Research by: Nikita Fokin, Israel Gubi, Mark Lechtik
On 17th September Check Point Research found a new online builder, dubbed ‘Gazorp’, hosted on the Dark Web. Gazorp is designed for building binaries of the popular malware, Azorult, an infostealer used for stealing user passwords, credit card information, cryptocurrency related data and more. Furthermore, the Gazorp service is provided free of charge and gives threat actors the ability to create fresh Azorult samples and corresponding panel server code, leaving them simply to provide their Command & Control (C&C) address. This address gets embedded into the newly created binary, which in turn can be distributed in any way the threat actor sees fit.
Our analysis of the built malware reveals that Gazorp effectively generates samples of Azorult version 3.0, which was known to be distributed five months ago. Since then, the malware was updated twice, and the subsequent versions, 3.1 and 3.2, were released and observed in the wild, making the version built by Gazorp obsolete. Even so, the outdated version has multiple stealing capabilities which can be leveraged by any actor to gather victim information and misuse it, as well as containing multiple upgrades and enhancements to the malware’s C2 panel code.
The Timing of Gazorp’s Release
An interesting thing to note about the builder is the timing of its release. Gazorp’s emergence on the Dark Web was preceded by a code leak of Azorult’s panel (for versions 3.1 and 3.2). Indeed, this leak allows anyone who wants to host an Azorult C&C panel to be able to do so with moderately low effort. The leak also contained a builder for the latest version of the malware, which did not appear to be the original one used by its authors. Instead, it merely encoded and placed the C&C address string given to it as an argument by the user to a particular field in a ready-made binary. It is possible then that the simple mechanism and the overall delivery of the recent versions to the public inspired Gazorp’s authors to introduce it online.
Another point to note is that the online builder links to a Telegram channel where the activity of its creators is visible to the public. People who participate can get updates on the project and suggest their own ideas for improvement. Also, the authors encourage users to donate money to their project by issuing transactions to a particular bitcoin wallet, which seems to be the only way to monetize Gazorp (as its usage is completely free). In return, they claim, the users will benefit from more development and upgrades from their side (or in their own words – “more donations, more updates”).
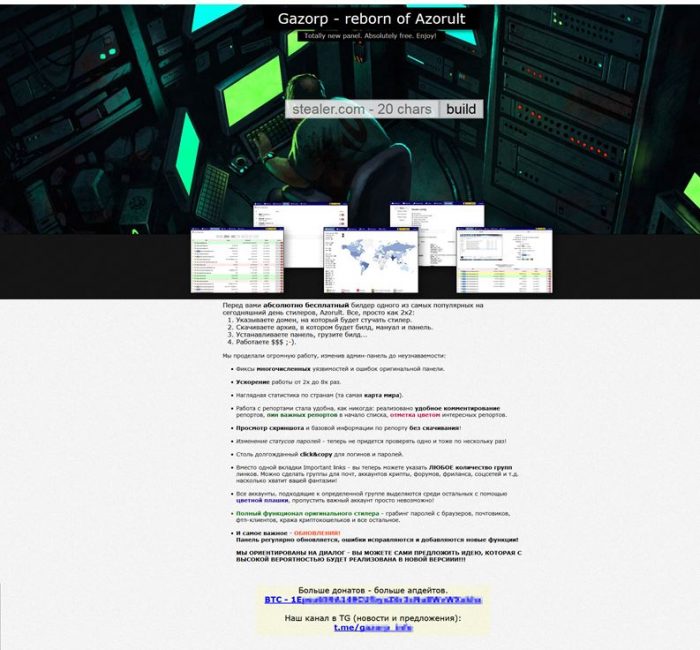
Figure 1: Gazorp’s page on the Dark Web.
The first paragraph in the builder’s page above specifies the simple actions required to be taken by any user who wishes to use it. It translates to the following:
“Totally free builder of one of the most popular stealers today, Azorult is right here. It’s as simple as 2×2:
1. Specify the domain to which the stealer will report.
2. Download the archive which will consist of the build, a manual and panel.
3. Install the panel, deploy the build.
4. Work $$$ ;-).”
Additionally, the authors attempt to portray the enhancements they introduced to the malware panel as the most prominent value provided by them in this project. Azorult’s panel for version 3 was also leaked in the past and uploaded to Github, providing the opportunity for crooks and cyber criminals to misuse it.
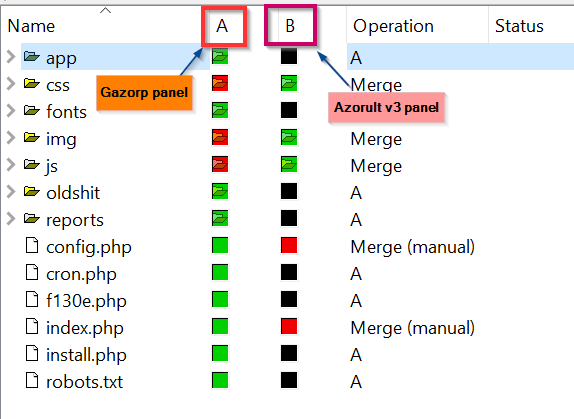
Changes to the panel, as the authors state, include multiple vulnerability and bug fixes, better performance, visual enhancements and a variety of new features. Indeed, if we diff the source code trees for both panels we can witness major differences and additions in Gazorp.
Figure 2: Code tree differences between Gazorp and Azorult v3 panels. The black squares indicate absent code directories from the Azorult tree.
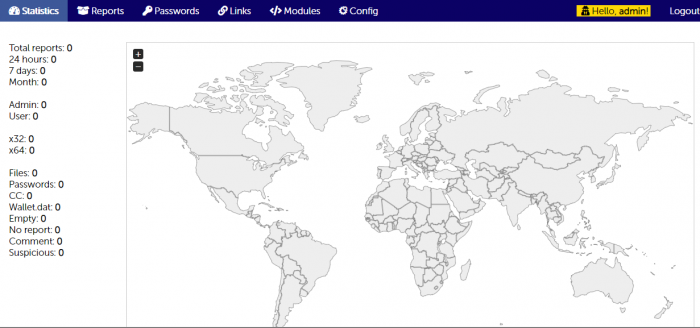
In reality, Gazorp’s panel’s look is far less enticing than promised. The main statistics page looks quite dull in comparison to that of Azorult v3, and its main improvement on its counterpart is the global heap map that provides statistics by country in a way that wasn’t accessible in the Azorult panels.
Figure 3: Gazorp’s main panel menu, with the new global statistics feature.
Figure 4: Azorult version 3 main panel menu.
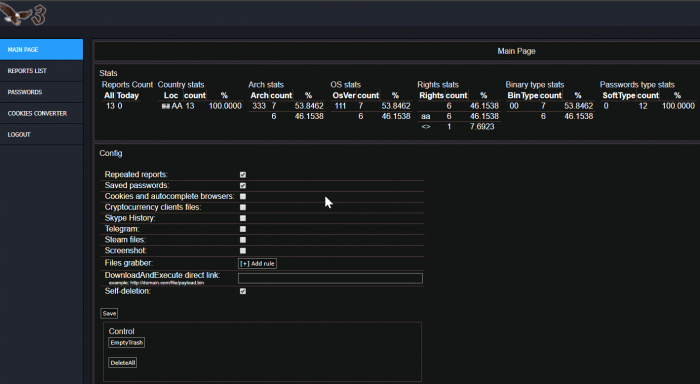
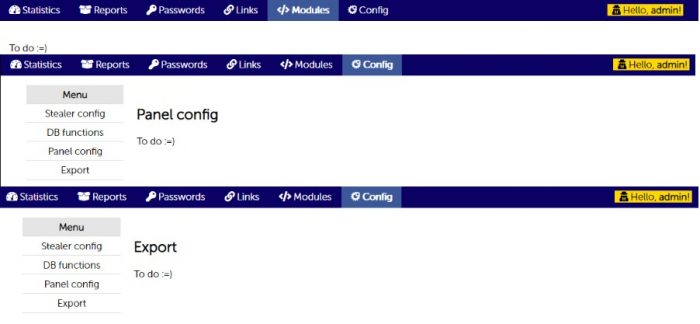
Apart from the suggested modifications, there are quite a lot promised features for the future. For instance, the authors incorporated a ‘modules’ section which suggests the ability to extend Azorult with new capabilities, but it is not yet implemented. They also offer more casual panel features like the ability to configure the panel and export the various databases to a file. These are also not available yet and are expected to be added as the project develops.
Figure 5: Planned panel features.
Usage of the Azorult v3.0 Binary
As stated before, Gazorp seems to produce a duplicate of Azorult’s v3.0 binary which has been analyzed before by Cert.lu (https://malware.lu/articles/2018/05/04/Azorult-stealer.html).
This version of Azorult, as produced by Gazorp, can be identified by several distinctive features:
- Every version of Azorult has a unique mutex which the malware creates at the beginning of execution. Azorult v3.0 in particular creates a mutex name which is a concatenation of the authorities of the current user (A-admin, U-user, S-system, G-guest) and the string “d48qw4d6wq84d56as”.
Figure 6: Azorult v3.0 and Gazorp mutex as well as C2 server names.
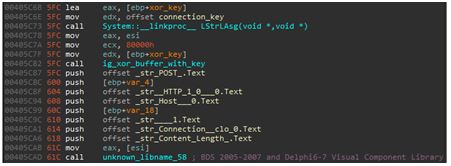
- Azorult encrypts its connection with the C2 server using a simple XOR method with a key hardcoded in file. Every version of Azorult has a different key. In the case of v3.0 its 0xfe, 0x29, 0x36.
Figure 7: Gazorp and Azorult 3.0 connection method and key.
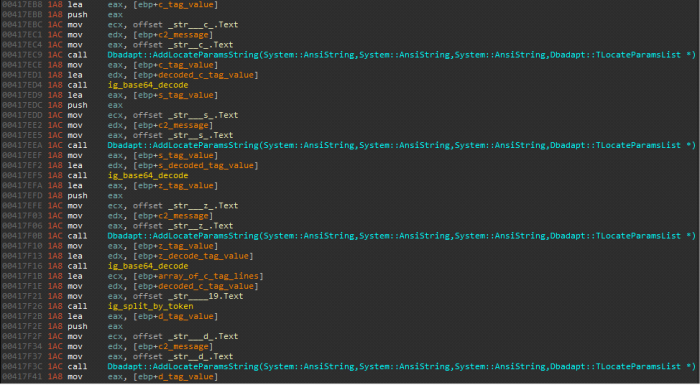
- The decrypted return message from the C2 server consists of tags. In version 3.0, the returned message has the following tags:
<c> configuration_data</c>
<s>Sqlite3_file</s>
<z>zip_functions_file</z>
<d>names_of_softwares_to_steal_credentials_from</d>.
The values between the tags are decoded with Base64.
Figure 8: Azorult v3.0 and Gazorp interpreting the received C2 message by tags.
Epilogue:
This new shady service gives an example for the ease of accessibility to some common malware in the web. For now, it seems we are looking at a very early version of the Gazorp service (0.1), where the main product delivered is an enhanced Azorult C&C panel code. However, we do expect the project to evolve with time, and possibly produce new variants for Azorult.
Given that the service is free, it is also possible that new campaigns with Gazorp built binaries will start to emerge in higher scale in the wild. We will keep monitoring this threat and provide any insights on our research blog when such will come up.