When the whistle of the first match of the 2018 World Cup blew, it didn’t just signal the start of an exciting tournament for football fans worldwide, but also gave the green light for threat actors to exploit this much anticipated event for their own gain.
Over the last few weeks, the Check Point Research team found a trend of threat actors exploiting the popularity of this year’s World Cup, including phishing campaigns as well as a highly invasive mobile espionage campaign, to lure potential victims.
At the start of this year’s tournament, a new phishing scheme exploited victims by enticing them to download an infected FIFA World Cup schedule and results checker onto their PCs. The campaign tried to peak their interest with an email subject line related to the world cup. When opened, the attachment used a known downloader of potentially unwanted programs (PUPs), called ‘DownloaderGuide’, which is most commonly used as an installer for applications such as toolbars, adware or system optimizers.
In a second phishing attack, a malicious executable was delivered, again using a schedule of the World Cup games to bait unsuspecting victims. This time, though, the malware used was intended to steal users’ login credentials from Chrome, Firefox and Outlook as well as log information about the infected computer and operating system itself.
Last week, Israeli security agencies announced that the Hamas terrorist organization had installed spyware on Israeli soldiers’ smartphones in its latest attempt to collect information on its long time enemy. About 100 people fell victim to the attack that came in the form of fake World Cup and online dating apps that had been uploaded to the Google Play Store, the official app store of Google. In fact, the oldest app was uploaded as early as November 2017, meaning it had hidden there, undetected, for several months.
Check Point researchers got hold of samples of the malware, dubbed ‘GlanceLove’, and analyzed its operation. In brief, this attack is a rare occurrence in which a fully operational Trojan managed to bypass Google Play’s protections. It also serves as a good example of how attackers make use of major events to attract potential victims and to hide within the scores of legitimate apps which relate to these events.
How The ‘GlanceLove’ Malware Operates
The attack begins when the user is lured from a seemingly innocent Facebook page and fake profiles promoting an app called ‘Golden Cup’. This is used to add credibility to the app and not raise any suspicions amongst its targets while the user is encouraged to proceed and download the app from Google Play. Earlier versions of the malware spread via similar tactics, disguised as dating and chat apps, called ‘Glance Love’ and ‘Wink Chat’.
Upon installation, the app requests the user to approve a long list of permissions, including access to the device’s network connection, contacts, SMSs, camera and external storage. These extensive permissions are used later for its malicious purpose. In fact, the app itself is completely benign, which is how it was able to infiltrate into Google Play despite Google’s protections. However, while the apps provide authentic functionalities, like ‘Golden Cup’ for example provides some World Cup related information, their actual purpose is to operate as droppers, and silently download and execute the malicious components of the attack without any user interaction at all.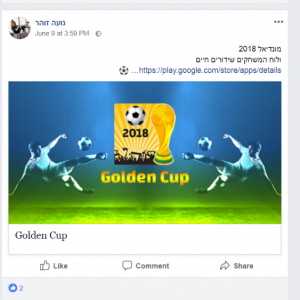
Figure 1: Facebook profile promoting the malware. 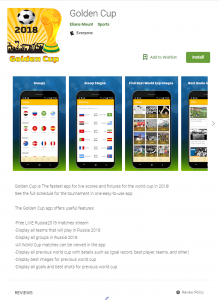
Figure 2: Golden Cup app on Google Play.
‘Golden Cup’ then contacts its Command and Control server (C&C) and downloads another component in the form of a dex file from it. The dex file contains several malicious capabilities including stealing the device’s photos, contacts, SMS messages and location, which are all sent back to the C&C server along with details regarding the device’s properties. If certain conditions are met, the attacker orders the second component to download an additional apk file containing the third component of the attack, which has the greatest capabilities. To download, this component, the app requires user consent.
The last component has three main interfaces:
ReceiverManager: This interface allows for recording phone calls by listening to the devices microphone and also reports back to the server about any new app installed and any phone calls made on the device. This effectively allows it to eavesdrop on the user. This interface also allows to take photos via the device’s camera.
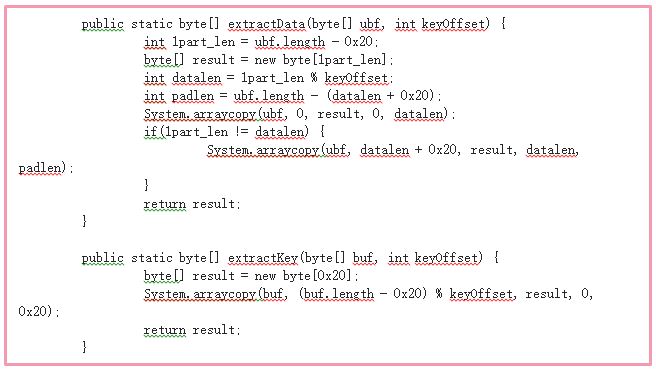
ConnectivityManager: This interface is responsible for communicating with the C&C server, which is different from the server used for earlier stages of the attack. The C&C The server can send the malware commands to collect information from the device, install additional apps, and even self-destruct (in an effort to leave behind no trace of it). This interface also sends the server a list of tasks to run on the device. The communication with the server is encrypted based on the AES algorithm, in which the app generates a random key, encrypts the data with it, and then stores the key between data chunks at an offset unique for the device.
TaskManager: This interface schedules data gathering instances and stores the collected information to files which are the uploaded to the server by the ConnectivityManager. Each data collection task can be enabled or disabled by a configuration command received from server.
Figure 3: Encryption code.
Figure 4: Diagram of GlanceLove’s operation flow.
What Is the ‘GlanceLove’ Malware Capable Of?
‘GlanceLove’ is a fully grown spyware, capable of pretty much anything.
To be more specific, the malware can conduct all of the following activities:
- Record Calls. ‘GlanceLove’ waits for a notification from the ReceiverManager interface, indicating the user has picked up the phone, upon which the malware takes a photo one second later. It then starts to record the conversation for as long as the attacker chooses to record for.
- Track Location. The malware periodically stores the location of the device.
- Open Microphone. The malware periodically records audio from the device’s microphone with a predefined length and interval between recordings. Both the location and the microphone can be set to a “special mode” which enables more frequent recordings.
- SMS Theft. The malware periodically collects SMS messages received or sent since the last time it collected them.
- Take photos from the Camera. The malware silently takes photos from the camera and saves the images.
- Storage Mapping. The malware collects the listing of all storage directories, including file names and sizes.
- Steal Contacts. The malware collects information from the user’s contacts directory. It stores the names of the contact, its number and the time when the user last contacted it.
- Steal Images. The malware collects images stored on the device and uploads them to the server. Additionally, it collects the images’ EXIF information, which indicates where the picture was taken.
Why Use Such a Complex Attack Structure?
There are several reasons for such an extensive build of the malware.
- Each component is dedicated to a specific process, and is tailored accordingly.
- The dropper must not include any malicious code itself to avoid detection, and is structured accordingly.
- The separation between the two malicious components allows the hacker to maintain a low profile on most devices, and handpick the targets he wishes to spy on, making his information gathering focused and less demanding.
This strategy is called a “chain attack”, and is extremely successful for attackers as it allows cybercriminals to easily tweak or upgrade a component that has only been partially identified without abandoning the attack altogether. Furthermore, chain attack link structures lend themselves to being built with a more modular code, which makes it simpler for the malware to later evolve and accustom itself to new systems, targets and geographic regions. Additionally, chain attacks allow attackers to limit unnecessary spreading of the malware, which makes it harder for security vendors to obtain samples in order to fight it.
We would like to thank our colleague, Eyal Sela, at Clear Sky Cyber Security who helped contribute to this research.
Appendix 1: A list of Sha 256 hashes:
Name: WinkChat (App from Google Play)
Sha 256: 2ce54d93510126fca83031f9521e40cd8460ae564d3d927e17bd63fb4cb20edc
Package name: com.winkchat
Name: GlanceLove (App from Google Play)
Sha 256: 67b1a1e7b505ac510322b9d4f4fc1e8a569d6d644582b588faccfeeaa4922cb7
Package name: com.coder.glancelove
Name: World Cup (App from Google Play)
Sha 256: 166f3a863bb2b66bda9c76dccf9529d5237f6394721f46635b053870eb2fcc5a
Package name: anew.football.cup.world.com.worldcup
Name: GlanceLove (App from Google Play)
Sha 256: d9601735d674a9e55546fde0bffde235bc5f2546504b31799d874e8c31d5b6e9
Package name: com.coder.glancelove
Name: GlanceLove (App from Google Play)
Sha 256: b45defca452a640b303288131eb64c485f442aae0682a3c56489d24d59439b47
Package name: com.coder.glancelove
Name: GlanceLove (App from Google Play)
Sha 256: 1664cb343ee830fa94725fed143b119f7e2351307ed0ce04724b23469b9002f2
Package name: com.coder.glancelove
Name: SoftwareUpdate (Payload)
Sha 256: 7c2c5909d86323c53830552b5e2fd130d2ed68fa22443e1bad22896e08f0a652
Package name: com.air.update
Name: System Update (Payload)
Sha 256: bcdeb31c0685667da5bf2b61bb0c7c7a00d76a8217d093713827dc5951cc98cb
Package name: com.system.update
Name: System Update (Payload)
Sha 256: 53482979ff5c40b93a6123c043a7deff01d085b08129f1931cfbbc541ba1ddf2
Package name: com.android.update
Name: System Update (Payload)
Sha 256: b9f64ffce38e224e15ec6f81b389a315b35aafe0da173205ff5e6bed4b5ee874
Package name: com.android.update