

By Oded Vanunu, Dikla Barda, Roman Zaikin
Unmasking Deceptive Tactics: A recent investigation by Check Point Research exposes a troubling trend in the cryptocurrency landscape. Deceptive actors are manipulating pool liquidity, sending token prices soaring by a shocking 22,000%.
$80,000 Heist Unveiled: The manipulation of pool liquidity resulted in a swift and calculated theft of $80,000 from unsuspecting token holders. This incident sheds light on the evolving strategies scammers employ to exploit decentralized finance platforms.
Continued Threat Landscape: This incident follows hot on the heels of a previously reported million-dollar scam. Check Point Research recently delved into the intricacies of a rug pull orchestrated through a fake token factory. For details on this preceding incident, visit Check Point Research: Unraveling the Rug Pull.
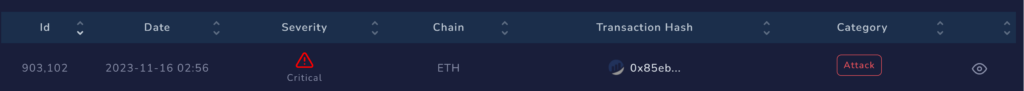
Check Point’s Blockchain Threat Intelligence system raised an alert on pool liquidity manipulation, resulting in a staggering token price increase of 22,000%. The malicious actor exploited the liquidity pool, stealing $80,000 from unsuspecting holders.
Check Point’sBblockchain Threat Intelligence system detected a malevolent transaction:
https://etherscan.io/tx/0x85ebb1b1d6f091a2d72c4cffb66beea0552a07b2efabb5fd53d4198f8d159b64
What did we find?
The scammer created two wallets:
- 0x48F7661E84A823505d683D092a2DccdA1e5aA119
- 0x151a2498826F9fe6f214C92bB1811f7d1153b630
Using the first wallet, they deployed the contract token WIZ (0x2ae38b2b47bf41ba4ab8f749b092fdd02b00bc1e) and its liquidity pool pair address (0x6e0367d897a8fd8bcbc44b4e2a14bafa904360aa), which included reserves of WETH and WIZ tokens. In the second wallet (0x151a2498826F9fe6f214C92bB1811f7d1153b630), the scammer created a malicious contract (0x796042E0032aC5247bc04A49102d49c5b5A5cF0c) designed to exploit a backdoor and manipulate the WIZ token price, resulting in an $80,000 theft from victims.
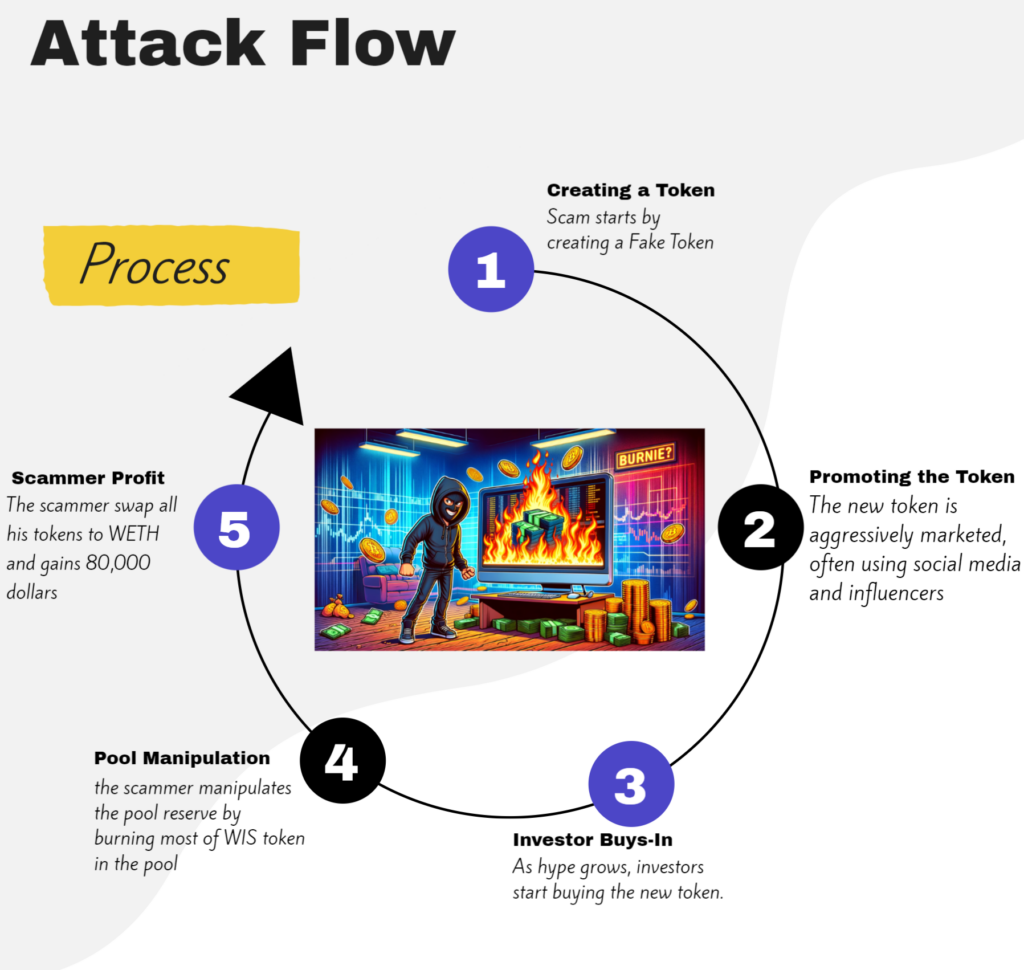
Method of Operation:
- Token Creation: The scammer launches a new cryptocurrency token, pairs it with a well-known cryptocurrency on a decentralized exchange (DEX), creating a liquidity pool.
- Token Promotion: Aggressive marketing, often leveraging social media and influencers, generates hype and attracts investors.
- Investor Participation: As investor interest grows, they start purchasing the new token.
- Pool Manipulation: After accumulating substantial investments, the scammer manipulates the pool reserve by burning most WIZ tokens, reducing the supply and temporarily inflating the token’s price by 22,000%.
- Scammer’s Gain: Exploiting the inflated price, the scammer sells a significant number of tokens, pocketing $80,000.
Technical Insights:
Liquidity pools
In the world of cryptocurrencies, you often need to swap one type of digital currency for another. But how do you do it easily and quickly without an intermediate? That’s where liquidity pools come in. Without these pools, you’d have to find someone willing to trade at the exact time and price you want, which can be difficult and time-consuming.
So how does a liquidity pool work?
Let’s break down the mechanics of a liquidity pool:
Picture a sizable digital reservoir holding two distinct cryptocurrencies—let’s call them Token A and Ethereum. This reservoir serves as an open arena where anyone can swap Token A for Ethereum or vice versa.
Now, when an individual decides to exchange Token A for Ethereum, they contribute Token A to the pool and withdraw an equivalent value of Ethereum. The dynamic pricing within the pool fluctuates based on the quantity of each token present. If there is an abundance of Token A but a scarcity of Ethereum, the value of Token A decreases while Ethereum’s value rises.
In the case at hand, the scammer manipulates the pool balance by burning tokens. Burning tokens within a liquidity pool, like the WIZ/WETH pool, can boost the token’s value by adhering to the core principles of supply and demand. As tokens are permanently removed from circulation, the overall supply diminishes.
Liquidity pools follows a formula that harmonizes the quantities of two tokens. When one token type (WIZ in this instance) undergoes reduction through burning, the relative value of the other token (WETH) in the pool escalates to maintain equilibrium. Failure to increase the amount of WETH leads to a substantial surge in the token price, particularly for WIZ.
Are you seeing how hackers or scammers exploit this method, known as liquidity pool manipulation, to sway token prices?
The crux of this strategy lies in the transient inflation of the token’s price within the liquidity pool. Given that decentralized exchange (DEX) prices hinge on asset ratios in the pool, diminishing one side (via burning) can ditort the price.
Liquidity pools become susceptible to exploitative tactics, including rug pulls or influencing contracts reliant on these pools for price data. This blog zeroes in on the former, unraveling the narrative of a scammer concealing a backdoor to manipulate the WIZ/WETH liquidity pool by incinerating their tokens.So, let us see what the scammer did:
The scammer runs the function ‘brr’ methodID (0x5606de36) on his malicious contract:
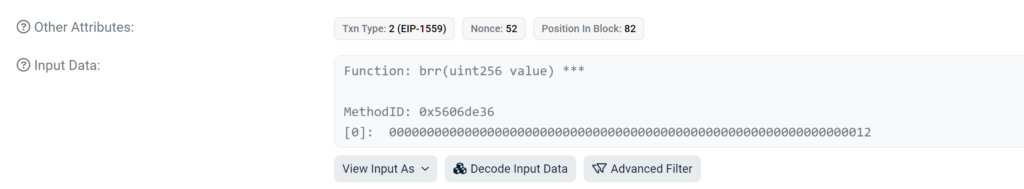
let’s see this function:
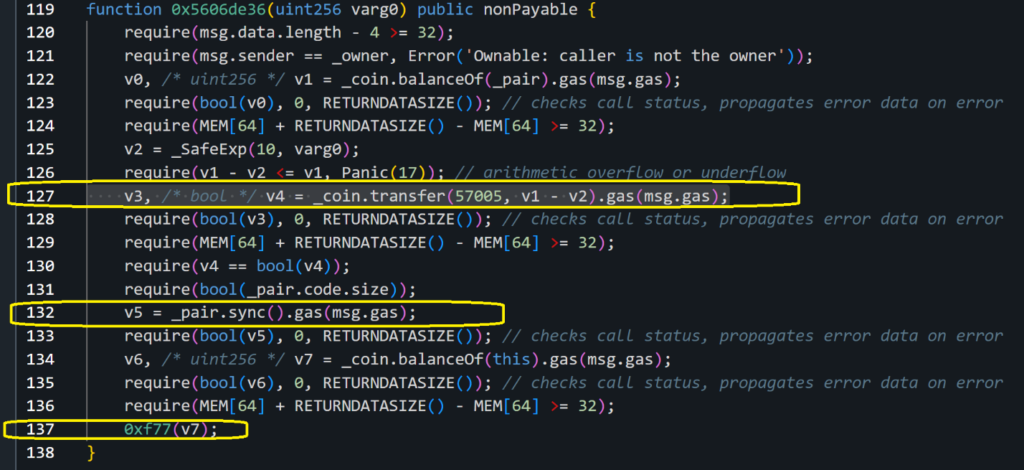
We can see on line 127 the scammer runs the transfer function on the _coin contract address, the _coin address will be set in an earlier function by the scammer to WIZ address: 0x2ae38b2b47bf41ba4ab8f749b092fdd02b00bc1e
Using this transfer function, the scammer was able to burn the WIZ tokens on the pool, let us understand how :
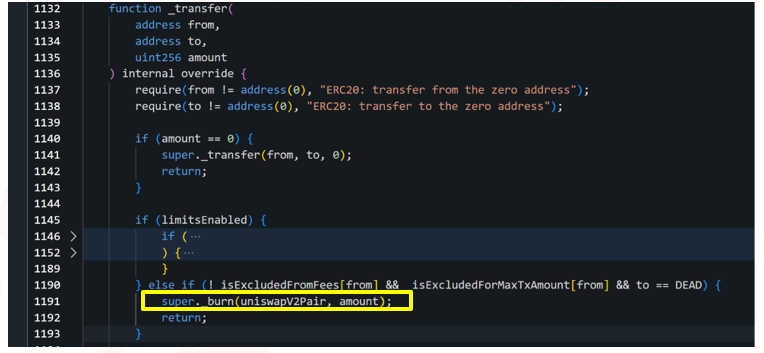
In order to get to the _burn function the scammer will have to pass a few checks, which we will explore now:
The first check he will need to go through is limitsEnabled, this would have needed to be set to False in order for the scammer to get to the second check.
for limitsEnabled to be False, the scammer needed to run the function called ‘removeLimits’
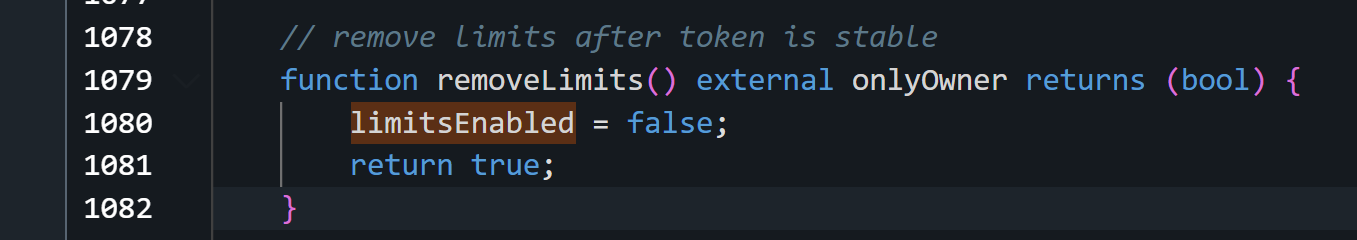
So this is how the scammer passes the first check.
Now let us look at the second check, in this, the ‘from’ address needs to return False on the ExcludeFromFees and True for isexcludedForMaxTxAmount,
since both functions _isExcludedFromFees and _isExcludedForMaxTxAmount are public, we can run them with the scammer contract address as input and check the results:
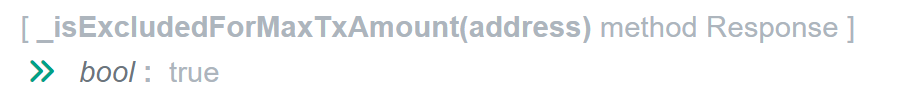
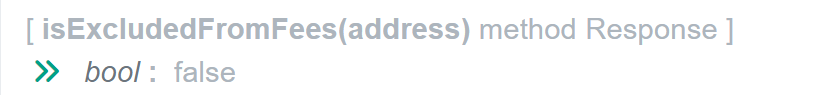
Let us look at how the malicious contract address was set to True on the ExcludedForMaxTxAmount, since this is the part that helps us understand that the person who created the WIZ token and the scammer is the same person.
In the WIZ contract code we found a backdoor, the scammer hardcoded the malicious contract address in the code as mktRecevier, and set the excludeFromMaxTranscation to True for this address:
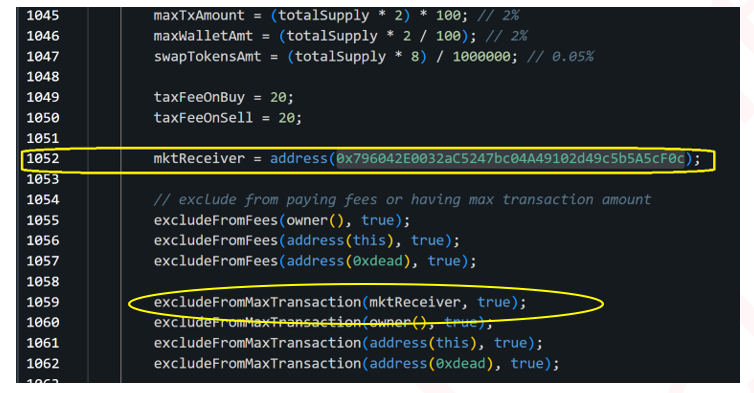
This helps the scammer to pass the second check, and allows him to get to the _burn function.
He then uses this function to burn the WIZ tokens in the WIZ/WETH liquidity pool.
If we will continue to look at the malicious contract code:
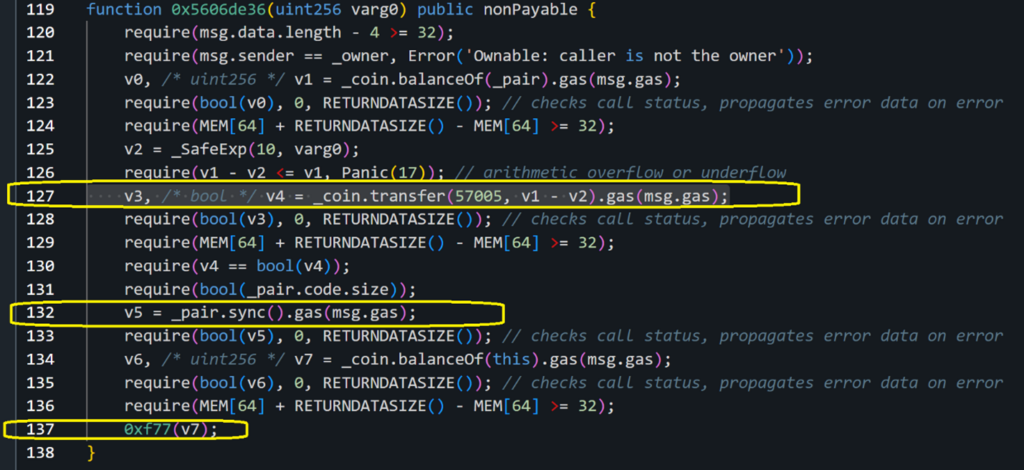
We can see the scammer in line 132 of the malicious contract sync the pool and raises the WIZ price. Then at the end in line 137 executes 0xf77 which sells all the tokens and steals almost 80,000 dollars.
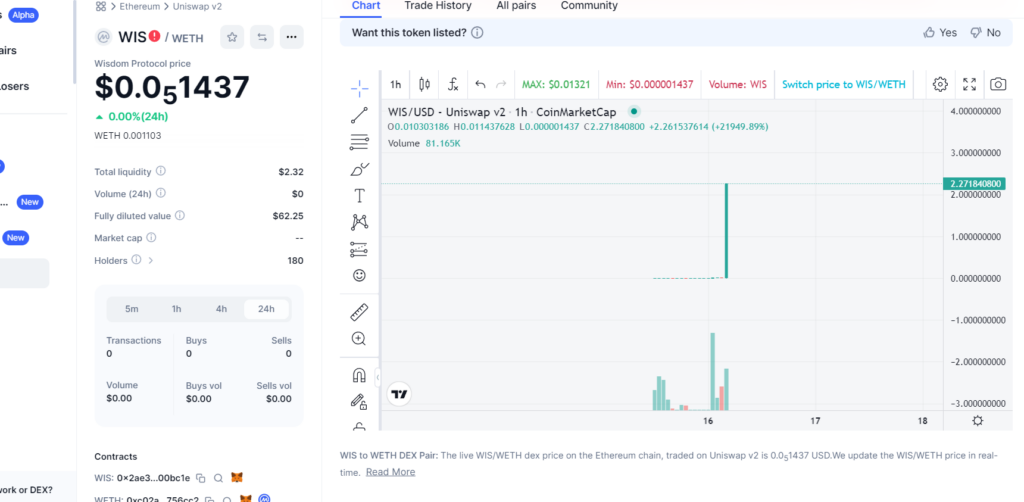
As you can see in CoinMarketCap the price of the token raises by 21949% at the time of this malicious transaction:
Scammer’s Strategy:
The scammer’s approach involves temporarily inflating the token price in the liquidity pool. By manipulating the pool balance, they influence the decentralized exchange prices. Liquidity pools, integral to various contracts, become vulnerable to manipulative schemes.
Conclusion:
This manipulation scheme highlights the susceptibility of liquidity pools to fraudulent activities. Scammers leverage backdoors and exploits to manipulate token prices, emphasizing the importance of vigilance in the decentralized finance space.
Check Point researchers are actively monitoring domains associated with the identified scammer’s wallet address and similar. The Threat Intel Blockchain system, developed by Check Point, continues to accumulate valuable information on emerging threats, and this intelligence will be shared in the future. In this collaborative effort, we aim to empower investors with the knowledge needed to navigate the crypto space securely and protect themselves from potential pitfalls. For more information contact us at: [email protected]





