On August 8th, a new ransomware, dubbed ‘RansomWarrior’, was found by the Malware Hunter Team.
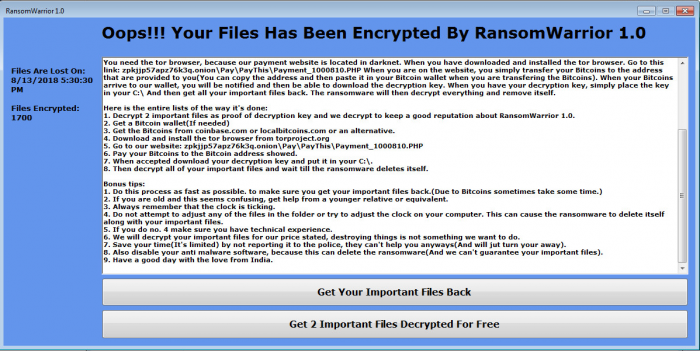
Going by the ransom note shown to its victims, RansomWarrior seems to have been developed by Indian hackers, who would appear to also not be so experienced in malware development. Written in .NET, the executable itself isn’t obfuscated, packed, or otherwise protected, suggesting those behind it are relatively new to the game.
In fact, the “encryption” used by the Ransomware is a stream cipher using a key randomly chosen from a list of 1000 hard-coded keys in RansomWarrior’s binary code.
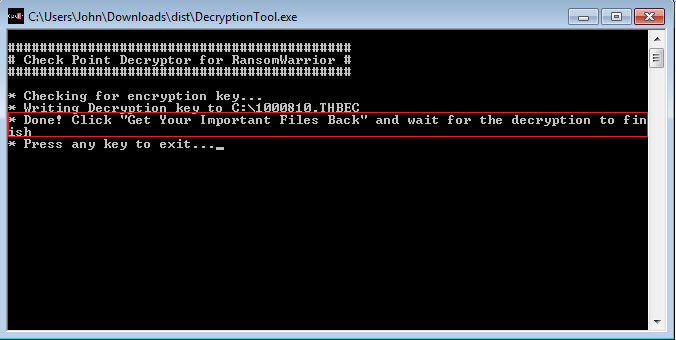
As a result, the Check Point Research team has been able to extract those keys, and, as the key’s index is saved locally on the victim’s computer, provide the correct keys to the Ransomware itself in order to unlock the files. Below is a Decryption Tool available for download, along with a usage guide, for anyone infected by RansomWarrior.
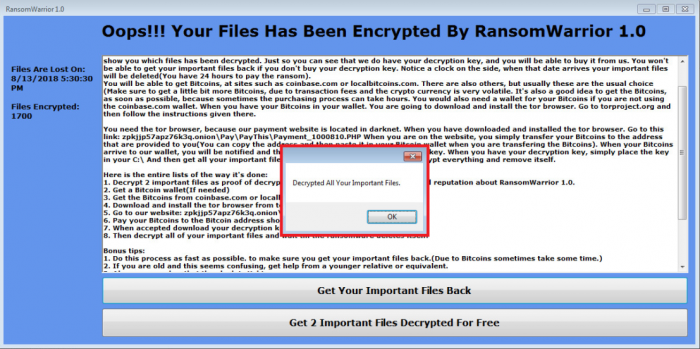
The ransom note shown to victims infected by RansomWarrior.
How to decrypt the ransomware:
First you will need to download the Decryption Tool here: RansomWarrior_Decryption_Tool.
Password: ‘infected’
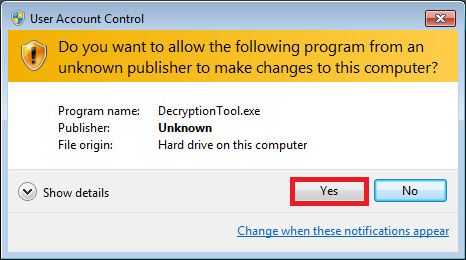
- Right click on the decryption tool to execute it ‘as administrator’
2. Click ‘Yes’ to approve execution as admin.
3. After being prompted with this message:
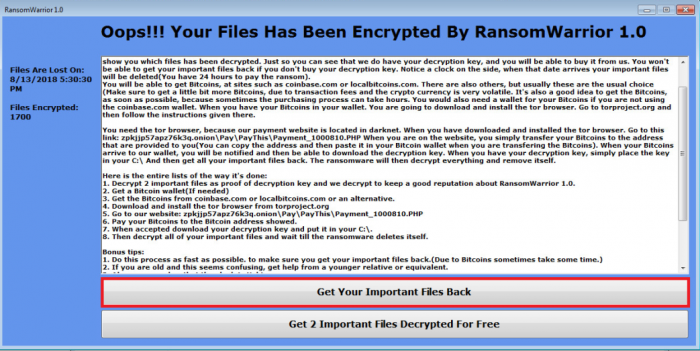
4. Go to the original ransom note and click the “Get Your Important Files Back” button.
5. Once the decryption process will be completed you will be prompted with this message: