

By: Dikla Barda, Roaman Zaikin & Oded Vanunu
After reviewing the off-chain forensic report, we can now provide additional insights into the Bybit attack
mechanism.
Security researchers have determined that hackers injected malicious JavaScript directly into Safe’s
online infrastructure hosted on AWS. The code was specifically designed to activate only when
interacting with Bybit’s contract address, allowing it to remain undetected by regular users.
The JavaScript manipulation modified transaction data behind the scenes:
- When Bybit signers accessed the interface, the code identified target addresses
- It silently modified critical transaction parameters including recipient address and operation
type - It preserved the appearance of legitimacy by displaying the original transaction details to signers
Just two minutes after successfully draining $1.4 billion in assets, the hackers removed all traces of themalicious code from Safe’s infrastructure.
This finding confirms our assessment that this attack sets a new precedent in crypto security by
bypassing a multisig cold wallet through sophisticated UI manipulation, further proving that multisigs
and cold wallets are not automatically secure when the interface layer can be compromised.
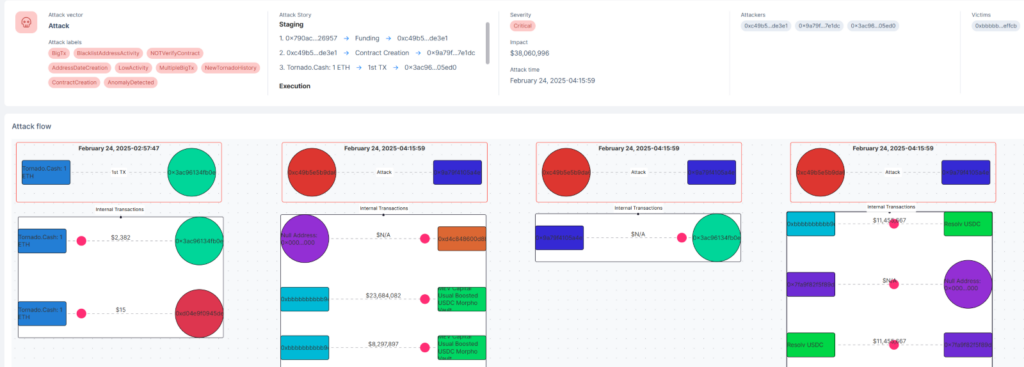
On February 21, Check Point Blockchain Threat Intel System observed a sophisticated attack on a DeFi protocol, Infini.
Infini is a digital banking platform in the crypto space that offers its users savings yields and other financial services. The platform aims to make crypto assets more accessible practical for everyday transactions.
Unfortunately, this project recently suffered a security breach that targeted its yield management system, resulting in the loss of approximately 50 million USDC. The attacker exploited compromised private keys, carefully manipulated access controls, and executed a precise sequence of transactions to drain funds.
Here, we’ll break down the heist step by step.
The Compromised Private Key
The attack began with transactions from address 0xc49b5e5B9DA66B9126c1a62e9761E6b2147DE3E1, which held administrative privileges in the protocol. Infini has stated that they believe this private key may have been compromised.
Private key security is one of the most challenging aspects of blockchain security. Even with best practices in place, sophisticated attackers can sometimes gain access through various vectors, including phishing, malware, or other techniques. Without a full investigation, it’s premature to draw conclude exactly how the administrative access was obtained.
With this key, the attacker could sign transactions as if they were the legitimate owners—a critical first step that gave them initial access to the protocol.
Exploiting the Role-Based Access Control System
Looking at the decompiled contract code, we can see the core function that determines role authorization:
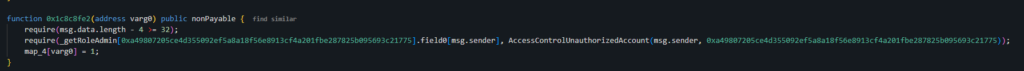
The compromised address had admin privileges, which allowed the attacker to grant the REDEEMER_ROLE to themselves using the stolen key.
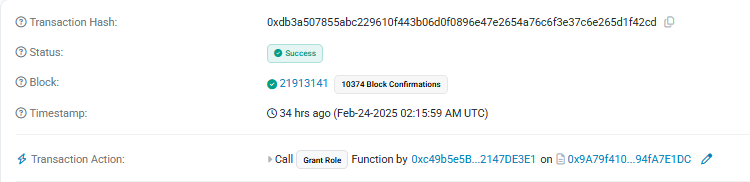
Setting Up the Extraction Path
Before funds could be withdrawn, the attacker needed to register their address as a valid destination. Looking at the contract code, we can see the critical function:

This function registers an address in the map_4 mapping, which the withdrawal function checks during execution.
The attacker used the compromised key to call this function and register their address as a valid destination, setting up the path for the funds to exit the protocol.
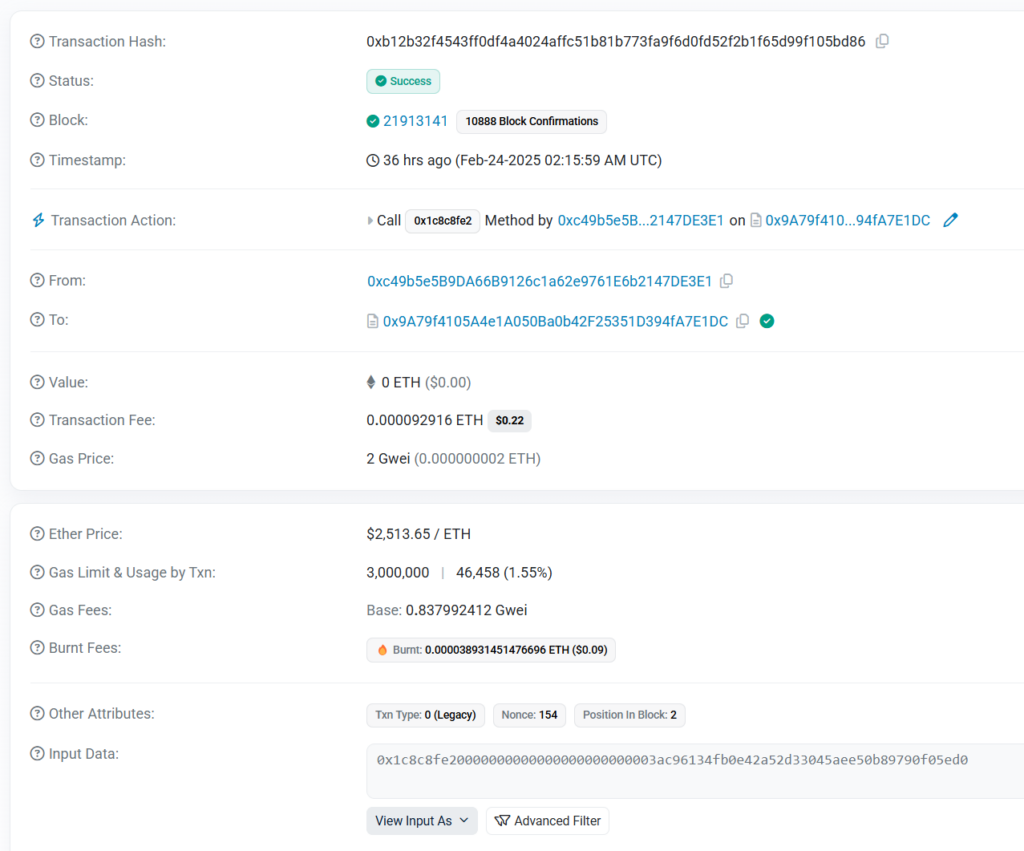
The Withdrawal Function
The heart of this exploit was the ability to call the token redemption function, which has the hex signature 0xcfda09ef. Let’s examine this critical function:
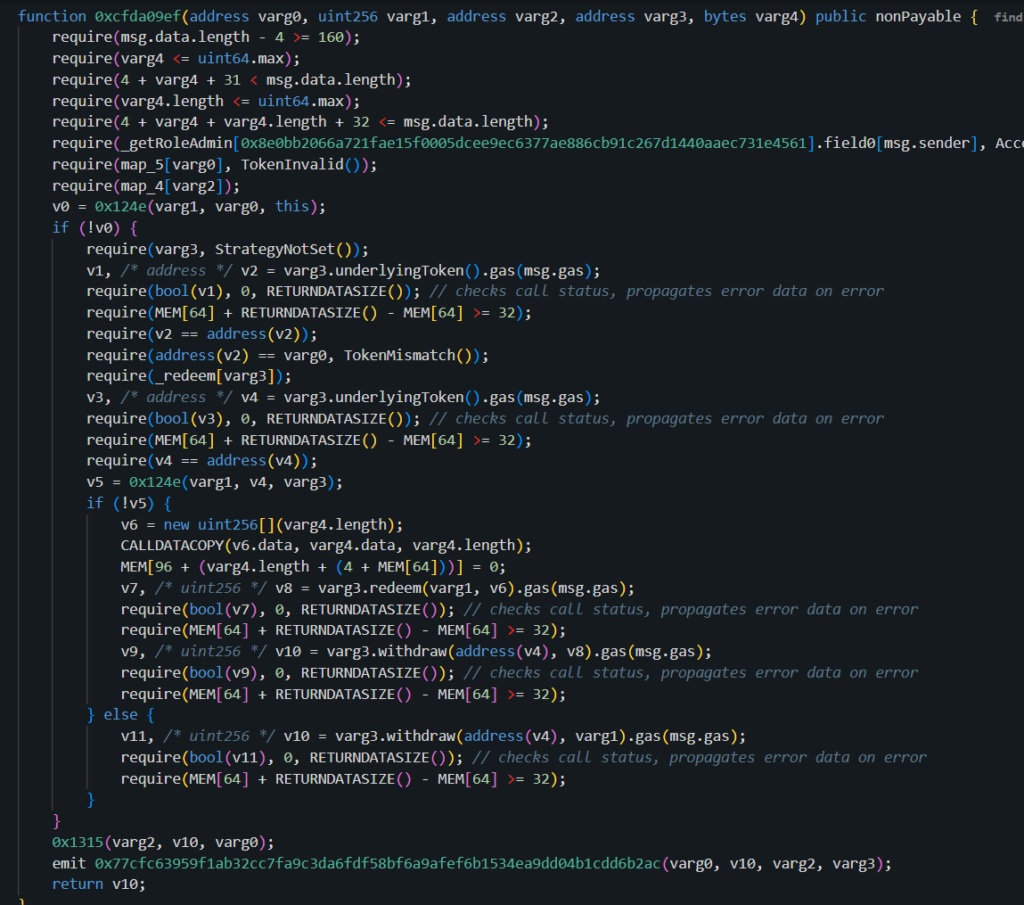
This function works by:
- Checking that the caller has the REDEEMER_ROLE
- Verifying the token is valid, and the destination is registered
- Checking if the contract has enough tokens directly
- If not, pulling tokens from the specified strategy
- Finally, transferring tokens to the destination address
With the REDEEMER_ROLE and their address registered in map_4, the attacker could now call this function to drain funds to their wallet.
The Execution
The attack culminated in a transaction that called the 0xcfda09ef function with these parameters:
Copy
0xcfda09ef000000000000000000000000a0b86991c6218b36c1d19d4a2e9eb0ce3606eb480000000000000000000000000000000000000000000000000000229dc42982570000000000000000000000003ac96134fb0e42a52d33045aee50b89790f05ed0000000000000000000000000e0e83f21d5b6da61c9cf75d3b89fbcacfbfde32700000000000000000000000000000000000000000000000000000000000000a00000000000000000000000000000000000000000000000000000000000000000
When decoded:
- Token: 0xa0b86991c6218b36c1d19d4a2e9eb0ce3606eb48 (USDC)
- Amount: 0x0000000000000000000000000000000000000000000000000000229dc4298257
- Destination: 0x3ac96134fb0e42a52d33045aee50b89790f05ed0 (Attacker-controlled)
- Strategy: 0x0e0e83f21d5b6da61c9cf75d3b89fbcacfbfde327 (Yield strategy holding funds)
- Extra data: Empty byte array
The Bounty Offer
Following the attack, Infini took an approach that has become increasingly common in the DeFi space. The protocol team sent an on-chain message to the attacker, offering a bounty of 20% of the stolen funds (approximately 10 million USDC) if the remaining funds were returned.
The message was embedded in a transaction to the attacker’s wallet and read:
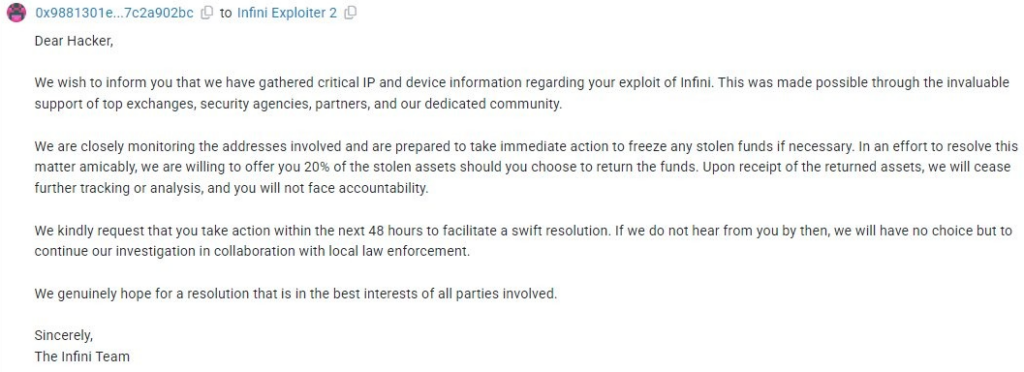
This approach, sometimes called a “white hat agreement” or “bug bounty after the fact,” has occasionally been successful in recovering funds from attacks where the exploiter is primarily motivated by financial gain rather than causing harm to the protocol. The strategy acknowledges that legal recovery of crypto assets can be difficult and time-consuming, while offering the attacker a legitimate way to profit from their discovery without risking legal consequences.
As of the time of writing, it remains to be seen whether the attacker will accept this offer.
Security Lessons
This attack highlights several critical security considerations for DeFi protocols:
- Private Key Security: This compromise was caused by a stolen private key. Hardware wallets, multi-signature schemes, and proper key management are essential.
- Role Separation: The compromised account had both administrative access to grant roles and could add destination addresses. Better separation of duties might have mitigated the impact.
- Time-Locks and Monitoring: Implementation of time-locks for sensitive operations and active monitoring could have detected and potentially prevented the attack before completion.
- Withdrawal Limits: The protocol lacked maximum withdrawal limits, allowing the attacker to drain funds in a single transaction.
Conclusion
This case study demonstrates how seemingly isolated security vulnerabilities can be chained together into devastating attacks. The attacker methodically:
- Obtained a private key with administrative privileges
- Granted themselves the REDEEMER_ROLE
- Registered their address as a valid destination
- Called the withdrawal function to drain approximately 50 million USDC
Each step built upon the previous one, ultimately leading to a complete protocol compromise. While the code contained various security checks, the fundamental issue was that once the private key was compromised, the role-based system could be manipulated from within.
This attack reinforces that security is only as strong as its weakest link, and sophisticated attackers will exploit multiple small vulnerabilities to achieve their goals.



