

Research by: Gil Mansharov and Alexey Bukhteyev
Introduction
In its 2018 annual publication, the FBI IC3 (Internet Crime Complaint Center) reported a 242% rise in extortion emails, the majority of which are “sextortion”, with total losses of $83 million in reported crimes.
The idea behind sextortion is simple – an email demanding blackmail payment is sent to a victim, threatening to expose sexual video and private data related to the recipient if payment is not received. You may have received such emails or know others who have. Here’s another disturbing thought: is it possible that this morning you yourself unknowingly distributed 15,000 sextortion emails?
Check Point Research has exposed a botnet that does precisely that: it uses many thousands of infected computers to deliver millions of such threats to innocent recipients.
The Phorpiex (aka Trik) botnet has been active for almost a decade and currently operates more than 500,000 infected hosts. In the past, Phorpiex was monetized mostly by distributing other malware including GandCrab, Pony, Pushdo, and used its hosts to mine cryptocurrency. Recently, Phorpiex added a new form of revenue generation. In this report, we describe the spam bot used by Phorpiex to run large scale sextortion campaigns.
In the 5 month period that we have been monitoring this operation, we recorded transfers of more than 14 Bitcoins (BTC) to the Phorpiex campaign wallets whose current value is over $110,000. This may not sound like a lot, but for a low maintenance operation requiring only a large credentials list and the occasional wallet replacement, this generates $22,000 per month.
Sextortion E-mails
The Phorpiex/Trik botnet uses a spam bot that downloads a database of email addresses from a C&C server. An email address is then randomly selected from the downloaded database, and a message is composed from several hardcoded strings. The spam bot can produce a large number of spam emails – up to 30,000 per hour. Each individual spam campaign can affect up to 27 million potential victims.
The most interesting feature of the last spam campaigns is that the Phorpiex/Trik spam bot uses databases with leaked passwords in combination with email addresses. A victim’s password is usually included in the email message; this exacerbates the threat by showing that the password is known to the attacker. For further shock value, the message starts with a string that contains the password.
Here is an example of a sextorion email created by the Phorpiex spam bot:
From: Save Yourself
Subject: I recorded you – ██████Hi, I know one of your passwords is: ██████
Your computer was infected with my private malware, your browser wasn’t updated / patched, in such case it’s enough to just visit some website where my iframe is placed to get automatically infected, if you want to find out more – Google: “Drive-by exploit”.
My malware gave me full access to all your accounts (see password above), full control over your computer and it also was possible to spy on you over your webcam.I collected all your private data and I RECORDED YOU (through your webcam) SATISFYING YOURSELF!
After that I removed my malware to not leave any traces and this email(s) was sent from some hacked server.
I can publish the video of you and all your private data on the whole web, social networks, over email of all contacts.
But you can stop me and only I can help you out in this situation.
The only way to stop me, is to pay exactly 800$ in bitcoin (BTC).
It’s a very good offer, compared to all that horrible shit that will happen if I publish everything!
You can easily buy bitcoin here: www.paxful.com , www.coingate.com , www.coinbase.com , or check for bitcoin ATM near you, or Google for other exchanger.
You can send the bitcoin directly to my wallet, or create your own wallet first here: www.login.blockchain.com/en/#/signup/ , then receive and send to mine.My bitcoin wallet is: 1Eim8U3kPgkTRNSFKN49jgz9Wv4A1qmcjR
Copy and paste my wallet, it’s (cAsE-sEnSEtiVE)
I give you 3 days time to pay.
As I got access to this email account, I will know if this email has already been read.
If you get this email multiple times, it’s to make sure that you read it, my mailer script is configured like this and after payment you can ignore it.After receiving the payment, I will remove everything and you can life your live in peace like before.
Next time update your browser before browsing the web!
The spam bot is one of the final payloads in each of the Phorpiex campaigns observed in 2019. The Phorpiex spam bot doesn’t have its own persistence mechanism, as it is downloaded and executed by other Phorpiex modules. Here are some of URLs from which the spam bot was downloaded:
| URL | Date | MD5 |
| hxxp://185.176.27[.]132/5 | 2019-07-31 | fac2fc1b97fc3ab4469e723e501cecef |
| hxxp://193.32.161[.]73/5 | 2019-07-28 | 8d1a1a39fec3efbd1700801266ba2529 |
| hxxp://193.32.161[.]77/5.exe | 2019-07-09 | f895a1875b3e112df7e4d548b28b9927 |
| hxxp://193.32.161[.]69/6.exe | 2019-07-09 | 39b326e56ab3c48b5bec19ad9300d2cf |
| hxxp://193.32.161[.]77/4.exe | 2019-06-30 | 586554bb5df08e8cabf54113d76b38e4 |
| hxxp://osheoufhusheoghuesd[.]ru/5.exe | 2019-06-13 | 29d3c08d5f9fcbbef6ea5493907f91d8 |
Table 1 – Phorpiex Spam Bot pre-infection URLs.
Technical Details
When it starts running, the spam bot performs several checks and initialization steps, similar to the rest of the Phropiex modules. First, to prevent running multiple instances, it tries to create a mutex with a specific name. This name is hardcoded in the sample, but each sample has a unique mutex name:
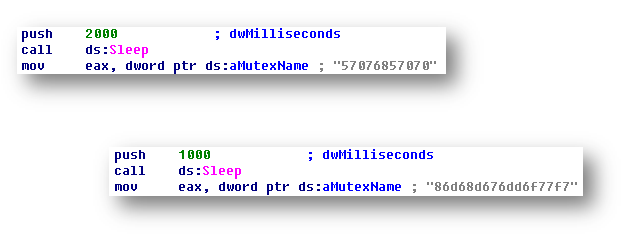
Figure 1: Spam bot mutex names.
If the mutex already exists, the spam bot stops running. Otherwise, it continues the initialization steps: the spam bot deletes the alternative file stream “:Zone.Identifier”, and adds a firewall exception by creating a new value under the registry key:
SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\
FirewallPolicy\StandardProfile\AuthorizedApplications\List\
The Spam Bot adds the value “<path_to_spam_bot>:*:Enabled:<hardcoded_ name>” to this key. For example:
%TEMP%\28764.exe:*:Enabled: WDrvConfiguration
Finally, the Phorpiex spam bot queries the MX DNS entry of the domain “yahoo.com” or “aol.com” and tries to connect to its SMTP server at port 25. If the SMTP server is unreachable, it also stops running:
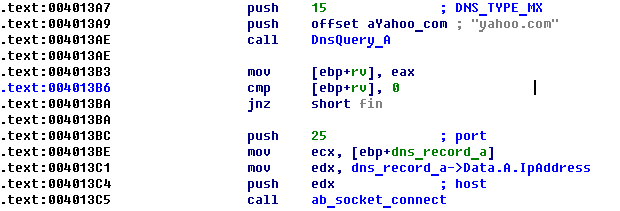
Figure 2: Checking if the Yahoo SMTP server is reachable.
Email Address Databases
The spam bot uses unencrypted HTTP communication with its C&C server. The following user-agent header, although it isn’t unique to the Phorpiex spam bot, is used for performing HTTP requests:
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:67.0) Gecko/20100101 Firefox/67.0, and sends a GET HTTP request using the URL:
hxxp://<C&C Server>/<hardcoded path>/n.txt or hxxp://<C&C Server>/<hardcoded path>/p.txt
Example:
hxxp://193.32.161[.]69/111/n.txt
The response to this request contains a number N of email address databases stored on the C&C server. Follow-up requests are sent to download those databases, and save them under the %TEMP% directory with “.jpg” extensions.
In the infinite loop, the malware generates URLs with the following format:
hxxp://<C&C Server>/<hardcoded path>/<rand>.txt
The <rand> is a random integer between 1 and N.
The final URL of an email database to download looks like this:
hxxp://193.32.161[.]69/111/135.txt
The downloaded database is saved in the %temp% folder with a filename composed of random digits and the “.jpg” extension. For example:
%temp%\5173150314183010.jpg
The downloaded database is a text file which contains up to 20,000 email addresses. In various campaigns, we observed between 325 and 1363 email databases on a C&C server. Therefore, one spam campaign covers up to 27 million potential victims. Each line of this file contains an email address and a password delimited by “:”, as shown below:
[email protected]:secretpassword1
[email protected]:secretpassword2
[email protected]:secretpassword3
[email protected]:secretpassword4
The spam bot creates a total of 15,000 threads to send spam messages from one database. Each thread takes a random line from the downloaded file. The next database file is downloaded when all the spam threads finish. If we consider the delays, we can estimate that bot is able to send about 30,000 emails in an hour:
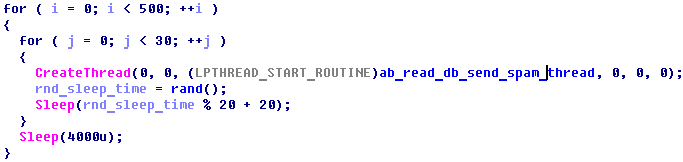
Figure 3: Creating threads for sending spam emails.
Distributing Spam
To send emails, the spam bot uses a simple implementation of the SMTP protocol. The address of the SMTP server is derived from the domain name of an email address. After establishing a connection to the SMTP server and receiving an invitation message, the spam bot sends a HELO/EHLO SMTP message with its own external IP address that it obtained using the icanhazip.com service.
The spam bot then tries to generate a valid random domain name with the following format:
“{4 random digits}.com”
The validity of the domain is checked using a DNS query. This leads to a large number of DNS requests being generated before contacting an SMTP server:
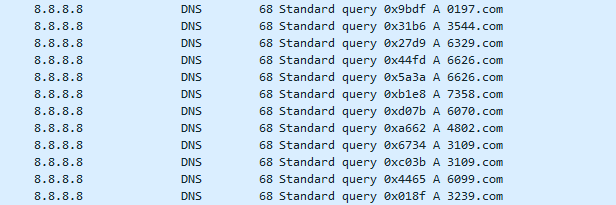
Figure 4: Large number of DNS requests produced by the Phorpiex spam bot.
If a domain was successfully resolved, it is used for the sender’s email address. The first part of the sender email (before “@”) is generated from a hardcoded word and 2 random digits. The sender’s host name, IP address, and a domain name of a fake SMTP server are also random values, as shown in the image below:
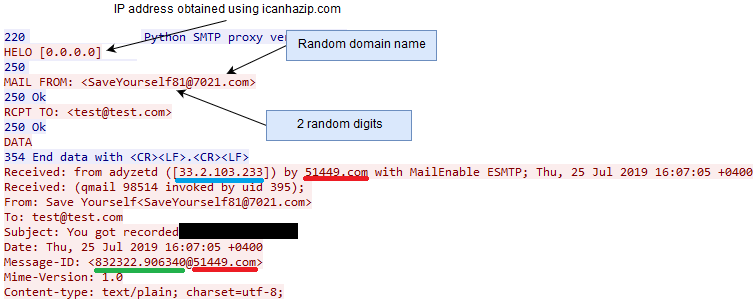
Figure 5: Example of the Phorpiex spam bot SMTP communication.
To set a subject field, the spam bot concatenates the username or password to randomly chosen strings (may vary from sample to sample):
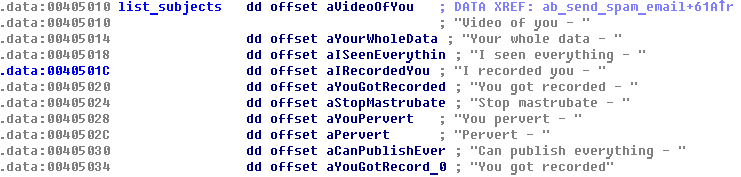
Figure 6: Email subjects used by the Phorpiex spam bot.
Therefore, if we assume that [email protected] is the victim’s email address, the subject of the email could be “I recorded you – john_doe”.
Revenue
We saw how threat actors try to use the Phorpiex spam bot to extort money from random victims, but how successful is the campaign indeed?
Check Point Research monitored the campaign and the Bitcoin wallets extracted from every spam bot spotted since April 2019. We found that more than 14 BTC were transferred to those wallets:
| BTC Wallet | Incoming Transactions | Amount |
| 1Eim8U3kPgkTRNSFKN49jgz9Wv4A1qmcjR | 2 | 0.14344608 |
| 1LwPAckT7ettEpLEuAU2dBXbqqSd9SrLAD | 2 | 0.01181594 |
| 1D1nXbBdPmCpy9rPRdtaXjA5ftGzYPPw51 | 1 | 0.00614417 |
| 1LZStbAiQYiBGUTEH8mbTYu8pbvmrDprZQ | 2 | 0.02160055 |
| 1FLREuhB3U56yJBTTsj6zzEXjNf4BTzeZr | 2 | 0.14981551 |
| 1QBfCvZUuA3fbXX9bHeeTpqzkYgikvhtXR | 2 | 0.08108546 |
| 1F73edsje5GbjqybTgKAesWfihvp4Q59Eq | 2 | 0.35886416 |
| 13HffyTVP8qcYzd5tga4Bc6rCGETNbbZuD | 1 | 0.03664995 |
| 1MnUgqSkToq3j7ozwjSh54m1WxWZ3Xqym6 | 3 | 0.24167993 |
| 12EMaHiZG75ztkjUjuPZhQDcyW89qRJVuR | 7 | 0.5553606 |
| 15WGVWt16CzuK3opvJHg6i1XSstbXGEPcZ | 2 | 0.66430707 |
| 1PC3q4JgAJvHcpsT2LqwoqVN2ckzAVQoxf | 1 | 0.01966277 |
| 1Nq84HeDmd2JGyRtjqh32QRG4zoSrp8bdL | 2 | 0.15959452 |
| 16JApT2K6Z9AirkMeBSWyhwuJ8dCfRhY9U | 1 | 0.036712 |
| 1GTzcCBW79F3BtBdN9jx7hqNq65ebbt1Wm | 1 | 0.03995683 |
| 19naMJAmQq6b9XJaSaWpw2MTBBVeW355Ro | 1 | 0.04334168 |
| 1HB3KtKoguFuZ4BdmCv9Fc4tYTwDQgmqmW | 8 | 1.22814147 |
| 1PzrJSAhZSiYK93qLZnKsRzQzS49j5Ugzc | 2 | 0.10102945 |
| 1BpwthndBC2aDHiztoMtMBnq7ejmNkHnSV | 2 | 0.25592471 |
| 1CSDpCjyVHsuTb6i7zZ8dr81iUGL5ff7vM | 11 | 0.4353143 |
| 1Lmb3V8PbqTtGmFawu41k9hSXZgJn4G2pS | 6 | 0.35394814 |
| 1MX8BUf7R4rE7xLoaVMyiceX8DE8D3aFQg | 7 | 0.42375914 |
| 1KDnUbAHkxb57RYjJufdmjYF9F4vFWjm5m | 1 | 0.131684 |
| 1BdMo6PKJCR9S6FzLDtE4ChszHdrJdbWJ7 | 2 | 0.14633115 |
| 12ZyXPMJBAFCfpyYTYo8V6QcG653Lcs9oj | 3 | 0.4714263 |
| 154J36DXD2wA512cJRdAJsr1KcKynbVtpM | 3 | 0.26725319 |
| 15xdJ5nhwQCTFGs9AqciPGxgf62hGdWog7 | 1 | 0.17406292 |
| 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 | 2 | 0.33377914 |
| 1GLJa8dMq9XBaiMhXNJSQjVoNzh2xRanzD | 1 | 0.00001 |
| 15dut9dbaZbSKZq27tyuLkjhCEiRaewvvh | 1 | 0.12965713 |
| 14VYd5JrPrrXD1qiMxZ5An2VsU5db5ZqS7 | 1 | 0.1893836 |
| 1PTNbkmQckDTjbhCMtfa5zqY992ZNZ8biG | 5 | 0.38752657 |
| 17v35QnAre7Vd2T74SD9xhEGJVwYfTPDhN | 7 | 0.86811787 |
| 1HwJeZ5uyNJ6Peq8x1wixKVnurY1yURK8P | 1 | 0.11707884 |
| 1Mh8T6eVbP8zCRPzUqbb7b9PiW6Wv3mRPY | 1 | 0.13190313 |
| 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ | 2 | 0.05092411 |
| 1PcZSbbc4u4juK64mpFSWwcR9hESPboRH8 | 1 | 0.00026772 |
| 1AEb2hcPpxDs89AJojyySyiZdW4vdEumZN | 1 | 0.11631063 |
| 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS | 6 | 0.94066411 |
| 18jZzWe4Wv4mUNm93rjeWJscqPdhecwsAY | 1 | 0.06811331 |
| 1CEi7Py9hNgMwqPMiCphFuF6SF263v7Yqj | 1 | 0.01378845 |
| 1AiBJcWZYQrz5Z9S9X7nYNueznU7iU5V5h | 2 | 0.26333251 |
| 1EwCEJr5JwpafZx11dcXDtX5QSPJvzth17 | 2 | 0.01003783 |
| 1HctxwLwjEFCacTPi83me927UBs7aTJ7LF | 9 | 0.40123518 |
| 14AuMKdDV5s6xmGa13xw6F9hc1CwntkcfT | 1 | 0.22131225 |
| 14poC1Jg97vuvsyoKSZYz7h276LoAZcrtn | 1 | 0.323483 |
| 1NpjBxiLhQQ5VVyDMrxESoA5HoHLLQXABa | 1 | 0.13428185 |
| 12KkDhdBX2zNv24D7SgBBrEBme7eNddvUj | 2 | 0.07116557 |
| 1JrdZLfH6j9KP2GjCJc7PhxwrrYKGYoSEi | 1 | 0.08167012 |
| 1Fjg3Q89MawTyfNcMbX6MUnfT923icRuMy | 2 | 0.1682459 |
| 1L9H1CtLsDCTtuvdE9hqpm9BD72jYBtvDF | 4 | 1.38988033 |
| 1PuxZLDEz2as13NKcTzC2BGadF2g2zhdfo | 1 | 0.00165365 |
| 1DZNohaDckSxJu6YxfeGkqCtxDAhtFP3Jq | 3 | 0.44394538 |
| 19razyqXme4evPi2wS9Zf8kor3VaYG8dTN | 8 | 0.24317082 |
| 1CWHmuF8dHt7HBGx5RKKLgg9QA2GmE3UyL | 3 | 0.23316271 |
| 1FqAEDNBFFjBZuVzk7V94tKgGwhVa8qABt | 1 | 0.05575892 |
| 1BXavFhbxCpno2dFpS4BU4NvEJjjqCN8Kd | 3 | 0.15631682 |
| 1164VJYmR8nP8z1NSPHqQreVWCMq2QdqUJ | 5 | 0.34881132 |
| Total | 158 | 14.4539 |
Table 2 – BTC wallets used in the sextortion campaign.
Given the number of incoming transactions to these wallets, we can also estimate the total number of victims affected by this campaign. Therefore, we can conclude that approximately 150 victims paid the blackmail demand over the span of five months. Considering the number of emails that the spam bot is capable of generating, despite the low numbers of payments received, this still means this simple scam technique was successful.
On the other hand, passwords from leaked databases, such as those used in the sextortion campaign, are most often not related to victims’ email accounts. Therefore, the value of this data is quite low. Such databases are sold at a low price, or may even be freely accessible. The Phorpiex actors came up with a method of using such low quality data to earn a respectable amount of profit.
Conclusion
Leaked credential lists, containing passwords that are often not compatible with their linked email addresses, are a common and inexpensive commodity. Phorpiex, a veteran botnet, has found a way to use them to generate easy income on a long term basis. This new activity might be connected with the termination of Gandcrab, a ransomware that Phorpiex used to distribute, or just because plain text emails still manage to infiltrate many cyber defense lines. In any case, Phorpiex, which currently operates more than 500,000 infected hosts, is continuously propagating sextortion emails – by the millions.
IOCs
| Pre-infection URLs |
| hxxp://185.176.27[.]132/5 |
| hxxp://185.176.27[.]132/4 |
| hxxp://185.176.27[.]132/3 |
| hxxp://193.32.161[.]73/5 |
| hxxp://193.32.161[.]73/4 |
| hxxp://193.32.161[.]73/3 |
| hxxp://193.32.161[.]69/6.exe |
| hxxp://193.32.161[.]77/5.exe |
| hxxp://osheoufhusheoghuesd[.]ru/3.exe |
| hxxp://193.32.161[.]77/6.exe |
| hxxp://osheoufhusheoghuesd[.]ru/4.exe |
| hxxp://ouhfuosuoosrhfzr[.]su/2.exe |
| hxxp://ouhfuosuoosrhfzr[.]su/3.exe |
| hxxp://ouhfuosuoosrhfzr[.]su/4.exe |
| hxxp://osheoufhusheoghuesd[.]ru/5.exe |
| hxxp://193.32.161[.]77/4.exe |
| hxxp://193.32.161[.]69/5.exe |
| hxxp://193.32.161[.]69/7.exe |
| MD5 | C&C URL |
| 790b14490eb56622f3cfa768887fcb08 | hxxp://193.32.161[.]77/oaa/ |
| b5dffcdf23ea0365c0bbf6e70983d351 | hxxp://193.32.161[.]77/from/ |
| a267bf9e58726a34a91c365b61e1424a | hxxp://92.63.197[.]153/test2/ |
| 5c17496674a49f7ebaa44c5b33d32ae4 | hxxp://193.32.161[.]77/3/ |
| f1a69224571f7749f261fd8c08d6d8cb | hxxp://193.32.161[.]77/2/ |
| 8887f6f532a489fcab28eba80185337b | hxxp://193.32.161[.]77/fu/ |
| c58bd54c962d4e236e770df983fd2329 | hxxp://193.32.161[.]69/111/ |
| 9398682b9740d15dfb7b2996364cd979 | hxxp://92.63.197[.]153/sp/ |
| 9434796df2d62e4f666525419db86d18 | hxxp://193.32.161[.]77/neww/ |
| 7f52a1c1d63053bcf02c6225e4245345 | hxxp://92.63.197[.]153/t2/ |
| 69076366f1a1bd622c0d813709f29e4a | hxxp://87.120.37[.]234/ |
| fc729a08001392406565808408cf6166 | hxxp://193.32.161[.]77/dsh/ |
| 8a74d531fa839caf056a7a9c24237cd7 | hxxp://193.32.161[.]77/send/ |
| 1f4447c12a0b8f99c1ce5b748c762a9f | hxxp://92.63.197[.]153/t/ |
| a2d30294e59cd15304d071c396618fa7 | hxxp://193.32.161[.]77/mails/ |
| 646c630aa377f414e1e6820916952e1e | hxxp://193.32.161[.]77/sorry/ |
| ba24a030bd4d4b89a6ad16249d1674c2 | hxxp://193.32.161[.]77/2/ |
| 0d7f456f908565fb547438cb402a4eff | hxxp://193.32.161[.]77/en/ |
| 5b046452db5836deb47e359b4462ee16 | hxxp://92.63.197[.]153/sex-pass/ |
| 6628c07aadd53f34357b9b63e07d62b8 | hxxp://92.63.197[.]153/sex-pass-new/ |
| d7cfd3b8d83ca0af1518267a15f9c249 | hxxp://193.32.161[.]77/1/ |
| 9af3d711fd4733181fcd78796dd21cfa | hxxp://193.32.161[.]77/en2/ |
| Email subjects |
| I know your password – |
| Your password – |
| You dirty pervert – |
| Pervert – |
| I hacked you – |
| You got owned – |
| You better read this – |
| You better pay me – |
| Video of you – |
| I recorded you – |
| Stop watching porn – |
| Dirty pervert – |
| You got hacked – |
| I know everything – |
| You got infected – |
| I infected your pc – |
| Take care – |
| Better pay me – |
| Safe your life – |
| Safe your privacy – |
| I can ruin your life – |
| Read carefully – |
| I give you one chance – |
| Recorded you mastrubating – |
| I seen everything – |
| Videos of you – |
| You got recorded – |
| Infected your computer – |
| Your life can be ruined – |
| Take care next time – |
| Pay – |
| Few days time – |
| Don’t wait too long – |
| I won’t wait too long – |
| Everyone will know – |
| No longer private – |
| Better read – |
| Read – |
| Your private data – |
| Your privacy – |
Check Point Anti-Bot blade provides protection against this threat:
Worm.Win32.Phorpiex.C
Worm.Win32.Phorpiex.D
Worm.Win32.Phorpiex.H





