Labeless, a plugin for both IDA and popular debuggers, is an invaluable tool in the researcher’s tool kit. In this first part of a four part series, we will be mainly introducing Labeless and covering the following:
- What is Labeless?
- What can be done with this tool.
- What are its features.
- What else will be covered in this series.
Let’s get started then and dive straight in.
Labeless is a plugin for both IDA and popular debuggers and resides here.
Labeless allows us to enrich a research database in IDA with dynamic debugging info which is not available during static analysis – with the help of side debugger.
What can be done with this tool?
These are some of the tasks we have solved with the help of Labeless:
- Automatically resolved WinAPI calls in LockPos Point-of-Sale malware without reconstructing Import Address Table;
- Decrypted strings in Boleto banking malware without knowing the encryption algorithm;
- Resolved function names by hashes in Ramnit Trojan malware without knowing the hashing algorithm.
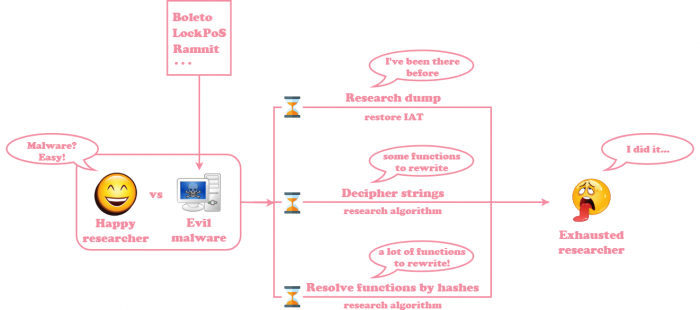
The main feature of this tool is keeping the researcher happy by saving his or her time. Consider these two cases, researching malware without Labeless:
And the case of researching the same malware samples with Labeless: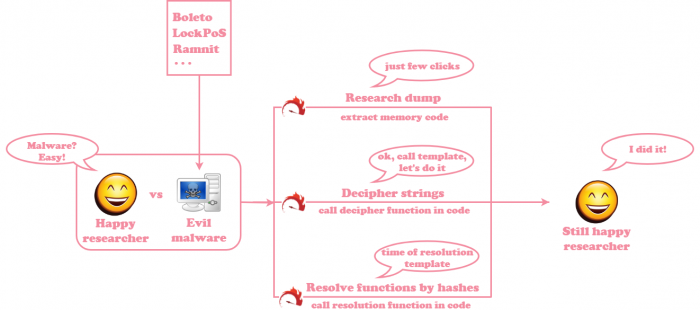
While Labeless is not a panacea, it is certainly able to ease extracting pivotal malware details.
Other features of the plugin include:
- Dumping of debugged process memory regions with auto resolution of WinAPI calls – disregarding present or absent Import Address Table (IAT); this can be useful in the following cases:
- When a debugged process has extracted/temporary/injected module which doesn’t appear in modules list.
- When an executable with non-valid PE header resides in this memory region.
- When an IAT of such an executable is corrupted.
- Propagating names and comments from IDA database to debugger. This doesn’t depend on possible differences in image bases in IDA and debugger.
- Auxiliary feature of one-click code navigation from IDA to debugger and vice-versa.
- Python scripting with the following possibilities:
- Dynamic execution of code in debugger, reading memory and registers, propagating these results to IDA side.
- Full IDA scripting with feature of applying results from dynamic code execution to static IDA database.
The Labeless plugin supports PE/AMD64 binaries.
We will discuss each of the featured aspects in greater detail throughout these series, applying them to solving real cases issues encountered during malware analysis.
What will be covered in these series?
Explaining the real cases mentioned in `What can be done with this tool?` section, the following topics will be discussed:
- Part 1: Introduction
- Part 2: How to install and use Labeless;
- Part 3: How to dump and auto-resolve WinAPI calls in LockPos Point-of-Sale malware;
- Part 4: How to decrypt strings without reconstructing the algorithm in Boleto banking malware;
- Part 5: How to resolve function names by hashes without reconstructing the algorithm in Ramnit trojan malware.
If it sounds like a plan, continue to the next part of these guides – and make sure to have fun along the way!