THE TAKEAWAY:
Check Point’s latest Global Threat Impact Index revealed more than one in four organizations globally was affected by the Fireball or Wannacry attacks during May.
The top three malware families were zero-day, previously unseen attacks. In rank order based on impact to networks globally, they are:
- Fireball: 20%
- RoughTed: 16%
- WannaCry: 8%
IN CONTEXT:
The most prevalent malware highlight that cyber-criminals are utilizing and impacting all stages of the infection chain with a wide range of attack vectors and targets. Fireball takes over target browsers and turns them into zombies, which it can then use for a wide range of actions including dropping additional malware, or stealing valuable credentials. In contrast, RoughTed, a large-scale malvertising campaign, and WannaCry, which takes advantage of a Windows SMB exploit called EternalBlue in order to propagate within and between networks. WannaCry was particularly high profile, bringing down networks on parts of Britain’s National Health Service (NHS), Spain’s Telefónica, FedEx and Deutsche Bahn.
May 2017’s Top 10 ‘Most Wanted’ Malware:
*The arrows relate to the change in rank compared to the previous month.
1. ↑ Fireball – Browser hijacker that can be turned into a full-functioning malware downloader. It is capable of executing any code on the victim machines, resulting in a wide range of actions from stealing credentials to dropping additional malware.
2.↑ Roughted – Large-scale Malvertising used to deliver various malicious websites and payloads such as scams, adware, exploit kits and ransomware. It can be used to attack any type of platform and operating system, and utilizes ad-blocker bypassing and fingerprinting in order to make sure it delivers the most relevant attack.
3.↑ WannaCry – Ransomware which was spread in a large scale attack in May 2017 utilizing a Windows SMB exploit called EternalBlue in order to propagate within and between networks.
4.↓ Slammer – Memory resident worm targeted to attack Microsoft SQL 2000. By propagating rapidly, the worm can cause a denial of service condition on affected targets.
5.↓ HackerDefender – User-mode Rootkit for Windows, can be used to hide files, processes and registry keys, and also implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means.
6. ↓ Conficker – Worm that allows remote operations and malware download. The infected machine is controlled by a botnet, which contacts its Command & Control server to receive instructions.
7.↑ Kelihos – Botnet mainly involved in bitcoin theft and spamming. It utilizes peer-to-peer communications, enabling each individual node to act as a Command & Control server
8.↑ Jaff – Ransomware which began being distributed by the Necrus botnet in May 2017.
9.↓ Rig ek – Exploit Kit first introduced in 2014. Rig delivers Exploits for Flash, Java, Silverlight and Internet Explorer. The infection chain starts with a redirection to a landing page that contains JavaScript that checks for vulnerable plug-ins and delivers the exploit
10. ↓ Cryptowall – Ransomware that started as a Cryptolocker doppelgänger, but eventually surpassed it. After the takedown of Cryptolocker, Cryptowall became one of the most prominent ransomwares to date. Cryptowall is known for its use of AES encryption and for conducting its C&C communications over the Tor anonymous network. It is widely distributed via exploit kits, malvertising and phishing campaigns.
In mobile malware, Hummingbad returned to first place and was closely followed by Hiddad and Triada:
Top 3 ‘Most Wanted’ mobile malware:
- Hummingbad – Android malware that establishes a persistent rootkit on the device, installs fraudulent applications, and with slight modifications could enable additional malicious activity such as installing a key-logger, stealing credentials and bypassing encrypted email containers used by enterprises.
- Hiddad – Android malware which repackages legitimate apps and then released them to a third-party store. Its main function is displaying ads, however it is also able to gain access to key security details built into the OS, allowing an attacker to obtain sensitive user data.
- Triada – Modular Backdoor for Android which grants superuser privileges to downloaded malware, as helps it to get embedded into system processes. Triada has also been seen spoofing URLs loaded in the browser.
The findings show that the threat of ransomware is not going away. Organizations need to remember the financial impact from an attack goes far beyond the initial incident. Restoring key services and repairing reputational damage can be a very long and expensive process. Organizations in every industry sector need a multi-layered approach to their cybersecurity. Check Point’s SandBlast™ Zero-Day Protection and Mobile Threat Prevention protects against the widest range of continually evolving attack types, while also protecting against zero-day malware variants.
Check Point’s Global Threat Impact Index and its ThreatCloud Map are powered by Check Point’s ThreatCloud intelligence, the largest collaborative network to fight cybercrime. This index delivers threat data and attack trends from a global network of threat sensors. The ThreatCloud database holds over 250 million addresses analyzed for bot discovery, more than 11 million malware signatures, over 5.5 million infected websites, and identifies millions of malware types daily.
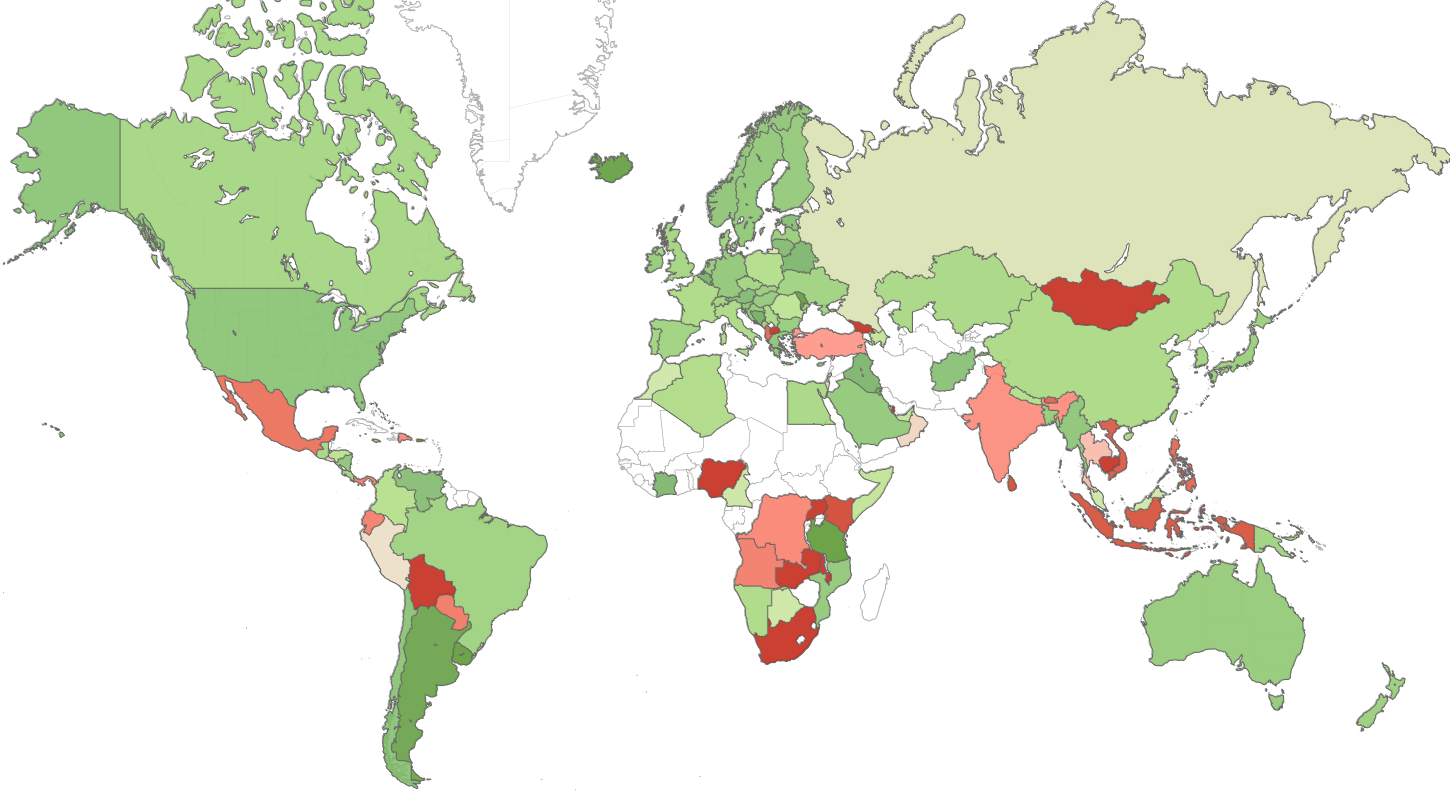
Threat Index per country
The map below displays the risk index globally (green – low risk, red- high risk risker, white – insufficient data), demonstrating the main risk areas around the world.