

By Dikla Barda, Roman Zaikin and Yaara Shriki
Background:
Some of the latest news regarding WhatsApp vulnerabilities are relating to a manipulation of the WhatsApp protocol using a tool built by Check Point Research in order to validate WhatsApp security without jeopardizing WhatsApp end to end encryption. This tool allows a user to modify WhatsApp messages before being sent and change the general parameters, such as participant’s phone number.
In the blog post (https://research.checkpoint.com/black-hat-2019-whatsapp-protocol-decryption-for-chat-manipulation-and-more/) we discussed how a threat vector could manipulate messages to their own advantage. In this blog post we will further investigate how a threat vector can use the tool in order to obstruct access to WhatsApp messenger for a group of users by causing a crash-loop.
The bug was discovered in August 2019 and responsibly reported to WhatsApp whose developers fixed the bug in the update for version 2.19.58 and onwards.
Technical Details:
A year after the previous WhatsApp research, the team was eager to dig back in and find new vulnerabilities in the app. We set up the WhatsApp Manipulation Tool and started testing new ways to manipulate WhatsApp protocol.
In this blog we will describe in detail the technique used in our testing where one can crash WhatsApp on multiple phones in a shared group.
We will briefly go over how to set everything up so we can start the manipulation (More details in previous blog post).
First, we need to browse to WhatsApp Web and open Chrome’s DevTools. We will need to set a few breakpoints in places where the encryption keys are generated and then obtain them during the login process.
Second, we need to get the “secret” parameter from the traffic passing through Burp Suite Web Socket tab after the QR is scanned. This parameter holds the necessary data required for the manipulation part which was explained in the previous blog post.
Third, we need to start the local python server (can be found in the GitHub project) which awaits a connection. Once the python server receives a message, it decrypts it (by using our encryption keys) and sends it back to the Burp Suite WhatsApp Manipulation Tool in clear text.
Lastly, both the private and public keys, and the “secret” parameter obtained in the preceding steps are used within the Burp Suite Extension to connect to the python server.
We should now be able to start decrypting and modifying messages in a conversation where we participate. Now that we have everything set up correctly, we can start intercepting our messages. Once a message is intercepted we can decrypt it by using the extension.
We should see the decrypted message in JSON format:
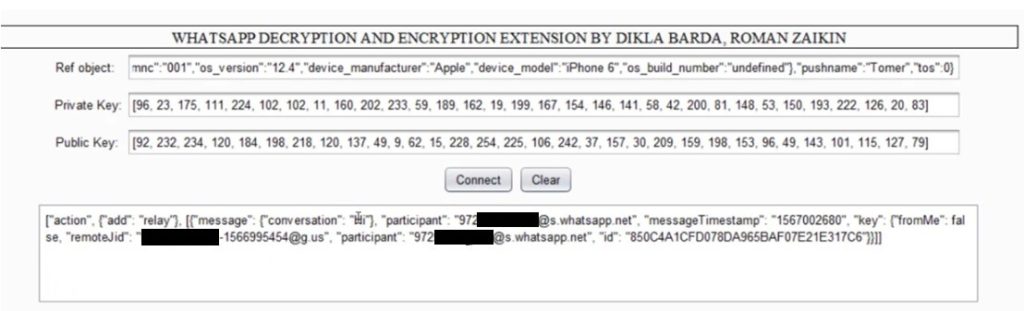
The bug resides in XMPP (Extensible Messaging and Presence Protocol), a communication protocol for instant messaging.
When we attempt to send a message where the parameter “participant” receives a value of “null” a ‘Null Pointer Exception’ is thrown.
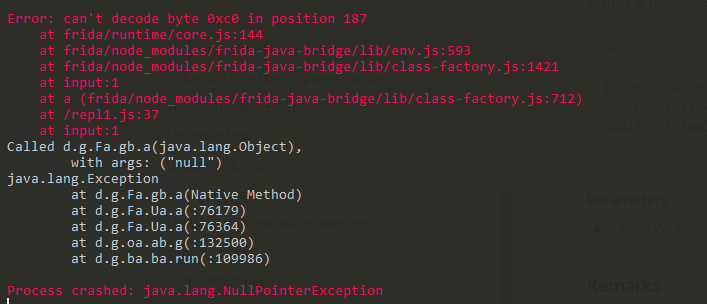
As can be seen in the stack trace, the function d.g.ba.ba.run handles all the message data, such as message id, participant’s details, etc.
The parser for the participant’s phone number mishandles the input when an illegal phone number is received. When it receives a phone number with length
not in the ranger 5-20 or a non-digit character it would read it as a ‘null’ string.
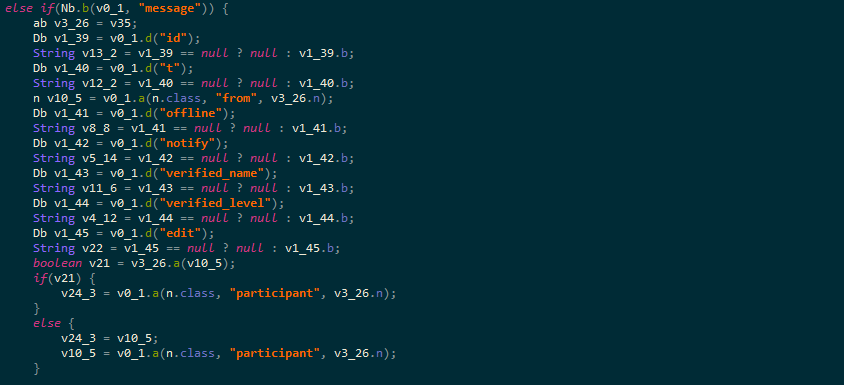
In a typical scenario, when a user in a WhatsApp group sends a message to the group, the application will examine the parameter participant to
identify who sent the message. While using our tool we were able to access this parameter and edit it.
In order to exploit this bug we would need to replace the participant’s parameter from the sender phone number to any non-digit character(s) e.g. ‘[email protected]’ as can be seen below:
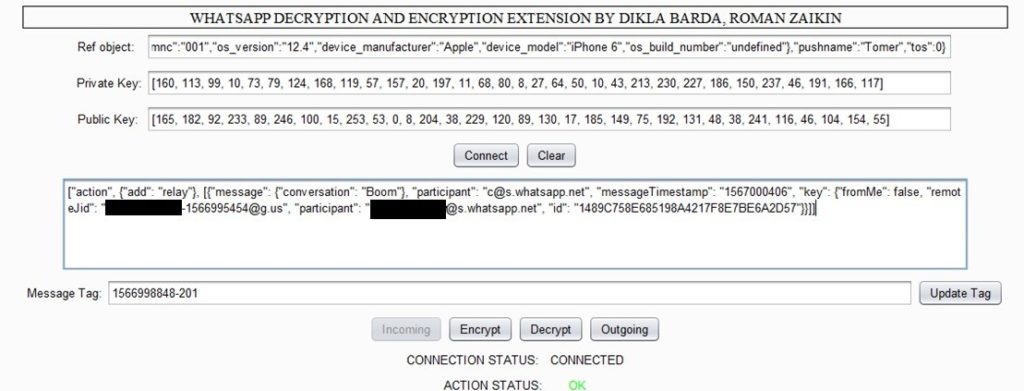
Which will look like this:
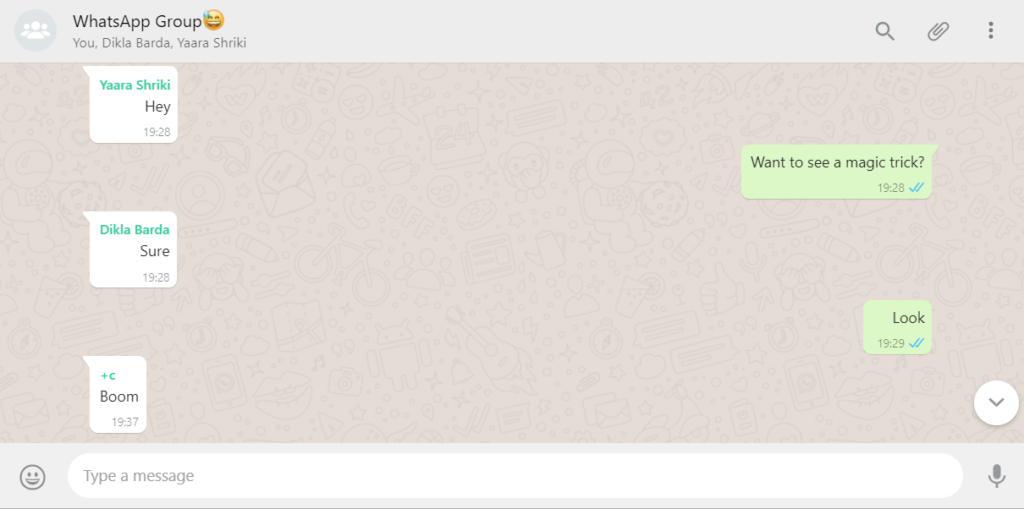
By sending this message WhatsApp application will crash in every phone that is a member of this group.
The bug will crash the app and it will continue to crash even after we reopen WhatsApp, resulting in a crash loop. Moreover, the user will not be able to return to the
group and all the data that was written and shared in the group is now gone for good. The group cannot be restored after the crash has happened and will have to be deleted in order to stop the crash.
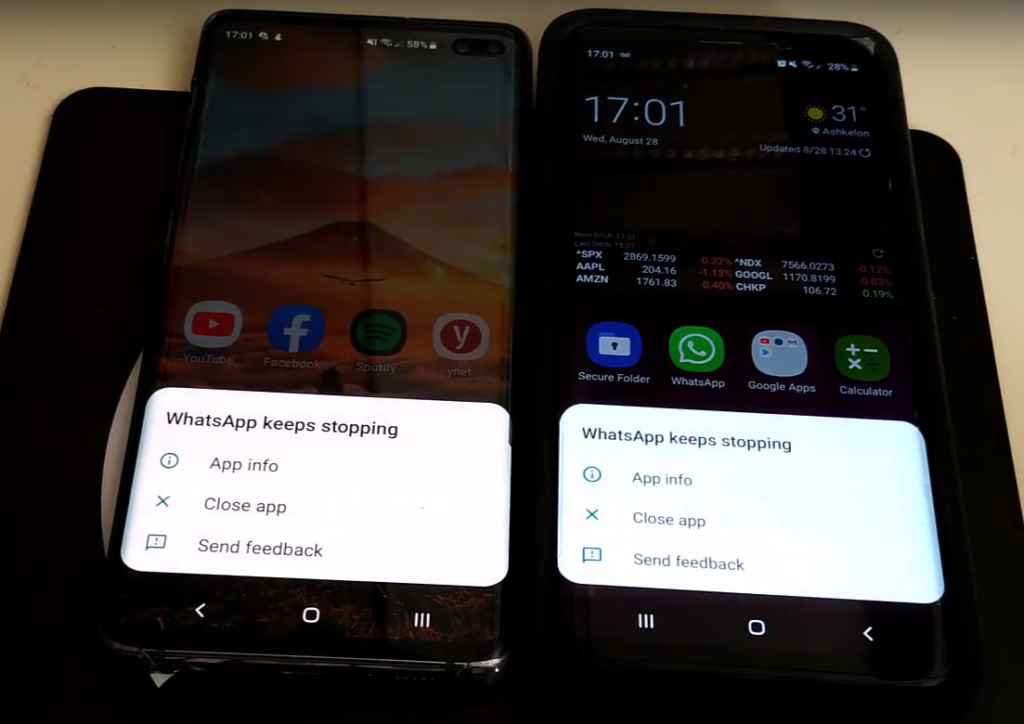
In WhatsApp there are many important groups with valuable content. If an attacker uses this technique and crashes one of these groups all chat history will be gone and further communication would be impossible.
The impact of this vulnerability is potentially tremendous, since WhatsApp is the main communication service for many people. Thus, the bug compromises the availability of the app which is a crucial for our daily activities.
In order to recover from the issue, the user have to uninstall WhatsApp, install it again and remove the group which contains the malicious payload.
Here is the PoC video with reproduction steps






