
- Check Point Research Publications

Research By: Liron Yosefian and Ori Hamama, Network Research Introduction Check Point Researchers ...
- Check Point Research Publications
- Threat Research

code, kbd, tt, var { font: 15px Monaco, Consolas, "Andale Mono", "DejaVu Sans Mono", monospace; ...
- Check Point Research Publications
- Threat Research

Italian company exposed on Clearnet earned up to $ 500,000 helping cybercriminals to deliver malware using ...
- Check Point Research Publications
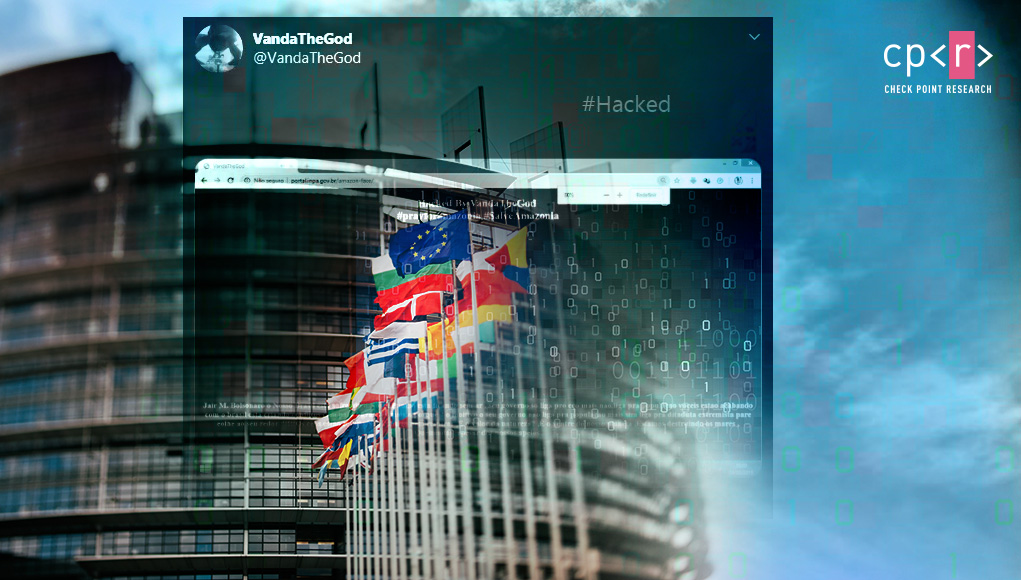
Introduction Since 2013, many official websites belonging to governments worldwide were hacked and defaced by an ...
- Check Point Research Publications

Research by: Eyal Itkin Overview One of our goals for every research project we work on in Check Point ...
- Check Point Research Publications
- Global Cyber Attack Reports
- Threat Research

Research by: Eyal Itkin Overview During 2019, we published our research on the Reverse RDP Attack: Part 1 ...
- Check Point Research Publications
- Threat Research

code, kbd, tt, var { font: 15px Monaco, Consolas, "Andale Mono", "DejaVu Sans Mono", monospace; ...
- Check Point Research Publications
- Threat Research

Research By : Netanel Ben-Simon and Yoav Alon Background: In our previous research , we used WinAFL to ...


