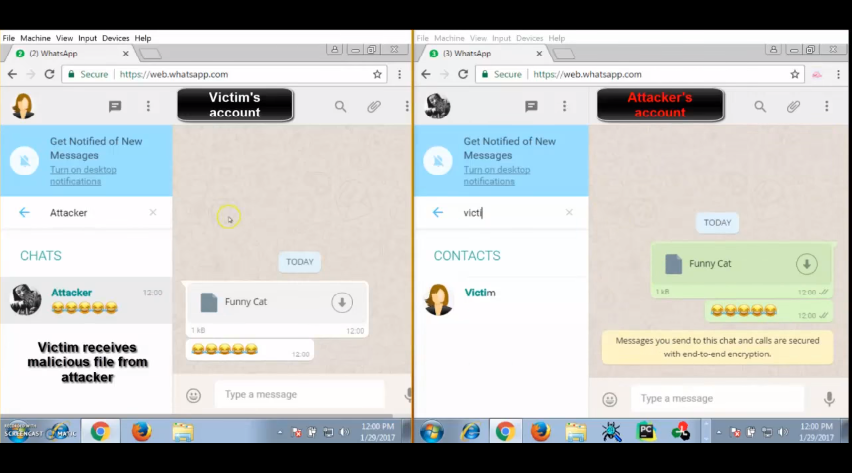
- Demos

https://www.youtube.com/watch?v=7wJhateDKUs
- Demos

https://www.youtube.com/watch?v=6G22gj18xbs
- Demos

https://www.youtube.com/watch?v=jIuvTtzLjGI
- Demos
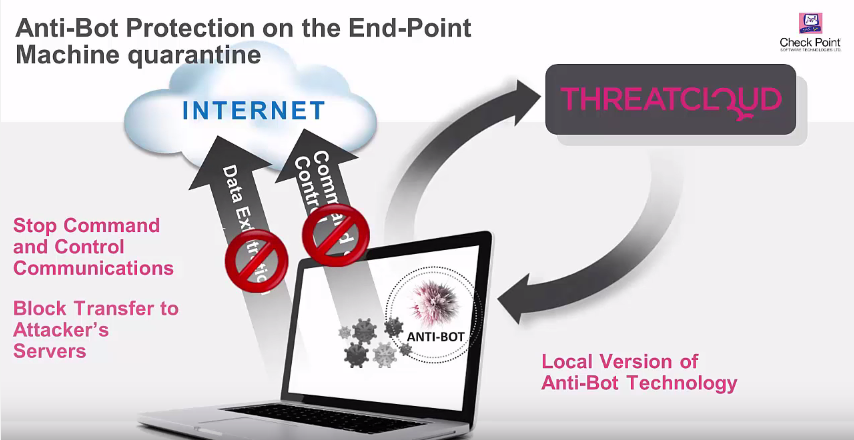
https://www.youtube.com/watch?v=sgmxDZNtOgk&t=32s