Last month, Check Point researchers were able to spot the distribution of Jaff Ransomware by the Necurs Botnet. The ransomware was spread using malicious PDF files that had an embedded docm file, which in its turn downloaded an encoded executable. After the downloaded file was decoded, the ransomware encrypted the user’s files. In the last weeks, however, we were able to detect a new spam campaign delivering the ransomware and altering the chain of infection to use malicious WSF files.
New Campaign
On May 28, Check Point SandBlastZero-Day Protection solution caught 8,000 messages delivering the ransomware, titled “Scanned Image from a Xerox WorkCentre,” a title which was in use in old spam campaigns dating back to 2013.
Previous Campaign Current Campaign
Infection Chain
A zipped folder including a WSF file is attached to the spam messages in the new Jaff campaign. The WSF file contains an obfuscated JavaScript, which parses various encoded strings; including hardcoded URLs from which it attempts to download the Jaff ransomware executable:
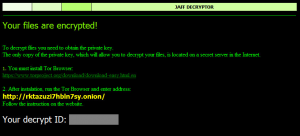
When the ransomware executes, a “.wlu” extension is appended to encrypted files’ names, as in a former Jaff campaign. In addition, the ransom note, which differs from former campaigns, is displayed on the victim’s screen.
The ransomware’s decryptor service must be accessed through the Tor Browser, as in the last Jaff campaign, and the requested ransom amount is 0.5486BTC (approximately 1530USD, June 7), lower than what was demanded by the Jaff distributers in previous campaigns.
Given the fact that the ransomware is still also being delivered by the Necurs Botnet using PDF files with embedded docm files, the recent changes mentioned in this article can suggest that Jaff may be functioning as a RaaS (Ransomware-as-a-Service), distributed by several threat actors.
Check Point customers are protected from Jaff ransomware by SandBlast, IPS, Anti-Bot and Anti-Virus.
The IPS signature that protects against this campaign is: “Suspicious Microsoft Office File Archive Mail Attachment”.
Anti-Virus and Anti-Bot signatures include Trojan-ransom.Win32.Jaff.*.