called Binom from binom.org.
We have seen up to twelve campaigns with different IDs from this TDS, some of which involved variations of OSDSoft’s miners, Graftor and redirections to affiliate programs:
Figure 10: Binom affiliate redirects.
The miners seem to be associated with the campaign ID 5, that appears in the Flash URLs:
Figure 11: The miner’s association with affiliate campaign ID 5
Moreover, the Binom login panel is available when entering one of the C&C domains, ztracker[.]club:
Figure 12: Binom login panel in ztracker[.]club
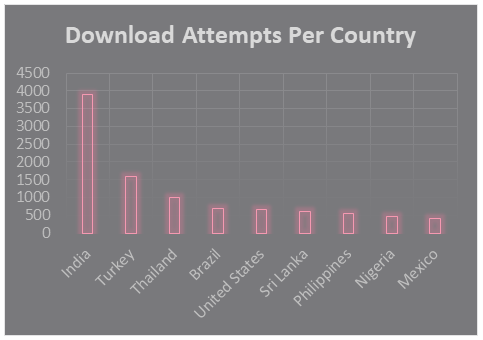
Statistics from Check Point Telemetry show that access to the Flash websites originated mainly from India, which confirms our previous findings regarding the miners’ maximal activity during Indian daytime hours:
Figure 13: The number of download attempts per country.
Summary
Correlating the current mining trend to a wider long term operation assisted us de-anonymize a Monero mining campaign, including its distribution methods, it’s profit, and even the identity of the threat actor who stands behind it, while overcoming the anonymity that Monero’s ecosystem provides.
Looking over at the increasingly malicious evolution of our threat actor, as it is reflected from the evidence above, we cannot help but wonder what future threat they have in store.
Check Point’s Sand Blast Agent, Threat Emulation, Anti-Bot and Anti-Virus blades protect our customers against this threat.
IOCs
C&C:
- osdsoft[.]com
- ztracker[.]xyz
- ztracker[.]club
- ztracker[.]ml
- ztracker[.]gq
- xtracker[.]club
Flash websites:
- flashdownloadonline[.]xyz
- flash2update[.]xyz
- flashdownload[.]club
- flashplayers[.]club
- flashplay[.]club
- flashplayerr[.]club
MD5s:
- fa183b39ea8c7abfed0f556166a4b557ce428911
- 2a9893c0585714b761431debec5e45826d28e761
- 549d56bd0f585738b18d02a40a27eb3fe253bf08
- 69ae90ecd5a4e8d34b668673ca602a120ac5b463
Miners:
- 9b96f74bb2cf4f73565df75de39f6375c7a36be4
- 27e4b7ff590b2b0ead04447d08d634c32a7604cf
- 3fc574af9baa50b4582bcd5a864fbb1ff27834f5
- c40f4e5ccc3d56601995ed43e03f46251c6b6f99
Associated Wallets:
- 49x5oE5W2oT3p97fdH4y2hHAJvANKK86CYPxct9EeUoV3HKjYBc77X3hb3qDfnAJCHYc5UtipUvmag7kjHusL9BV1UviNSk
- 4AXxRJhrXh72Kv2WHzLLQ87Xq7WSQxc7q92ZZNVtEqo6R2oZeXCGwBa9zRzEd3RJ8kiD8cjwYsTxxgcnH9mo9x943TpDyjp
- 44pCscLkFgoLcNj5FqaET8dFhYgrjGgJzMtqJdTtap9Xa4eWLSYCm8nH68Jf8NzXiF4SM2K4mJFDsMh7JWQp3eydQtFHYzv
- 48Zn8xnfeymWuAE1osgDkUPQHT6cEwppZFgkBtLx8U9wd7Euo5bViFFHAMWjechwziSoLm3A8xsJtXZKEHHxHxh8SmfP8Dp
- 42NJgtw17RnJ5g1tYQeGLm2KUqpM8ddfwcMUkPRix9HJ2MxBb8Ds1UaKnfL145K9E677wtZoaDb89KfZpFso4tKa9CERxZT
- 45amt6kvQJo7kUKnrcwLuAV4vo8hfeu8kWhkjP39P6JCQ64oiTEyqAe7Z8fUxBCFLxBQzYEzkAFVsSeDv7bg5dFM4efV5mc
- 49EXwQHg6UAhWdV55U4TA2D2TaQrUHs3JhsiTYPJvFB3S7CssyhehF3885dY8qg18aUaNZ1eA1Ki36eF8zkQjR1aPrMwZ7G
- 48B3GKJv1eBXgw1AN9YbuQcHANKyLtwt4djMf6STMdzfKN3tEuZdGFy7qTb95ZoessFt4encGNZ2gB9Zj8mc1uomLoNSFps
- 41ompKc8rx9eEXtAAm6RJTTm6jg8p6v3y33UqLMsUJS3gdUh739yf7ThiSVzsU4me7hbtVB61rf7EAVsJeRJKGQH4LFi3hR
- 43nZNjoEPp3C1gqjpvaj9UUDyzVwQGVkpcmVHWHucCFFbAHZAgNjUbUYaHgTTijPs17ZBYWjsVEDBJuYhDXCJpnq76sma7o
- 422qLV9iQCW35yRY6EjVtbLBSaJZw4W9RJWPsWBNp5MYd9VkYnvMUiWHQQqqBW2qej1uQV9dmzJzW7dp8JhhLWvrFrSJP7Z
- 49knYtxf9TzGGha9TykH4UDg9TR9PMQ6FJhT6eXRmKaYbGuqmAxEaw2Hx8J5AU2zY992BmqmJ9iet1UU9Z5ooWEC8jvt4QC
- 4Aodji9gejTH3U1tSbVEBRH3DLiGP1AqDCzUnBmhtJfH92iciN4Y9wFexBZrhjyBbR1K62jdeaRkLLRUnvHQNyEKCWotvTf
- 41r12vzbUd8coXCZLaKTUaWb7J5kEzfkUasiaxc4RgEh3tbshpGVJWh7HEWzjbHyo1PsyZR7a5pwYXZUpznwcFoNJDUAmc6
- 4JUdGzvrMFDWrUUwY3toJATSeNwjn54LkCnKBPRzDuhzi5vSepHfUckJNxRL2gjkNrSqtCoRUrEDAgRwsQvVCjZbS5bqVDka5onRM8ytDh
- 4Apo2MGudNkHhCa1aiEBDu4vehNy9VDRje1qjoG7JQEYYY2FR1KeSe78mR4wsM9qvGVnAojw4fb322gsr65Kzbx1ThrghCe
- 4BG6mDFaSc9EAsKvFtYfzC8yDpWeKEmTrPAMcvMb38FXPHbG6YwWzBZ18ZcA6DduxzWeiFnEDnFPyS39iNQ5TpzZBx8Vh49